Boost Your Business with SMS gateway for transactions : A Overview
\"Discover how leveraging an SMS gateway for transactions can propel your business forward in this comprehensive overview. Explore the benefits of seamless communication, enhanced customer engagement, and streamlined transactions. Unlock the potential to boost sales, improve efficiency, and cultivat
1 views • 6 slides
Taxation and Reporting of Futures and Options (F&O) Transactions
Explore the taxation aspects and reporting requirements related to Futures and Options (F&O) transactions. Learn about the types of F&O transactions, relevant heads of income for reporting income/loss, and the provisions of Section 43(5) of the Income Tax Act, 1961, defining speculative tran
2 views • 24 slides
Database System Concurrency Control and Transactions Overview
Studying relational models, SQL, database system architecture, operator implementations, data layouts, and query optimization laid the foundation for advanced topics like Concurrency Control and Recovery. Discover how transactions group related actions, ACID properties ensure data integrity, and the
0 views • 57 slides
Delete Expense Transactions in QuickBooks Online?
Delete Expense Transactions in QuickBooks Online?\nKeeping clean books in QBO requires managing expenses effectively. This includes deleting unnecessary transactions. Confused about how? Don't worry! This guide simplifies the process. Learn when to delete, what to consider beforehand, and follow the
1 views • 3 slides
Taxation of F&O Transactions under Indian Income Tax Law
This content discusses the taxation of Futures and Options (F&O) transactions in India under the Income Tax Act of 1961. It covers the types of F&O transactions, relevant heads of income for reporting income or loss, and the provisions of Section 43(5) related to speculative transactions. The articl
1 views • 24 slides
Accounting for Independent Branches: Salient Features and Transactions
Independent branches maintain separate sets of accounts and carry out business transactions autonomously. The accounting system of an independent branch involves double entry bookkeeping, reconciliation of accounts between the branch and head office, and recording transactions like dispatch of goods
2 views • 10 slides
Legal Implications of the Digital Economy in Malawi
Explore the legal implications of the digital economy in Malawi as discussed at the ICAM Annual Lakeshore Conference. Topics include the Electronic Transactions and Cyber Security Act, principles of implementation, Malawi CERT, data privacy, and the significance of the digital economy in transformin
0 views • 44 slides
Essential Knowledge for Sales & Finance Transactions
Understanding the intricacies of titles in sales and finance transactions is crucial to avoid costly mistakes and ensure smooth processes. This guide highlights the importance of titles, handling trade-in packets, and managing drive-away transactions effectively. It emphasizes the significance of ve
0 views • 7 slides
UCPath vs KFS GL Reconciliation Tips & Audit Messages
Explore essential tips for reconciling UCPath and KFS GL transactions, including checking if transactions were posted, identifying period mismatches, and understanding audit messages in DOPE reports. Learn how to handle unposted transactions and recognize future or past period discrepancies to ensur
1 views • 10 slides
Texas Standard Electronic Transactions (TX.SET) Overview
Texas Standard Electronic Transactions (TX.SET) provide an interactive platform for various transactions involving ERCOT and non-ERCOT entities. The TX.SET Version 4.0 includes a range of transaction names and documents related to service orders, outages, invoices, customer information maintenance,
0 views • 33 slides
Blockchain Technology and Its Applications
Blockchain technology enables secure, decentralized transactions by utilizing open ledgers and cryptographic techniques. It eliminates the need for intermediaries, reduces fees, enhances privacy, and provides a permanent record of transactions. With a focus on concepts like open ledger, history, net
1 views • 35 slides
Compliance Obligations and PAN Requirements for Financial Transactions
This outreach program by the Directorate of Income Tax in Nagpur, in collaboration with the Nagpur Branch of WIRC of ICAI, focuses on effective compliance with Statement of Financial Transactions (SFT). It covers PAN compliance obligations, forms, and penalties for non-compliance related to specifie
1 views • 14 slides
Efficient Submission of Forms Solution via EDI Transactions
Streamlining the submission of Forms Solution to the Bureau through mandated EDI transactions. Claims adjusters must provide injured workers with a copy of the form. Key features include form generation via accepted EDI transactions, avoiding paper versions, and ensuring timely filing. Details on Ag
0 views • 16 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Quantum Money Solution for Scalability Issue in Blockchain
Addressing the blockchain scalability problem, this study introduces a quantum money solution by Andrea Coladangelo and Or Sattath. It explores the challenges of resource-intensive transactions in traditional blockchain systems and proposes the use of public key quantum money as a secure and efficie
2 views • 24 slides
Benefits of E-Banking and Its Impact on Customer Service
E-banking provides various benefits such as offering extra service channels, convenience, flexibility with online banking, reduction in cash transactions, self-inquiry facilities, remote and anytime banking, branch networking, and electronic data interchange. These benefits enhance customer service
0 views • 22 slides
Financial Transactions Summary for Mr. Kamal Sahan Gamage
Mr. Kamal Sahan Gamage conducted two financial transactions at the Gampaha branch of Test Finance Company. On 10/08/2023, he deposited 5 million LKR into his account (LFC_ACC111). On 10/10/2022, he withdrew 1 million LKR via a cash cheque from the collection account (COL_ACC100). Both transactions w
0 views • 24 slides
High-Performance Transactions for Persistent Memories
Explore the optimization of transactions for persistent memories, focusing on ordering constraints, synchronous vs. deferred commit transactions, persistency models, and performance evaluation. The study aims to improve transaction performance in the presence of high persistent memory latencies by m
0 views • 26 slides
Building Effective Board Memos for City Transactions
Guidance on building a board memo for the Board of Estimates, a public board overseeing city transactions. Learn about the reviewing agencies involved, such as the Law Department, Dept. of Finance/BBMR, MWBOO, and Pre-Audits, and their roles in the approval process. Follow their guidelines to ensure
0 views • 18 slides
360 Control Manager & Cardholder Training Commercial Card Payment Solutions
Explore how 360 Control Manager provides an online Employee Expense Reporting tool for coding transactions related to the company's Visa business cards. Learn how to access the system, code transactions, split a transaction, add comments, attach receipts, and follow a 3-step process for coding, revi
0 views • 18 slides
Secure Method of Information Exchange: Overview of Hub Concept & Prototype
This document presents an overview of the Hub Concept & Prototype for Secure Method of Information Exchange (SMIE) developed in April 2013 by New Zealand and the USA. It discusses drivers, ePhyto transmission options, Direct NPPO to NPPO ePhyto exchange, Hub/Cloud communication, security mechanisms,
0 views • 20 slides
Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
Google Spanner: A Distributed Multiversion Database Overview
Represented at OSDI 2012 by Wilson Hsieh, Google Spanner is a globally distributed database system that offers general-purpose transactions and SQL query support. It features lock-free distributed read transactions, ensuring external consistency of distributed transactions. Spanner enables property
1 views • 27 slides
Optimizing Read-Only Transactions for Performance
Explore the nuances of performance-optimal read-only transactions in distributed storage systems. Focus on achieving high throughput and low latency while considering algorithmic properties and engineering factors. Learn how coordination overhead affects performance and strategies to design efficien
0 views • 42 slides
Ensuring Security and Trust in Online Transactions
Establishing trust and security is crucial for online transactions. Guidelines include verifying company legitimacy, safeguarding personal information, and using secure payment methods. In case of doubt, research the company and its reputation. Tips for secure transactions are highlighted, emphasizi
0 views • 6 slides
Simplifying Loan Transactions for Better Management
Explore the new functionality introduced for handling loan transactions easily, distinguishing between loan and lease agreements, and designating ownership effectively. Learn about different options for recording ownership changes and managing transactions seamlessly.
0 views • 27 slides
Financial Transactions and Budgetary Control Overview
The content delves into requirements and configuration management for general ledger teams, chart of accounts reporting, budget references, fund management, commitment control, and budgetary rules. It emphasizes the establishment of budgets at various levels of the account hierarchy and details the
0 views • 49 slides
Advanced Database Transactions and Recovery Concepts
Explore the key concepts of transactions and recovery in advanced databases. Topics include durability, input/output operations, expanded transactions, logging approaches, and log records. Learn about undo logging, redo logging, and undo/redo logging techniques for system crash recovery.
0 views • 36 slides
Distributed Database Management and Transactions Overview
Explore the world of distributed database management and transactions with a focus on topics such as geo-distributed nature, replication, isolation among transactions, transaction recovery, and low-latency maintenance. Understand concepts like serializability, hops, and sequence number vectors in ma
0 views • 17 slides
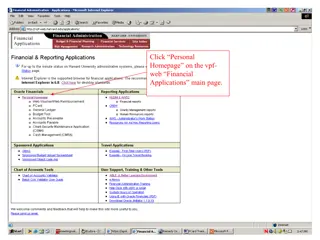
Guide to Reviewing Purchases and Transactions on the VPF Web Financial Application
This comprehensive guide provides step-by-step instructions on how to review purchases and transactions on the VPF Web Financial Application. From logging in to reviewing transactions and adding business purposes, this guide covers all aspects in detail with accompanying visuals.
0 views • 15 slides
Database Transactions in SQL
Database transactions in SQL ensure data integrity and consistency by allowing users to group SQL commands into atomic units that can be committed or rolled back as needed. Learn about the ACID properties of transactions, autocommit mode, and how to create and manage transactions effectively.
1 views • 29 slides
Overview of Redomiciliation Transactions and Section 7874 Implications
Section 7874 imposes restrictions on domestic corporations becoming owned by foreign entities with the same or similar shareholder base. It outlines tests triggering adverse consequences and discusses self-inversion transactions, tax considerations, and cross-border combinations. Notably, substantia
0 views • 8 slides
Foreign Exchange Management Act, 1999: Overview and Structure
The Foreign Exchange Management Act (FEMA) of 1999 replaced the Foreign Exchange Regulation Act (FERA) and empowers the Reserve Bank of India to regulate foreign exchange transactions. FEMA imposes restrictions on foreign exchange dealings and requires transactions to be conducted through authorized
4 views • 6 slides
Analysis of EAST Retention Impact on Interlibrary Loan Transactions
Analyzing the impact of retention commitments on Interlibrary Loan (ILL) transactions, this study delves into the circulation patterns of retained items, digital surrogates utilization, and speed of delivery considerations. Key findings include a significant proportion of transactions with retention
0 views • 11 slides
Taxation Guidelines for Share and Derivative Transactions by CA Mahavir Atal
Guidelines by CA Mahavir Atal regarding taxation of share and derivative transactions, including determining business income vs. capital gain, treatment of shares as stock-in-trade, maintaining separate portfolios, and the classification of transactions as either business or investment. The circular
0 views • 31 slides
Enhancing Cloud Data Transactions with Deuteronomy
Deuteronomy aims to provide ACID transactions for cloud data, addressing the current limitations of transactions in cloud environments. The motivation, technical aspects, and implementation of Deuteronomy are discussed, highlighting the need for efficient transaction support across the cloud. Throug
0 views • 20 slides
Distributed Transactions in Spanner: Insights and Mechanisms
Spanner, a strictly serializable system, leverages TrueTime for timestamping to enforce the invariant between transactions. It ensures efficient read-only transactions and multi-shard transactions. Mechanisms like 2PL, 2PC, and (Multi)Paxos contribute to Spanner's fault tolerance and scalability. Le
0 views • 21 slides
Kaspa Wallet- The Most User-Friendly and Secure Option for Kaspa Transactions
Kaspa Wallet- The Most User-Friendly and Secure Option for Kaspa Transactions
1 views • 2 slides
Get the Best Bank Flashing Software and More for Secure Transactions
Get the Best Bank Flashing Software and More for Secure Transactions
0 views • 3 slides
Secure and Convenient Transactions with KasWare Wallet
Secure and Convenient Transactions with KasWare Wallet
0 views • 2 slides