Efficient Remote Work Strategies for Optimal Productivity
Learn best practices for remote work to navigate slow VPN connections, offline mode usage, browser settings for better performance, and effective data synchronization. Discover ways to enhance productivity and avoid network-related challenges while working remotely.
5 views • 8 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Credentialing Process for Adjuncts and GTAs Created by Felipe Vargas
This process overview details the steps and requirements for credentialing adjuncts and Graduate Teaching Assistants (GTAs). It covers accessing the Wizard program, submitting necessary documents, and the workflow from department to Provost. Various credentialing avenues are explained based on degre
0 views • 20 slides
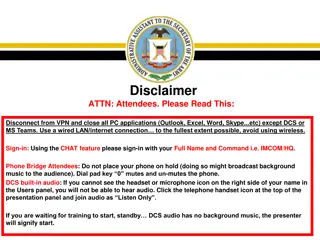
Army Records Management Virtual Symposium
Army Records Management-FOIA-Privacy-Civil Liberties Virtual Symposium will cover topics such as ARCIS, records retention schedules, record transfers, and accessing ARCIS accounts. Attendees are required to disconnect from VPN, use wired LAN, and follow specific guidelines for audio and phone usage
0 views • 21 slides
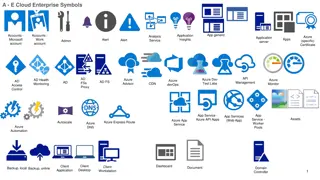
Symbolic Representation of Azure Cloud Enterprise Services
The images depict a variety of symbols representing different Azure cloud enterprise services, including application insights, analysis, monitoring, security, storage, virtual networks, and more. Each symbol represents a specific aspect or component of Azure services, such as VPN gateways, firewalls
0 views • 6 slides
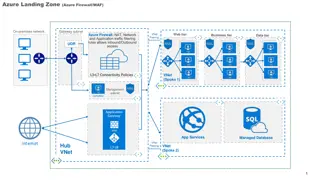
Azure Network Architecture Deployment Overview
An in-depth look at Azure network architectures, including landing zone configurations with Azure Firewall and WAF, deployment to primary Azure regions, hub and spoke models, network virtual appliances (NVAs), VPN tunnels, DMZ setups, and more. This comprehensive guide covers various network compone
3 views • 7 slides
Secure Networking Best Practices for Municipalities
Explore the implementation of secure networking practices for municipalities, including dedicated circuits, VPN connections, VLAN segmentation, and VoIP considerations. Learn about maintaining network integrity and protecting sensitive information in compliance with CJIS policies.
0 views • 9 slides
DIT Demo Remote Access Guidelines for Working from Home
Explore the remote access guidelines for working from home provided by DIT Demo, covering essential aspects such as multi-factor authentication, virtual private network (VPN), virtual desktop infrastructure (VDI), conferencing options, and more. Learn about the necessary steps to access these resour
0 views • 11 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Business Continuity Planning in Times of Crisis
During challenging times like the current Covid-19 pandemic, it's crucial for businesses to develop a comprehensive business continuity plan. This plan should focus on maximizing productivity while minimizing risks to employees, clients, and vendors. Classify your employees into informational, hybri
0 views • 15 slides
What is NordVPN_ Is NordVPN safe and secure_
Share :\n \n \n \nA VPN, or Virtual Private Network, is a technology that creates a secure connection over a less secure network, such as the Internet. It allows users to send and receive data as if their devices were directly connected to a private
0 views • 12 slides
Network Deployment and Monitoring Overview
Explore key updates on network deployment for Pico2 testbed EOSC, including L3VPN deployment status, site connections, VPN management governance, and the importance of monitoring for cloud deployment. Gain insights into collaboration efforts between GEANT and RENATER, addressing challenges and advan
0 views • 7 slides
Free Indian VPN for Tiktok
Access effortlessly with our Free Indian VPN for Tiktok, designed for fast speeds and secure browsing. Ideal for overcoming geo-restrictions and enjoying unrestricted content from India.
0 views • 5 slides
Free Indian VPN for Tiktok
Access effortlessly with our Free Indian VPN for Tiktok, designed for fast speeds and secure browsing. Ideal for overcoming geo-restrictions and enjoying unrestricted content from India.
0 views • 5 slides
MATLAB Remote Access Instructions for Off-Campus and BU Network Users
Access MATLAB remotely using VPN for off-campus and BU network users. Establish a VPN connection, control it via tray icon, and set up X-Win32 for SSH access. Download and install necessary software following step-by-step instructions provided. By following these steps, users can easily access MATLA
0 views • 11 slides
Implementing VPN for Secure Corporate Communication
A Virtual Private Network (VPN) offers a secure method for corporations with multiple sites to transfer data over the Internet while maintaining confidentiality. By encrypting data and using tunneling techniques, VPN software ensures that communications remain private, making it a cost-effective and
0 views • 10 slides
Networking and Distributed Computing Systems Lab Setup Guide
Set up your lab environment for networking and distributed computing systems using Unix, Bash, and Emacs. Learn to access lab machines via SSH, use PuTTY and Terminal for communication, simulate Linux environment on Windows with Cygwin, run different OS on VMware Player, download and install Linux o
0 views • 14 slides
Understanding Noise*: A Verified Secure Channel Protocol Library
Explore Noise*, a library of high-performance secure channel protocol implementations that have been verified for correctness. The Noise protocol examples, such as IKpsk2, showcase key exchange patterns used in applications like WhatsApp and Wireguard VPN. Discover the importance of verified impleme
0 views • 18 slides
Troubleshooting Guide for SSLVPN Connection Issues
Learn how to troubleshoot common SSLVPN connection problems such as difficulties connecting to remote computers, network access device errors, conflicts with other programs, and issues with user privileges or certificates. Find solutions to resolve these issues and ensure a stable VPN connection.
0 views • 19 slides
Free Indian VPN for PUBG
Enhance your experience with our Free Indian VPN for PUBG, providing fast speeds and reliable connections. Perfect for bypassing geo-restrictions and accessing the game seamlessly from India.
0 views • 4 slides
Protect content from VPN requests
Safeguard your website's content by implementing measures to protect content from VPN requests and block. Enhance security and guard against possible abuse or illegal access by implementing sophisticated tools that examine incoming connections. In or
0 views • 4 slides
Emerging Career Paths in Computer Networking Field
The demand for individuals with expertise in computer network management is on the rise due to the increasing use of internet-based applications like e-commerce, e-governance, and VPN. Job titles in this domain include Network Administrator, Network Technician, and Network Security professional. Res
0 views • 23 slides