Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
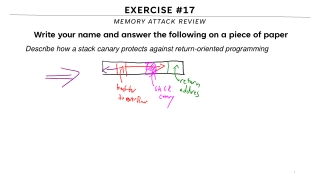
Memory Attack Review Overview
This content provides insights on memory attacks, particularly focusing on return-oriented programming and stack canary protection. It explores how stack canaries safeguard against return-oriented programming by detecting buffer overflows and preventing the alteration of return addresses. With a vis
1 views • 32 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Dynamic Buffer Sizing using Passive Measurements from P4 Switches
This study explores the dynamic modification of router buffer sizes by leveraging passive measurements from P4 switches. By dynamically adjusting buffer sizes based on factors like the number of long flows, average round-trip time, queueing delays, and packet loss rates, network performance can be o
3 views • 14 slides
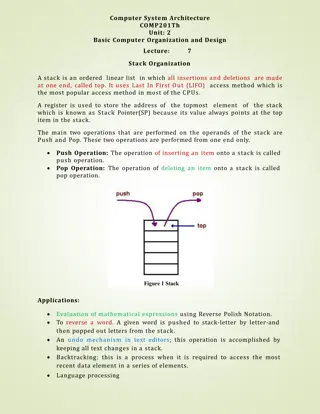
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Understanding Circular Buffers and Linked Lists in Data Structures
Circular Buffers are data structures designed to efficiently manage streams of data while maintaining a fixed amount of memory usage. The buffer consists of a fixed-length array with head and tail indexes, allowing data to loop back to the beginning when the end of the buffer is reached. It is cruci
0 views • 24 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Understanding Buffer Solutions: Properties and Applications
Buffer solutions are essential in resisting pH changes and consist of mixtures of weak acids or bases with their salts. They maintain constant pH levels despite dilution or addition of acids/bases. Buffer capacity measures the amount of acid/base needed for a pH change. Biological systems and pharma
3 views • 4 slides
Neural Shift-Reduce Dependency Parsing in Natural Language Processing
This content explores the concept of Shift-Reduce Dependency Parsing in the context of Natural Language Processing. It describes how a Shift-Reduce Parser incrementally builds a parse without backtracking, maintaining a buffer of input words and a stack of constructed constituents. The process invol
0 views • 34 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Buffer Overflow: Understanding, Defenses, and Detection
Dive into the world of buffer overflow attacks with insights on understanding the concept, implementing defenses, and detecting stack smashing using techniques like canary values. Discover how to protect against vulnerabilities and grasp the significance of elements such as EIP, ASLR, DEP, and NX bi
0 views • 10 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding Computer System Exploits and Prevention
Exploring program exploitation, stack buffer overflows, vulnerability analysis, and exploit prevention strategies in computer systems. Learn about setting the stage for exploits, exploiting stack buffer overflows, and the challenges faced in executing shellcode attacks. Dive into the world of cyber
0 views • 36 slides
Understanding Buffer Overflows and Exploits in C Programs
Explore the concepts of buffer overflows and exploits in C programming, covering memory layout, program details, and examples of stack smashing and implicit casting bugs. Learn how attackers manipulate code sequences and take control through vulnerabilities like the misuse of functions like memcpy.
0 views • 39 slides
Buffer Overflows in CSE351 Autumn 2017
Explore buffer overflows in CSE351 Autumn 2017, covering topics like memory layout, stack, heap, and defenses against buffer overflows. Learn about important concepts such as input buffers, code injection, and memory allocation examples, with insights into x86-64 Linux memory layout.
0 views • 33 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Understanding Software Weaknesses and Exploits
Discover the vulnerabilities present in software such as buffer overflows and format string vulnerabilities, and how these weaknesses can be exploited to cause security issues. Learn about the technical aspects of weaknesses, stack frames, memory organization, and the potential consequences of stack
0 views • 57 slides
Understanding Memory Layout in Computer Systems at Carnegie Mellon
Explore the memory layout in computer systems through the lens of Carnegie Mellon University's advanced topics in machine-level programming. Learn about buffer overflow vulnerability protection, memory allocation examples, x86-64 Linux memory layout, and addressing schemes. Dive into practical examp
2 views • 47 slides
Understanding Heap Overflow Attacks
A heap is a collection of variable-size memory chunks managed by the program. Heap overflow attacks occur when malicious actors corrupt heap memory, potentially allowing them to overwrite data and execute arbitrary code. This poses a significant security risk. The process involves manipulating heap
2 views • 19 slides
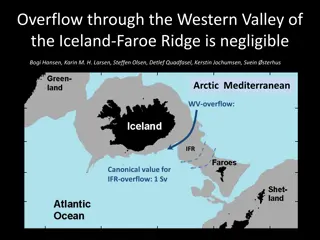
Insights on Overflow through the Western Valley of the Iceland-Faroe Ridge
Research by Bogi Hansen, Karin M. H. Larsen, Steffen Olsen, Detlef Quadfasel, Kerstin Jochumsen, and Svein Østerhus delves into the negligible overflow through the Western Valley of the Iceland-Faroe Ridge. Various field experiments and data analyses demonstrate minimal flow through the Western Val
0 views • 12 slides
Role of Sugar Industry in Circular Economy - Case Study on Spray Pond Overflow Treatment
The two-day summit organized by Mahatma Phule Krushi Vidhyapeet Krushi Mahavidhyalaya, Pune, in collaboration with various organizations, focused on the significant role of sugar and allied industries in promoting circular economy and sustainability. The event highlighted the necessity of treating s
0 views • 15 slides
Understanding Buffer Overflow in Computer Programming
This content delves into the intricacies of buffer overflow vulnerabilities in computer programming, showcasing real-world examples such as the Internet Worm and IM War incidents. It covers topics like stack buffer overflow exploits, Unix function implementations prone to buffer overflow, and the re
0 views • 35 slides
Understanding Memory Layout and Allocation in Computer Systems at Carnegie Mellon University
Exploring the memory layout and allocation in computer systems through lectures at Carnegie Mellon University, focusing on topics such as buffer overflow vulnerability protection, unions, shared libraries, stack, heap, data locations, addresses, and practical memory allocation examples. The content
1 views • 55 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Efficient Buffer Management Strategies in Database Systems
Buffer management is a crucial aspect of database systems, ensuring optimal data storage and retrieval. This involves intelligent shuffling of data between memory and disk, guided by replacement policies like LRU and Clock algorithm. Understanding how buffer managers operate and make decisions is ke
2 views • 38 slides
Understanding Buffers in Chemistry
Buffers play a crucial role in maintaining stable pH levels in solutions. They are composed of a weak acid and its conjugate base or a weak base and its conjugate acid. This summary covers the definition of buffers, differentiation between buffer and non-buffer systems, the behavior of buffers when
3 views • 23 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Buffer Overflow in C and C++ Programs
Buffer overflow is a common vulnerability in C and C++ programs where the allocated memory buffer is overwritten, causing unpredictable behavior. This vulnerability allows attackers to exploit the program by injecting malicious code. The lack of automatic bounds checking in these languages makes it
0 views • 6 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Understanding Control Hijacking Attacks in Computer Systems
Explore the concept of control hijacking attacks in computer systems, including buffer overflows, format string vulnerabilities, and use-after-free exploits. Learn about the attacker's goal, examples of attacks, and the importance of understanding C functions, the stack, and the heap. Delve into sys
0 views • 39 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
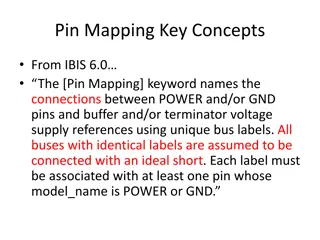
Understanding Pin Mapping and Interconnect in IBIS 6.0
Pin Mapping in IBIS 6.0 defines the connections between POWER/GND pins and buffer/terminator voltage supplies using unique bus labels. Interconnects between VDD pins and buffer supply terminals are crucial, with all pins associated with a named supply being shorted together. Draft 9 Interconnects an
0 views • 6 slides
Efficient UL Buffer Status Reporting in IEEE 802.11 Networks
IEEE 802.11-16/0856r1 discusses the importance of UL buffer status reporting in 11ax for efficient resource allocation. The document addresses managing unmanaged P2P flows to enhance buffer status reporting accuracy. It proposes solutions to prevent misallocation of resources due to large data amoun
0 views • 11 slides
Proposed Buffer Mitigation Rules Overview
The proposed buffer mitigation rules aim to address nutrient loading by adopting alternative measures to replace lost riparian buffers. The rules include options for location of mitigation, accounting for buffer and nutrient offset, and various optional methods like coastal headwater stream mitigati
0 views • 21 slides
Understanding Buffers: A Comprehensive Overview
Explore the concept of buffers, their role in resisting pH changes, and how they differ from non-buffer systems. Learn about buffer solutions like acetate buffer and how they react to acids and bases. Discover the importance of pH indicators in understanding the pH of buffer solutions.
0 views • 24 slides