Algorithm Analysis
Algorithm analysis involves evaluating the efficiency of algorithms through measures such as time and memory complexity. This analysis helps in comparing different algorithms, understanding how time scales with input size, and predicting performance as input size approaches infinity. Scaling analysi
1 views • 30 slides
Market Analysis (Project Formulation)
This detailed guide covers essential aspects of market analysis and project formulation in entrepreneurship, including feasibility analysis, techno-economic analysis, market demand analysis, steps in market analysis, and factors to consider for market demand analysis. Explore how to assess market de
2 views • 30 slides
Static Analysis Techniques Overview
Explore static analysis techniques such as syntactic analysis, dataflow analysis, and model checking. Understand the concept of basic blocks in static analysis and their boundaries. Dive into the opportunities provided by static analysis in summarizing program behavior without executing it.
9 views • 27 slides
Bioinformatics for Genomics Lecture Series 2022 Overview
Delve into the Genetics and Genome Evolution (GGE) Bioinformatics for Genomics Lecture Series 2022 presented by Sven Bergmann. Explore topics like RNA-seq, differential expression analysis, clustering, gene expression data analysis, epigenetic data analysis, integrative analysis, CHIP-seq, HiC data,
0 views • 36 slides
Comprehensive Cost Management Training Objectives
This detailed training agenda outlines a comprehensive program focusing on cost management, including an overview of cost management importance, cost object definition, cost assignment, analysis, and reporting. It covers topics such as understanding cost models, cost allocations, various types of an
2 views • 41 slides
Understanding TCP/IP Networking Fundamentals
Explore the basics of TCP/IP networking, including protocols like IP, UDP, RTP, and more. Learn about the structure of the Internet, the role of routers, OSI network model, TCP/IP network model, and packet encapsulation in data transmission. Gain insights into the layers of the OSI model and the TCP
1 views • 36 slides
Qualitative Data Analysis Techniques in Research
The purpose of data analysis is to organize, structure, and derive meaning from research data. Qualitative analysis involves insight, creativity, and hard work. Researchers play a crucial role as instruments for data analysis, exploring and reflecting on interview discussions. Steps include transcri
1 views • 27 slides
Enhancing Eduroam Security with New Standards and Practices
Explore the foundations of eduroam and the challenges with RADIUS, along with recommendations for improving security. Learn why moving away from RADIUS/UDP and adopting shared secrets of 16 characters is essential. Discover the issues with transitioning from UDP to RADIUS/TLS, and the new standards
0 views • 12 slides
Understanding Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
1 views • 51 slides
Understanding TCP and UDP in Computer Network Interoperability
The Transport Layer in computer networks facilitates logical communication between application processes on different hosts. Two key transport protocols, UDP and TCP, provide distinct services - UDP offers unreliable and unordered delivery, while TCP ensures reliable and ordered delivery with featur
1 views • 9 slides
Understanding QUIC: A Quick Overview by Geoff Huston
QUIC is a modern transport protocol that improves upon TCP by offering features like improved multi-stream capabilities, encryption, and congestion control. It is built on top of UDP and enables faster, more secure data transfers. QUIC is address-agile, which helps it navigate challenges posed by NA
1 views • 22 slides
Understanding Socket Programming and Application Interface
Socket programming involves creating interfaces for applications to communicate over a network. The application programming interface (API) defines how applications interact with the network through sockets, which serve as the point of connection between an application and the network. Different soc
0 views • 16 slides
Understanding User Datagram Protocol (UDP) in Unix and Network Programming
Explore the fundamentals of User Datagram Protocol (UDP) in Unix and Network Programming, covering topics such as UDP client/server programs, network layers, transport layer services, UDP packet format, and socket programming. Learn about the characteristics and usage of UDP, including its simple me
2 views • 28 slides
Overview of Socket Programming in Computer Networks
This information presents a detailed overview of socket programming, covering topics such as Socket API, BSD Socket API, types of sockets (TCP vs UDP), and the basic functions related to I/O multiplexing. It explains the concept of sockets, their various types, their similarities, and differences, a
3 views • 53 slides
Data Analysis and Passage Analysis Project Proposal
This project proposal by Anthony Yang focuses on developing a Java program for data analysis and passage analysis. The motivation behind the project is to gain more knowledge in computer science and statistics-related topics while utilizing technology to extract useful insights from data. The propos
0 views • 8 slides
Efficiency Methodological Approaches in Prisons Service Quality Study
Exploring efficiency methodologies in analyzing prisons service quality, this study focuses on parametric and non-parametric approaches such as Data Envelopment Analysis (DEA) and Stochastic Frontier Analysis (SFA). It delves into benchmarking techniques, productivity analysis, and the implications
0 views • 21 slides
Understanding UDP and Reliable Communication
Explore the differences between UDP and TCP protocols, the need for UDP in certain applications, the basic UDP Socket API, and the concept of adding reliability to UDP communication through flow control and error management techniques.
0 views • 16 slides
Understanding Reliable Transport and User Datagram Protocol in Computer Networking
This content covers the concepts of reliable transport in computer networking, including the reliable transport layer protocols like TCP, UDP, and the basics of Domain Name Service (DNS). It explains the layers of the Internet, the functions of each layer, and the differences between TCP and UDP pro
0 views • 28 slides
Understanding Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Understanding Communication Networks: Transport and Protocols
Explore the intricacies of communication networks focusing on transport services, protocol stack, UDP, TCP, error control, congestion control, and more. Learn about interworking, routing, DHCP, NAT, connection setup, and error recovery mechanisms. Dive into TCP and UDP headers, handshake processes,
0 views • 46 slides
Understanding Socket Programming in Java
Exploring the essentials of socket programming with Java, covering topics such as network sockets, socket lifecycle, communication protocols (UDP and TCP), and considerations for client/server applications using UDP and TCP. TCP is highlighted as suitable for services like remote login and file tran
0 views • 18 slides
Understanding L3 and VXLAN Networking for OpenStack Deployments
Today, many OpenStack deployments rely on L2 networks, but there are limitations with this approach, including scalability issues and wasted capacity. The solution lies in transitioning to L3 networking designs, which offer benefits such as increased availability, simplified feature sets, and better
0 views • 28 slides
Understanding IP Addressing and Routing in Networking
Delve into the fundamentals of IP addressing, CIDR, subnetting, and network layer protocols like TCP and UDP. Explore the intricacies of Internet architecture, NAT, IPv6, and forwarding techniques. Grasp the essentials of IP datagram format, path-selection algorithms, SDN, and more for a comprehensi
0 views • 22 slides
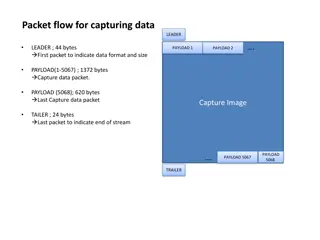
Wireshark Data Capture and UDP Analysis
Capturing data flow through packets in Wireshark reveals a series of fragmented payloads, starting with a leader packet of 44 bytes and ending with a trailer of 24 bytes. The UDP data payloads range from 44 to 1372 bytes, with specific lengths for different payloads and packets. Analysis includes UD
0 views • 4 slides
Overview of Front-End DAQ for TREND
Cutting-edge Front-End DAQ system featuring components like the Texas Instruments ADS6424 ADC, ALTERA 5CEFA4F23C6N FPGA, Ring Buffer for data management, u-blox Precision Timing GPS module for accurate time stamping, and General Slow Control Architecture for monitoring. The system utilizes Ethernet
0 views • 15 slides
Optimizing Real-Time Data Delivery with UDP Offload Engines in LambdaGrids
Real-time interactive scientific visualization and high-definition video conferencing in large-scale visualization environments like LambdaGrids require high-throughput, low latency, and low jitter data delivery. This article discusses the motivation behind using UDP-based transport protocols and th
0 views • 12 slides
Introduction to IBM SPSS Modeler: Association Analysis and Market Basket Analysis
Understanding Association Analysis in IBM SPSS Modeler 14.2, also known as Affinity Analysis or Market Basket Analysis. Learn about identifying patterns in data without specific targets, exploring data mining in an unsupervised manner. Discover the uses of Association Rules, including insights into
0 views • 18 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Introduction to Static Analysis in C.K. Chen's Presentation
Explore the fundamentals of static analysis in C.K. Chen's presentation, covering topics such as common tools in Linux, disassembly, reverse assembly, and tips for static analysis. Discover how static analysis can be used to analyze malware without execution and learn about the information that can
0 views • 54 slides
Simplified Router Implementation for CSC458/2209 Course
You will be designing a simplified router for CSC458/2209 course with specific functionalities such as handling Ethernet frames, ICMP messages, ARP requests, IP packets, and more. The router will operate in an emulated network environment using Mininet and will need to route traffic between a client
0 views • 16 slides
Industrial, Microbiological & Biochemical Analysis - Course Overview by Dr. Anant B. Kanagare
Dr. Anant B. Kanagare, an Assistant Professor at Deogiri College, Aurangabad, presents a comprehensive course on Industrial, Microbiological, and Biochemical Analysis (Course Code ACH502). The course covers topics such as Industrial Analysis, Microbiological Analysis, and Biochemical Analysis. Dr. K
0 views • 16 slides
An In-Depth Look at QUIC Protocol
QUIC, developed by Geoff Huston, Joao Damas, and APNIC Labs, is a modern transport-level protocol that enhances network service capabilities by leveraging UDP for data transmission. It incorporates features like HTTP/3, encryption, session control, and congestion control while minimizing network exp
0 views • 24 slides
Benefits of Probabilistic Static Analysis for Improving Program Analysis
Probabilistic static analysis offers a novel approach to enhancing the accuracy and usefulness of program analysis results. By introducing probabilistic treatment in static analysis, uncertainties and imprecisions can be addressed, leading to more interpretable and actionable outcomes. This methodol
0 views • 11 slides
Speak: Simple VoIP Application Project 2
Develop a basic two-person VoIP application with speech detection capabilities using TCP and UDP protocols. The project involves evaluating speech quality, simulating latency, implementing speech detection based on energy levels, and handling packet loss. Explore various architectural possibilities,
0 views • 8 slides
Understanding Reliable Communication over UDP: A Comprehensive Overview
Reliable communication over UDP is crucial for applications that prioritize performance over 100% reliability, such as VoIP, video streaming, and DNS servers. This involves adding flow control and error control mechanisms to handle transmission errors and buffer overflow. By making UDP more reliable
0 views • 16 slides
Understanding Network Protocols: TCP, UDP, DHCP, DNS
Explore the fundamentals of key network protocols including TCP, UDP, DHCP, and DNS. Learn about IPv4 and IPv6 addresses, IP address classes, and the roles of these protocols in the TCP/IP suite. Understand the differences between TCP and UDP in terms of connection setup and reliability. Discover th
0 views • 13 slides
Understanding IP Addressing, Ports, and Hostnames in Networking
Exploring methods to obtain own IP address, well-known ports, hostname resolution, and mapping hostnames to IP addresses in networking. Discover the significance of ports, addressing projects, and DNS servers in establishing communication protocols like UDP and TCP.
0 views • 8 slides
Understanding Resolverless DNS and its Implications
Resolverless DNS, as discussed by Geoff Huston, delves into the architecture and issues of the DNS system. It explores the impact of resolver caches on speed and predictability of resolution, the potential for filtering DNS content, and the significance of metadata collection. The evolution of DNS s
0 views • 30 slides
Comprehensive Guide to Network Programming in Python
This detailed guide covers a range of topics including network programming in Python, inter-process communication using TCP and UDP, TCP and UDP servers and clients, testing methods, remote procedure calls, and remote objects. Each section provides insights, explanations, and practical examples to h
0 views • 21 slides
Insights into DNS Flag Day 2020 Trends and Analysis
Delve into the DNS Flag Day 2020 observations and trends, including changes in buffer sizes, UDP fragmentation, and the selection of threshold points for DNS to switch to TCP. Explore the impact of varying buffer sizes on users and the DNS system, highlighting shifts in usage percentages and implica
0 views • 29 slides