Rescue Drone: Increasing Autonomy and Implementing Computer Vision
Focuses on developing a rescue drone with increased autonomy and implementing computer vision for advanced object detection. The team, consisting of Cody Campbell (Hardware Engineer), Alexandra Borgesen (Computer Engineer), Halil Yonter (Team Leader), Shawn Cho (Software Engineer), Peter Burchell (M
480 views • 44 slides
Sports Volunteers Movement in Botswana: Challenges and Strategies
The Sports Volunteers Movement (SVM) in Botswana, under the Botswana National Sport Commission, aims to promote volunteerism in sports for community development. Despite successful events, there is a decline in volunteer participation. Reasons include lack of incentives, burnout, and feeling unappre
15 views • 11 slides
Counterfeit Detection Techniques in Currency to Combat Financial Fraud
Currency counterfeiting poses a significant challenge to the financial systems of countries worldwide, impacting economic growth. This study explores various counterfeit detection techniques, emphasizing machine learning and image processing, to enhance accuracy rates in identifying counterfeit curr
2 views • 15 slides
Machine Learning Algorithms and Models Overview
This class summary covers topics such as supervised learning, unsupervised learning, classification, clustering, regression, k-NN models, linear regression, Naive Bayes, logistic regression, and SVM formulations. The content provides insights into key concepts, algorithms, cost functions, learning a
4 views • 39 slides
Kernel Tricks in Machine Learning
Kernel tricks in machine learning involve transforming inputs into higher-dimensional spaces to make linear models work for nonlinear data. Kernels can be applied to various algorithms like SVM, ridge regression, and more, allowing for better model performance with complex datasets.
4 views • 15 slides
Efficient Anomaly Detection for Batch Systems Using Machine Learning
Explore a lightning talk session focusing on using Collectd metrics and job data in HTCondor batch systems for anomaly detection. Challenges with raw historical data are addressed through data collection, manipulation, and application of anomaly detection techniques using ML. Various algorithms such
1 views • 14 slides
NLDB 2020 Pattern Learning for Detecting Defect Reports and Improvement Requests
This research paper focuses on automatically learning patterns to detect actionable feedback in mobile app reviews, specifically identifying defect reports and improvement requests. The main goal is to develop a mechanism that can effectively classify feedback types using both manual and learned pat
4 views • 17 slides
Functional Approximation Using Gaussian Basis Functions for Dimensionality Reduction
This paper proposes a method for dimensionality reduction based on functional approximation using Gaussian basis functions. Nonlinear Gauss weights are utilized to train a least squares support vector machine (LS-SVM) model, with further variable selection using forward-backward methodology. The met
4 views • 23 slides
Evolution of Sentiment Analysis in Tweets and Aspect-Based Sentiment Analysis
The evolution of sentiment analysis on tweets from SemEval competitions in 2013 to 2017 is discussed, showcasing advancements in technology and the shift from SVM and sentiment lexicons to CNN with word embeddings. Aspect-Based Sentiment Analysis, as explored in SemEval2014, involves determining asp
4 views • 23 slides
Gender Identification in SMS Texts: An Exploration of Authorship Characteristics
Cyber forensics methods play a crucial role in detecting SMS authors for potential use in criminal persecution cases as visual anonymity in text messages can be exploited by criminals. This study delves into the authorship characterization of SMS texts by categorizing authors based on sociolinguisti
0 views • 17 slides
Stream Management and Online Learning in Data Mining
Stream management is crucial in scenarios where data is infinite and non-stationary, requiring algorithms like Stochastic Gradient Descent for online learning. Techniques like Locality Sensitive Hashing, PageRank, and SVM are used for critical calculations on streaming data in fields such as machine
3 views • 46 slides
Implicit Citations for Sentiment Detection: Methods and Results
This study focuses on detecting implicit citations for sentiment detection through various tasks such as finding zones of influence, citation classification, and corpus construction. The research delves into features for classification, highlighting the use of n-grams, dependency triplets, and other
2 views • 14 slides
Overview of Linear Classifiers and Perceptron in Classification Models
Explore various linear classification models such as linear regression, logistic regression, and SVM loss. Understand the concept of multi-class classification, including multi-class perceptron and multi-class SVM. Delve into the specifics of the perceptron algorithm and its hinge loss, along with d
1 views • 51 slides
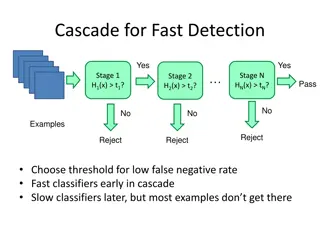
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Exploring Iris Dataset: Attribute Analysis and Prediction
This analysis explores the Iris dataset containing 150 samples with continuous features like Sepal Length, Sepal Width, Petal Length, and Petal Width, classified into Setosa, Versicolor, and Virginica species. The focus is on determining the best attributes to predict the species, evaluating the inf
5 views • 18 slides
Aspect-Based Sentiment Analysis Study
Aspect-Based Sentiment Analysis is a key area in natural language processing, focusing on extracting sentiment at a granular aspect level, such as specific features of products or services. This study delves into feature selection using Information Gain, highlighting the importance of identifying re
4 views • 21 slides
Predicting Treatment Outcome in Cervical Cancer Using Texture Analysis and SVM
Determine if treatment outcome for locally advanced cervical cancer can be predicted using dynamic contrast-enhanced MR images. Texture analysis and support vector machines were used to differentiate between cured and relapsed patients based on spatial relations within the tumor. Statistical feature
5 views • 16 slides
Support Vector Machines
A comprehensive overview of Support Vector Machines (SVM), a popular machine learning algorithm used for classification and regression tasks. Learn about the principles behind SVM, how it works, its strengths and weaknesses, and practical applications in various fields such as finance, healthcare, a
5 views • 57 slides
Machine Learning for Public Health in R
In this comprehensive guide, delve into the realm of machine learning for public health in R. Explore key tasks such as clustering, classification, and prediction/regression. Uncover various methods like K-means, SVM, and RPT for both unsupervised and supervised learning. Gain insights into distance
2 views • 51 slides
Introduction to SVM & Logistic Regression: A Comparative Analysis
Dive into the comparison between SVM's soft and hard margins with Logistic Regression. Explore generative vs. discriminative approaches, linear classifiers, support vector machines, handling non-linearly separable data, and more!
5 views • 17 slides
Black-box Image Extraction Attacks on RBF SVM Model
Explore black-box image extraction attacks on RBF SVM classification model, analyzing vulnerabilities and extracting meaningful information from machine learning models. Learn about defenses and the motivation behind these attacks.
6 views • 15 slides
Support Vector Machines for Classification and Regression
Explore the fundamentals of Support Vector Machines (SVM), a supervised learning technique that creates decision boundaries to separate data points into distinct sets. Learn about SVM basics, hyperplanes, maximum-margin classifiers, support vectors, creating the maximum margin hyperplane, and suppor
4 views • 19 slides
Advanced Protein Prediction Methods: Deep Learning Approach
Explore the cutting-edge realm of protein structure predictions using deep learning methods for enhanced accuracy in single model quality assessment. This research delves into the development and testing of algorithms such as DL-Pro, SVM-Pro, and FFNN-Pro, showcasing superior accuracy in protein mod
5 views • 53 slides
Implementing AdaBoost Algorithm: Overview, Boosting Concept, and Dataset Analysis
Explore AdaBoost algorithm implementation with a focus on boosting concept, classifier support using SVM, dataset analysis for credit card fraud detection, and techniques for handling class imbalance. Understand the iterative process, classifier training, and feature selection for optimal prediction
4 views • 10 slides
Anomaly Detection Schemes in Data Mining
Explore the various approaches in anomaly detection, such as graphical, model-based, One-Class SVM, distance-based, and profile-based schemes. Learn how anomalies are identified based on deviations from normal behavior, with applications in fraud detection, network security, and more.
1 views • 36 slides
Innovative Discrimination of Outer Membrane Proteins with Neutrosophic Set SVM
Explore the novel approach of utilizing neutrosophic set with reformulated SVM for discriminating outer membrane proteins. This innovative classifier reduces outlier effects and outperforms traditional SVM in accuracy and MCC. Neutrosophic logic, introduced in 1995, enhances fuzzy logic by incorpora
5 views • 22 slides
Handwritten Character Recognition: Machine Learning Algorithms and Programming Languages
Explore how machine learning algorithms and multiple programming languages are utilized for handwritten character recognition. This study delves into the application of OCR and showcases the effectiveness of character recognition in various fields. The project objectives involve implementing classif
3 views • 48 slides
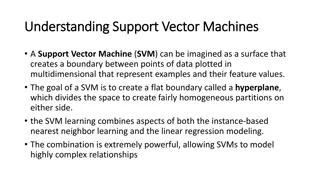
Understanding Support Vector Machines and their Applications
Explore the concept of Support Vector Machines (SVM) as powerful models for classification and numeric prediction tasks. Learn how SVMs create hyperplanes to separate data points in high-dimensional space, making them valuable for various applications like gene expression analysis and rare event det
3 views • 36 slides
Introduction to SVM and Logistic Regression in Machine Learning
Explore the fundamental concepts of Support Vector Machines (SVM) and Logistic Regression in machine learning through topics such as soft and hard margin comparisons, generative versus discriminative approaches, linear classifiers, margin optimization, and more. Dive into the differences between SVM
0 views • 17 slides
Support Vector Machine Overview and Application
Explore the concepts and applications of Support Vector Machines (SVM) for classifying data with maximum margin separation. Learn about linear and non-linear SVM theories, dual solutions, and numerical examples. Gain insights into finding optimal parameters (w,b) for clean data classification.
3 views • 40 slides
Support Vector Machine in Information Retrieval
Learn about Support Vector Machine (SVM) in information retrieval, a machine learning method aiming to find maximal separation between classes. Explore the concept of maximizing margins, decision boundaries, and linear programming for effective classification.
0 views • 33 slides
Kernel Learning with a Million Kernels - Methods and Formulations
Explore the intricate world of kernel learning with a focus on methods and formulations such as SVM, regularizers, GMKL primal formulation, and optimization techniques like Projected Gradient Descent. Uncover the challenges and solutions in this cutting-edge field.
13 views • 18 slides
Large Margin Classification & Perceptron Algorithm Overview
Learn about Large Margin Classification, Support Vector Machine (SVM), Perceptron algorithm, and their contributions. Explore the concepts of SVM, Voted-perceptron, and Perceptron in machine learning for supervised classification.
2 views • 23 slides
Enhancing Audio Classification with Sparsity-Eager SVM Fusion
Explore how the combination of Sparsity-Eager SVM and regression classifiers can build a robust supervised audio classifier, achieving high generalization on new test examples while avoiding over-fitting. Learn about the integration of SVM principles with sparse regression techniques to create a pow
1 views • 18 slides
Introduction to Machine Learning with SVM Dual & Kernels
SVM dual formulation, Lagrangian duality, and dual SVM derivation for linearly separable and non-separable cases. Discover the significance of learning about the dual SVM, its interpretation in terms of sparsity, and how the dual formulation relies on dot products.
1 views • 15 slides
Dual SVM Formulation & Interpretation: Insights into Machine Learning
Exploring the Lagrangian duality in Support Vector Machines (SVM) through dual formulations, focusing on the linearly separable and non-separable cases. Uncover the significance of learning the dual SVM, its sparsity interpretation, and the kernel trick for faster problem-solving.
2 views • 24 slides
AdaBoost Algorithm and SVM for Credit Card Fraud Detection
Explore the implementation of AdaBoost and SVM algorithms for detecting credit card fraud, including the concept of boosting through AdaBoost, the support vector machine (SVM) classifier, handling class imbalance, and dataset insights. Learn how these techniques work together to enhance prediction a
0 views • 10 slides
Learning Using Privileged Information: SVM and Weighted SVM
Explore SVM and Weighted SVM techniques in this study, which reveal the uniqueness of SVM solutions, the relation between SVM and WSVM, and the direct weight learning from data. Discover how these methods optimize risk estimation and enhance classifier performance across various experimental setting
1 views • 13 slides
Synergistic Multiclass SVM for Gene Identification from Protein Sequences
Explore a novel method for identifying genes from protein sequences using a position-specific scoring matrix (PSSM) and multiclass SVM. The approach combines results from multiple SVMs for improved gene identification accuracy.
0 views • 13 slides
Sparsity-Eager SVM for Audio Classification and Fusion with Regression Classifiers
Explore the integration of sparsity-eager SVM for audio classification and fusion with regression classifiers to build a robust supervised audio classifier. The goal is to avoid overfitting, achieve better generalization, and provide scalability in classification complexity. Learn about the applicat
0 views • 18 slides