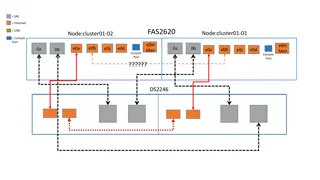
BSIP 101 Citrix Usage Policies and Technical Guidelines
"Learn about the BSIP 101 Citrix usage policies and technical guidelines for remote access. Understand the responsibilities, limitations, and security standards associated with using personal equipment and accessing the Internet while offsite. Contact Stephen Wright for any questions or assistance."
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
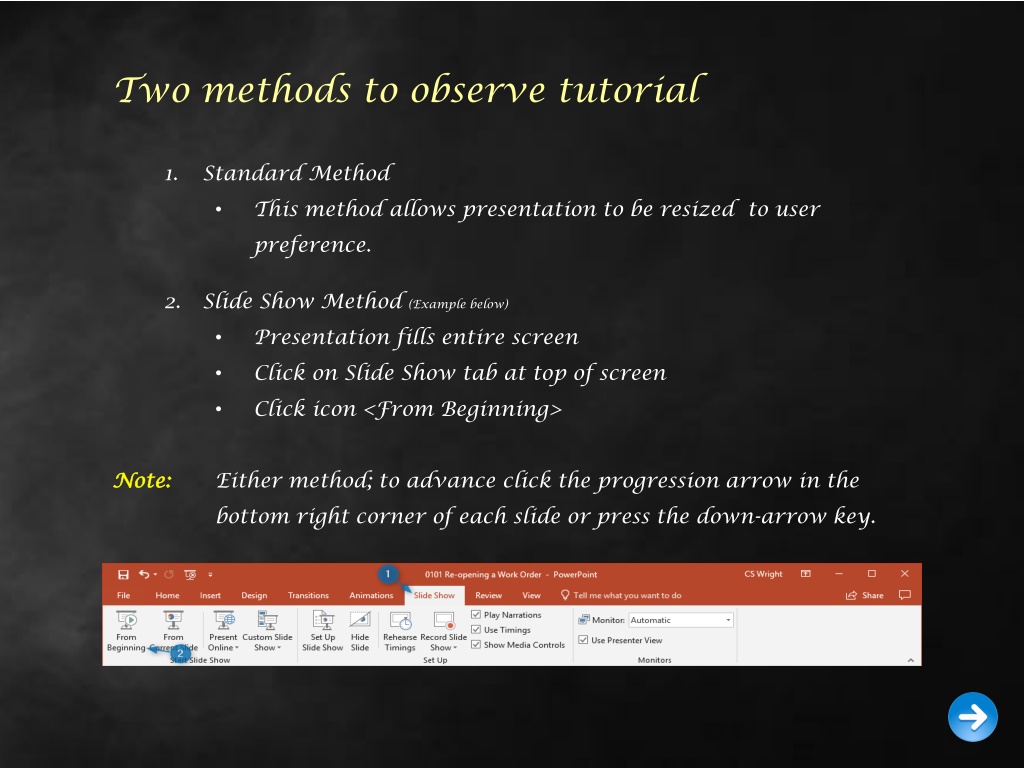
Two methods to observe tutorial 1. Standard Method This method allows presentation to be resized to user preference. 2. Slide Show Method (Example below) Presentation fills entire screen Click on Slide Show tab at top of screen Click icon <From Beginning> Note: Note: Either method; to advance click the progression arrow in the bottom right corner of each slide or press the down-arrow key.
Welcome to BSIP 101 Citrix Usage Policies Instructor: Stephen Wright DPI Technical Consultant
1. You may use personal equipment while offsite to facilitate this service. However, IT Technical Services is not responsible for loading or maintaining privately owned personal computers. 2. It is your responsibility to arrange access to the Internet via an Internet Service Provider (ISP). 3. Due to software limitations, local printing is not guaranteed to work for Citrix applications on the DOT/DPI network or through this service. 4. You must not share any system or user information regarding this service with anyone either inside or outside DOT/DPI. Specifically, the sharing of user ids and passwords is explicitly forbidden. If another employee needs this service, they must get the proper approval and authorization. 5. In compliance with the State of North Carolina Enterprise Security Standards and the NC DOT supplemental standards, all usage of the remote access system will be logged and can be audited at the discretion of IT-Technical Services. Privacy is not guaranteed with the use of this system. 6. This list does not constitute an exhaustive list of rules and procedures and can be updated as needs arise. IT-Technical Services retains the right to revoke access to this service for noncompliance with security policies, at the request of the Unit Manager, or any other reasonable circumstance.
Questions Questions Email: Email: Stephen.Wright@dpi.nc.gov
Thank You! Thank You! Stephen Wright Stephen Wright Technical Consultant Technical Consultant