Intra-Distillation for Parameter Optimization
Explore the concept of parameter contribution in machine learning models and discuss the importance of balancing parameters for optimal performance. Introduce an intra-distillation method to train and utilize potentially redundant parameters effectively. A case study on knowledge distillation illust
8 views • 31 slides
Parameter and Feature Recommendations for NBA-UWB MMS Operations
This document presents recommendations for parameter and feature sets to enhance the NBA-UWB MMS operations, focusing on lowering testing costs and enabling smoother interoperations. Key aspects covered include interference mitigation techniques, coexistence improvements, enhanced ranging capabiliti
3 views • 18 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
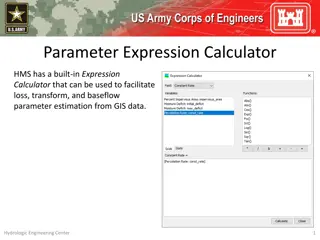
Parameter Expression Calculator for Efficient Parameter Estimation from GIS Data
Parameter Expression Calculator within HEC-HMS offers a convenient tool to estimate loss, transform, and baseflow parameters using GIS data. It includes various options such as Deficit and Constant Loss, Green and Ampt Transform, Mod Clark Transform, Clark Transform, S-Graph, and Linear Reservoir. U
2 views • 5 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
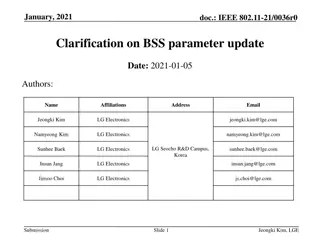
IEEE 802.11-21/0036r0 BSS Parameter Update Clarification
This document delves into the IEEE 802.11-21/0036r0 standard, specifically focusing on the BSS parameter update procedure within TGbe D0.2. It details how an AP within an AP MLD transmits Change Sequence fields, Critical Update Flags, and other essential elements in Beacon and Probe Response frames.
1 views • 11 slides
Understanding Root Locus Method in Control Systems
The root locus method in control systems involves tracing the path of roots of the characteristic equation in the s-plane as a system parameter varies. This technique simplifies the analysis of closed-loop stability by plotting the roots for different parameter values. With the root locus method, de
0 views • 41 slides
Understanding S-Parameter Measurements in Microwave Engineering
S-Parameter measurements in microwave engineering are typically conducted using a Vector Network Analyzer (VNA) to analyze the behavior of devices under test (DUT) at microwave frequencies. These measurements involve the use of error boxes, calibration techniques, and de-embedding processes to extra
0 views • 20 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Exploring Web Application Vulnerabilities and JavaScript Worms
Web applications face pervasive vulnerabilities, with Cross-site Scripting (XSS) leading the threats. The domination of XSS and buffer overruns has enabled the propagation of JavaScript worms, exemplified by infamous cases like Samy's MySpace outbreak. These exploits, marked by obfuscation and polym
1 views • 20 slides
Enhancing Ecological Sustainability through Gamified Machine Learning
Improving human-computer interactions with gamification can help understand ecological sustainability better by parameterizing complex models. Allometric Trophic Network models analyze energy flow and biomass dynamics, but face challenges in parameterization. The Convergence Game in World of Balance
0 views • 12 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Code Assignment for Deduction of Radius Parameter (r0) in Odd-A and Odd-Odd Nuclei
This code assignment focuses on deducing the radius parameter (r0) for Odd-A and Odd-Odd nuclei by utilizing even-even radii data from 1998Ak04 input. Developed by Sukhjeet Singh and Balraj Singh, the code utilizes a specific deduction procedure to calculate radius parameters for nuclei falling with
1 views • 12 slides
Learning to Rank in Information Retrieval: Methods and Optimization
In the field of information retrieval, learning to rank involves optimizing ranking functions using various models like VSM, PageRank, and more. Parameter tuning is crucial for optimizing ranking performance, treated as an optimization problem. The ranking process is viewed as a learning problem whe
0 views • 12 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Comprehensive Malware Analysis Techniques
This detailed guide covers basic static techniques, malware analysis in virtual machines, and basic dynamic analysis. It includes information on static analysis, such as examining payloads without execution, file signatures, and signatures generated via analysis. Additionally, it delves into counter
0 views • 17 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Understanding Weird Machines in Transient Execution
Weird machines refer to models exhibiting unintentional behaviors triggered by adversarial inputs. They serve as computation primitives, enabling tasks like program obfuscation and secret computations. TSX weird machines, computing with time, manipulate cache states through gates like Assign, AND, O
0 views • 18 slides
Efficient Parameter-free Clustering Using First Neighbor Relations
Clustering is a fundamental pre-Deep Learning Machine Learning method for grouping similar data points. This paper introduces an innovative parameter-free clustering algorithm that eliminates the need for human-assigned parameters, such as the target number of clusters (K). By leveraging first neigh
0 views • 22 slides
CEPC Partial Double Ring Parameter Update
The CEPC Partial Double Ring Layout features advantages like accommodating more bunches at Z/W energy, reducing AC power with crab waist collision, and unique machine constraints based on given parameters. The provided parameter choices and updates aim to optimize beam-beam effects, emittance growth
0 views • 14 slides
Foundations of Parameter Estimation and Decision Theory in Machine Learning
Explore the foundations of parameter estimation and decision theory in machine learning through topics such as frequentist estimation, properties of estimators, Bayesian parameter estimation, and maximum likelihood estimator. Understand concepts like consistency, bias-variance trade-off, and the Bay
0 views • 15 slides
Understanding Estimation and Statistical Inference in Data Analysis
Statistical inference involves acquiring information and drawing conclusions about populations from samples using estimation and hypothesis testing. Estimation determines population parameter values based on sample statistics, utilizing point and interval estimators. Interval estimates, known as con
0 views • 41 slides
Sampling and Parameter Fitting with Hawkes Processes
Learn about sampling and parameter fitting with Hawkes processes in the context of human-centered machine learning. Understand the importance of fitting parameters and sampling raw data event times. Explore the characteristics and fitting methods of Hawkes processes, along with coding assignments an
0 views • 20 slides
Linear Classifiers and Naive Bayes Models in Text Classification
This informative content covers the concepts of linear classifiers and Naive Bayes models in text classification. It discusses obtaining parameter values, indexing in Bag-of-Words, different algorithms, feature representations, and parameter learning methods in detail.
0 views • 38 slides
Encrypted Data Deletion for Cloud Storage Servers
Explore the concept of software with certified deletion for private cloud storage servers. Discover how data recoverability is influenced by secret key leaks and encryption scheme vulnerabilities. Learn about techniques for computing on encrypted data and ensuring provable deletion, with a focus on
0 views • 29 slides
Insight into Tuning Check and Parameter Reconstruction Process
Delve into the process of tuning check and parameter reconstruction through a series of informative images depicting old tuning parameters and data sets. Explore how 18 data and 18 MC as well as 18 MC and 12 MC old tuning parameters play a crucial role in optimizing performance and accuracy. Gain va
0 views • 4 slides
Enhancement of TWT Parameter Set Selection in September 2017
Submission in September 2017 proposes improvements in TWT parameter selection for IEEE 802.11 networks. It allows TWT requesting STAs to signal repeat times, enhancing transmission reliability and reducing overheads. Non-AP STA challenges and current TWT setup signaling are addressed, providing a me
0 views • 12 slides
Advanced Security Concepts in SNARGs Using iO and Lossy Functions
Explore the latest research on Adaptive and Selective Soundness in Succinct Non-interactive Argument of Knowledge (SNARGs), presenting theorems and the inclusion of subexponentially secure techniques like indistinguishability obfuscation, one-way functions, and very lossy functions. Discover the pot
0 views • 20 slides
Understanding Anti-Anti-Virus Techniques and Retroviruses
Explore the world of anti-anti-virus techniques including Retroviruses and Entry Point Obfuscation. Learn about the methods used by viruses to evade detection and damage anti-virus software. Discover how Retroviruses like Ganda virus operate stealthily to hinder anti-virus programs. Delve into strat
0 views • 24 slides
Techniques for Protecting Web User Identity: Part 2 Overview
Explore offensive, defensive, and forensic techniques for safeguarding web user identity in this detailed guide by Zachary Zebrowski. Learn about obfuscation methods, browser protection, and important caveats to enhance online privacy. Discover strategies like borrowing a neighbor's network, using s
0 views • 45 slides
Evaluating Android Anti-malware Against Transformation Attacks
This study evaluates the effectiveness of Android anti-malware solutions against transformation attacks, focusing on the resistance to various types of malware obfuscations. It explores different transformations such as repacking, trivial changes, and sophisticated obfuscation techniques. Ten popula
0 views • 23 slides
Exploring SMT Solvers for Malware Unpacking
In this informative content, we delve into the world of malware analysis, binary packers, and the challenges posed by obfuscation techniques. The article discusses tools like UPX and Themida, as well as the complexities of virtualization and handler obfuscation in unpacking malware. Understanding th
0 views • 24 slides
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
Hyper-Parameter Tuning for Graph Kernels via Multiple Kernel Learning
This research focuses on hyper-parameter tuning for graph kernels using Multiple Kernel Learning, emphasizing the importance of kernel methods in learning on structured data like graphs. It explores techniques applicable to various domains and discusses different graph kernels and their sub-structur
0 views • 20 slides
Exploring Metalearning and Hyper-Parameter Optimization in Machine Learning Research
The evolution of metalearning in the machine learning community is traced from the initial workshop in 1998 to recent developments in hyper-parameter optimization. Challenges in classifier selection and the validity of hyper-parameter optimization claims are discussed, urging the exploration of spec
1 views • 32 slides
Understanding Confidence Limits in Statistical Analysis
Confidence limits are a crucial concept in statistical analysis, representing the upper and lower boundaries of confidence intervals. They provide a range of values around a sample statistic within which the true parameter is expected to lie with a certain probability. By calculating these limits, r
0 views • 4 slides
Understanding Confidence Limits in Parameter Estimation
Confidence limits are commonly used to summarize the probability distribution of errors in parameter estimation. Experimenters choose both the confidence level and shape of the confidence region, with customary percentages like 68.3%, 95.4%, and 99%. Ellipses or ellipsoids are often used in higher d
0 views • 16 slides