Deploying Secure Applications on Azure PaaS
This session covers essential aspects of deploying secure applications on Azure PaaS, including understanding Azure PaaS products, security offerings, common/best practices, and utilizing Microsoft Defender as a guide. Explore Azure App Service, Azure SQL, security features, limitations, and more, presented by Mitchel Sellers, a Microsoft MVP. Stay informed on Azure security tools, practices, and stay compliant with changing security standards in the Azure world.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Deploying Secure Applications on Azure PaaS
About Your Speaker Mitchel Sellers Microsoft MVP, ASPInsider CEO @ IowaComputerGurus, Inc. Contact Information msellers@iowacomputergurus.com Twitter @mitchelsellers
Agenda Understanding Azure PaaS Products Understanding Azure Security Offerings App Service Networking Security Quick Win App Service VNet Managed Identities & Access Managing Security Center Limitations/Risks with Configurations
Disclaimer The information contained within this session is designed to be an overview only, and provide a starting point for understanding and implementation within your own application/solution architectures. Please be sure to read ALL relevant Microsoft documentation and verify fitness to your particular application before implementation Security features, and configuration, within the Microsoft Azure world, are ever changing and careful validation is needed.
Azure PaaS Offerings The Basic Stuff Azure App Service Azure Functions Power Apps Azure SQL Azure Blob Storage Azure Cosmos DB The Secure or Private stuff More Expensive Isn t Always Secure Azure App Service Isolated instances Azure SQL Managed Instance
Azure Security Offerings Microsoft Defender for Cloud The product is formerly known as Security Center Think of it as Audit/Compliance tool or workbook Can help to educate as changes occur in Azure Built In Security Microsoft Anti Malware - https://docs.microsoft.com/en- us/azure/security/fundamentals/antimalware Magic, and has limitations Azure Firewall Azure Front Door Individual Service Features
Common/Best Practices Excluded SSL Configurations TLS Configuration Load Balancing Backups Audit/Log Retention
Using Microsoft Defender as Guide The primary purpose of Microsoft Defender is to provide guidance, compliance, and reporting on security standards. However, as with any reporting and compliance tool, it is only as good as the user of the tool. False Positives Storage Accounts should NEVER allow public read access Well .except for those used for a CDN Subscriptions should ALWAYS have more than one admin Well .except for CSP controlled subscriptions that utilize a foreign principle System Limitations may require disabling/adjusting
Microsoft Defender for Azure Pricing
Key Defender Helpers to Security SQL Databases Management/Audit of High-Privilege accounts Management/Audit of IP Address Rules Management of Vulnerability Monitoring Setting of Admin Accounts Web Applications Forcing of SSL Disabling of Plain FTP
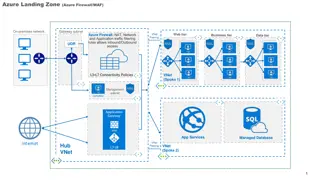
App Service VNet By adding your App Service & Azure SQL Server to a Vnet you can get private networking, in the public cloud. Accomplished by creating a Vnet, Adding it to the SQL Server and App Service, then you can deny access to Azure Services for the Vnet.
Azure Front Door & Incoming Traffic Complex Pricing Standard $35/month + Bandwidth But is only a CDN Premium $330/month + Bandwidth Includes Firewall Works incredibly well, but not fully supported for configuration by all DNS providers Can obtain similar functionality via other means
Securing Access to Assets Azure Active Directory (AAD) integration allows App Service, and other Azure resources to have individual service accounts. Unique per resource and managed via Azure Can be granted access to things such as SQL Server or otherwise Allows password-less authentication EF Core Requires the addition of Microsoft.Data.SqlClient project https://docs.microsoft.com/en-us/azure/app-service/tutorial-connect-msi-sql- database?tabs=windowsclient%2Cefcore%2Cdotnet Connection: "Server=tcp:<server-name>.database.windows.net;Authentication=Active Directory Default; Database=<database-name>; CREATE USER [<identity-name>] FROM EXTERNAL PROVIDER; ALTER ROLE db_datareader ADD MEMBER [<identity-name>]; ALTER ROLE db_datawriter ADD MEMBER [<identity-name>]; ALTER ROLE db_ddladmin ADD MEMBER [<identity-name>];
Additional VNET & Identity Concerns Storage Accounts If the storage account is ONLY accessed via Azure Resour Azure Functions Other Applications
Risks with Implementing Changes Far more efficient to implement changes before in production, but it is possible to deploy as needed Not all changes are additive you may need to remove features too, which have less backout options For example, you can add a VNET, and get it all working, but the only way to validate is to kill access.
Questions? Feel free to reach out for specific guidance/help as well msellers@iowacomputergurus.com @mitchelsellers on Twitter