Comprehensive Overview of Security Risk Analysis and Management
Explore the essential aspects of security risk analysis and management, including risk identification, assessment, and control techniques within an Information Security (InfoSec) context. Learn about the purpose of risk management, steps involved in a risk management plan, asset identification and c
0 views • 22 slides
Parsimoni – the European IoT/Edge OS. Secure, efficient, flexible.
Revolutionizing IoT/Edge computing with secure, efficient, and flexible technology, Parsimoni aims to set new standards in the industry. Led by CEO Miklos Tomka, the company leverages European open-source technology to create a secure-by-design OS for IoT/Edge applications. Seeking partners for cons
1 views • 5 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Overview of Vibrio cholerae: Characteristics and Identification
Vibrio cholerae is a gram-negative, curved rod bacterium known for causing cholera. Its distinctive features include polar flagellum motility, oxidase-positive nature, and resistance to inhibitory substances. Various culture media are used for its isolation and growth, such as transport, routine, an
0 views • 8 slides
Decoding the GT Identification Process: Understanding the Numbers
Exploring the intricate world of Gifted and Talented (GT) identification, this insightful guide delves into the significance of 1s and 0s, the criteria for GT scoring, percentile ranks, and the importance of Ability Profiles. Discover the nuances of GT testing, identification, stanines, and more to
1 views • 19 slides
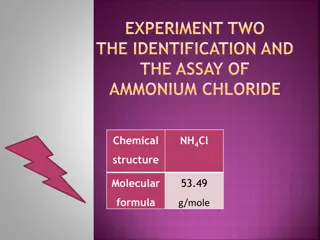
Identification and Assay of Ammonium Chloride: Experiment Insights
Explore the identification and assay process of Ammonium Chloride (NH4Cl), a weak inorganic acid commonly used in various applications. Discover its chemical properties, synthesis, reactivity, identification tests, and details of a titration process using NaOH and phenolphthalein as indicators.
0 views • 16 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
Understanding Talent Identification and Selection in Sports
Talent identification in sports involves recognizing and developing the total potential of athletes in various aspects, aiming for long-term growth rather than focusing solely on immediate performance. It focuses on understanding real potential and systematically developing it over time through qual
1 views • 9 slides
Rapid Identification System for Inmate Release
The Rapid Identification System, also called Rapid ID System, provides a quick way to verify an inmate's identity using fingerprints before release from custody. It allows law enforcement agencies, including IPD users under SDSheriff, to log in and access the system. By searching the San Diego AFIS
3 views • 8 slides
Safe & Secure Gaming Platform Is Online Cricket ID In India
The most secure and safe gaming platform in India is Online Cricket ID. Faster withdrawals within 5 minutes with your online cricket ID. Secure and trusted online cricket and casino ID provider with 24x7 customer support.\nVisit for more information:
1 views • 3 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Understanding LRIT System for Ship Identification and Tracking
LRIT (Long Range Identification and Tracking) system enables global identification and tracking of ships for security purposes. Ships equipped with LRIT system can autonomously transmit ship data to authorized authorities. LRIT system is mandatory for certain types of vessels as per SOLAS convention
0 views • 12 slides
Language Identification System for DARPA RATS Program Evaluation
The Patrol Team Language Identification System was developed for DARPA RATS Program to create algorithms and software for speech tasks in noisy environments. The system involved analyzing datasets, implementing subsystems for language identification, and evaluating performance across different langu
0 views • 19 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Mineral Identification Challenge for 7th Grade Science Students
Engage in a Mineral Identification Challenge where 7th-grade students will explore various minerals using color, streak, luster, transparency, texture, composition, density, crystal shape, cleavage/fracture, hardness, and special properties. Students will rotate through different stations, perform t
0 views • 11 slides
Enhancing Animal Telemetry Data Systems for Secure Collaboration
Wide spectrum of animal telemetry data collection protocols and platforms require enhanced data stewardship options for secure sharing before public release. The need for a more granular understanding of available data and structured systems integration is crucial. Initial workflow involves providin
0 views • 4 slides
Livestock Data Management and Recording Guidelines
This documentation outlines the correct procedures for submitting livestock data, including details on birth notifications, calving information, AI processes, calf identification, and more. Topics covered include birth dates, twin identification, AI horn codes, dam and sire identification, calving e
0 views • 11 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Understanding Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Exploring Secure Care Services in Scotland
Delve into the world of secure care services in Scotland, focusing on achievements, challenges, and opportunities in providing youth justice. Learn about trends in secure care, reduction in costs, reasons for referrals, and evidence-based programs like DBT in Glasgow. Gain insights from industry lea
0 views • 77 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Proposal for Transient Station Identification in IEEE 802.11-21
TGbh use cases necessitate a form of Identity for Non-AP STAs for access control. This proposal delves into the concept of a Transient ID, detached from a MAC address, to support use cases securely. It explores the generation and validation of Transient Identity (TSID) and its key (TSIDK) in conjunc
0 views • 13 slides
Fine-Grained Language Identification Using Multilingual CapsNet Model
This study explores fine-grained language identification through a multilingual CapsNet model, addressing challenges such as short audio snippets, multiple languages, noise, limited training data, and non-class identification. The dataset includes various languages like Arabic, Bengali, Chinese, Eng
0 views • 36 slides
Livestock Identification Methods: Exploring Different Techniques
Explore the importance of livestock identification, methods used, and their significance in various situations. Understand why animals need to be identified, from proof of ownership to disease eradication. Learn about types of identification like branding, ear notching, tattooing, and more, each wit
0 views • 16 slides
Understanding Remote Identification of Unmanned Aircraft: Compliance Methods
The Final Rule on Remote Identification of Unmanned Aircraft introduces compliance methods for the model aircraft community to fly safely in national airspace. Explore the three ways to comply, including Standard Remote ID, Broadcast Modules, and FAA Recognized Identification Areas. Learn about regi
0 views • 11 slides
Understanding Structural Identification in Vector Autoregressions
Explore the algebra of identification problems in VARs, including Cholesky factorization, timing restrictions, long-run impact restrictions, sign restrictions, and identification through heteroskedasticity. Discover why structural identification is crucial for policy design, economic modeling, and u
0 views • 63 slides
German eID and eIDAS: Secure Digital Identification Overview
The German eID system, including eIDAS integration, offers secure digital identification services through government-issued ID cards with embedded chips. It allows citizens and service providers to authenticate each other securely online. The system emphasizes interoperability and privacy protection
0 views • 16 slides
Approaches to Secure Identification in Communication Networks
This content discusses various methods and protocols for secure identification and authentication in communication networks. It covers topics such as using passwords, biometrics, cryptographic protocols, and one-time password systems. Different approaches, their reliability, security levels, and cos
0 views • 11 slides
Foundations of Cryptography: Secure Multiparty Computation
Explore the foundations of cryptography with insights into secure multiparty computation, including the Secure 2PC from OT Theorem and the Two-Party Impossibility Theorem. Delve into the impossibility of 2-Party Secure MPC, claims, and exercises on extending to statistical security. Learn about redu
0 views • 39 slides
Understanding Minerals: Properties and Identification
Minerals are naturally occurring solid inorganic substances with definite compositions and structures. They are classified based on physical and chemical properties. This content discusses the definition of minerals, the conditions that classify gold as a mineral, distinguishing mineral characterist
0 views • 29 slides
Performance Studies of dRICH Detector at ePIC Experiment
The Electron-Ion Collider ePIC experiment focuses on the performance studies of the dRICH detector for particle identification crucial in various physics channels. The detector features aerogel optimization, SiPM sensors, and test-beam analyses. Key capabilities include different techniques for part
0 views • 28 slides
Fundamentals of Marketing: Product Identification and Branding Insights
Explore the essential concepts of marketing including the marketing mix, product identification methodology, and the significance of branding in differentiating products. Learn about the 4Ps of marketing mix - Product, Price, Place, and Promotion, and how branding plays a crucial role in establishin
0 views • 15 slides
Six Step Approach to Problem Identification in Medical Curriculum Development
In this comprehensive guide on curriculum development for medical education, the focus is on identifying and addressing key problems in the curriculum design. The six-step approach outlined covers problem identification, needs assessment, goal setting, educational strategies, implementation, and eva
0 views • 12 slides
Importance of Verification for Patient Identification & Blood Product Labeling in Medical Procedures
This educational program emphasizes the crucial role of verifying patient identification and blood product labeling in medical settings. It covers the significance of accurate verification, policy expectations, and the process for ensuring patient safety during blood product administration. The prog
1 views • 30 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides
Tracking and Identifying People with Millimeter Wave Radar
This study presents a human tracking and identification system using mmWave radar technology, offering high precision and the ability to conceal behind materials. The system achieved a median tracking accuracy of 0.16m and an identification accuracy of 89% for 12 individuals. Unlike traditional meth
0 views • 12 slides