Gear Types and Applications in Power Transmission
An overview of different types of gears, their nomenclature, and applications in power transmission. Learn about spur gears, helical gears, rack and pinion, bevel gears, worm gears, and gear trains.
4 views • 28 slides
Biology of Eisenia foetida (Manure Worm)
Learn about Eisenia foetida, a key earthworm species used in vermicomposting, its identification, ecology, efficiency, and morphology. Discover its burrowing habits, feeding behavior, reproduction capabilities, and environmental preferences for optimal performance in composting.
0 views • 25 slides
Insect Identification for FFA Agronomy Skills Contest
Explore a variety of insects including the Alfalfa Weevil, Aphid, Army Worm, Assassin Bug, Bean Leaf Beetle, Black Cutworm, Chinch Bug, Colorado Potato Beetle, Common Stalk Borer, Corn Earworm, Corn Rootworm, Cricket, Cucumber Beetle, European Corn Borer, Flea Beetle, Grasshopper, Green Lacewing, Gr
1 views • 37 slides
Stuxnet: The Changing Face of Cyberwarfare
A deep dive into the Stuxnet cyberweapon, a malicious computer worm targeting industrial control systems with its sophisticated capabilities, affecting multiple countries and posing significant threats to critical resources. Despite being linked to American and Israeli origins, neither country has a
2 views • 11 slides
Elevate Performance with Parkash Industrial Gears' Precision Worm Gear Manufactu
Parkash Industrial Gears excels in worm gear manufacturing, offering precision-engineered solutions for diverse industrial applications. With decades of expertise and cutting-edge technology, we ensure the highest standards of quality and accuracy in every gear produced. Our dedication to excellence
5 views • 7 slides
Choosing the Perfect Gear Manufacturer: A Comprehensive Guide
Selecting the right gear manufacturer is pivotal for machinery quality and longevity. Parkash Industrial Gears is a leading in bevel, spur, helical, and worm gear manufacturer. This article guides you through choosing the perfect gear manufacturer, focusing on quality, customization, advanced techno
1 views • 9 slides
Comprehensive Guide to Precision Gear Manufacturing Processes
This comprehensive guide by Parkash Industrial Gears explores the manufacturing processes of worm gear manufacturing, bevel gears, spur gears, and helical gears. Learn about the precision crafting techniques and materials used to ensure durability and efficiency in these essential mechanical compone
0 views • 7 slides
Worm Gear Manufacturing Unveiled: Driving Industries Forward with Precision
Explore the intricate world of gear manufacturing with our comprehensive guide. From the precision of worm gear manufacturing to the efficiency of helical gears and the versatility of bevel gears, discover how these components drive industries forwar
1 views • 8 slides
Understanding Stephanurus Dentatus: Kidney Worm of Pigs
Stephanurus dentatus is a parasitic worm that infects pigs, with an intricate life cycle involving earthworms as transport hosts. Transmission occurs through ingestion of larvae or infected earthworms, leading to various pathological effects, including subcutaneous nodules, cirrhosis, and organ dama
0 views • 13 slides
Overview of Hookworm, Toxocariasis, and Guinea Worm Infections
These infections are significant global health issues affecting millions of individuals worldwide. Hookworm infection, a leading cause of iron-deficiency anemia, is prevalent in tropical and sub-tropical regions. Risk factors include poor sanitation and walking barefoot on contaminated soil. The bio
0 views • 46 slides
Overview of Ancylostoma duodenale (Hookworm) Infection
Ancylostoma duodenale, a parasitic worm causing Ancylostomiasis, is discussed in this lecture. The infection's distribution, morphology, life cycle, and pathology are detailed, emphasizing the impact on humans. The lifecycle stages, including egg production, larval development, and entry into the hu
0 views • 12 slides
Understanding Anthelmintics: Drug Therapy for Parasitic Worm Infections in Veterinary Medicine
Anthelmintics are essential drugs to combat parasitic worm infections in animals. They work either by killing (vermicide) or expelling (vermifuge) the worms, reducing worm burdens and controlling infections. This comprehensive overview covers different aspects of anthelmintics, including their prope
2 views • 34 slides
Understanding Curl-Free and Div-Free Radial Basis Functions in Physical Situations
This content explores the applications of Curl-Free and Div-Free Radial Basis Functions in solving partial differential equations for fields, the theoretical soundness of using RBFs, and examples illustrating divergence-free interpolation. It also delves into matrix-valued RBF formulations, converge
3 views • 13 slides
Comprehensive Overview of Toxocara canis Life Cycle and Characteristics
Toxocara canis, also known as the Arrow-headed worm, is a parasite commonly found in dogs, particularly in puppies less than six months old. This article explores the general characteristics, life cycle, transmission routes, and prenatal infections of Toxocara canis. From the appearance of the male
0 views • 12 slides
Understanding Anthelmintics in Veterinary Pharmacology
This lecture by Dr. Kumari Anjana covers anthelmintic drugs used in veterinary medicine, focusing on the classification of simple heterocyclic compounds, benzimidazoles, and their prodrugs. It discusses the spectrum, mechanism of action, administration, contraindications, and uses of piperazine and
0 views • 27 slides
Understanding Echinococcus Granulosus and Hydatid Disease
Echinococcus Granulosus, also known as the hydatid worm or dog tapeworm, causes cystic echinococcosis. The tapeworm has distinct characteristics and a complex life cycle involving canids as definitive hosts and humans as accidental hosts. Hydatid disease in humans can be dangerous, with symptoms var
0 views • 8 slides
Major Information Security Challenges Faced by Financial Services Firms
In today's digital age, large financial services firms encounter significant information security challenges such as exponential growth in malware threats, sophisticated cyber attacks, and frequent penetrations of information systems. The perfect storm of technological advancements and connectivity
0 views • 29 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Fossorial Specimens: Mole and Caecilian Adaptations
Fossorial specimens, including the mole and caecilian, are uniquely adapted for subterranean burrowing. The mole, commonly known for its wedge-shaped head and reduced eyes, lives in tunnels and feeds on small worms and insects. On the other hand, the limbless caecilian, resembling a worm, thrives in
1 views • 25 slides
Nature's Astonishing Encounters: Beauty, Danger, and Intrigue
Nature's diversity is showcased in captivating images, from a fish hosting a parasitic tongue-eating creature to a hermit crab using a doll's head as a shell. Witness intriguing phenomena such as calcified flowers, a snake's head caterpillar, and a toothed worm from Antarctica. Discover extraordinar
1 views • 33 slides
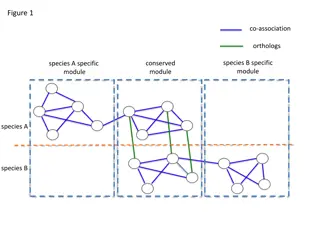
Comparative Genomics Analysis of Co-Association Networks in Species A and B
Explore Figures 1 through 5 depicting a novel method for identifying co-association networks of orthologs between species A and B. The analysis includes optimizing a cost function through simulated annealing, identifying cross-species modules, and assessing network modularity with respect to GO refe
1 views • 17 slides
Understanding Trichostrongyle Transmission and Strategic Control
Trichostrongyle transmission primarily occurs through pasture contamination with eggs shed by adult worm populations in grazing hosts. The development of infective larvae on pasture involves specific conditions like moisture and warmth, leading to different types of ostertagiasis infections. Various
0 views • 20 slides
Important Information on National Deworming Day
Educational outcomes, cognitive development, nutritional uptake, and physical growth are crucial for a child's well-being. Protect your child from worm infestation by following preventive measures such as keeping surroundings clean and ensuring deworming on National Deworming Day. Worm infestations
0 views • 14 slides
The Digestive System of Worms: Functions and Structure
The digestive system of a worm plays a crucial role in converting its food intake into energy. It consists of various parts such as the mouth, crop, gizzard, esophagus, intestine, and anus. The mouth serves as the entry point for food intake, leading to further digestion through the other components
0 views • 9 slides
Effective Fuzz Testing for Programmable Logic Controllers - Research for Nuclear Safety
This paper discusses the significance of fuzz testing for Programmable Logic Controllers (PLCs) to ensure nuclear safety, citing incidents like the Stuxnet worm attack. It delves into the methodology, zero-day vulnerability findings, and results of the research conducted by authors in February 2020,
1 views • 11 slides
Silk Worm Life Cycle and Culture at Mohanlal Sukhadiya University Udaipur
The life cycle of silk worms, particularly Bombyx mori, is detailed in this practical study conducted by the Department of Zoology at Mohanlal Sukhadiya University, Udaipur. The process from eggs to larvae, cocoon formation, and the emergence of the adult silk moth is explained. Silk worms feed on m
0 views • 13 slides
Understanding Buffer Overflow in Computer Programming
This content delves into the intricacies of buffer overflow vulnerabilities in computer programming, showcasing real-world examples such as the Internet Worm and IM War incidents. It covers topics like stack buffer overflow exploits, Unix function implementations prone to buffer overflow, and the re
1 views • 35 slides
Evolution of Vulnerability Disclosure Practices
The history of vulnerability disclosure, from the early days of mailing lists and zines to the emergence of Full Disclosure and the debates around anti-disclosure groups. The timeline covers key events like the Morris worm, Code Red, the founding of Bugcrowd, and more, illustrating the evolution of
0 views • 11 slides
Understanding Giant Intestinal Roundworms: Ascaris lumbricoides
Ascaris lumbricoides, also known as the Giant Intestinal Roundworm, is a common parasitic nematode infecting the human intestines, especially prevalent in underdeveloped regions with poor sanitation. Found in the small intestines, this worm can cause significant health issues. Learn about its morpho
0 views • 31 slides
Unveiling the Remez in Psalm 22:6 - Journey into Hebrew Symbolism
Delve into the mysterious symbolism of Psalm 22:6, exploring the hidden meaning behind the term "worm" and its profound significance in the context of Hebrew scripture and prophetic allusions to the Messiah's sacrifice. Unravel the layers of interpretation, from the traditional Hebrew translations t
0 views • 23 slides
Understanding Cestoda: The Tapeworms in Platyhelminthes
Cestoda, a class of parasitic flatworms in the phylum Platyhelminthes, have a unique body structure with a scolex, neck, and segmented strobila. These tapeworms lack a digestive tract, absorbing nutrients through their body. They are hermaphrodites, with male and female reproductive organs in the sa
0 views • 12 slides
Understanding Heterakis Gallinarum: Poultry Ascarid Worm
Heterakis gallinarum, a caecal worm found in domestic and wild birds, plays a role in transmitting Histomonas meleagridis, causing diseases like blackhead in turkeys. Clinical signs include anaemia, diarrhoea, and emaciation. Diagnosis involves microscopic examination, and treatment with fenbendazol
0 views • 10 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Learn the Break-Dancing Move - Kick-Worm or Caterpillar!
Explore the iconic break-dancing move known as the kick-worm or caterpillar, its history, and popularity. Discover how to perform this dance skill at events like parties, weddings, and more. The step-by-step instructions and muscle engagement guide will help you master this dynamic movement.
0 views • 19 slides
Overview of Common Worm Infestations in Children and Neglected Tropical Diseases (NTDs)
Common worm infestations in children, such as Ascaris lumbricoides and Enterobius vermicularis, are a significant health concern globally. Neglected Tropical Diseases (NTDs) like ascariasis, hookworm, and lymphatic filariasis affect millions of people, particularly those in poverty. For just 50 cent
0 views • 25 slides
Understanding Tape Worm Diseases in Veterinary Medicine
Tape worm diseases, such as cysticercosis and coenurosis, affect various animals like sheep, cattle, horses, dogs, and cats. The pathogenesis involves indirect mechanisms, leading to larval stages like metacestodes. Heavy infections can result in colic, diarrhea, and anemia in animals. Diagnosis inv
0 views • 14 slides
National Deworming Day - August 10: Ensure Your Child's Health
National Deworming Day on August 10 aims to provide children with a worm-free life. Don't miss the opportunity to deworm your child and promote their well-being. The event emphasizes the importance of deworming for physical and cognitive development. Albendazole, a safe and beneficial treatment, wil
0 views • 9 slides
Kiwi's Nighttime Adventure: A Charming Story
Join Kiwi the bird in his nighttime escapades in the forest as he wakes up, searches for food, and enjoys a delicious meal of a worm. Follow along as Kiwi fills his stomach and experiences pure happiness under the starlit sky.
0 views • 10 slides
Understanding Lock-Free and Wait-Free Algorithms in Concurrent Data Structures
Illustration of lock-free and wait-free algorithms compared to blocking algorithms, with insights on concurrent object execution, blocking vs. non-blocking algorithms, definitions, comparisons between locks, lock-free, and wait-free approaches, and explanations on making algorithms wait-free. Exampl
0 views • 23 slides
Understanding Weaknesses of Discretionary Access Control (DAC) in Data Security
Explore the vulnerabilities of DAC in data security through a detailed examination of the Morris Worm incident as a case study. Learn about the implicit trust in program integrity, sandboxing approaches, and the need to align access control policies with program behavior.
0 views • 65 slides