Understanding Ethereum Token Standards: ERC-20, ERC-721, and ERC-1155
Delve into the world of blockchain, cryptocurrencies, and decentralized technologies with a focus on Ethereum token standards ERC-20, ERC-721, and ERC-1155. Learn about the differences between fungible and non-fungible tokens, smart contracts, and examples of popular tokens in the space. Explore how
0 views • 9 slides
Understanding COVID-19's Impact on Joint Health: Reactive Arthritis vs Viral Arthritis
Explore the distinction between reactive arthritis and viral arthritis in the context of COVID-19, discussing symptoms, triggers, and potential long-term consequences on joint health. Learn how viral infections can lead to acute arthralgia and arthritis, including common pathogens such as Hepatitis
0 views • 30 slides
Update on Computing and IAM Service Developments in WLCG/HSF Workshop
Details about the update campaign for HTCondor CEs, APEL support for tokens, and IAM service developments presented at the WLCG/HSF Workshop on May 14, 2024. Highlights include HTCondor CE upgrades, APEL support discussions, and advancements in IAM services for LHC experiments.
1 views • 12 slides
Exploring Helium: A Decentralized IoT Network Revolution
Delve into the world of Helium, a blockchain-based IoT network revolutionizing connectivity. Managed by a community of crypto investors, this global network offers innovative solutions for telecom industry challenges through decentralized deployment and mining of HNT tokens.
0 views • 17 slides
What Are The Benefits Of Proactive IT Support Versus Reactive It Support?
Stop IT headaches! Discover how proactive IT support prevents problems & saves you money compared to reactive fixes.
1 views • 5 slides
Real World Asset Tokenization in Blockchain Technology
Tokenization of real-world assets in blockchain technology digitizes physical assets into blockchain tokens, increasing liquidity, transparency, and accessibility by transforming traditional markets through fractional ownership and automated smart contracts.
0 views • 9 slides
Layer 2 Token Marketing Services
Layer-2 token marketing promotes tokens built on scalable layer-2 solutions, highlighting benefits like faster transactions and lower fees. Get connected with our experts today and launch a lucrative \ntoken platform.
0 views • 3 slides
Resource Integration Small Generation Topics and Processes
This document discusses various topics related to small generation resources such as Distributed Generation Resources (DGR) and Distributed Energy Storage Resources (DESR). It covers processes, modeling, Reactive and Automatic Voltage Regulation (AVR) testing scenarios, timelines, simplified modelin
1 views • 39 slides
Understanding C-Reactive Protein (CRP) Test: Uses and Principle
C-Reactive Protein (CRP) is a liver-produced protein that indicates inflammatory conditions. The CRP test helps detect infections, monitor diseases like cancer, and evaluate inflammatory conditions. The test principle involves latex agglutination for CRP detection in human serum.
0 views • 21 slides
Understanding the Power of Java Reactive Programming
Java Reactive Programming offers a solution to handling increasing data complexity and diverse device types in today's fast-paced business environment. By embracing reactive principles, businesses can accelerate their transformation by building flexible, loosely-coupled, and scalable systems. Learn
0 views • 18 slides
Expand Advantages with Hamster Tokens on Hamster Trade
Hamster Trade on Message is a progressive decentralized cryptographic money exchanging stage that consolidates the comfort of virtual entertainment with cutting-edge blockchain innovation. Clients benefit from secure, minimal expense exchanges, impro
0 views • 4 slides
Token Economies and Behaviour Modification in Custody: Evaluating Efficacy
This article explores the application of token economies in prisons as a behaviour modification technique based on operant conditioning. Token economies involve exchanging tokens for desired behaviours, aiming to replace undesirable actions with positive reinforcement. The use of increments, consist
0 views • 19 slides
Managing Risks and Leveraging Opportunities in Digital Asset Space
Explore the dynamics of crypto compliance in the Caribbean region, delving into blockchain technology, remote work trends, algorithm challenges, and the transformation of tech and tokens. Discover how the financial services sector navigates risks and harnesses opportunities in the digital asset land
0 views • 10 slides
ELECTRA: Pre-Training Text Encoders as Discriminators
Efficiently learning an encoder that classifies token replacements accurately using ELECTRA method, which involves replacing some input tokens with samples from a generator instead of masking. The key idea is to train a text encoder to distinguish input tokens from negative samples, resulting in bet
0 views • 12 slides
Understanding JSON Web Tokens (JWT) in Web Development
JSON Web Tokens (JWT) are a simple and commonly used type of token that is self-contained, meaning the data is stored within the token itself. They consist of three parts: Header, Payload, and Signature. JWTs are signed by the server using a secret key, allowing clients to read the data without bein
3 views • 6 slides
Balancing Proactive and Reactive Cyber Defenses
Learn how to balance proactive and reactive strategies in cyber defense. Protect your business with a comprehensive security approach.\n
2 views • 6 slides
Secure Access to OAuth-Based Services in HTCondor Jobs
Enhance the security of HTCondor job submissions by leveraging OAuth tokens for secure access to file storage services. Learn how the Credd and Credmon architecture facilitates the management and secure transfer of credentials, ensuring sensitive data remains protected during job execution.
0 views • 23 slides
Understanding Noise Control Methods in Environmental Engineering
Explore the concepts of noise control in environmental engineering, focusing on mufflers, reactive mufflers, and noise control in the transmission path. Learn about absorptive and reactive mufflers, their principles, and applications. Discover how barriers and panels can effectively reduce noise tra
0 views • 9 slides
Enhancing Library Accessibility: Request Alternate Formats for Print Disabled Users
This project focuses on providing accessible library services for print-disabled users by allowing them to request alternate formats, reducing their workload and promoting awareness of available services. The workflow involves users accessing the library website, logging in with ACE tokens, populati
1 views • 24 slides
SHAKEN and STIRed: Current State of Anti-Spoofing and Robocall Mitigation
Exploring the challenges and efforts in combatting robocalls and caller spoofing in the telecommunications industry, focusing on restoring trust in voice networks through initiatives like SHAKEN (Secure Handling of Asserted information using toKENs) and STIR (Secure Telephone Identity Revisited). Th
0 views • 22 slides
Expression Tree Construction: Building Fully Parenthesized Expression Trees
In the process of building expression trees, nodes are inserted based on operators and operands, creating a fully parenthesized expression. The construction involves parsing the expression, inserting new nodes as tokens are examined, and linking nodes accordingly. By following the steps for handling
0 views • 17 slides
Dumping Data from Alma Using PERL and the Alma Analytics API
Learn how to extract data from Alma using PERL programming language and the Alma Analytics API. Get insights on API calls, required parameters, optional parameters like setting row limits, and using resumption tokens for handling large data sets efficiently.
0 views • 16 slides
Strategies for Children with SEMH Needs by Sofia Hussain
Exploring strategies for children with SEMH needs, this content discusses in-the-moment thinking and reactive strategies presented by Dr. Sofia Hussain. It delves into addressing concerning behaviors, practitioner emotions, and ways to support both practitioners and children. The approach emphasizes
0 views • 11 slides
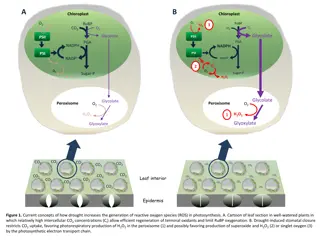
Understanding Drought-Induced Reactive Oxygen Species Generation in Photosynthesis
Leaf responses to drought conditions leading to increased generation of reactive oxygen species (ROS) in photosynthesis are explained. Drought-induced stomatal closure affects CO2 uptake, promoting H2O2 production in peroxisomes and potential ROS production by the photosynthetic electron transport c
0 views • 5 slides
Requirements for Grid Connection of Wind Farms in Hellenic Grid Code
The Hellenic Grid Code outlines the specific requirements for wind farms regarding grid connection, including frequency and voltage operation boundaries, active/reactive power boundaries, voltage/reactive power control, and load-frequency control. These requirements ensure the safe and efficient int
0 views • 6 slides
Systems-Oriented Concept Map Extension for Reactive Nitrogen Flows
International Organization for Chemical Sciences in Development presents a Systems-Oriented Concept Map Extension (SOCME) focusing on biogeochemical flows of reactive nitrogen from NH3. The concept explores core reaction subsystems, energy input subsystems, equilibrium conditions, and the integratio
0 views • 11 slides
Understanding Different Types of Artificial Intelligence
Artificial Intelligence is categorized into Narrow AI (Weak AI), General AI, and Super AI based on capabilities, while Reactive Machines, Limited Memory, Theory of Mind, and Self-Awareness are types based on functionality. Each type serves a specific purpose with varying levels of intelligence. Narr
0 views • 27 slides
Understanding User Identity and Access Tokens in Windows Security
Delve into the intricate world of user identity and access tokens in Windows security. Explore how user identities are represented, the structure of access tokens, and the significance of processes running under different user contexts. Gain insights into advanced Windows security principles and lea
1 views • 13 slides
Understanding Reactive Arthritis: Symptoms, Diagnosis, and Treatment
Reactive arthritis, a rare disease associated with infections like Chlamydia, Salmonella, and Yersinia, presents with musculoskeletal features such as oligoarthritis, enthesitis, and dactylitis. Extraarticular manifestations include eye involvement and genitourinary symptoms. Diagnosis involves lab
0 views • 9 slides
Overview of Unified Power Flow Controller (UPFC) in Power Systems
A Unified Power Flow Controller (UPFC) is a combination of a Static Synchronous Compensator (STATCOM) and a Static Synchronous Series Compensator (SSSC) interconnected via a common DC link. UPFC allows bidirectional flow of real power and provides concurrent real and reactive series line compensatio
0 views • 20 slides
Systematic Testing of Reactive Software - A Case Study on LG Electric Oven
Overview of a case study conducted on LG Electric Oven using systematic testing of reactive software with non-deterministic events. The study focused on detecting concurrency bugs in the software controller of the oven through an automated testing framework that generates event timing sequences. It
0 views • 32 slides
Understanding Synchronous Reactive Components in Autonomous Cyber-Physical Systems
Synchronous Reactive Components (SRCs) play a crucial role in Autonomous Cyber-Physical Systems, involving inputs, state variables, outputs, and updates. Valuation functions, input valuations, and state valuations are key concepts in formalizing SRCs. Explore the definition, variables, valuations, a
0 views • 37 slides
Reactivity of Metals and Non-Metals: A Comprehensive Overview
Metals like potassium and sodium react vigorously with water, while non-metals like phosphorus are highly reactive and stored in water. Metals react with acids to form hydrogen gas, while non-metals generally do not react with acids. Reactivity series explains displacement reactions where more react
0 views • 11 slides
Understanding Session Management Challenges in Web Applications
Session management is crucial in web applications to maintain user authentication and authorization. This presentation delves into the evolution of session management, highlighting issues with HTTP authentication, the use of session tokens, and challenges in storing and securing session data. Variou
0 views • 18 slides
Reactive Tokens and Prosodic Features in Korean Conversation Analysis
This study delves into Reactive Tokens (RTs) and their role in Korean conversation, focusing on prosodic cues that elicit RT usage. It explores RT placement, differing functions, and the impact of boundary tones on RT utilization. Data collected through telephone conversations between young male spe
0 views • 20 slides
Understanding LL(1) Grammars and Computing First & Follow Sets
Exploring LL(1) grammars and the computation of First and Follow sets for non-terminals. This involves defining FIRST(.) as the set of tokens that appear as the first token in strings derived from a non-terminal and FOLLOW(A) as the terminals that can appear immediately to the right of A in the sent
0 views • 33 slides
Integrating Hashicorp Vault with HTCondor for Secure Oauth Credential Management
Exploring the use of token-based authentication over X.509 certificates for improved security in HTCondor workflows. The transition to tokens offers enhanced control and flexibility, with a focus on utilizing JWTs and Scitokens. Leveraging Hashicorp Vault alongside HTCondor streamlines the managemen
0 views • 18 slides
Reactive Clocks with Variability-Tracking Jitter in ICCD 2015
Explore the research on reactive clocks with variability-tracking jitter presented at ICCD 2015. The study delves into the cost of variability margins, timing analysis, clock variability comparison between PLL and reactive clocks, and adaptive frequency utilization. Understand the benefits and impli
0 views • 24 slides
Innovative Fluid Solutions for Textile and Leather Finishing
Specialty Fluids by Blue Star Silicone offer a comprehensive range of silicone-based products for textile and leather finishing. From softeners and water repellents to emulsions and lubricants, these solutions cater to the needs of formulators in the textile and leather industries. The Amino Fluids
0 views • 6 slides
Enhancing Security with Two-Factor Authentication (2FA) at University Library
Explore the implementation of Two-Factor Authentication (2FA) at the University Library for heightened security measures. This comprehensive system involves hardware tokens, mobile devices, and temporary passcodes, ensuring secure access to sensitive data and systems. Learn about the processes and r
0 views • 9 slides