WhatsApp Direct Message
With the greatest \"WhatsApp Direct Message\" app that we've brought to you, which allows users to message random numbers without needing to save them. While this feature may offer convenience for users who frequently communicate with unknown contacts.
8 views • 22 slides
CS 404/504 Special Topics
Adversarial machine learning techniques in text and audio data involve generating manipulated samples to mislead models. Text attacks often involve word replacements or additions to alter the meaning while maintaining human readability. Various strategies are used to create adversarial text examples
1 views • 57 slides
The Truth of Righteousness by Faith Message in Laodicean Context
Understanding the significance of righteousness by faith message is crucial for Christians, especially in today's Laodicean condition. The message emphasizes justification through faith in Christ, leading to obedience to God's commandments and holy living. Encouraging believers to seek righteousness
0 views • 35 slides
Craft the Best WhatsApp Business Greeting Message Guide.
Read about the WhatsApp Business greeting message: tips and best examples to craft the perfect WhatsApp Business greeting message.\n
0 views • 7 slides
An Easy Way to Craft a 2024 Quick Message
\"Creating a quick message that stands out in 2024 requires brevity, relevance, and personalization. Ensure the subject line is concise and grabs the reader's attention. Be sure to keep the message short, focusing on the recipient's needs or interests. Engagement can be enhanced with emojis and visu
1 views • 5 slides
Accessing Electronic Case Documents via mySocialSecurity Message Center
Learn how to access your electronic case documents through the mySocialSecurity Message Center. Follow these steps: sign in to mySocialSecurity, verify your cell phone number, enter the security code, agree to the terms, select messages, open the message, and click to view the PDF document. Retrieve
0 views • 8 slides
Guide to Using the EPR Message Centre for Electronic Patient Records
Learn how to efficiently navigate and utilize the Message Centre in the Electronic Patient Record (EPR) system for managing workflow, signing off letters, reviewing results, and handling notifications. Accessible through Cerner Millennium, the Message Centre allows healthcare providers to electronic
0 views • 45 slides
Comprehensive Guide to Message Evaluation, Testing, and Provisioning System (MVPS)
Explore the Message Evaluation, Testing, and Provisioning System (MVPS) used by the Center for Surveillance, Epidemiology, and Laboratory Services. MVPS streamlines data collection, collaboration, and provision of timely and accurate data, enhancing public health goals. Learn about the Components of
2 views • 13 slides
Real-Time Payments: Actors and Message Flows Overview
This document provides an overview of the actors involved in a payment flow and the message portfolio in Real-Time Payments (RTP). It includes details on various actors like Instructing agent, Forwarding agent, Ultimate Debtor, Reimbursement agents, and more. The provided message flows illustrate th
1 views • 12 slides
Understanding Sender, Message, Receiver Correspondence in Communication Process
Communication process involves sender, message, and receiver elements. The sender initiates communication, generates a message, and conveys it to the receiver. The message is encoded, transmitted through a channel, and decoded by the receiver. Noise can hinder the communication process by interferin
1 views • 13 slides
Understanding Message Passing in Distributed Systems
Explore the key concepts of message passing in distributed systems, covering inter-process communication, desirable features like simplicity, efficiency, and reliability, different methods for information sharing, and the importance of synchronization and buffering. Dive into the intricacies of enco
0 views • 68 slides
Understanding Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Introduction to Structured Text in PLC Programming
Structured text is a high-level text language used in PLC programming to implement complex procedures not easily expressed with graphical languages. It involves logical operations, ladder diagrams, and efficient control logic for industrial automation. Concepts such as sensor input, logic operation
5 views • 23 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Enhancing Accessibility Through Alternate Text in Microsoft Documents
Explore the importance of alternate text in Microsoft documents for accessibility. Learn what alternate text is, why and when you should use it, and how to add it effectively. Discover the benefits of incorporating alternate text and the legal aspects related to accessibility under Section 508. Enha
0 views • 23 slides
Understanding the Impact of Message Creation on Communication Processes
The process of communication begins with creating a message, which can significantly influence how it is received. Messages, conveyed through words, signs, or sounds, are interpreted by receivers based on the sender's delivery. Littlejohn (2018) emphasizes the importance of how senders initiate comm
1 views • 9 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Text Classification and Nave Bayes: The Power of Categorizing Documents
Text classification, also known as text categorization, involves assigning predefined categories to free-text documents. It plays a crucial role in organizing and extracting insights from vast amounts of unstructured data present in enterprise environments. With the exponential growth of unstructure
0 views • 28 slides
Understanding Audience and Purpose in Text Analysis
When analyzing written texts, identifying the purpose and audience is crucial. The purpose reflects the reason behind the text, while the audience indicates who the text is intended for. By recognizing these aspects, one can better understand the content, language, and overall impact of the text. Va
1 views • 50 slides
Essential Information on Text-to-911 System
Explore key details about the text-to-911 system, including capturing text conversations, handling abandoned calls, transferring text calls to queues, and managing text conversations effectively. Learn about system configurations, call release timings, and dispatcher capabilities in handling text me
0 views • 12 slides
Text-to-911 System Operations Quiz
Test your knowledge on Text-to-911 system operations with this quiz. Learn about capturing text conversations, handling abandoned calls, transferring calls to queues, text conversation timelines, and more. Enhance your understanding of the protocols and procedures involved in managing text-based eme
1 views • 12 slides
Implementing Your Budget & Message for Effective Media Partnership
This presentation delves into the crucial aspects of implementing a budget and crafting a message for effective collaboration with media partners. Learn how to strategize your spending across different outlets, work with media sales representatives to maximize audience reach, and identify the best t
0 views • 13 slides
Detecting Sensitive Data Disclosure via Text Analysis
This article discusses techniques for detecting sensitive data disclosure, including taint analysis and bi-directional text correlation analysis. It covers existing detection methods, challenges with generic APIs, and solutions using text correlation analysis to determine data sensitiveness. Example
0 views • 34 slides
Enhancing Corpus Analysis: Text and Sub-text Level Analysis
This study delves into the importance of improving text and sub-text level analysis of corpora, highlighting traditional approaches, current tools, challenges, and the necessity for effective database design. It emphasizes the need for user-friendly solutions to enhance research capabilities.
0 views • 19 slides
Understanding Message Passing Models in Computer Science
Message passing models in computer science involve concepts like producer-consumer problems, semaphores, and buffer management. This content explores various scenarios such as void producers and consumers, as well as the use of multiple semaphores. The functions of message passing are detailed, high
0 views • 50 slides
Understanding Text Representation and Mining in Business Intelligence and Analytics
Text representation and mining play a crucial role in Business Intelligence and Analytics. Dealing with text data, understanding why text is difficult, and the importance of text preprocessing are key aspects covered in this session. Learn about the goals of text representation, the concept of Bag o
0 views • 27 slides
Introduction to JMP Text Explorer Platform: Unveiling Text Exploration Tools
Discover the power of JMP tools for text exploration with examples of data curation steps, quantifying text comments, and modeling ratings data. Learn about data requirements, overall processing steps, key definitions, and the bag of words approach in text analysis using Amazon gourmet food review d
0 views • 23 slides
Impact of Message Execution on Advertising Effectiveness
The impact of a message in advertising is not just about what is said, but also how it is said. Different cultures and ads have varying approaches, with some focusing on rational positioning while others appeal to emotions. The choice of headlines and copy can significantly influence the effectivene
0 views • 11 slides
Early Church Message and Format in Acts of the Apostles: Kerygmata by C. H. Dodd
The early church's message and format in Acts of the Apostles, particularly focusing on the kerygmata as elucidated by C. H. Dodd, with references to Acts 2:14-39 and 3:12-26. Explore the challenges to the kerygmata and the adaptation of the Christian message to various audiences. Additionally, insi
0 views • 17 slides
IPC Lab 2 MessageQ Client/Server Example
This MessageQ example demonstrates the client/server pattern using SYS/BIOS heap for message pool, anonymous message queue, and return address implementation. The example involves two processors - HOST and DSP, where the DSP processor acts as the server creating a named message queue, and the HOST p
0 views • 12 slides
Exploring Text Mining Methods and Applications
Text mining is a complex field that presents a significant disjunction in methods compared to other data analysis approaches. Pre-LLM methods are still relevant in various applications, showcasing different performance in text mining tasks. The analysis involves examining individual words' presence,
0 views • 13 slides
Understanding Bigrams and Generating Random Text with NLTK
Today's lecture in the Computational Techniques for Linguists course covered the concept of bigrams using NLTK. Bigrams are pairs of words found in text, which are essential for tasks like random text generation. The lecture demonstrated how to work with bigrams, including examples from the NLTK boo
0 views • 19 slides
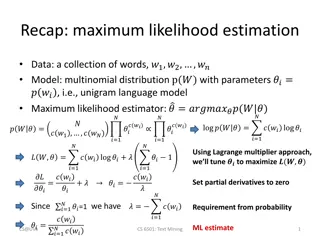
Statistical Text Analysis Techniques Overview
The content covers key concepts in statistical text analysis, including maximum likelihood estimation, N-gram language model smoothing, and perplexity calculation. It then delves into Latent Semantic Analysis and the practical application of vector space models, highlighting considerations like syno
0 views • 28 slides
Enhancing Reading Comprehension Through Text-Dependent Questions
This resource delves into the significance of text-dependent questions in improving students' reading comprehension skills by emphasizing the importance of evidence from the text, building knowledge through nonfiction, and developing critical thinking abilities. It highlights key advances in educati
0 views • 16 slides
Annotating Fiction Elements: How To Effectively Mark Text and Add Comments
Learn how to annotate fiction elements with this step-by-step guide. Discover how to highlight text, change text colors, add comments, and insert text boxes for notes. Enhance your reading comprehension and analysis skills by mastering the art of annotating literary works.
0 views • 18 slides
Understanding Message Passing Interface (MPI) Standardization
Message Passing Interface (MPI) standard is a specification guiding the development and use of message passing libraries for parallel programming. It focuses on practicality, portability, efficiency, and flexibility. MPI supports distributed memory, shared memory, and hybrid architectures, offering
0 views • 29 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
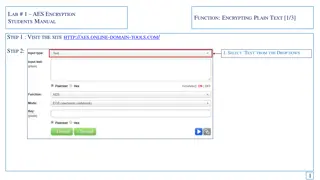
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides
CC5212-1 Procesamiento Masivo de Datos Otoño 2016 Lab 2: Aidan Hogan's Message
In this lab project, Aidan Hogan provides instructions for accessing a code repository and implementing an instant messaging system. The steps include logging in, connecting to a directory, implementing message servers and apps, and setting up the command line to message peers. Detailed visuals acco
0 views • 24 slides




























![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245322/bulk-sms-providers-in-australia-august-2024-price-comparison.jpg)
![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245325/bulk-sms-providers-in-australia-august-2024-price-comparison-245325.jpg)