Wireshark Data Capture and UDP Analysis
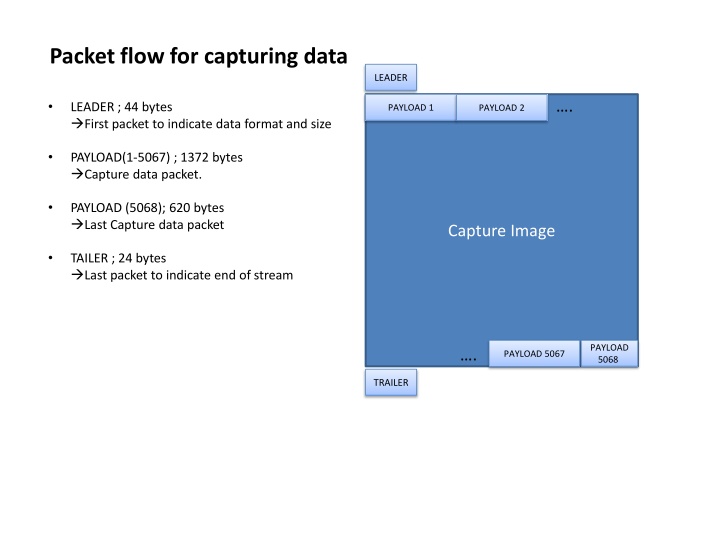
Capturing data flow through packets in Wireshark reveals a series of fragmented payloads, starting with a leader packet of 44 bytes and ending with a trailer of 24 bytes. The UDP data payloads range from 44 to 1372 bytes, with specific lengths for different payloads and packets. Analysis includes UDP and IPS status updates, CPU halt details, and recv() responses. Tracking UDP and IP status changes during packet sequence aids in understanding data capture nuances in network monitoring.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Packet flow for capturing data LEADER . LEADER ; 44 bytes First packet to indicate data format and size PAYLOAD 1 PAYLOAD 2 PAYLOAD(1-5067) ; 1372 bytes Capture data packet. PAYLOAD (5068); 620 bytes Last Capture data packet Capture Image TAILER ; 24 bytes Last packet to indicate end of stream PAYLOAD 5068 . PAYLOAD 5067 TRAILER
The beginning of capture in wireshark LEADER ; Length 86 Recv()`s return value is 44. This is expected. UDP data payload = 44 bytes PAYLOAD 1 ; Length 1414 Resv()`s return value is 1372. This is expected. UDP data payload = 1372 bytes A series of Capture data (fragmented) PAYLOAD 1 ; Length 1414 Resv()`s return value is 1372. This is expected. UDP data payload = 1372 bytes
The end of capture in wireshark A series of Capture data (fragmented) PAYLOAD 1 ; Length 1414 Recv()`s return value is 1372. This is expected. UDP data payload = 1372 bytes PAYLOAD 1 ; Length 1414 Recv()`s return value is 1372. This is expected. UDP data payload = 1372 bytes PAYLOAD 1 ; Length 662 Recv()`s return value is 620. This is expected. UDP data payload = 620bytes TAILER ; Length 66 Recv() ruturns nothing (blocking) If socket is configured as non-blocking call, Recv() always returns 0. UDP data payload = 24bytes Please note windows app using winsock can capture all of data completely.
udps and ips status during the later packets Comment packet sequence id udp packet size in bytes 5066 1372 5067 1372 5068 620 5069 24 Lost CPU halt 00008AB1 00000000 00000007 00000000 00000000 00000000 00000000 0000000F 00000000 response of recv() in bytes udps status after UINT32 RcvTotal; UINT32 RcvShort; UINT32 RcvBadLen; UINT32 RcvBadSum; UINT32 RcvFull; UINT32 RcvNoPort; UINT32 RcvNoPortB; UINT32 SndTotal; UINT32 SndNoPacket; 1372 recv() 00008AB1 00000000 00000007 00000000 00000000 00000000 00000000 0000000F 00000000 1372 recv() 00008AB1 00000000 00000007 00000000 00000000 00000000 00000000 0000000F 00000000 620 recv() 00008AB1 00000000 00000007 00000000 00000000 00000000 00000000 0000000F 00000000 no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets Blocking ips status after UINT32 Total; /* total packets received */ UINT32 Odropped; /* lost packets due to nobufs, etc. */ UINT32 Badsum; /* checksum bad */ UINT32 Badhlen; /* ip header length < data size */ UINT32 Badlen; /* ip length < ip header length */ UINT32 Badoptions; /* error in option processing */ UINT32 Badvers; /* ip version != 4 */ UINT32 Forward; /* packets forwarded */ UINT32 Noproto; /* unknown or unsupported protocol */ UINT32 Delivered; /* datagrams delivered to upper level */ UINT32 Cantforward; /* packets rcvd for unreachable dest */ UINT32 CantforwardBA; /* packets rcvd with illegal addressing */ UINT32 Expired; /* Packets not forwards becaused expired */ UINT32 Redirectsent; /* packets forwarded on same net */ UINT32 Localout; /* total ip packets generated here */ UINT32 Localnoroute; /* Local packets discarded due to no route */ UINT32 Reassembled; /* total packets reassembled ok */ UINT32 Fragments; /* fragments received */ UINT32 Fragdropped; /* frags dropped (dups, out of space) */ UINT32 Fragtimeout; /* fragments timed out */ UINT32 Fragmented; /* datagrams successfully fragmented */ UINT32 Ofragments; /* output fragments created */ UINT32 Cantfrag; /* don't fragment flag was set, etc. */ UINT32 CacheHit; /* Route cache hit */ UINT32 CacheMiss; /* Route cache miss */ UINT32 Filtered; /* packets filtered by firewall */ recv() 00008AB1 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00008AB1 00000000 00000000 00000000 00000000 0000000F 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000E 00000001 00000000 recv() 00008AB1 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00008AB1 00000000 00000000 00000000 00000000 0000000F 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000E 00000001 00000000 recv() 00008AB1 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00008AB1 00000000 00000000 00000000 00000000 0000000F 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000E 00000001 00000000 CPU halt 00008AB1 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00008AB1 00000000 00000000 00000000 00000000 0000000F 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000E 00000001 00000000 no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets no change during the packets Blocking