Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
Understanding Network Interference and Censorship in Social Media
Discover the insights into detecting network interference, censorship, and social media manipulation through a collection of case studies, research papers, and real-world examples discussed in a Spring 2018 lecture. Topics include the goals of PAM 2011 paper, the Green Dam and Blue Dam projects, the
1 views • 27 slides
Exploring Adversarial Machine Learning in Cybersecurity
Adversarial Machine Learning (AML) is a critical aspect of cybersecurity, addressing the complexity of evolving cyber threats. Security analysts and adversaries engage in a perpetual battle, with adversaries constantly innovating to evade defenses. Machine Learning models offer promise in combating
0 views • 43 slides
Staying Safe Online: Essential Tips for a Secure Online Experience
Stay safe online by protecting your personal information, avoiding strangers, and being cautious of viruses and spam emails. Learn how to use the internet wisely while respecting others and staying secure online.
0 views • 12 slides
Understanding Water Activity and Mass Transfer in Food Engineering
Water activity (aw) plays a crucial role in microbial activity, chemical and physical changes in foods, and the dehydration process. Maintaining water activity below specific levels can prevent microbiological spoilage and deterioration reactions, while also affecting texture, aroma, and overall qua
0 views • 11 slides
Introduction to Machine Learning Concepts
This text delves into various aspects of supervised learning in machine learning, covering topics such as building predictive models for email classification, spam detection, multi-class classification, regression, and more. It explains notation and conventions used in machine learning, emphasizing
1 views • 22 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Enhancing Email Security with DMARC: A Comprehensive Approach
Explore the vital components of DMARC, a robust spam filtering and phishing protection methodology, as presented by Ben Serebin. Discover how DMARC integrates SPF and DKIM to safeguard email authenticity and ensure a secure communication environment. Uncover the challenges, prerequisites, and implem
0 views • 13 slides
Collective Spammer Detection in Evolving Social Networks
Exploring the growth of spam in social networks, this study highlights the challenges posed by spammers and the need for collective detection mechanisms. With insights on spam trends, interaction methods, and user profiles, it sheds light on the evolving landscape of social network spam.
0 views • 65 slides
Text Classification and Naive Bayes in Action
In this content, Dan Jurafsky discusses various aspects of text classification and the application of Naive Bayes method. The tasks include spam detection, authorship identification, sentiment analysis, and more. Classification methods like hand-coded rules and supervised machine learning are explor
1 views • 82 slides
Understanding Text Classification Using Naive Bayes & Federalist Papers Authorship
Dive into the world of text classification, from spam detection to authorship identification, with a focus on Naive Bayes algorithm. Explore how Mosteller and Wallace used Bayesian methods to determine the authors of the Federalist Papers. Discover the gender and sentiment analysis aspects of text c
0 views • 71 slides
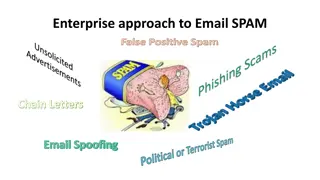
Understanding Enterprise Email Spam Prevention Techniques
Learn about the key strategies used by enterprises to combat email spam, including spam filters, SPF records, DMARC, DKIM, whitelisting, and SCL ratings. Discover how these tools work together to protect against spam, spoofing, and phishing attempts.
0 views • 8 slides
Understanding Text Classification in Information Retrieval
This content delves into the concept of text classification in information retrieval, focusing on training classifiers to categorize documents into predefined classes. It discusses the formal definitions, training processes, application testing, topic classification, and provides examples of text cl
0 views • 57 slides
Analysis of Spam Activity on Popular Social Networks
This research paper presents an in-depth analysis of spam activity on major social networking platforms such as Facebook, MySpace, and Twitter. The study includes data collection, analysis of spam bots, identification of spam campaigns, and analysis of results. It reveals insights into user behavior
2 views • 38 slides
Personalized Spam Filtering for Gray Mail Analysis
This work delves into the concept of gray mail - messages that some users want while others don't. It explores the challenges posed by gray mail and presents a large-scale personalization algorithm to address these issues. The study leverages data from Hotmail Feedback Loop, focusing on user prefere
3 views • 22 slides
Efficient Email Management Strategies and Tips for Organizing Your Inbox
Learn essential email management techniques such as categorizing emails, setting up rules, minimizing unread messages, blocking spam, and handling important messages effectively. Discover how to manage your email efficiently to stay organized and ensure you don't miss critical information or lose im
0 views • 7 slides
Adversarial Learning in ML: Combatting Internet Abuse & Spam
Explore the realm of adversarial learning in ML through combating internet abuse and spam. Delve into the motivations of abusers, closed-loop approaches, risks of training on test data, and tactics used by spammers. Understand the challenges and strategies involved in filtering out malicious content
0 views • 13 slides
Protect Yourself and Your Campaign: Digital Threat Protection Guide
Safeguard your data, accounts, and devices from cyber threats by controlling your information, avoiding malware, spam, viruses, and phishing attempts. Learn to use secure links, encryption, and sensitivity labels to enhance your online security.
0 views • 5 slides
Homomorphic Encryption and RLWE Schemes Overview
Homomorphic encryption allows computation on encrypted data, enabling privacy in outsourced computing services and applications like spam filters for encrypted mail. The Ring Learning With Errors (RLWE) scheme and its properties are discussed, along with symmetric encryption from RLWE and fully homo
0 views • 16 slides
Exploring Graph Structure in the Web: A Comprehensive Analysis
Delve into a detailed analysis of the web graph, leveraging a vast dataset of 3.5 billion web pages and 128.7 billion links. The study compares various features such as degree distributions, connectivity, average distances, and connected components' structures. The research aims to enhance ranking m
0 views • 16 slides
Protecting Your Business from Cybersecurity Threats
In today's digital landscape, the risk of cyber attacks is higher than ever. Hackers offer malicious services for a low cost, increasing the threat of ransomware, phishing, and spam attacks. With statistics showing the rise in ransomware incidents, it's crucial for organizations to prioritize securi
0 views • 24 slides
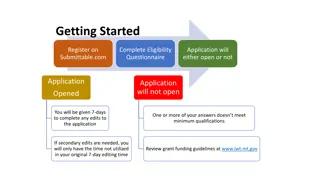
Application Process for IWT Grant Cycle
Complete the application process for the IWT grant cycle on Submittable.com, including eligibility questionnaire, application submission, review, and approval steps. Make sure to check your SPAM folder for important correspondence and follow the deadlines for editing, acceptance of terms, financial
0 views • 13 slides
Collaborative Bayesian Filtering in Online Recommendation Systems
COBAFI: COLLABORATIVE BAYESIAN FILTERING is a model developed by Alex Beutel and collaborators to predict user preferences in online recommendation systems. The model aims to fit user ratings data, understand user behavior, and detect spam. It utilizes Bayesian probabilistic matrix factorization and
0 views • 49 slides
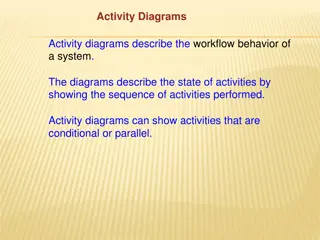
Understanding Activity Diagrams and State Chart Diagrams
Activity diagrams describe the workflow behavior of a system by showing the sequence of activities performed, including conditional and parallel activities. Elements such as Initial Activity, Symbol Activity, Decisions, Signals, Concurrent Activities, and Final Activity are depicted in these diagram
0 views • 10 slides
Understanding Email Campaigns in Internet Marketing
Email campaigns have transformed communication by allowing easy distribution of messages and documents worldwide within seconds. They can take various forms like direct emails, newsletters, and press releases. This chapter explores different types of email campaigns, including direct mail vs. direct
0 views • 25 slides
Understanding Classification in Data Mining
Classification in data mining involves assigning objects to predefined classes based on a training dataset with known class memberships. It is a supervised learning task where a model is learned to map attribute sets to class labels for accurate classification of unseen data. The process involves tr
0 views • 26 slides
Email Best Practices for Postfix and Dovecot Setup
In this guide, Kevin Chege discusses best practices for configuring email servers with Postfix and Dovecot. Topics covered include setting up SPF records, reverse records, using anti-spam and anti-virus software, implementing greylisting, and ensuring well-formatted messages to reduce spam. Learn ho
0 views • 38 slides
ARPA Reporting and Compliance Guidelines for Recipients
This content provides important information regarding ARPA reporting and compliance requirements for recipients of government funding. It covers topics such as spam/phishing warnings, recipient tiers, resources for reporting, Treasury's disclaimer on project approval, and guidance on using the Treas
0 views • 21 slides
Determining Email Spam using Statistical Analysis and Machine Learning
The discussion revolves around classifying spam from ham emails by analyzing word frequencies. Various techniques such as Logistic Regression, Linear Discriminant Analysis, and 10-fold Cross-Validation are employed to achieve this goal. Statistical analysis and machine learning models like LDA and L
0 views • 8 slides
Proactive Network Protection Through DNS Security Insights
Exploring proactive network protection methods using DNS, security challenges, botnet threats, firewall management, malware controls, and DNS-based malware control. Discussions on DNS security vulnerabilities, DNSSEC, threat intelligence, machine learning, and best practices like RPZ for DNS protect
0 views • 29 slides
Uncovering Social Network Sybils in the Wild
Unveiling the presence of malicious Sybil accounts on large online social networks like Renren, this research delves into understanding Sybil behavior in the wild to enhance detection mechanisms. Leveraging ground-truth data on over 560K Sybils on Renren, a measurement-based real-time Sybil detector
0 views • 18 slides
Insights on Web Spamming Techniques and Moroccan Oil Benefits
The article discusses various web spamming techniques, emphasizing the importance of authentic content. It also highlights the benefits of Moroccan Oil for hair care, addressing common concerns and misconceptions. The content delves into the taxonomy of techniques used, showcasing advancements in th
0 views • 24 slides
Passive DNS And The Halting Problem by Joe St. Sauver, Ph.D.
Exploring the interplay between Passive DNS and the Halting Problem, this document presents insights shared by Dr. Joe St. Sauver at B|Sides Vancouver, BC in March 2015. The detailed presentation covers various aspects such as the dynamic format of the session, unique slide style, author's backgroun
0 views • 84 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Understanding Computer System Security Threats and Malware Types at Eshan College of Engineering
Explore the world of computer system security threats and malware at Eshan College of Engineering through insightful presentations prepared by Associate Professor H.K. Sharma from the CS Department. Learn about security threats like intrusion, phishing, spyware, spam, and malware categories such as
0 views • 13 slides
Understanding Success in ML Systems through Goals and Metrics
Explore the importance of setting good goals in ML systems, the connection between model properties and user outcomes, and the impact of achieving desired outcomes in SMS spam detection. Learn about defining success, types of goals, and ensuring measurable and achievable objectives for ML implementa
0 views • 11 slides
Understanding the Origin and Impact of the Internet
The Internet, a global network of networks, connects individuals, businesses, and organizations worldwide. This session explores the inception of the Internet, its significance, major uses, and how to manage spam effectively. Learn about its origins, advantages, and disadvantages to grasp its role i
0 views • 54 slides
Understanding Consumer Rights and Responsibilities
Explore key concepts such as legal voting age, lemon laws, budget surplus, and more in relation to consumer protection and government accountability. Learn about identifying and handling issues like spam, pyramid schemes, slander, and counterfeit drugs.
0 views • 29 slides
Safeguarding Devices and Edge Computing: A Responsive Anti-Scam Approach
The article discusses the prevalence of scamming in the digital landscape, emphasizing the financial harm and security risks it poses. It explores the challenges in detecting scam messages, particularly in short messaging platforms, and proposes a comprehensive and adaptive strategy to address this
0 views • 20 slides
Updates on ABS and Anti-Spam Efforts in Japan
The content discusses the challenges faced by the ABS committee, the need for new members due to changing dynamics, and the apology for lack of communication. It also highlights significant changes in Japan regarding Anti-Spam regulations, forming an Anti-Spam council to combat abuse. The post empha
0 views • 5 slides