Understanding IDS/IPS: Enhancing Security with SecurityGen's Advanced Solutions
In the realm of cybersecurity, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play pivotal roles in safeguarding networks against evolving threats. SecurityGen's IDS IPS solutions are designed to monitor network traffic, detect suspicious activities, and prevent potential i
4 views • 1 slides
KILL NET SWITCH
Discover how to tell if your WiFi is hacked. Look out for unexplained activity, strange device connections, and unexpected slowdowns. Stay proactive about WiFi security and safeguard your network against intrusion.\n
0 views • 2 slides
Hands-On Training with P4 and Hardware Switches at University of South Carolina
The University of South Carolina offers hands-on training using hardware switches in a cloud system. The system provides remote-access capability to lab equipment for virtual labs on P4, routing, high-speed networks, and cybersecurity. Open-source libraries consist of various activities and experime
0 views • 11 slides
Overview of UTSA's IS-6353 Incident Response Course
Introduction to the IS-6353 Incident Response course at UTSA covering topics such as course administration, information assurance, incident response, intrusion detection, and more. The course includes details on the schedule, grading criteria, required textbooks, and notable SQL injection breaches i
5 views • 47 slides
Advancements in Chemical Mechanisms for Air Quality Management
Daniel Jacob and team have been enhancing chemical mechanisms in the GEOS-Chem model to support US air quality management. Ongoing work includes developing new mechanisms for aromatic VOCs, tropospheric halogens, mercury redox, adaptive mechanism reduction, machine learning applications, and unifica
0 views • 19 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Semantics-Aware Intrusion Detection for Industrial Control Systems by Mer Yksel
Mer Yksel, a PhD candidate at Eindhoven University of Technology, specializes in intrusion detection and data analytics with a focus on industrial control systems. His research covers targeted attacks, threat modeling, protection of ICS networks, and innovative anomaly-based approaches for cybersecu
0 views • 31 slides
Yale Intrusion Alarm System Overview
Yale, a global leader in security solutions, offers the Yale Intrusion Alarm system designed to secure homes and personal belongings. This system features the HSA-6403-PS and HSA-6404-GSM panels with various security elements like sensors, sirens, keypad, and more. Users can easily program and test
0 views • 24 slides
Understanding Weak Signal Propagation in Radio Waves
This informative content delves into weak signal propagation and its various aspects related to electromagnetic waves, particularly in the context of radio communication. It covers topics such as radio waves, radio horizon, knife-edge diffraction, tropospheric scatter mode, auroral reflection, and m
1 views • 37 slides
Understanding Tropospheric Delays in Geodetic Techniques
Explore the fundamentals of troposphere delays in geodetic measurements, including refractivity, modeling techniques, and impact on positioning accuracy. Discover the complexities of radio signal delays and bending effects due to atmospheric interactions. Gain insights into the Vienna troposphere mo
0 views • 80 slides
Comprehensive Overview of Distributed Intrusion Detection System (DIDS)
Explore the Distributed Intrusion Detection System (DIDS) introduced by Mohammad Hossein Salehi and Kiumars Talaee. Learn about the significance, working, and different types of IDS within DIDS like HIDS, NIDS, and agent-based IDS. Understand the division, information sources, and roles of client-ba
0 views • 25 slides
A Hybrid Intrusion Detection System Approach for IEEE 802.11 Wireless Networks
This research project explores the development of a hybrid intrusion detection system for IEEE 802.11 wireless networks. The study includes research objectives, background information, experimental results, evaluation, and comparison of existing systems, HWIDS design, conclusions, future work, and r
0 views • 73 slides
Stratospheric and Tropospheric NO2 Separation Approaches
This document discusses the separation of stratospheric and tropospheric NO2 using different approaches such as spectral retrieval, conversion of slant columns, and two distinct methods for handling the data. Challenges for geostationary sensors and baseline approaches for operational algorithms are
0 views • 23 slides
Effective Strategies for Virtualizing Intrusion Detection Systems
Explore the benefits of virtualizing intrusion detection systems through microservices, addressing the limitations of traditional monolithic IDS setups. Learn how this approach improves scalability, efficiency, and customization for enhanced security measures in network environments.
0 views • 25 slides
Comparison of Model 1 Simulations to Satellite Observations for July 1, 2010
Explore the comparison of Model 1 simulations with various satellite measurements such as AIRS, OMI, CloudSat, and CALIPSO for July 1, 2010. Focus on OMI Tropospheric NO2 data and factors impacting the tropospheric NO2 column retrieval.
0 views • 27 slides
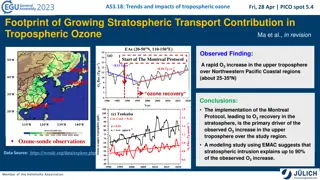
Impacts of Tropospheric Ozone and Stratospheric Transport Contribution
The study examines the trends and impacts of tropospheric ozone, focusing on the significant increase observed over the Northwestern Pacific Coastal regions. It explores the primary drivers behind this ozone increase, attributing up to 90% to stratospheric intrusions as a result of the Montreal Prot
0 views • 6 slides
Mastering Intrusion Detection with Snort: A Comprehensive Guide
Dive into the world of network security with Snort, the powerful intrusion detection system. Learn how to analyze network traffic in real time, create custom configuration files, and defend against zero-day attacks. Explore Snort's versatility, portability, and configurability, and discover advanced
0 views • 5 slides
Understanding IDS and IPS for Network Security
Enhance the security of your network with IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) by monitoring traffic, inspecting data packets, and detecting malicious activities based on known signatures. Learn about different types like HIDS and NIDS, their functions, and tools us
0 views • 7 slides
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are software pieces that monitor computer systems to detect unauthorized intrusions and misuse, responding by logging activity, notifying authorities, and taking appropriate countermeasures. IDS help address security challenges, aiming to find and fix serious securi
0 views • 40 slides
Root Causes of Intrusion Detection False Negatives: Methodology and Case Study
This study, presented at IEEE MILCOM 2019 by Eric Ficke, Kristin M. Schweitzer, Raymond M. Bateman, and Shouhuai Xu, delves into the analysis of root causes of intrusion detection false negatives. The researchers explore methodologies and present a case study to illustrate their findings.
0 views • 24 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
Understanding Intrusion Detection and Prevention Systems
Learn about the components and implementation options of intrusion detection and prevention systems, as well as the goals and role of an IDPS in network defense. Discover the capabilities of IDPS, such as assessing network traffic, detecting unauthorized access, and responding to threats. Explore an
0 views • 57 slides
Study on Lower Tropospheric Ozone Increase in Indochina Peninsula
Research conducted in Hanoi, Vietnam, reveals an increase in lower tropospheric ozone over the eastern edge of the Indochina Peninsula. The study focuses on understanding the three-dimensional distribution and temporal variation of ozone to comprehend air pollution and atmospheric variability. Findi
0 views • 11 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Understanding Radon and Chemical Soil Gas Vapor Intrusion
This presentation at the 2019 International Radon Symposium in Denver, Colorado explores the association between radon, chemical soil gas, and vapor intrusion. It discusses the challenges in testing, analyzing differences, and the need for supplemental measurements like radon to validate models. The
0 views • 19 slides
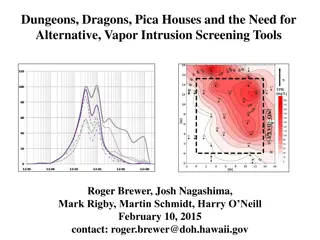
Alternative Vapor Intrusion Screening Tools for Environmental Investigations
Estimation of subslab attenuation factors for vapor intrusion investigations is crucial in assessing indoor air quality. This study reviews EPA methods, emphasizing the importance of vapor attenuation in screening indoor air for contaminants. Various experts contributed insights, leading to the deve
0 views • 35 slides
Understanding Atmospheric Composition and Structure
The presentation covers fundamental concepts related to the Earth's atmosphere, including its composition, origin of oxygen, dry and moist layers, standard atmosphere layers, and temperature variations. Key topics discussed include the primordial atmosphere, atmospheric constituents, water vapor dis
0 views • 58 slides
Pandora Advanced Validation Capabilities for NO2 Monitoring
Pandora advanced validation capabilities for NO2 monitoring involve measurement techniques such as Total and Tropospheric columns of NO2 through direct sun and MAX-DOAS methods, with emphasis on spatial coverage dependent on various factors. The system provides real-time near-surface concentrations,
0 views • 6 slides
Understanding Client-Side Attacks and Intrusion Detection
Explore client-side attacks, their methodology, and defense strategies in Ali Al-Shemery's comprehensive guide. Discover the evolving challenges of network security and the importance of staying ahead with effective intrusion detection techniques.
0 views • 65 slides
Understanding Intrusion Detection and Security Tools
Explore the world of intrusion detection, access control, and security tools through terminology, systems, classifications, and methods. Learn about intrusion detection systems (IDSs), their terminology, alert systems, classification methods like signature-based and statistical anomaly-based approac
0 views • 39 slides
GEOS-Chem Atmospheric Chemistry Model Overview
GEOS-Chem, developed by Daniel J. Jacob at Harvard University, is a global model of atmospheric composition used to understand human and natural influences on the environment. The model addresses various atmospheric chemistry issues on different scales, from local to global, and is regularly updated
0 views • 19 slides
Comprehensive Guide to Hacking Techniques and Intrusion Detection
This guide by Ali Al-Shemery provides insights into hacking techniques, intrusion detection, fingerprinting, external and internal footprinting, passive reconnaissance, WHOIS lookups, and various online tools for intelligence gathering during penetration tests. It covers identifying customer externa
0 views • 29 slides
Understanding Coupling of Convective Motions and Cloud Macrophysics in Climate Model CMDV-CM4
This project led by Lawrence Berkeley National Laboratory aims to mechanistically couple convective motions and cloud macrophysics in the CMDV-CM4 climate model. Through observational techniques and parameterization development, they seek to evaluate and enhance current cloud representations, develo
0 views • 16 slides
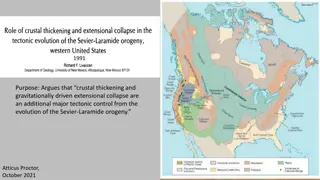
Tectonic Controls of the Sevier-Laramide Orogeny
The Sevier-Laramide orogeny was influenced by crustal thickening and gravitational extensional collapse. The tectonic model proposed suggests that conductive heating from subduction weakened the crust, leading to compression, uplift, and lateral growth. Deformation persisted from the Cretaceous to t
0 views • 8 slides
Analysis of Tropospheric Intrusion Evolution in START08 Field Campaign
The study presents the analysis of tropospheric intrusion evolution during the START08 Field Campaign using models such as WACCM and GFS. The primary goals include comparing model output with observations, verifying dynamical transport features, and studying the spatial and temporal evolution of mid
0 views • 26 slides
Analysis of GEO-CAPE Atmospheric Science Mission Alternatives
The Geostationary Coastal and Air Pollution Events (GEO-CAPE) mission aims to measure atmospheric composition and ocean color. The impact of the Tropospheric Emissions Monitoring of Pollution (TEMPO) instrument on GEO-CAPE planning is acknowledged, with a need to adjust GEO-CAPE activities. An analy
0 views • 20 slides
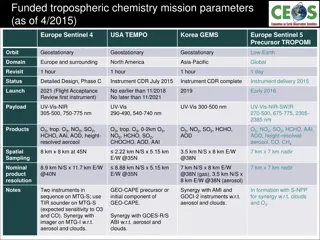
Funded Tropospheric Chemistry Mission Parameters Overview
Funded tropospheric chemistry missions like Europe Sentinel 4, USA TEMPO, Korea GEMS, and others aim to monitor atmospheric composition for air quality assessment. The missions involve advanced instruments to measure ozone, nitrogen dioxide, sulfur dioxide, aerosols, and more, with specific spatial
0 views • 9 slides