Unlocking Opportunities Comprehensive Nursing Colleges Email List for Targeted Outreach
In the ever-evolving landscape of healthcare education, staying connected and informed is crucial for institutions aiming to provide quality nursing education. A Nursing Colleges Email List serves as a powerful tool for seamless communication, networking, and targeted outreach. This comprehensive li
5 views • 7 slides
Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Operating Systems
An operating system is a crucial program that manages all other programs on a computer. It handles tasks like input recognition, file management, and device control. There are different types of operating systems such as single-user, single-task systems, multi-user, multi-task systems, real-time ope
6 views • 11 slides
DNC cast list popuplation in as per Ambasankar Commission .
Denotified Communities (DNC) refer to social and educationally Backward groups officially recognized and labelled as such by the Government under the Tamilnadu Backward community.DNC population Count as per the Ambasankar Commission report:Note: The Following are the Communities that are in the Cent
4 views • 5 slides
BC Caste population as per Ambasankar Commission in India
In India, the term \u201cBackward Classes\u201c(BC) refers to socially and educationally Backward groups. In India, they come to OBC at the National level.\nBC population Count as per Ambasankar Commission:\nNote: The Following are the Communities that are in the Central Government list of \u201cOBC
6 views • 5 slides
MBC Caste population as per Ambasankar Commission in India.
MBC in the Indian context typically refers to \u201cMost Backward Classes.\u201d This is a category used in some Indian states to identify communities that are considered socially and educationally Backward.\nMBC population Count as per Ambasankar Commission\nNote: The Following are the Communities
3 views • 5 slides
Malayalis in Forbes Richest List 2024
Forbes released its World's Billionaires List for the year 2024. American business magazine found an unprecedented 2,781 billionaires around the globe for this year\u2019s list with 141 more than in 2023 and 26 more than the previous record, set in 2021. 14 Malayalis made it into the list and their
32 views • 15 slides
The Evolution of Graphical User Interfaces in Computing
Graphical User Interfaces (GUIs) have transformed computing into a more user-friendly and interactive experience, emphasizing the shift from technology-focused to human-centric living. This chapter delves into the various aspects of GUIs, including I/O alternatives, common GUI tasks, programming per
1 views • 32 slides
Understanding Linux User Capabilities and Namespace Management
Linux user namespaces and capabilities play a critical role in managing system security and permissions. Users and groups are assigned unique IDs, and processes are associated with the user's ID. The kernel enforces permission checks based on user IDs and group IDs, allowing root access to bypass ce
0 views • 14 slides
Understanding Heuristic Evaluation in User Interface Design
Heuristic evaluation is an analytical method where experts evaluate interfaces based on usability principles. This evaluation helps in identifying potential design issues that may impact user satisfaction. The process involves a small group of evaluators reviewing the interface against a set of reco
5 views • 12 slides
Understanding Different Types of Operating Systems
An operating system is the crucial program that manages a computer's resources and acts as an interface between the user and the machine. Various types of operating systems exist, including real-time, multi-user vs. single-user, multi-tasking vs. single-tasking, distributed, and embedded systems. Re
1 views • 11 slides
College List Organization Workshop
Learn how to create a college list with this interactive workshop. Explore preferences, research colleges online, and list potential options for a good fit. Engage in reflective activities to tailor your list to your needs.
0 views • 14 slides
Implementing Alert Messages and User Input Handling in Java
This tutorial guides you through creating alert messages, handling user input, defining functions, calling functions from the `onCreate` method, and creating an XML file for user data entry validation in Java. Learn how to display alerts for empty user credentials and process user actions accordingl
1 views • 6 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Domain-Specific Visual Analytics Systems: Exploring Expert User Insights
This presentation delves into domain-specific visual analytics systems focusing on political simulation, wire fraud detection, bridge maintenance, and more. It emphasizes leveraging user expertise for effective system design and evaluation, highlighting the importance of user insights in data analys
0 views • 27 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
User Roles and Responsibilities Overview
The user roles within the application are categorized into Account Manager, Data Steward, and Common Functionality roles. Each role comes with specific responsibilities such as managing user accounts, database management, data stewardship, incident management, and more. Non-privileged roles provide
0 views • 11 slides
Understanding Agile User Stories in Software Development
Agile user stories play a crucial role in software development by providing short descriptions of features desired by customers in a language they understand. This method allows for agile planning, efficient documentation, and effective communication between development teams and clients. Extracting
0 views • 30 slides
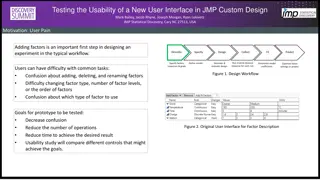
Exploring Usability Testing of New Interface in JMP Custom Design
In this study by Mark Bailey et al. from JMP Statistical Discovery in the USA, the focus lies on testing the usability of a new user interface using JMP Custom Design. The researchers highlight the significance of adding factors in the initial experiment design workflow to enhance user experience. U
0 views • 8 slides
Understanding List Operations in Python
A comprehensive guide to list operations in Python, covering topics such as defining lists, performing functions on lists, indexing, slicing, and more. Learn about the basics of lists, initializing lists, updating elements within a list, deleting list elements, and common list operations like concat
0 views • 26 slides
Guide to Court Management System User Administration
Learn how to effectively manage user profiles, create sub-user accounts for legal assistants, update user information, and create associates' accounts in the Court Management System for the 17th Judicial Circuit Court of Florida. Detailed instructions provided for changing usernames, passwords, and
0 views • 15 slides
Enhancing User Experience Through Data Trails and Metrics
Andrea Thompson, a Sr. User Experience Manager at The Home Depot, highlights the importance of measuring and analyzing user experience metrics to understand and improve customer interactions. By investigating data trails from various touchpoints, such as customer sign-ups, interactions with associat
0 views • 17 slides
Understanding User Identity and Access Tokens in Windows Security
Delve into the intricate world of user identity and access tokens in Windows security. Explore how user identities are represented, the structure of access tokens, and the significance of processes running under different user contexts. Gain insights into advanced Windows security principles and lea
1 views • 13 slides
Understanding User and Group Permissions in Linux Systems
Linux uses user and group permissions to control access to files, directories, and peripherals. Users are managed for security purposes by limiting access, with the root user having full system access. Grouping users into groups with specific access grants can enhance security. Each file is owned by
0 views • 23 slides
Understanding Lists and List Operations in Python
This content provides valuable insights into lists in Python, covering topics such as list creation, querying, modification, loop examples, the range function, list operations, and list querying expressions. It explains the concepts with examples, images, and practical demonstrations, making it easi
0 views • 32 slides
Understanding Python Lists Operations
Python lists are versatile data structures that allow for efficient creation, querying, modification, insertion, removal, replacement, and rearrangement of elements. This comprehensive guide covers essential list operations such as extracting parts of a list, finding elements, and altering list cont
0 views • 18 slides
Understanding ADT List Operations and Implementations
In this detailed content, you will learn about the specifications and operations involved in working with an ADT list. The structure, domain operations, and user instructions are clearly outlined for efficient implementation. The content also delves into the representation and implementation aspects
0 views • 30 slides
Understanding List Comprehensions in Haskell Programming
In Haskell programming, list comprehensions provide a concise way to construct new lists from existing ones. By following comprehension notation similar to mathematics, you can generate sets and lists based on specified criteria. The order of generators and the use of dependent generators can signif
0 views • 22 slides
Understanding the Speaker's List in Committees
A Speaker's List is a crucial tool in committee proceedings, outlining the order of delegates set to deliver formal speeches. Delegates can request to speak by raising their placards and must be acknowledged by the Chair to open or close the list for agenda setting or voting. Once enough speeches ar
0 views • 7 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides
Introduction to Graphical User Interfaces (GUIs) in Python for Geographical Information Analysis
This content provides insights into creating Graphical User Interfaces (GUIs) in Python for Geographical Information Analysis. It covers the basics of GUI development using TkInter and event-based programming with a focus on user experience design and functionality. The lecture emphasizes the import
0 views • 45 slides
Importance of Human-Computer Interaction (HCI) in User Interface Design
Human-Computer Interaction (HCI) is a crucial discipline focusing on creating interactive computing systems that are user-friendly and efficient. This involves designing, evaluating, and implementing systems that cater to users' needs, ultimately improving user satisfaction and productivity. The fie
0 views • 39 slides
User Interface Design Principles in Human-Computer Interaction
User interface design principles are crucial in Human-Computer Interaction. This content highlights key principles such as aesthetics, anticipation, autonomy, and color consideration for users with color blindness. It emphasizes the importance of user testing, user autonomy, and providing essential
0 views • 24 slides
Understanding Interaction Design in Human-Computer Interaction
Interaction design focuses on creating interactive products that are easy, effective, and enjoyable to use. It aims to reduce negative user experiences while enhancing positive ones. Designing interactive products requires understanding user activities, interfaces, and device arrangements to support
0 views • 11 slides
IEEE 802.11-20/1317r1 EHT-SIG Proposal Discussion
The document discusses EHT-SIG for single-user and sounding NDP in IEEE 802.11-20/1317r1, focusing on overflow bits, user fields, CRC, and tail formats. It covers the format details, subfields, and overhead compared to HE sounding, proposing specific bit allocations for different elements. The EHT-S
0 views • 16 slides
Difference Between Combo Box and List Box in VB 6.0
Combo boxes in VB 6.0 combine features of text boxes and list boxes, providing drop-down functionality for selecting values. There are three styles of combo boxes, with the Drop-Down List style being most similar to a ListBox. Combo boxes have limitations in terms of user interactions compared to Li
0 views • 6 slides
Administrator Deletes User - User Management System Storyboard
An administrator navigates through a user list, selects a user for deletion, confirms the action, and successfully removes the user from the system. The process involves interacting with user details, confirming the deletion, and updating the user list accordingly in a structured manner.
0 views • 4 slides
Enhancing Library Services with the New A-to-Z List Interface
Explore the innovative features and customization options of the new A-to-Z list interface for managing academic library resources. Learn about setting up and configuring the interface post its release in June 2017, indexing procedures, documentation, and contact information for support. Enhance use
0 views • 7 slides
User Interface vs User Experience: Understanding the Essentials
Exploring the distinctions between User Interface (UI) and User Experience (UX) in human-computer interaction design. UI focuses on the space of interaction between humans and machines, while UX encompasses users' behavior, attitude, and emotions towards a product or service. The goal is to create i
0 views • 63 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides