Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Color Theory: A Comprehensive Guide to Colors
Explore the fascinating world of colors with an in-depth look into color theory. Learn about chromatic and achromatic colors, neutral colors, hues, color wheels, primary and secondary colors, tertiary colors, values, tints, shades, and tones. Delve into the visual responses of the eye to reflected r
2 views • 19 slides
Exploring Transpositional Combination and Contour Theory in Music
Dive into the world of transpositional combination and contour theory within music theory, which involves creating larger sets by combining one set with its transpositions. Examples include creating tetrachords and diatonic collections through dyads and their transpositions. Explore the reversibilit
0 views • 23 slides
Renal Function Tests and Kidney Health
Renal function tests are essential for diagnosing and monitoring kidney health. These tests assess functions like glomerular filtration, tubular reabsorption, and endocrine functions of the kidneys. Common indicators include serum urea, creatinine levels, and more. It's crucial to evaluate renal fun
0 views • 34 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
2 views • 27 slides
Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
2 views • 17 slides
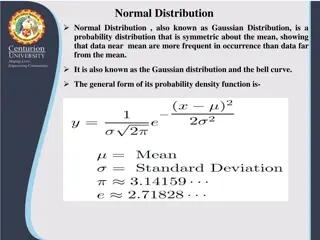
Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
2 views • 8 slides
Hopfield Nets in Neural Networks
Hopfield Nets, pioneered by John Hopfield, are a type of neural network with symmetric connections and a global energy function. These networks are composed of binary threshold units with recurrent connections, making them settle into stable states based on an energy minimization process. The energy
0 views • 37 slides
Optical Telescope Types and Lens-Maker's Formula
Optical telescopes utilize lenses or mirrors to collect and focus light for imaging celestial objects. The lens-maker's formula is crucial for determining the focal length of lenses, considering factors like index of refraction and radii of curvature. Different lens configurations and materials help
0 views • 17 slides
Introduction to Gamma Function and Equivalent Integral Forms
The Gamma function is a versatile mathematical function that generalizes the factorial function to non-integer and complex values. It has various integral definitions such as the Euler-integral form. The proof of the factorial property of the Gamma function is demonstrated through analytical continu
1 views • 20 slides
Light: Reflection, Refraction, and Interference in Optics
Explore the fascinating world of optics with topics ranging from the principles of reflection and refraction to the intricate phenomenon of interference. Delve into the concepts of index of refraction, chromatic dispersion, rainbows, and more. Discover the secrets behind the blue-green color of a Mo
0 views • 15 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Chromaticity Compensation Options for the Ion Collider Ring
The MEIC Interaction Region faces challenges due to high beta functions causing chromatic perturbation. To address this, local compensation through Chromaticity Compensation Block (CCB) with sextupoles is proposed. Three CCB options are presented for consideration. The report explores the impact of
0 views • 17 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Insights into Graph Colorings, Chromatic Polynomials, and Conjectures in Discrete Geometry
Delve into the fascinating world of graph colorings, chromatic polynomials, and notable conjectures in discrete geometry. Explore the impact of June Huh in bringing Hodge theory to combinatorics and his proof of various mathematical conjectures. Uncover the significance of the four-color theorem, co
0 views • 17 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
1 views • 37 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Basics of Digital Image Processing in Computer Applications
Understanding digital image processing involves analyzing monochromatic and chromatic images, using morphological operators like erosion and dilation, and utilizing structuring elements. The process includes concepts such as image representation, grey levels, and colour models like RGB. By learning
0 views • 51 slides
Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Dynamic Aperture Study for Ion Ring Lattice Optimization
This study focuses on optimizing the dynamic aperture of the ion ring lattice, covering topics such as correct chromaticity, aperture scanning, effects of alignment and field errors, and correction procedures. The comparison of various lattice schemes provides insights into aperture characteristics,
0 views • 25 slides
Overview of Graphing Techniques and Functions
Explore graphing techniques including stretching, shrinking, reflecting, symmetry, translations, and various types of functions such as the identity function, square function, cube function, square root function, cube root function, and absolute value function. Understand vertical and horizontal shi
0 views • 25 slides
Monitoring Thyroid Function After Head and Neck Cancer Treatment
This collection of images and data discusses the importance of monitoring thyroid function after head and neck cancer treatment, specifically focusing on post-treatment thyroid function tests, audits of practices in head and neck units, thyroid function post laryngectomy, and the significance of det
1 views • 11 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Analysis of WLAN Sensing Sequence Design Using Ambiguity Function and Range-Doppler Map
In this document, the authors from Huawei discuss the analysis of employing the ambiguity function for WLAN sensing sequence design. They delve into the ambiguity function's definition, analysis, and its comparison with the range-Doppler map. The document highlights the importance of ambiguity funct
0 views • 15 slides
Function-Based Behavior Support Plans: A Comprehensive Guide
Explore the process of developing Function-Based Behavior Support Plans (BSP) using Functional Behavioral Assessment (FBA). Understand the concepts of function and functional behavior assessment, learn how FBA/BSP fits within a multi-tiered support system, and practice developing BSP for students. D
0 views • 74 slides
Lens Defects and Aberrations in Optics
Lens defects and aberrations in optics, such as chromatic and spherical aberrations, are caused by the laws of reflection and refraction. They lead to issues like longitudinal and lateral chromatic aberration, as well as spherical aberration. Proper correction methods, like using achromats with yell
0 views • 24 slides
Optical Instruments: Lenses, Images, and Magnification
Discover how combinations of lenses form images, explore thin lens equations and magnification principles, learn about compound microscopes, and understand the limits to resolution including spherical and chromatic aberrations and dispersion effects in this informative lecture on optical instruments
0 views • 21 slides
Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides