TSPLUS Advanced Security
Most organizations assume that hackers target them for the value of their information. However, cyber criminals often target systems for their processing power. TSplus Advanced Security provides robust protection against remote desktop attacks.
8 views • 4 slides
Cybersecurity Threats and Facebook Security
In today's digital landscape, cybersecurity threats are ever-present, ranging from phishing to ransomware. This presentation by Paul Haithcock sheds light on protecting networks and data. It also emphasizes the importance of securing Facebook accounts amidst the prevalence of cybercriminal activitie
3 views • 15 slides
Cybersecurity Risk Management in K-12 Education: Challenges and Strategies
Facing a surge in cyberattacks, K-12 schools struggle with limited funds, expertise, and staff for cybersecurity. This leads to vulnerabilities that make them prime targets for hackers. Lack of dedicated cybersecurity resources and training exacerbates the risks, highlighting the urgent need for com
2 views • 47 slides
Comprehensive Digital Risk Assessment Guide for Businesses
Conducting a digital risk assessment is vital for securing your business against threats like viruses, malware, hackers, and human errors. This guide outlines key areas to focus on, such as identifying critical assets, assessing potential impacts of breaches, prioritizing threats, utilizing tools li
3 views • 4 slides
security service solutions
Ingenuity Security Solutions is one of the best security firms in Maryland. Our security services are flexible and tailored to your needs, and we focus on using new technologies and methods. Our skilled experts will use everything from video systems to access control and hackers to make sure that yo
1 views • 1 slides
security solutions company in maryland
Ingenuity Security Solutions is one of the best security firms in Maryland. Our security services are flexible and tailored to your needs, and we focus on using new technologies and methods. Our skilled experts will use everything from video systems to access control and hackers to make sure that yo
1 views • 1 slides
Cyber Crime: Risks and Prevention Measures
Cyber crime, including hacking, phishing, and pharming, poses a significant threat in today's digital world. Learn about the types of hackers and how to tackle phishing and pharming attacks effectively. By following security measures such as avoiding sharing sensitive information and updating anti-p
4 views • 18 slides
Practice Reading and Paraphrasing with HACKERS TOEIC
Enhance your English skills by practicing reading comprehension and paraphrasing exercises using the HACKERS TOEIC materials provided. Test your understanding of letters, emails, and vocabulary while improving your language proficiency. Sharpen your ability to interpret and respond to written conten
0 views • 21 slides
Internet Safety Tips: Protect Yourself Online
Internet safety is crucial in safeguarding your online activities from threats like malicious software, hackers, and data leaks. Learn how to protect yourself against these risks, prevent password breaches, save passwords securely, back up your data, and be cautious about what information you share
1 views • 15 slides
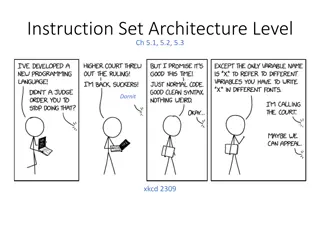
Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
3 views • 13 slides
Information Security Basics
Information security involves protecting information and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes safeguarding assets from various threats such as hackers, malware, natural disasters, and human errors. The chapter covers topics like u
0 views • 27 slides
ethical hacker learning
Ethics hackers use a range of specialized tools to test and analyze systems. These include software for scanning networks, testing web applications, and sniffing out vulnerabilities. Some popular tools you might encounter include Nmap, Metasploit, an
1 views • 1 slides
Fundamentals of Ethical Hacking
Ethical hackers are often called \u201cwhite hats\u201d in contrast to \u201cblack hats,\u201d who are the malicious hackers. White hats use their skills to improve security and protect information, while black hats exploit vulnerabilities for illega
0 views • 1 slides
Ethical Hacking Essential Knowledge
Ethical hackers use the same tools and techniques as cybercriminals but with permission and for good reasons.\n\nThink of it as a friendly security check-up. Just like you might get a health check-up to catch any issues early, ethical hacking helps o
0 views • 2 slides
Insights on Interactive Narrative and New Media
Discussion on the evolution of interactive narrative and new media, highlighting Janet Murray's work, the complementary skills of hackers and bards, the concept of the Holodeck as a universal fantasy machine, Janeway's Holonovel, and the early reactions to new media technologies. Topics covered incl
0 views • 22 slides
Computer Viruses and Their Types
Computer viruses, created by malicious hackers, are programs that can replicate themselves and harm computer systems by damaging data files. They can cause various issues like slow response, crashes, and distorted graphics. Common virus types include time bombs, logical bombs, worms, and boot sector
0 views • 19 slides
Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Importance of Updating Devices for Cyber Security
Keeping your devices up to date is crucial for protecting your important data from cyber criminals. Regular updates fix vulnerabilities in operating systems and apps, making it harder for hackers to breach your device. Remember to update not only your device's software but also third-party apps, web
0 views • 7 slides
Ethical Hacking_ Principles, Practices, and Significance
Ethical hacking involves authorized attempts to gain unauthorized access to a system, application, or data. Also known as penetration testing or white-hat hacking, ethical hacking uses the same methods as malicious hackers to find security weaknesses
0 views • 8 slides
Protecting Your Business from Cybersecurity Threats
In today's digital landscape, the risk of cyber attacks is higher than ever. Hackers offer malicious services for a low cost, increasing the threat of ransomware, phishing, and spam attacks. With statistics showing the rise in ransomware incidents, it's crucial for organizations to prioritize securi
0 views • 24 slides
Addressing Software Security, Economic, and Liability Issues
In the realm of software security, economic considerations often lead to negligence in addressing vulnerabilities, resulting in billions of dollars wasted annually due to exploits by hackers. The focus is on the prevalence of vulnerabilities, limited sources of security issues, and the need for a sh
0 views • 37 slides
Java Data Types and Variable Declaration
Dive into the world of Java data types and variable declaration with this comprehensive guide. Learn about primitive data types, declaring variables, integer types, floating-point data types, character data type, and boolean data type. Master the art of assigning names and data types to efficiently
0 views • 31 slides
Importance of Internet Security and Setting Up an Office Proxy Server
Learn how to enhance internet security by setting up an office proxy server to limit staff web surfing. Understand the risks associated with system flaws in Windows, Mac, browsers like Internet Explorer, Firefox, Chrome, and the immediate threat of Zero-Hour Attacks by hackers.
0 views • 28 slides
Ethical Hacking: Understanding the Different Types of Hackers
Ethical hacking, presented by Mr. Bhushan S. Kulkarni, involves identifying and exploiting vulnerabilities in computer systems for security improvement. This article delves into the definition of hacking, the roles of hackers (Black Hat, White Hat, Grey Hat), and their distinct characteristics and m
0 views • 7 slides
Safeguarding Your Online Presence: A Guide to Cybersecurity Awareness
Understand the importance of managing your digital footprint, learn about safe online practices, discover the impact of social media on future opportunities, and explore ways to protect yourself from cyber threats. From email safety to types of hackers, empower yourself with essential knowledge for
0 views • 8 slides
Inside the Mind of Hackers: Behavior, Motivation, and Notable Cases
Explore the intriguing world of hackers, delving into their behavior, motivations, and infamous cases such as Kevin Mitnick's social engineering hacks and Adrian Lamo's unique approach to vulnerability disclosures. Discover how figures like Stephen Wozniak and Loyd Blankenship transitioned from hack
0 views • 59 slides
Hacking: Types, Hackers, and Ethics
Hacking is a complex area covering various topics and activities, originating from MIT in 1960. It involves finding vulnerabilities in computer systems and networks for unauthorized access, potentially harming systems or stealing information. Ethical hacking serves the purpose of identifying and fix
0 views • 11 slides
Essential Tips for Computer Security
Protecting your computer is crucial in today's digital world. Follow these steps to enhance your computer's security: 1. Utilize a firewall to block hackers. 2. Install and update anti-malware software. 3. Create strong, unique passwords. By implementing these measures, you can safeguard your system
0 views • 4 slides
Data Types, Expressions, and Operators in Java
This resource provides information on data types, expressions, and operators in Java. It covers topics such as data types (int, double, String, boolean), operator precedence, and practice problems to work on expressions and types. The content includes announcements, reminders, a recap of data types,
0 views • 20 slides
Haskell Types, Classes, Functions, and Polymorphism
In Haskell, types are collections of related values, ensuring type safety through compile-time type inference. Type errors occur when functions are applied to arguments of the wrong type. Annotations help define types, and Haskell offers basic types like Bool, Char, String, Int, Integer, Float, and
0 views • 30 slides
Types and Classes in Haskell Programming
Types in Haskell are names for collections of related values, allowing for safer and faster programs by catching errors at compile time. Haskell supports basic types like Bool, Char, String, Int, Integer, and Float, as well as list and tuple types. Type errors occur when functions are applied to arg
0 views • 27 slides
Introduction to Python Data Types, Operators, and Expressions
Understanding data types, expressions, and operators is fundamental in Python programming. Learn about Python's principal built-in types such as numerics, sequences, mappings, and classes. Explore numeric types, strings, and their operations like concatenation, escape sequences, and conversions betw
1 views • 20 slides
Threats and Attacks in Information Systems
Threats and attacks pose risks to information systems through vulnerabilities that can be exploited, leading to data loss, system unavailability, and compromised security. Four primary classes of threats include unstructured threats from inexperienced individuals, structured threats from skilled hac
0 views • 21 slides
Legal Issues in Data Breaches and Confidentiality Violations
The content covers various scenarios related to breach of confidence, liability of businesses in safeguarding data, and legal causes of action in case of data breaches. It discusses real-life analogies and legal principles concerning the mishandling of confidential information, including a case stud
1 views • 23 slides
Different Types of Malware and How to Protect Your Computer
Malware can pose serious threats to your computer's security. Learn about various types of malware such as spyware, adware, trojans, ransomware, and how to prevent malware attacks by installing antivirus software and practicing safe online browsing habits. Stay informed and keep your data safe from
0 views • 7 slides
IT Security and Control
Systems are vulnerable to various threats like viruses, hackers, and cyberterrorism. Security and control practices are crucial to mitigate risks and protect valuable information assets from potential harm and legal liabilities. This chapter discusses contemporary security challenges and vulnerabili
0 views • 38 slides
Introduction to Computer Science
This material covers essential aspects of computer science security and privacy, including cybercrime, cybersecurity, malware, social engineering, and methods for protection against cyberattacks. Explore common IT security concerns, methods of attack, malware types, wireless device security, EHR con
0 views • 33 slides
Generics
Generics in Java allow for compile-time error detection by enabling the definition of classes, interfaces, or methods with generic types. This feature replaces generic types with concrete types, such as with the ArrayList class in Java. Discover motivations, benefits, defining generic classes, metho
0 views • 32 slides
Ethical Hacking and Penetration Testing
Let's explore the mindset of penetration testers and ethical hackers, emphasizing the importance of balancing creativity with methodical approaches. Dive into information security (InfoSec) and its critical objectives, such as ensuring confidentiality, integrity, authenticity, availability, and reli
0 views • 70 slides
New Security Rates Deliver Additional Protections
Discover how new security rates offer improved protections, addressing various threats like hackers, malware, and human error. Learn about initiatives, compliance with NIST, and identity/access management milestones to enhance security programs
0 views • 17 slides