Types of communication systems
Various types of communication systems including Coaxial, Microwave, Satellite, Cable, and Cellular. Learn about receivers, transmitters, path loss, power calculations, and the use of Matlab and Simulink for system design and simulation. Discover the significance of mathematical symbols in communica
2 views • 23 slides
Understanding the Communication Process: Key Concepts and Characteristics
Communication is the exchange of information, ideas, and emotions between two or more individuals. It is a process involving a source, encoding of messages, communication channels, receivers, decoding of messages, feedback, and potential noise. Important characteristics include the involvement of at
1 views • 8 slides
Understanding Computer Networks: Basics, Components, and Topologies
Computer networks are essential for sharing resources, exchanging files, and enabling electronic communications. This includes components like senders, receivers, messages, transmission media, and various modes of communication. The need for networking arises from file sharing, resource sharing, com
14 views • 28 slides
SMuRF: SLAC Microresonator RF Readout
SMuRF group at SLAC developed a cutting-edge RF readout system for cryogenic micro-resonators used in research. The system features cold resonators tuned with TES current and a flux ramp to eliminate 1/f noise. Key technical challenges include noise, linearity, wide bandwidth, and computation power.
4 views • 16 slides
Understanding Networking Bridges and Transceivers
Bridges in networking play a crucial role in dividing logical bus networks into subnets, improving performance by managing traffic flow. Although network switches have largely replaced bridges today, the advantages of bridges in reducing unnecessary traffic and isolating busy networks remain signifi
0 views • 40 slides
Understanding Traffic Engineering Analysis in Telecommunication Networks
Traffic engineering analysis in telecommunication networks involves determining the network's capacity to carry traffic with a loss probability. Blocking probability, which is a key design concern, is influenced by various elements such as switching devices, digit receivers, call processors, and tru
1 views • 50 slides
Understanding Insolvency Accounts and Laws in Financial Accounting
Insolvency in financial accounting refers to the inability to pay debts when they fall due. This article covers the meaning of insolvency, the criteria for being declared insolvent, the Insolvency Act in India, and its applicability to individuals, firms, and Hindu Undivided Families. It distinguish
1 views • 10 slides
Proposal for Efficient Bandwidth Utilization in IEEE 802.11 Networks
This proposal aims to address the inefficient utilization of bandwidth in IEEE 802.11 networks by allowing stations to transmit on idle channels within their operating bandwidth. The document discusses the problem statement, high-level solution, relevant capabilities of transmitters and receivers, p
0 views • 15 slides
Specific Reliefs under the Specific Relief Act, 1877
The Specific Relief Act, 1877 provides various ways to give specific reliefs, including taking possession, ordering obligations, abstaining from acts, declarations, and appointing receivers. It covers the recovery of immovable and movable property, with specific procedures outlined. The Act allows f
0 views • 32 slides
Enhancing Throughput with Aggregated PPDU for Large Bandwidth IEEE 802.11 Networks
This document discusses the implementation of Aggregated PPDU to boost throughput in IEEE 802.11 networks with large bandwidth. The focus is on accommodating various STAs with different operating bandwidths and optimizing traffic flow. By utilizing Aggregated PPDU, significant gains in throughput ca
5 views • 7 slides
Understanding Cascade Amplifiers and Their Applications
Cascade amplifiers are two-port networks designed with amplifiers connected in series, providing enhanced signal strength in various applications such as TV receivers and tuned RF amplifiers. These amplifiers use multiple stages to amplify the overall voltage gain, overcoming limitations of single-s
0 views • 15 slides
Understanding Android App Development Basics
Android apps operate within a secure, multi-user environment with each app having its own user identity and permissions. Components like Activities, Services, Receivers, and Providers handle various aspects of app functionality. Permissions safeguard user privacy by controlling access. Developers mu
0 views • 20 slides
Air waybill tracking to track air cargo
Air waybill tracking is a crucial feature in air freight logistics, enabling shippers and receivers to monitor the status and location of their shipments in real-time. By using air waybill tracking, you can easily track your goods from the moment the
0 views • 1 slides
Understanding the Impact of Message Creation on Communication Processes
The process of communication begins with creating a message, which can significantly influence how it is received. Messages, conveyed through words, signs, or sounds, are interpreted by receivers based on the sender's delivery. Littlejohn (2018) emphasizes the importance of how senders initiate comm
1 views • 9 slides
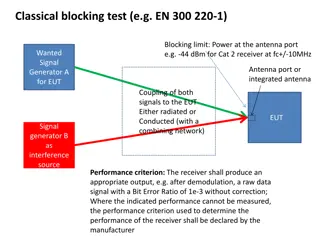
Classical Blocking Test and Receiver Performance Criteria
Classical blocking test procedures such as EN 300.220-1 outline limits on power at the antenna port for receivers, with criteria for achieving desired performance levels without errors. Manufacturers must declare appropriate performance criteria for devices, even if certain performance metrics are n
0 views • 6 slides
Understanding Receivers and Noise in Radio Astronomy
Discover the challenges faced in radio astronomy due to noise, with the signal often indistinguishable from background noise. Learn about receiver sensitivity issues, minimizing thermal noise, and mitigating atmospheric effects to improve observation quality. Explore the essential elements of telesc
0 views • 55 slides
Transimpedance Amplifiers in CMOS Technology for Optical Communications at 40 Gb/s
This research by Joseph Chong at Virginia Tech delves into the use of transimpedance amplifiers (TIAs) in CMOS technology for optical communications operating at a data rate of 40 Gb/s. The study outlines the motivation behind the project, the role of TIAs in optical receivers, TIA circuit topologie
0 views • 52 slides
Advancing Radio Astronomy Through Technology: RADIOBLOCKS Project Overview
Exploring the innovative use of technology in radio astronomy, the RADIOBLOCKS project is focused on enhancing the entire data process from receivers to final output. With a grant number of 101093934, the project aims to streamline project management tasks, facilitate communication, and foster colla
0 views • 9 slides
Exploring AirPlay Technology for Wireless Display in Education
AirPlay technology by Apple enables wireless mirroring of screens and streaming of content from iOS devices and Mac computers to AirPlay receivers, providing flexibility for educators to move around while presenting in classrooms. This session delves into various Apple and third-party options, discu
0 views • 17 slides
Understanding Global Positioning System (GPS) Technology
Explore the invention and evolution of GPS, its safe handling, examples of GPS receivers, how GPS works through satellite communication, and the role of satellites in GPS technology. Delve into receiver initialization methods for accurate location services.
0 views • 15 slides
Enhanced Replay Detection for Header Protection in IEEE 802.11-23/1960r1
Enhancing security in IEEE 802.11 is a key goal of UHR. This document discusses the need for improved replay detection mechanisms for header protection in the MAC layer. The proposal suggests incorporating a time component in the Packet Number (PN) to mitigate jam, record, and replay attacks. By uti
0 views • 11 slides
Understanding Wireless Power Technology
Explore the functionality of wireless power technology, focusing on applications like battery charging for mobile devices. Learn about the system components, power conversion processes, control mechanisms, and communication between transmitters and receivers. Discover the principles behind wireless
0 views • 16 slides
Understanding Mobile Computing Services and Broadcast Receivers
Mobile computing services play a vital role in background operations of apps, allowing them to perform tasks even when not in use. Broadcast receivers help in efficient communication between components. Learn about key concepts and examples of services, how they are declared in the app manifest, and
2 views • 72 slides
Optical Fiber Link Systems for Data Transmission Design Guide
Explore the principles of optical power budget and rise time budget in light wave systems for designing efficient point-to-point links. Understand system considerations, architecture, and major components like transmitters, regenerators, and receivers. Learn to apply subject knowledge in designing r
0 views • 53 slides
Stephen Minister Training: Assertiveness and Relating Skills
The Stephen Minister Training Module discusses the importance of assertiveness in relating gently yet firmly. It emphasizes expressing oneself clearly and respectfully while considering the needs and opinions of others. The training distinguishes assertiveness from passivity and aggression, highligh
0 views • 21 slides
The Power of Direct Mail in Influencing Influencers
Direct mail has a significant impact on influencers, with up to 80% believing that it can change their opinion of a company or brand. While most people are receivers of influencer content, influencers themselves are influenced by mail more than the average. Mail helps in creating cut-through and hel
0 views • 6 slides
Transportation of Dangerous Materials Regulations
Lab workers handling dangerous materials need to follow strict regulations to prevent accidents. The United Nations and IATA provide guidelines for shipping dangerous goods, with responsibilities for shippers, carriers, and receivers outlined. Classification of dangerous materials and proper handlin
0 views • 9 slides
Understanding GPS Data Processing and RINEX Formats
Learn about the process of transferring GPS data from receivers to processing input, the importance of RINEX formats for universal data exchange, different raw data formats, motivation behind RINEX development, and details about RINEX versions. Explore RINEX 2 data format, its file naming convention
0 views • 13 slides
Vulnerabilities in Unprotected MAC Header Fields in IEEE 802.11 Standard
The document discusses the risks associated with unprotected fields in the MAC header of MPDUs in IEEE 802.11 standards, highlighting how these fields can be vulnerable to attacks leading to adverse effects on receivers. Fields like Frame Control, Sequence Control, and QoS Control are identified as
0 views • 10 slides
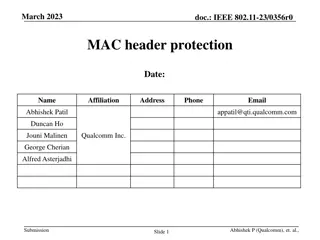
Enhancing MAC Header Protection in IEEE 802.11 for Improved Security
Numerous critical fields in the MAC header of IEEE 802.11 frames lack protection during encryption, making them vulnerable to attacks that can have adverse effects on receivers. By safeguarding these fields, performance goals can be met, power efficiency enhanced, and reliability improved. The docum
0 views • 9 slides
Understand Broadcast Receivers in Android Development
Discover the role of broadcast receivers in Android development as components that allow registration for system or application events. Learn how to register receivers, receive intents, and utilize popular system broadcasts for efficient app functionality. Explore static and dynamic registration met
0 views • 20 slides
Youth Football Offensive Fundamentals and Drills Overview
Explore the essential offensive skills and drills for youth football players coached by Mike Elder from Avon High School in Ohio. Learn about practice structure, position-specific skills for offensive linemen, quarterbacks, running backs, and wide receivers, along with fun and fundamental drills to
0 views • 14 slides
Understanding the RSA Algorithm - An Overview
Cryptography is the science of writing in secret code to protect information. The RSA algorithm, introduced by Rivest, Shamir, and Adleman in 1978, is a popular public key system. It involves the exchange of secure messages between senders and receivers to avoid code breaking. This algorithm uses bo
1 views • 31 slides
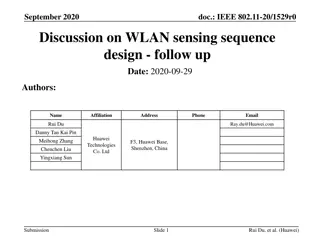
Analysis of WLAN Sensing Sequence Design Using Ambiguity Function and Range-Doppler Map
In this document, the authors from Huawei discuss the analysis of employing the ambiguity function for WLAN sensing sequence design. They delve into the ambiguity function's definition, analysis, and its comparison with the range-Doppler map. The document highlights the importance of ambiguity funct
0 views • 15 slides
Implementation of Cornell Ionospheric Scintillation Model in Spirent GNSS Simulator
Researchers from the University of Nottingham and Spirent Communications collaborated to implement the Cornell Ionospheric Scintillation Model into the Spirent GNSS Simulator. The study focuses on the diffractive effects of ionospheric scintillation on GNSS signals, examining small-scale plasma irre
0 views • 24 slides
Overview of POCA Applications and Restraint Orders in Criminal Law
This collection of information delves into the application of Proceeds of Crime Act (POCA) in criminal investigations, focusing on topics such as Restraint Orders, Discharge, POCA Timetable, Benefit Figures, Available Amount determination, Making Confiscation Orders, Enforcement, Enforcement Receive
0 views • 27 slides
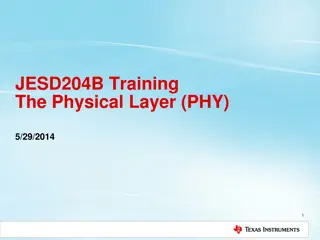
Understanding JESD204B Physical Layer (PHY) in High-Speed Serial Interfaces
The JESD204B training presentation delves into the Physical Layer (PHY) of high-speed serial interfaces, covering topics such as speed grades, compliance types, SERDES solutions for long channels, clocking information, differential link data transmission, and electrical requirements for drivers and
0 views • 20 slides
Understanding the Basics of Forward Passes in Football
In football, a forward pass is a crucial play that involves specific rules to determine legality. This includes when a passer is beyond the neutral zone, limitations on multiple forward passes, conditions for illegal forward passes, and eligibility rules for receivers. Knowing these fundamentals hel
0 views • 15 slides
Channel Modeling for Image Sensor-Based Sea and Digital Signage Communication
This submission by Kookmin University presents a proposed channel model for image sensor communication in sea and digital signage applications. The proposal considers specific scenarios, transmitters, channel mediums, and receivers for effective communication in varied conditions.
0 views • 12 slides
Receiver Requirements for Realistic Interference Scenarios in Wireless Personal Area Networks
This document discusses the receiver requirements for handling realistic interference scenarios in Wireless Personal Area Networks (WPANs). It covers topics such as second-order distortion, direct conversion receivers, blocker mitigation techniques, and proposals to specify sensitivity levels in the
0 views • 6 slides