Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
3 views • 26 slides
Understanding SHA-256 Algorithm and History
SHA-256 is a secure hashing algorithm that produces 256-bit hash values and is more secure than MD5, SHA-0, and SHA-1 due to fewer collisions. Created in 2001 by the NSA, it is widely used in various applications like cryptocurrency, SSL certificates, and blockchain. This summary provides insights i
0 views • 17 slides
Best Acupuncture in Tanjong Pagar
If you\u2019re looking for an Acupuncture in Tanjong Pagar, contact La Guerison TCM Pte Ltd \u7597\u6108\u4e2d\u533b. They offer many services promoting overall well-being and healing. They specialize in various TCM therapies including tuina massage, acupuncture, cupping, TCM ear-picking services, G
0 views • 6 slides
Get the Best Acupuncture in Tanjong Pagar
Get the Best Acupuncture in Tanjong Pagar at Healing Health TCM Therapy Pte Ltd! Specializing in Health, Beauty & Body Wellness, their team of registered TCM physicians and skilled therapists are dedicated to providing top-quality medical consultation and treatments. They offer a range of services i
0 views • 6 slides
Start Your Healthcare Career_ CNA Online Course by CNA
Open a new chapter in your life, and work towards filling a vital niche in the growing healthcare sector. You should check a course like the CNA online course provided by CNA.School if you are in need of such a class. This Course will equip you with all imaginable knowledge and practical skills that
1 views • 3 slides
Access Free CNA Classes Online and Start Your Career
Do you want to make a leap towards the healthcare industry but do not want to spend a lot of money? CNA.School provides free CNA classes online for everyone interested in learning more. These courses offer an accessible and affordable means of receiving the training and passing the tests required to
16 views • 8 slides
Versatile 256 276 II Tractor Operator’s Manual Instant Download (Publication No.42025620)
Please open the website below to get the complete manual\n\n\/\/
0 views • 22 slides
Versatile 256 276 Tractors Operator’s Manual Instant Download (Publication No.42025621)
Please open the website below to get the complete manual\n\n\/\/
0 views • 20 slides
Versatile 2360 Loader (Serial Number 434100 and above) for 256 276 276II and 9030 Tractors Operator’s Manual Instant Download (Publication No.43236014)
Please open the website below to get the complete manual\n\n\/\/
0 views • 11 slides
Caterpillar Cat 416E BACKHOE LOADER (Prefix SHA) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 32 slides
Caterpillar Cat 416E BACKHOE LOADER (Prefix SHA) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 32 slides
Understanding AES Encryption Algorithm and Its Implementation
Learn about the Advanced Encryption Standard (AES) algorithm - a NSA-approved NIST standard encryption method. Explore how AES works, its key rounds, SubBytes, ShiftRows, MixColumns operations, and its optimization for embedded systems and small memory devices. Discover the importance of secure cryp
0 views • 14 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Proposal for New 802.11bd 20MHz Mode for Enhanced ITS Interoperability
The document discusses the necessity of a new 802.11bd 20MHz mode for improved interoperability within Intelligent Transportation Systems (ITS) due to limitations with current Wi-Fi channels and the scope of 256-QAM modulation. It presents proposals approved by the Car-2-Car Communications Consortiu
0 views • 8 slides
Understanding Character Sets in Computer Science
Alphanumeric characters, special symbols, and control characters play crucial roles in representing data through character sets like ASCII and Unicode in computer science. ASCII, with its 7-bit binary codes, represents 128 characters, while Extended ASCII allows for 256 characters. Unicode covers a
1 views • 12 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Maximizing HDL Repository Management Efficiency with Hog Toolset
Explore the benefits of using Git for HDL repositories with Hog toolset. Ensure reproducibility and absolute control of HDL files, constraint files, and settings. Learn how to embed Git SHA into firmware registers automatically for traceability. With Hog, developers can integrate version control sea
1 views • 22 slides
MC-OOK Symbol Design for IEEE 802.11 - March 2018
Introducing MC-OOK waveforms with low peak-to-average power ratio for IEEE 802.11, utilizing 256-QAM modulation and 4 MHz bandwidth. The design methodology involves generating time-domain waveforms, transforming to frequency domain, and proposing symbols with and without DC subcarriers. Detailed sym
0 views • 20 slides
Overview of Git Commit Workflow
Explore the Git Commit Workflow, including commands like git log, git diff, git status, git add, git commit, and git show. Learn about the importance of the .git folder in a repository and how to identify commits using their SHA-1 hashes.
0 views • 23 slides
Overview of SMX Algorithm and AES Encryption Standard
The SMX Algorithm presents a fresh approach to the avalanche effect in the Advanced Encryption Standard (AES). Initially developed to overcome the limitations of the Data Encryption Standard (DES), AES boasts improved security and efficiency, supporting key lengths of 128, 192, and 256 bits. The AES
3 views • 19 slides
Kompetisi Fungsi Hash NIST (SHA-3): Proses Pemilihan Finalis dan Detail Desain
Seperti sejarah AES, National Institute of Standards and Technology (NIST) menyelenggarakan kompetisi terbuka untuk mengembangkan fungsi hash baru yang disebut SHA-3. Kompetisi ini diadakan dari tahun 2007 hingga Oktober 2012. Proses pemilihan terdiri dari 2 putaran dan babak final dengan total 64 s
0 views • 17 slides
Freelance digital marketing strategist in Calicut
Iam Febin Sha Freelance Digital Marketing strategist in Calicut,Kerala,India I build Custom Websites that are both Playful and Efficient and I help Grow your business With Creative Solutions \n\/\/febinsha.com\/\n
0 views • 8 slides
Computer Forensics: Capturing and Verifying Evidence
This guide focuses on the process of capturing and verifying digital evidence in computer forensics. Topics include creating forensic images of hard drives, using forensically sound methods, imaging internal hard drives, utilizing hardware write blockers, different types of forensic images, hashing
0 views • 28 slides
Powercor Industry Forum Audit Results and Trends Analysis
Audit results and trends analysis reveal that there were 256 audits completed, with 50 being re-audits. Additional resources were acquired to meet industry demand, but audit volumes in Q4 did not meet forecast. Turnaround times improved with the deployment of more auditor resources. Trends show issu
0 views • 8 slides
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
Highlights of ICA Journalism Studies Division Business Meeting 2014 in Seattle
Agenda highlights included discussions on upcoming elections, ways to engage members, presentation of awards, introduction of new membership categories, proposed changes to board representation, establishment of guidelines for affiliate journals, and the creation of new divisions and interest groups
0 views • 15 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Understanding Interrupt Processing Sequence in X86 Processors
X86 processors have 256 software interrupts, functioning similarly to a CALL instruction. When an INT n instruction is executed, the processor follows a sequence involving pushing the flag register, clearing flags, finding the correct ISR address, and transferring CPU control. Special interrupts lik
0 views • 10 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Evaluation of Ed25519 Cryptography Performance in DNSSEC Validation
Edwards Curve Cryptography, specifically the Ed25519 algorithm, offers faster performance and high crypto density compared to other algorithms. This evaluation study compares key sizes, processing times, and validation support for Ed25519, ECDSA P-256, RSA-2048, and RSA-4096 in DNSSEC validation sce
0 views • 19 slides
Understanding EIGRP Network Protocol
EIGRP (Enhanced Interior Gateway Routing Protocol) is a network protocol that facilitates efficient information exchange among routers. Evolving from IGRP, EIGRP allows interoperability and can be used for IP, AppleTalk, and Novell NetWare networks. EIGRP metrics scale IGRP metrics by a factor of 25
0 views • 13 slides
Comparative Analysis of Health Systems: Insights from SHA and Irish Health Policy
This policy researcher's perspective delves into the key roles of SHA and Irish health policy, exploring similarities, differences, and the relationship between expenditure levels, service provision, financing patterns, and health outcomes. Through detailed analyses, the paper highlights the importa
0 views • 9 slides
IPv6 Public Policy Considerations - Addressing the Global IP Address Shortage
In light of the global shortage of IPv4 addresses, there is a pressing need for a fair policy for the allocation of remaining addresses. The rapid growth of the Internet has further increased demand for IP addresses, with IPv4 expected to run out soon. The deployment of IPv6 has become a critical is
0 views • 23 slides
Fiat Kobelco E235SR Evolution Excavator Service Repair Manual Instant Download (Print N. 604.13.256)
Please open the website below to get the complete manual\n\n\/\/
0 views • 14 slides
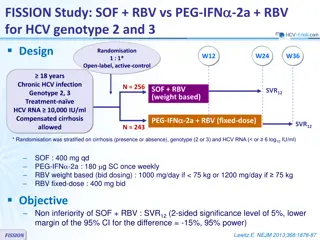
Comparison of SOF+RBV vs PEG-IFN-2a+RBV for HCV Genotype 2 and 3 Treatment
FISSION Study compared the efficacy of SOF+RBV and PEG-IFN-2a+RBV for HCV genotypes 2 and 3 in treatment-naive patients with chronic HCV infection. The study included 256 participants in the SOF+RBV group and 243 in the PEG-IFN-2a+RBV group. The primary objective was to determine the non-inferiority
0 views • 6 slides
Top 10 Tips for Buying a Used Car_ Navigate the Market Like a Pro
Purchasing a used car can be an excellent investment, offering value for money and a wide variety of options. However, navigating the used car market requires caution to avoid potential pitfalls. Whether you\u2019re buying in Abu Dhabi, Dubai, or Sha
0 views • 4 slides
Expert Guide_ Top 10 Tips for Buying a Used Car Like a Pro
Purchasing a used car can be an excellent investment, offering value for money and a wide variety of options. However, navigating the used car market requires caution to avoid potential pitfalls. Whether you\u2019re buying in Abu Dhabi, Dubai, or Sha
0 views • 4 slides