Protecting Your Business from Cybersecurity Threats
In today's digital landscape, the risk of cyber attacks is higher than ever. Hackers offer malicious services for a low cost, increasing the threat of ransomware, phishing, and spam attacks. With statistics showing the rise in ransomware incidents, it's crucial for organizations to prioritize security measures like top-rated antivirus software, firewall installation, enforcing strict password policies, and more. Collaborating to find a balance between IT operational efficiency and security is key to safeguarding your business against potential threats.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
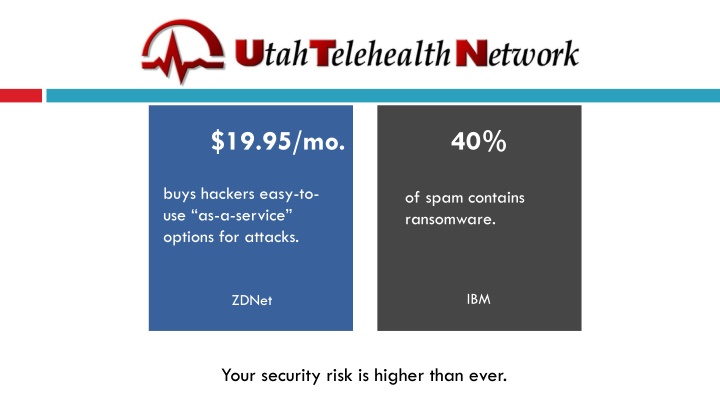
$19.95/mo. 40% buys hackers easy-to- use as-a-service options for attacks. of spam contains ransomware. IBM ZDNet Your security risk is higher than ever.
2016 ransomware attacks were up 16% 16% over 2015. Verizon 2016 DBIR
30% of recipients open phishing messages. 12% click on attachments. Verizon 2016 DBIR
You cant afford to be wrong on this one. 1 in 2 70% $1B USD executives experience a ransomware attack in ransom paid in 2016 of businesses hit pay the ransom IBM IBM FBI estimate
Feedback from a survey of 100 CIO/CSOs IT wants things to work smoothly, while security wants security. At the endpoint, they have to work together to maintain both.
https://www.youtube.com/watch?v=dHtIGp0DP cA&feature=youtu.be
10 Security tips Install top rated antivirus software
Restrict administrator rights
Install and update a firewall
Implement patches and software on popular software
Enforce strict password policies
Top 25 most common passwords 123456 123456789 qwerty 12345678 111111 1234567890 1234567 password 123123 987654321 qwertyuiop mynoob 123321 666666 18atcskd2w 7777777 1q2w3e4r 654321 555555 3rjs1la7qe google 1q2w3e4r5t 123qwe zxcvbnm 1q2w3e
Secure your browsers
Train and recruit users.
Our defense-in-depth solutions Application Control & Privilege Management Patch & Vulnerability Management Secure Program Management Endpoint Security Marry security capabilities with workflows and asset management processes to complete a secure lifecycle. Patch and secure the OSes and 3rd-party apps that you can. Prevent all other apps from running while practicing the principles of least privilege. Add advanced anti- malware and AV capabilities, device control, and global policy for all devices. Asset management Service management Secure configuration management Patch management Vulnerability management Application control Privilege management Device control Anti-malware Threat alerting
The first 5 controls CIS, US-CERT, ASD, and other authorities prioritize these five elements of cyber hygiene to significantly reduce security threats. I n v e n t o r y o f a u t h o r i z e d a n d u n a u t h o r i z e d d e v i c e s I n v e n t o r y o f a u t h o r i z e d a n d u n a u t h o r i z e d s o f t w a r e S e c u r e c o n f i g u r a t i o n C o n t r o l l e d u s e o f a d m i n i s t r a t i o n p r i v i l e g e s C o n t i n u o u s v u l n e r a b i l i t y a s s e s s m e n t a n d r e m e d i a t i o n
Department of Homeland Security/FBI Cybersecurity Briefing December 30, 2016 22 Although in the context of nation-state cyber hacking, in this nationwide public (no clearance required) call, the following techniques were recommended to improve cybersecurity prophylaxis Data Backups Risk Analysis and remediation Staff Training Vulnerability Scanning & Patching Application Whitelisting Incident Response Business Continuity Planning Penetration Testing