BUY PREPAID CARD ONLINE — globcoff.com
Buy Pre-paid Cards that make it simple and convenient to give gifts, recognize achievement, and inspire team members. Meal Cards, Gift Cards, Rewards Cards, and Smart Pay Cards are all options. Prepaid cards have a variety of advantages, such as the ability to instantaneously make purchases using Gi
2 views • 4 slides
Buy Clone Cards Online - Telegram -@Eurneosbillsnotes
Order Clone ATM Cards dump with the Pin Sell CVV, CC full. All cards are verified and cash out is sure and secured with a secure and safe method Dumps Track 1 2 with pin 101, 201 worldwide dumps With Pin CVV Dumps Shop. Dumps Pin\u2013CCV Shop PRICE: SKIMMER PIN PAD (OR CAMERA PANEL) ATM SKIMMERS
3 views • 2 slides
BUY MASTERCARDS CLONE ATM CARDS ONLINE - @EUROSBILLSNOTES
Buy Mastercards Clone ATM Cards dump with the Pin Sell CVV, CC full. All cards are verified and cash out is sure and secured with a secure and safe method Dumps Track 1 2 with pin 101, 201 worldwide dumps With Pin CVV Dumps Shop. Dumps Pin\u2013CCV Shop PRICE: SKIMMER PIN PAD (OR CAMERA PANEL) ATM
3 views • 2 slides
Guardians of Collection Enhancing Your Trading Card Experience with the Explorer Sleeve Bundle [4-pack]
For trading card collectors, the art of preserving and showcasing their valuable cards is a crucial part of the hobby. Trading cards represent not just collectibles but also pieces of history, personal memories, and sometimes significant investments. Prismatic Defender\u00ae, a name known for innova
1 views • 2 slides
CWRU PCard Training
Explore the intricacies of Procurement Cards at Case Western Reserve University (CWRU), including the types of cards offered, responsibilities of cardholders, guidelines for card issuance, and usage scenarios. Learn about the PCard, DCard, and other specialized cards available, their acceptance, and
1 views • 32 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Guided Approach to Developing Investigative Skills with Card Set
Explore a card set designed to enhance investigative skills, comprising different types of cards - DBE Cards, Research Cards, and Reflection Cards. Each phase of the investigative process in the DBE cycle is supported by specific cards, aiding in questioning, knowledge generation, ideation, prototyp
8 views • 21 slides
What Types of Data Can Be Stored on Proximity Smart Cards_ What Types of Data Can Be Stored on Proximity Smart Cards
Unsure what data proximity cards hold? Explore common types of information stored on these contactless cards and their security features.
1 views • 4 slides
What Are Proximity Cards Used For?
Proximity cards do more than unlock doors! Learn about surprising applications for these versatile cards, from secure payments to library checkouts
2 views • 5 slides
Who Uses Proximity Cards?
Unsure who uses proximity cards? Used for access control & beyond, explore the wide range of industries that rely on these contactless cards for security and convenience
1 views • 5 slides
Buy Custom USB Business Cards to Empower Your Brand
Are you looking for fantastic giveaways for corporate events? The custom USB business cards are the perfect solution. \n\nThey are designed to fit easily in a wallet and are always handy when needed. The large surface area allows for prominent branding, making your logo and message more impactful.\n
2 views • 5 slides
Mastering Credit and Debt in Head Start Program
Understand the complexities of credit and debt to make informed financial decisions. Learn about different types of credit, pros and cons of credit cards, debit cards, prepaid cards, and secured credit cards. Gain insights on how to manage your finances effectively and build a strong credit history
0 views • 29 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Everything You Need to Know About TOTUM Cards
TOTUM Cards, formerly NUS Cards, offer student discounts and exclusive deals. They act as proof of student status and provide access to a variety of discounts on shopping, travel, and more. With ISIC verification, you can also benefit from discounts abroad. The card pays for itself quickly with savi
0 views • 6 slides
Understanding Credit Cards: A Beginner's Guide
Explore the basics of credit cards, including how they work, differences from debit and prepaid cards, obtaining one, and building credit. Learn about credit character, revolving credit, and tips for getting approved for a credit card. Discover the importance of good credit and income when applying
0 views • 20 slides
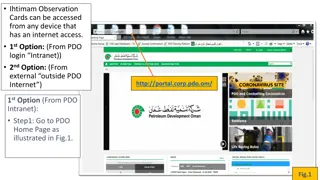
Accessing Ihtimam Observation Cards: Step-by-Step Guide
Learn how to access Ihtimam Observation Cards from any device with internet access, whether within PDO's intranet or externally. Follow detailed steps provided for both options, including selecting behaviors, inputting observations, and submitting cards.
0 views • 8 slides
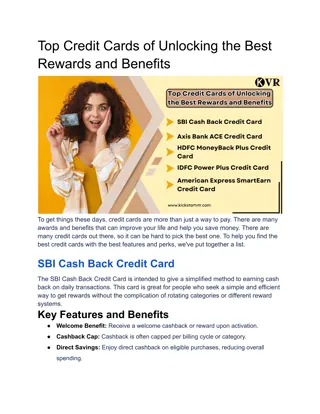
Top Credit Cards of Unlocking the Best Rewards and Benefits
To get things these days, credit cards are more than just a way to pay. There are many awards and benefits that can improve your life and help you save money. There are many credit cards out there, so it can be hard to pick the best one. To help you
15 views • 4 slides
Effective Revision Techniques Using Flash Cards
Utilize the power of revision or flash cards to enhance your learning process. Testing yourself is crucial for reinforcing material. Create color-coded cards with clear titles, facts on one side, questions on the other, and diagrams to aid in memory recall. Customizing your own cards fosters better
0 views • 8 slides
Exploring Vowel Teams Word Cards for Language Development
Discover a variety of word cards featuring vowel teams like ai, ay, au, aw, ee, a, e, oa, w, ow, ew, o, ue. These cards provide engaging opportunities for learners to practice reading and spelling words with different vowel combinations. Improve language skills by exploring and using these word card
1 views • 20 slides
Enhancing Vocabulary with Long Spellings Word Cards
Improve your vocabulary with this collection of long spelling word cards including words like bike, mine, flight, night, and many more. Enhance your language skills by practicing spelling and pronunciation with these visually appealing cards.
0 views • 4 slides
Enhancing Resident Observations with Shift Cards in Outpatient Clinic
Explore the utility of Shift Cards in providing real-time feedback to residents in the outpatient clinic setting. Learn how to observe, provide feedback, and engage with the Clinical Competency Committee effectively using this innovative tool. Discover the benefits, learning objectives, and audience
0 views • 16 slides
Digital Payment Methods and Security Issues Explained
Digital payment methods like credit and debit cards, e-wallets, and smart cards are becoming increasingly popular in a cashless economy. This article discusses the types of digital payment methods available, such as credit and debit cards, and addresses security issues related to using these forms o
2 views • 16 slides
American History Flash Cards
This collection of American History flash cards covers topics such as why the colonists fought the British, who wrote the Declaration of Independence, and who authored the Federalist Papers. It also encourages students to study, take notes, ask questions, and review with a friend. Engage with these
1 views • 8 slides
Phonogram Word Cards for Teaching Phoneme-Grapheme Correspondences
Phonogram Word Cards include lists of words with the same phonogram, such as -ub, -uck, -ud, -udge, -ue, -uff, -ug, -um, -ump, -un, -unch, and -ung. These cards can be used in teaching new phoneme-grapheme correspondences, review games, and various literacy activities. Each set of words focuses on a
0 views • 19 slides
Hands-On Geometry Activity: Transforming Shapes with Mini Whiteboards and Grids
Engage students in a pair activity using mini whiteboards with grids to explore transformations of shapes. Students will work on Shape cards linked by Arrow cards, turning them into a network to understand translations, reflections, and rotations. Consumable and reusable resources are required for t
0 views • 11 slides
Avoco's Cloud-Based Information Card Selector: Enhancing Usability and Security
Avoco's Cloud-Based Information Card Selector is a leap forward in Information Card usability, offering benefits such as universal access to Information Cards, zero footprint for end users, and enhanced security features. The platform allows for easy creation, import, and backup of cards, as well as
0 views • 29 slides
Football Cards and Offences Statistics as of July 15
This data presents detailed statistics on football cards and offences recorded as of July 15. It includes information on red cards, total cards, types of offences, distribution of cards, and the breakdown by competition. The visuals provide insights into the number of cards issued, the nature of off
0 views • 7 slides
Benefits of Using Prepaid Cards for Direct Payments in the Public Sector
Prepaid cards offer a range of advantages in the public sector, such as financial inclusion, ease of use, cost savings, and improved financial management. They are widely adopted by local authorities, clinical commissioning groups, and various organizations for direct payments, leading to enhanced s
0 views • 10 slides
EPC RFID Tag Security Weaknesses and Defenses: Passport Cards, Enhanced Driver's Licenses, and Beyond
Explore the vulnerabilities in EPC RFID tag security related to passport cards, enhanced driver's licenses (EDLs), and more. Learn about cloning risks, defensive strategies, and experimental evaluations of security measures for these identification documents.
0 views • 22 slides
Teen Mating Game - Relationship Situation Cards Scenarios
Explore various relationship scenarios depicted through situation cards in the Teen Mating Game. From annoying habits to revelations about sexuality, cheating, financial dynamics, health issues, distance challenges, personal preferences, familial opinions, substance use, and more, these cards offer
0 views • 17 slides
Creative Word Play Storytelling Kit
Unleash your creativity with the Creative Word Play Storytelling Kit using word cards. Safely cut out and sort the word cards into piles representing different parts of speech. Create unique sentences by combining cards from each pile and let your imagination run wild as you build stories. Expand th
0 views • 6 slides
Understanding Compound Cards for Maximum Information Utilization
Compound cards offer a versatile way to present and manage information in a structured manner. They are akin to workbenches but in a compact card format, allowing for efficient display of details across 2 to 4 sections. Learn how to define, create, and utilize compound cards effectively to enhance i
0 views • 31 slides
Best Invitation Cards Online to Make Your Special Day Memorable
Universal Wedding Cards focuses on helping you find the best options to Buy Designer Wedding Cards Online, ensuring your special day starts with the perfect invitation.\u200b Explore more @ \/\/ \/
1 views • 9 slides
Teen Mating Game Discussion Cards by School Health Team
Explore the Teen Mating Game Discussion Cards created by the School Health Team in July 2022. The cards provide insights on behavior and communication when someone is "into" or not "into" someone else. Discover the cues and actions that indicate interest or lack thereof in a potential partner or cru
0 views • 5 slides
Probability Calculations for Events with Cards, Dice, and More
Explore various scenarios involving probabilities with standard decks of cards, dice, and other items. From determining the likelihood of pulling specific cards from a deck to rolling dice and flipping coins, learn about independent and dependent events, as well as the rules governing their probabil
0 views • 7 slides
Discover a Fun Collection of Swap Cards: Colors, Numbers, and Drinks Preferences
Dive into the world of swap cards featuring various themes such as colors, numbers, and favorite drinks. Explore the vibrant images showcasing different aspects of the swap card collection, from colorful designs to numerical patterns. Uncover the excitement of swapping cards with friends and sharing
0 views • 4 slides
PrAACtical AAC Topic Cards for Improved Communication
Using the PrAACtical AAC Topic Cards designed by www.PrAACticalAAC.org can help individuals with unclear speech to indicate the topic of their message before communicating the actual content. These cards assist in conveying intent effectively and enhancing communication. The cards cover a range of c
0 views • 10 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
All About Credit Cards: A Comprehensive Guide
Explore the world of credit cards, from understanding the basics to managing credit wisely. Delve into the advantages and disadvantages, learn about different types of credit cards, and discover how to use credit cards responsibly. Discuss whether high school students, college students, and adults s
0 views • 36 slides
Understanding the Generalized Pigeonhole Principle in Discrete Math
The Generalized Pigeonhole Principle is illustrated through an example involving selecting cards from a deck. By strategically grouping the cards, we determine the minimum number needed to guarantee at least three cards of the same suit are chosen. Additionally, the process is applied to finding the
1 views • 5 slides


![Guardians of Collection Enhancing Your Trading Card Experience with the Explorer Sleeve Bundle [4-pack]](/thumb/3698/guardians-of-collection-enhancing-your-trading-card-experience-with-the-explorer-sleeve-bundle-4-pack.jpg)