A Comprehensive Guide to 192.168.188.1: Login and Troubleshooting
192.168.188.1 serves as the default login gateway for numerous WiFi routers, offering access to various network configurations. In this guide, we will delve into the essential aspects of 192.168.188.1, encompassing both the login process and troubleshooting procedures.\n \nTo know more : https:\/\/1
7 views • 2 slides
Introduction to Networking Devices: Hubs, Switches, and Routers
Explore the essential networking devices - hubs, switches, and routers - that facilitate connections between computers and networks. Learn about the functions, differences, and applications of these devices in managing data flow and enhancing network efficiency. Dive into the basics of network conne
0 views • 28 slides
Understanding TCP/IP Networking Fundamentals
Explore the basics of TCP/IP networking, including protocols like IP, UDP, RTP, and more. Learn about the structure of the Internet, the role of routers, OSI network model, TCP/IP network model, and packet encapsulation in data transmission. Gain insights into the layers of the OSI model and the TCP
1 views • 36 slides
Benefits and Structure of VoIP for Business
VoIP offers various benefits for businesses, including cost savings, increased productivity, and feature-rich communication. It allows seamless voice networks, mobility, and integration of data applications with phones. The traditional phone system is likely to be replaced by VoIP. The VoIP structur
0 views • 42 slides
Networking Fundamentals and Challenges in Data Centers
Today's lecture covers definitions of routing and switching in networking, focusing on data center challenges, traffic patterns, fabric management, and parallelism within networks. The session also explores the role of switches and routers in data center and Internet design, emphasizing the importan
0 views • 38 slides
Understanding Computer Communication Networks at Anjuman College
This course focuses on computer communication networks at Anjuman College of Engineering and Technology in Tirupati, covering topics such as basic concepts, network layers, IP addressing, hardware aspects, LAN standards, security, and administration. Students will learn about theoretical and practic
0 views • 72 slides
Understanding Computer Network Components
Computer network components, including NIC, switch, hub, router, and modem, play vital roles in setting up networks. NIC (Network Interface Card) connects computers, hubs distribute data to multiple devices, switches provide direct connections, and routers connect LAN to the internet. Each component
1 views • 13 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Understanding Buffering Problems in Communication Networks
Buffering problems in communication networks involve managing the flow of packets at routers to maximize throughput while considering factors like packet deadlines and buffer size limitations. These problems are often viewed as online games between algorithms and adversaries, with competitive ratios
0 views • 38 slides
Analysis of Onion Routing Security and Adversary-based Metrics
In this comprehensive analysis, the security aspects of Onion Routing are scrutinized along with adversary-based metrics. Various security vulnerabilities such as compromised relays and potential attacks on the first and last routers are examined. Existing metrics like entropy coefficients and proba
0 views • 21 slides
Understanding Onion Routing for Enhanced Privacy Protection
Explore the concept of onion routing for anonymous internet communication explained through images. Learn how users create circuits and exchange data through multiple routers to enhance privacy and security. Discover the intricate process step by step in a visual format.
0 views • 49 slides
Understanding Router Routing Tables in Computer Networks
Router routing tables are crucial for directing packets to their destination networks. These tables contain information on directly connected and remote networks, as well as default routes. Routers use this information to determine the best path for packet forwarding based on network/next hop associ
0 views • 48 slides
Understanding Networking Principles and Routing Algorithms in Distributed Systems
Delve into the intricacies of networking principles and routing algorithms in distributed systems. Explore the four layers studied, including the network layer that handles routing. Discover the role of routers in forwarding packets between networks and the challenges of designing routing algorithms
1 views • 23 slides
Evolution of Programmable Switches and Routers
Explore the evolution of programmable switches and routers, from early attempts at programmability to the introduction of the P4 programming language and Software Defined Networking (SDN). Discover the shift towards greater customization and control in network infrastructure, leading to the developm
0 views • 40 slides
Enhancing Internet Backbone Performance through Parallel Resolution of Packets and Rules
The bottleneck in Internet backbones lies in the decision-making process for incoming packets. This article explores the challenges faced in efficiently processing policies in routers and middleboxes by introducing parallel resolution techniques to increase throughput and reduce latency. It discusse
0 views • 22 slides
Exploring Advanced D-STAR Technologies at InfoCon 2015
Delve into the world of advanced D-STAR technologies showcased at InfoCon 2015 held in Big Spring, TX. From high-speed data modes to setting up routers, DV dongles, and DVAPs, this event highlights the diverse capabilities and applications of D-STAR technology. Discover how to enhance your communica
0 views • 19 slides
Design and Evaluation of Hierarchical Rings with Deflection Routing
This research explores the implementation of Hierarchical Rings with Deflection (HiRD) routing as a solution to the performance and energy inefficiencies found in traditional hierarchical ring designs. HiRD guarantees livelock freedom and efficient delivery while simplifying the network structure by
0 views • 52 slides
Understanding Wide Area Networking Using Frame Relay Cloud
The field of networking is advancing rapidly, with technologies like cloud computing relying on robust wide area networking. This presentation explores the use of Frame Relay Cloud in improving the security and configuration complexities faced in interconnecting wide area networks. It discusses the
0 views • 16 slides
Understanding LAN Interconnection and Switching Technologies
This content delves into the concepts of interconnecting LANs, exploring the reasons and methods behind partitioning LANs and interconnecting them at different layers using repeaters, hubs, bridges, switches, and routers. It also highlights the differences between these devices in terms of their net
0 views • 21 slides
Bhutan's eHealth Pilot Project Using TV White Space
Bhutan implemented an eHealth pilot project utilizing TV White Space technology for last-mile connectivity in remote communities. The project aimed to deliver healthcare services efficiently and replicate similar systems in underserved areas. The implementation involved strategic partnerships with A
0 views • 10 slides
AERO: Mobile Routing & Addressing System for IP Internetworks
AERO, Asymmetric Extended Route Optimization, is a mobile routing and addressing system designed for IP internetworks like aviation, enterprise, and campus networks. It enables stable IPv6 prefixes for mobile devices, treating them as routers to connect to the Internet of Things. AERO offers feature
0 views • 26 slides
Understanding IP Routing and Switching in Computer Networks
In the world of computer networking, IP routing and switching play crucial roles in ensuring efficient data transmission. Switches make decisions based on MAC addresses, while routers route based on IP information. By managing routing tables and using static or dynamic routing protocols, networks ca
0 views • 13 slides
Innovations in Software-Defined Network Computing
The presentation explores the evolution of routers in the early 2000s, the limitations of hardware routers, and the need for more flexible and extensible software routers. It discusses the concept of the Click modular router and its architecture, emphasizing the benefits of a modular design approach
0 views • 35 slides
Parental Control Based on MAC Address in Wi-Fi Routers
The document discusses the implementation of parental control features based on MAC addresses in home-brand wireless routers and enterprise-class access points. It highlights real-world examples and market prevalence of this functionality, emphasizing its presence in various Wi-Fi router brands. The
0 views • 13 slides
Decoy Routing in Internet Circumvention Strategies
Decoy routing in network interference involves making hosts on the internet appear as proxy servers, enabling access to blacklisted sites with normal latency and throughput. The approach aims to maintain content secrecy and actual destination privacy by making traffic filtering difficult for interme
0 views • 14 slides
Understanding BGP Basics and Routing Security
Border Gateway Protocol (BGP) is a crucial protocol used by routers to exchange routing information and make routing decisions. This protocol plays a key role in how the Internet functions, with over 76,000 Autonomous Systems and millions of routes being advertised. Research and Education (R&E) netw
0 views • 33 slides
IT Infrastructure Updates and Deployments Overview
Deployment and upgrade progress of IT infrastructure at LBNL includes wireless network expansion, router replacements with 100G upgrade, 100G tapping evaluation for IDS, DTN deployment for data transfer automation, and video conferencing cart deployment. The updates range from network switches to ro
0 views • 7 slides
Understanding Subnet Mask in Network Simulation Course
Dive into the world of subnet masks and CIDR notations in the context of network simulation. Learn to determine subnet masks, divide networks, and configure routers to optimize network efficiency. Practice subnetting with exercises and explore default subnet masks and CIDR values for enhanced networ
0 views • 12 slides
Understanding Routing Issues in Information-Centric Networks
This section delves into the routing issues within Information-Centric Networks, highlighting vulnerabilities such as misconfigured routers, prefix hijacking, and impersonation. It emphasizes the importance of validating routes and proposes improvements to address security concerns associated with B
0 views • 15 slides
Understanding ARP, ICMP, and DHCP in TCP/IP Protocol Stack
ARP (Address Resolution Protocol) plays a crucial role in bridging the Layer 2/Layer 3 addressing boundary in the TCP/IP protocol stack, allowing IP to be agnostic about layer 2 addressing while still using layer 2 for packet delivery. Machines ARP for MAC addresses within their local network, where
0 views • 39 slides
Understanding EIGRP Network Protocol
EIGRP (Enhanced Interior Gateway Routing Protocol) is a network protocol that facilitates efficient information exchange among routers. Evolving from IGRP, EIGRP allows interoperability and can be used for IP, AppleTalk, and Novell NetWare networks. EIGRP metrics scale IGRP metrics by a factor of 25
0 views • 13 slides
Understanding VLANs and Virtual LANs in Networking
This detailed guide explores VLANs (Virtual LANs) in network configuration, covering concepts like switch hosts, aggregation, subnets, routers, and port configurations. Learn about setting up VLANs, managing broadcast domains, ARP requests, and more to enhance network security and performance.
0 views • 28 slides
RF Exposure for Amateur Radio: Understanding Sources and Safety Measures
Exploring the various sources of RF exposure in relation to amateur radio, this comprehensive guide by Harold C. Fleischer, III AE5AS sheds light on different antennas like those used by AM, FM radio stations, TV stations, MW telecommunications, police, taxis, and even Wi-Fi routers. Each image show
0 views • 39 slides
Understanding IP Addressing in Networking
IP addressing plays a crucial role in providing unique addresses to machines on the internet, identifying networks and hosts, enabling routing, and ensuring proper packet delivery across networks. This content covers the need for IP addresses, their role in routing, address parts, classful IP addres
0 views • 36 slides
Understanding Layer 3 Switches: Functionality and Configuration
Layer 3 switches combine the features of Ethernet switches and routers, allowing them to process both MAC and IP headers. By configuring VLANs, trunking, and management interfaces, these switches can handle data forwarding across different subnets efficiently. This guide explains the basic principle
0 views • 19 slides
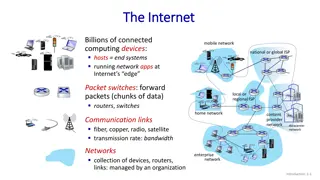
Understanding the Basics of the Internet and Network Structure
Billions of connected computing devices make up the Internet, with hosts, packet switches, routers, and communication links facilitating data transmission. The Internet functions as a network of networks, enabling various services like web browsing, video streaming, and online communication. Differe
0 views • 17 slides
Ultra-Fast DDoS Detection with FastNetMon at Coloclue
Discover how Coloclue, a non-profit ISP, leverages FastNetMon and automation to detect and mitigate DDoS attacks within seconds, automating the problem away and protecting their network effectively. With 2 datacenters, 4 routers, and a volunteer-driven approach, Coloclue successfully defended agains
0 views • 16 slides