Overview of Security Testing in Management Processes
Exploring the importance of security testing in management processes, the Payment Card Industry Data Security Standard (PCI DSS) requirements, and practical demonstrations using tools like VirtualBox and wpscan for testing and securing websites.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Security Testing Outside Looking In Nigel Pentland @nigelpentland
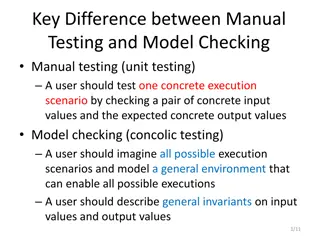
Testing what and why Security is part of a management process https://www.nist.gov/cyberframework Motoring / MOT analogy
Payment Card Industry Data Security Standard What is PCI DSS The payment standard has 12 high level requirements which fall into the six categories below: 1.) Build and Maintain a Secure Network Install and maintain a firewall configuration to protect data Do not use vendor-supplied defaults for system passwords and other security parameters 2.) Protect Cardholder Data Protect stored data (use encryption) Encrypt transmission of cardholder data and sensitive information across public net 3.) Maintain a Vulnerability Management Program Use and regularly update anti-virus software Develop and maintain secure systems and applications 4.) Implement Strong Access Control Measures Restrict access to data by business need-to-know Assign a unique ID to each person with computer access Restrict physical access to cardholder data 5.) Regularly Monitor and Test Networks Track and monitor all access to network resources and cardholder data Regularly test security systems and processes 6.) Maintain an Information Security Policy Maintain a policy that addresses Information Security
https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/ Be sure to get .ova file! Cute command: kali-undercover
Demo local website DNS configuration: Kali Windows sudo nano /etc/hosts As administrator c: cd \windows\system32\drivers\etc notepad++ hosts Add following entry to hosts file 192.168.0.15 local.apache
Using some wpscan commands wpscan --url local.apache/wordpress/ wpscan --url local.apache/wordpress/ --enumerate u cd /usr/share/wordlists sudo gunzip rockyou.txt.gz wpscan --url local.apache/wordpress/ --passwords rockyou.txt
Some additional content follows, i.e. some other useful Kali programs
Nmap certificate scanning nmap -sV --script ssl-cert -p 443 local.apache nmap -sV --script ssl-enum-ciphers -p 443 local.apache