Understanding Multimedia Systems: Hardware and Software Components
Multimedia systems require specific hardware and software components to meet the demands of producing and playing multimedia content. Development systems are used for creating content with higher specifications, while playback systems are used for playing multimedia files with lower specifications.
8 views • 46 slides
Embedded Systems Design Process in the Embedded systems
Embedded systems are all around us, from the tiny microcontrollers in our household appliances to the sophisticated control systems in cars and aeroplanes. But how are these systems designed? Let's delve into the basics of the embedded systems design process in simple terms that anyone can understan
2 views • 9 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
9 views • 126 slides
Understanding Information Systems in Organizational Management
Management in organizations is divided into three levels: operational, tactical, and strategic. Each level requires different information systems to support various activities. Operational systems focus on routine transactions and control processes, while middle-level systems aid in semi-structured
9 views • 39 slides
Understanding System Management RAM (SMRAM) in x86 Architecture
Delve into the internals of System Management RAM (SMRAM) in x86 architecture, exploring how the processor switches to SMRAM upon entering System Management Mode (SMM). Learn about SMBASE, the base address of SMRAM, and how the address space layout is defined. Discover how SMBASE and SMRAM are essen
1 views • 43 slides
Securing BIOS: Flash Protection Mechanisms and Best Practices
Explore advanced x86 BIOS security mechanisms like Global Flash Protection, Global BIOS Write Protection, and SMM-derived Write Protection to prevent unauthorized writing to the BIOS. Discover how BIOS vendors can enhance security configurations to thwart attackers effectively.
2 views • 38 slides
Introduction to Intel Assembly Language for x86 Processors
Intel Assembly Language is a low-level programming language designed for Intel 8086 processors and their successors. It features a CISC instruction set, special purpose registers, memory-register operations, and various addressing modes. The language employs mnemonics to represent instructions, with
2 views • 12 slides
Understanding Different Types of Recommender Systems
Recommender systems play a crucial role in providing personalized recommendations to users. This article delves into various types of recommender systems including Collaborative Filtering, Content-Based, Knowledge-Based, and Group Recommender Systems. Collaborative Filtering involves making predicti
0 views • 7 slides
Understanding Memory Virtualization in Operating Systems
Memory virtualization in operating systems involves mapping guest addresses to host addresses with an added level of indirection managed by the hypervisor. Virtualization extensions in x86 processors enhance efficiency by allowing safe execution of guest code in Ring 0 through supervisor mode. The a
1 views • 28 slides
Understanding PCI Expansion ROMs in x86 Systems
This content delves into the intricacies of PCI Expansion ROMs (XROMs) in x86 systems. It covers the basics of XROMs, their execution during the boot process, configuration through Expansion ROM Base Address Register, and handling in PCI and PCIe devices. The role of BIOS in initializing XROMs and t
4 views • 21 slides
Understanding PCI/PCIe Expansion ROMs in x86 Systems
Explore the internals of PCI/PCIe Expansion ROMs (XROMs) in x86 systems, examining their role as executable code located on PCI devices, handling by BIOS during boot, configuration via Expansion ROM Base Address Register, and differences on legacy versus modern systems.
4 views • 21 slides
Introduction to Embedded Systems Design
Embedded Systems Design, Chapter 1 provides an insightful overview of embedded systems, distinguishing them from general-purpose computers. The chapter delves into the characteristics of embedded systems, their design considerations, and the various types of embedded computers such as general-purpos
1 views • 7 slides
Understanding System Management Mode (SMM) in x86 Processors
System Management Mode (SMM) is a highly privileged mode in x86 processors that provides an isolated environment for critical system operations like power management and hardware control. When the processor enters SMM, it suspends all other tasks and runs proprietary OEM code. Protecting SMM is cruc
1 views • 26 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
Binary Basic Block Similarity Metric Method in Cross-Instruction Set Architecture
The similarity metric method for binary basic blocks is crucial in various applications like malware classification, vulnerability detection, and authorship analysis. This method involves two steps: sub-ldr operations and similarity score calculation. Different methods, both manual and automatic, ha
0 views • 20 slides
Understanding Flash Descriptor in x86 Systems
Explore the internals of the Flash Descriptor in x86 systems, essential for BIOS and system management mode. Learn about SPI regions, determining SPI regions, flash protection mechanisms, and the structure of the Flash Descriptor for Intel systems. Complete with images and detailed explanations.
5 views • 30 slides
Understanding Virtualization in Modern Systems
Virtualization plays a crucial role in modern systems by improving portability, security, and efficient resource utilization. Historical uses, examples like IBM VM/370, and benefits in cloud environments are discussed. The working of virtualization, including naive software interpreters and protecte
1 views • 18 slides
Fundamentals of Operating Systems Explained
Explore the core concepts of operating systems, including kernel-userspace interactions, system calls, context switching, and virtual memory management. Delve into x86 assembly for system calls, hardware interrupts, and the flow of control during system call invocations. Gain insights into key compo
7 views • 19 slides
15-213 Recitation: Bomb Lab Overview and Tips
This content covers the Bomb Lab exercise in x86-64 assembly code and GDB debugging techniques. It explains the purpose of Bomb Lab, downloading the bomb, detonating the bomb, hints for solving phases, and x86-64 Linux register usage. The material emphasizes the importance of using GDB for efficient
1 views • 42 slides
Buffer Overflows in CSE351 Autumn 2017
Explore buffer overflows in CSE351 Autumn 2017, covering topics like memory layout, stack, heap, and defenses against buffer overflows. Learn about important concepts such as input buffers, code injection, and memory allocation examples, with insights into x86-64 Linux memory layout.
0 views • 33 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Understanding Memory Layout in Computer Systems at Carnegie Mellon
Explore the memory layout in computer systems through the lens of Carnegie Mellon University's advanced topics in machine-level programming. Learn about buffer overflow vulnerability protection, memory allocation examples, x86-64 Linux memory layout, and addressing schemes. Dive into practical examp
2 views • 47 slides
Advanced Multi-Threaded Development Overview
Explore the challenges and tips for developing multi-threaded applications in a workshop conducted by Jarrod Hollingworth in Melbourne. Learn about thread safety, Delphi Parallel Programming Library, and delve into low-level thread details. Dive into parallel programming with XE7+ and discover TPara
0 views • 15 slides
Framework for Developing Verified Assemblers for ELF Format
This research paper discusses the importance of verified assemblers in the context of verified compilation, focusing on the development of verified assemblers for the ELF format for multiple architectures like X86, RISC-V, and ARM. The framework aims to be configurable, extensible, and general to su
0 views • 32 slides
Information Systems in Organizations: Overview and Implementation
Information systems play a crucial role in organizations, encompassing transaction processing systems, functional area information systems, and enterprise resource planning systems. This content delves into the purpose of transaction processing systems, the support provided by information systems ac
0 views • 30 slides
Understanding Memory Layout and Allocation in Computer Systems at Carnegie Mellon University
Exploring the memory layout and allocation in computer systems through lectures at Carnegie Mellon University, focusing on topics such as buffer overflow vulnerability protection, unions, shared libraries, stack, heap, data locations, addresses, and practical memory allocation examples. The content
1 views • 55 slides
Introduction to Y86 Instruction Set Architecture
Y86 Instruction Set Architecture is a simplified pseudo-language based on x86 (IA-32) architecture. It involves implementing the Fetch-Decode-Execute cycle, where instructions are fetched from memory, decoded, and executed. The Y86 ISA offers a simpler set of instructions and formats compared to x86
0 views • 25 slides
Simplifying Post-Silicon Timing Diagnosis with NGSPA Tool
Explore how the NGSPA tool by Intel simplifies post-silicon timing diagnosis, replacing costly machines with a CAD application running on an x86 server, saving resources and enabling parallelized CAD operations. Learn about the challenges in post-silicon speed debugging, the importance of static tim
0 views • 26 slides
Understanding SMI Suppression in x86 BIOS Management
Delve into the intricacies of SMI Suppression in x86 BIOS and System Management Mode internals, where SMI stands as a crucial defense mechanism to safeguard the BIOS flash from unauthorized modifications. Explore the impact of suppressing SMI generation and learn about the SMI_EN register's role in
1 views • 18 slides
Understanding Interrupt Processing Sequence in X86 Processors
X86 processors have 256 software interrupts, functioning similarly to a CALL instruction. When an INT n instruction is executed, the processor follows a sequence involving pushing the flag register, clearing flags, finding the correct ISR address, and transferring CPU control. Special interrupts lik
0 views • 10 slides
Understanding X86 ISA Flags in System Security
This article delves into the details of various flags in the X86 ISA architecture, such as CF (Carry Flag), PF (Parity Flag), AF (Auxiliary Flag), ZF (Zero Flag), SF (Sign Flag), TF (Trace Flag), IF (Interrupt Flag), DF (Direction Flag), OF (Overflow Flag), and IOPL (Input Output Privilege Level). T
0 views • 16 slides
Assembly Programming in CSE351 Spring 2017
Explore the world of assembly programming through CSE351 in Spring 2017. Delve into topics like memory, data, x86 assembly, procedures, executables, arrays, and more. Learn about the differences in Java and C, machine code, hardware, compilers, and the factors that influence program performance. Und
0 views • 24 slides
Efficient Memory Virtualization: Reducing Dimensionality of Nested Page Walks
TLB misses in virtual machines can lead to high overheads with hardware-virtualized MMU. This paper proposes segmentation techniques to bypass paging and optimize memory virtualization, achieving near-native performance or better. Overheads of virtualizing memory are analyzed, highlighting the impac
0 views • 48 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
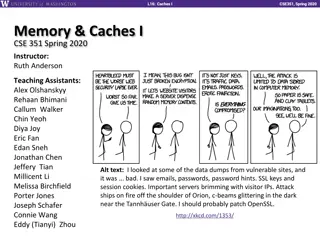
Memory and Caches in CSE 351 Spring 2020: Insights and Roadmap
Exploring the world of memory and caches in CSE 351 Spring 2020 led by Instructor Ruth Anderson and her dedicated team of Teaching Assistants. Discover the essential topics covered such as data integers, x86 assembly, processes, and more. Dive into the nuances of memory allocation, Java implementati
0 views • 30 slides
Understanding Microprocessor Architecture and Instruction Processing
Explore the basic architecture of a microprocessor, including CPU registers, memory locations, and instruction processing steps. Learn about Intel microprocessor components, addressing modes, and the operation of pipeline microprocessors. Understand the role of control units, ALU, and bus interfaces
0 views • 38 slides
Introduction to Malware Reverse Engineering
Explore the fundamentals of reverse engineering malware in this comprehensive guide for beginners. Covering topics like x86/64 ASM basics, setting up an environment, using debuggers, malware analysis techniques, and essential tools needed for the trade. Learn about the importance of software breakpo
0 views • 35 slides
Understanding Embedded Systems and Cyber-Physical Systems
Embedded systems are specialized computer systems embedded within larger systems, such as control systems and car controllers. This lecture covers real-time aspects, applications of Cyber-Physical Systems (CPS), and examples like the Boeing 777/Airbus A380 cockpit. It discusses the design process of
0 views • 22 slides
Hardware Performance Monitoring with Kernel Modules
This document explores the use of hardware performance counters and cycle counting on x86 and ARM architectures for monitoring and analyzing system performance. It covers topics such as the utilization of hardware counters, cycle counting on x86 processors, and the ARM Performance Monitor Unit (PMU)
0 views • 12 slides
Understanding Instruction Set Architectures (ISAs) in Computer Science
Explore the concepts of RISC, CISC, and ISA variations in computer architecture. Dive into the differences between MIPS, ARM, X86, and other ISAs, focusing on load/store, arithmetic, control flow, and more. Gain insights into the evolution and variations of ISAs, and discover the alternatives beyond
0 views • 37 slides