Comprehensive Guide to FERC Order 676j Managed Encumbrance Process
This comprehensive guide provides step-by-step instructions on managing encumbrances under FERC Order 676j. Learn about creating new encumbrances, untagged pseudo-ties using PTP or NITS TSR, and accessing dynamic notifications within the system. Detailed images and clear explanations make this guide
1 views • 25 slides
Pseudo-Scientific Ideas About Race and Eugenics in the USA and Australia
The eugenics movement in the USA, under leaders like Charles Davenport, promoted the separation of "inferior" races to prevent genetic contamination of the "superior" groups. Laws like the Virginia Racial Integrity Act enforced racial segregation and punished interracial marriages. This era saw the
1 views • 20 slides
MIPS CPU Design Using Verilog and Instruction Set Architecture Overview
Explore the world of MIPS CPU design using Verilog with a deep dive into Instruction Set Architecture (ISA), SPIM instruction formats, addressing modes, and more. Learn about the key components such as Program Counter (PC), Instruction Memory (IM), Register Files (RF), Arithmetic Logic Unit (ALU), D
1 views • 29 slides
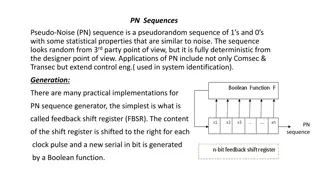
Pseudo-Noise Sequences and Applications
Pseudo-Noise (PN) sequences are deterministic yet appear random, with applications in various fields such as communication security, control engineering, and system identification. Generated using shift registers, they exhibit statistical properties akin to noise. Linear and nonlinear feedback shift
2 views • 19 slides
Patch Bundle Mode Walkthrough for Device Configuration
Explore the Patch Bundle Mode walkthrough consisting of flowcharts and pseudo code examples for controlling a device's patch mode, downloading configurations, and changing device modes. The content provides a detailed guide on using commands to initiate patch burst mode, specify I2C addresses, and t
0 views • 4 slides
Analysis of Vance Joy's "Riptide" Music Video and Intertextual References
Australian singer-songwriter Vance Joy, signed to Atlantic Records, released "Riptide" as his first single in the USA, known for its unique music video style. The video, directed by Dimitri Basil and Laura Gorun, has garnered over 250 million views on YouTube. This analysis delves into the economic
4 views • 7 slides
Exploring Monte Carlo Simulations and Probabilistic Techniques
Dive into the world of Monte Carlo simulations and probabilistic methods, understanding the basic principles, the Law of Large Numbers, Pseudo-Random Number Generators, and practical Monte Carlo steps. Explore topics like conditional probability, basic geometry, and calculus through engaging exercis
3 views • 10 slides
Overview of Alkaloids: Classification, Sources, and Characteristics
Alkaloids are organic nitrogenous compounds found in plants with physiological activity. They may also contain elements like oxygen, sulfur, chlorine, and phosphorus. Alkaloids can be sourced from plants, animals, bacteria, fungi, or industrial synthesis. Their names can be derived from plant names,
0 views • 19 slides
Reasonable Arguments vs. Pseudo-Arguments
The provided content focuses on distinguishing between reasonable arguments and pseudo-arguments through thought-provoking questions such as the ethical treatment of animals, city subsidies for sports venues, and subjective opinions on aesthetics. It also explains the structure of an argument, highl
0 views • 18 slides
Pseudo Code and Flow Charts for Algorithm Analysis
Explore the concepts of pseudo code and flow charts for analyzing algorithms, problem-solving, and understanding space and time complexity. Learn about basic elements of pseudo code, assigning operations, and writing effective pseudo code statements in a clear and structured manner. Discover the imp
0 views • 26 slides
Algebraic Solutions for Two-Dimensional Adjoint QCD
Two-dimensional adjoint QCD is explored with a basis-function approach aiming to achieve single-particle states over cluttered multi-particle states. The algebraic solution involves t'Hooft-like integral equations and pseudo-cyclicity considerations to address parton number violation and boundary co
0 views • 22 slides
Phonic Screening Checks Bank of Words 2012-2019
Explore real and pseudo words featuring various phonetic patterns such as CVC, CCVC, CVCC, CVVC, CCVCC, VCC, CVVV, CCVVV, CVCV, CCVCV, CCCVCC, CCCVC, CCCVV, and more from Phonic Screening Checks between 2012 and 2019.
0 views • 420 slides
Exploring Pseudo-Goodwin Cycles in a Minsky Model
This paper delves into the dynamics of Pseudo-Goodwin cycles within a Minsky model, examining the counter-clockwise movement of output and wage share. It distinguishes between true Goodwin cycles and pseudo variants, highlighting the role of income distribution, debt, and demand in shaping economic
0 views • 27 slides
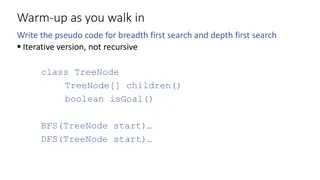
AI Search Algorithms: BFS and DFS Pseudo-code Iterative Version
Explore the iterative versions of Breadth First Search (BFS) and Depth First Search (DFS) with pseudo-code examples implemented for class TreeNode. Understand the concept of TreeNode, children() function, isGoal() method, and apply BFS and DFS starting from TreeNode start.
0 views • 53 slides
Post-Quantum Security of Hash Functions Explained
Explore the intricacies of post-quantum secure hash functions, their properties, surprises, and implications in quantum settings. Delve into collision resistance, pseudo-random generators, efficient signatures, and more, presented by Dominique Unruh from the University of Tartu.
0 views • 23 slides
Key Learnings from Exams: Algorithm Strategies & Representations
Exploring vital lessons from exams, including algorithm development tips, representation examples, and pseudo-code explanations. Understand the importance of reading questions carefully, creating precise steps, and terminating algorithms effectively. Dive into the world of algorithms, pseudo-code, a
0 views • 44 slides
Lessons Learned from On-Orbit Anomaly Research
The On-Orbit Anomaly Research workshop held at the NASA IV&V Facility in 2013 focused on studying post-launch anomalies and enhancing IV&V processes. The presentations highlighted common themes like Pseudo-Software Command Scripts, Software and Hardware Interface issues, Communication Protocols, and
0 views • 55 slides
Pseudodeterministic Algorithms and Their Application in Search Problems
Pseudodeterministic algorithms provide a unique approach to the search problem associated with binary relations, offering an error reduction technique while sacrificing the ability to approximate the average value of a function. By introducing m-pseudodeterministic and pseudo-pseudodeterministic alg
1 views • 6 slides
Muscled Milton: The Journey of Redemption in the Indian Ocean Trade Route
Muscled Milton, a young boy scarred by bandit attacks, embarks on a journey through the Indian Ocean Trade route with his mentor, Goodwin. Facing perilous encounters and seeking to avenge his parents' death, Milton's quest for redemption unfolds in cities like Hangzhou, Malacca, and Constantinople.
0 views • 21 slides
DePauw University Medicare Benefits Program Overview
This presentation details the DePauw University Medical & Rx Benefits Program for Medicare retirees, presented by Justin Goodwin from Amwins Group Benefits. It covers the agenda for the day, introduction to the program, information about Amwins Group Benefits, DePauw University's role in the Medicar
1 views • 39 slides
Introduction to Psychology: Understanding Behavior and Mental Processes
This material covers key aspects of psychology including the definition of psychology, its scientific nature, comparison with fake sciences, the birth of modern psychology, and different perspectives in psychology such as learning, biological, cognitive, and sociocultural. It delves into the roots o
0 views • 42 slides
Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Introduction to Y86 Instruction Set Architecture
Y86 Instruction Set Architecture is a simplified pseudo-language based on x86 (IA-32) architecture. It involves implementing the Fetch-Decode-Execute cycle, where instructions are fetched from memory, decoded, and executed. The Y86 ISA offers a simpler set of instructions and formats compared to x86
0 views • 25 slides
Migrating Pre-Banner Hardcopy Forms into the Digital Age at Kent State University
Kent State University's Division of Information Technology presents a successful solution for migrating pre-Banner hardcopy forms into a digital format. Discover the process of creating pseudo IDs to handle document indexing without new Banner IDs. Learn about the technology used and the strategic a
0 views • 41 slides
Exploring Pseudo-Complex General Relativity for Gravitational Waves
Delve into the concept of pseudo-complex General Relativity (PC-GR) as an alternative theory to Einstein's General Relativity. The study considers algebraic extensions, weak field limits, and the extension of metrics in momentum-energy space. By analyzing predictions and implications, this research
0 views • 21 slides
Understanding the Language of Advertising Claims
The language of advertising claims, as explored by Jeffrey Schrank, delves into how ads make assertions about product superiority. It discusses misleading versus true claims, the prevalence of pseudo-information for parity products, and various types of claims like Weasel, Water is Wet, Unfinished,
0 views • 13 slides
Overview of Assembly Language Programming in 8086 Architecture
Assembly language programming in the 8086 architecture involves writing case-sensitive instructions represented by statements. Each statement corresponds to an 8086 instruction or an assembler directive. Instructions follow a specific format with optional components like labels and comments. Assembl
0 views • 31 slides
Typed Assembly Language and Type Inference in Program Compilation
The provided content discusses the significance of typed assembly languages, certifying compilers, and the role of type inference in program compilation. It emphasizes the importance of preserving type information for memory safety and vulnerability prevention. The effectiveness of type inference me
0 views • 17 slides
Insights on Magnetic Field Strength for Electron Ion Collider
Discussion on the requirements and advantages of different magnetic field strengths in detector solenoids at the Electron Ion Collider, emphasizing the impact on particle tracking, momentum resolution, and detector space needs. The analysis compares 1.5T and 3T fields, highlighting the implications
0 views • 9 slides
The Right Way to Code Simulation Studies in Stata
Simulation studies in Stata involve using (pseudo) random numbers to generate data from a distribution for studying statistical methods. This process helps to evaluate different scenarios and understand the properties of statistical techniques. Key components like ADEMP (Aims, Data-generating mechan
2 views • 18 slides
Pseudo-Tie Business Procedure Tariff Administration, August 2017
Pseudo-tie business procedure tariff administration from August 2017 outlines the purpose, implementation, and types of pseudo-ties in the energy industry. It covers dynamic transfers, pseudo-tie procedures, and various stakeholder involvements. The document details the process of implementing pseud
0 views • 11 slides
Rights and Responsibilities in Protecting Confidential Sources
Understanding the legal and ethical considerations surrounding the protection of confidential sources in journalism and beyond. Exploring landmark cases, such as Goodwin v. United Kingdom, and the implications for press freedom. Highlighting the universal right of all social communicators to safegua
0 views • 10 slides
Pseudo-Tie Entry in Electric Industry Registry
Explore the requirements and measures of NERC Standard INT-004-3.1 for dynamic transfers in the electric industry. Learn about data fields required for pseudo-tie entry and approval methodology in the Electric Industry Registry. Discover the publishing schedule for EIR entries and the approval proce
0 views • 6 slides
Ordering of Pseudo Dispatch Instructions for QBOA
This document outlines the specific order in which Pseudo Dispatch Instructions (DIs) are to be arranged for QBOA in scenarios where multiple instructions are issued simultaneously. The order prioritizes certain instructions to maintain consistency and alignment with system implementation rules.
0 views • 11 slides
Pseudo Code: A Beginner's Guide to Organizing Programs
Pseudo code is a helpful way to organize your program logic before actual coding. It provides a structured outline from inputs to outputs, focusing on step-by-step guidelines that are not language-specific. This guide covers the basics of pseudo code, including general guidelines, steps to pseudo co
0 views • 29 slides
Evolution of Communication Systems: From Bandwidth Division to Spread Spectrum
Third-generation communication systems utilize Pseudo-Noise (PN) codes to share bandwidth without interference, while first and second-generation systems divide bandwidth into smaller channels. PN codes are vectors with 1s and -1s, orthogonal to each other. Users transmit data using PN coding, combi
0 views • 14 slides
Overview of Ceph Distributed File System
Ceph is a scalable, high-performance distributed file system designed for excellent performance, reliability, and scalability in very large systems. It employs innovative strategies like distributed dynamic metadata management, pseudo-random data distribution, and decoupling data and metadata tasks
0 views • 42 slides
The Case of the Missing Keys
In this amusing tale, Kylee Goodwin narrates the comical ordeal of her mum losing her keys yet again. The family embarks on a frantic search through various rooms, only for the keys to be found hanging safely on their hook by Dad in the end. A lighthearted story of everyday mishaps and the relief of
0 views • 13 slides
Handling Label Noise in Semi-Supervised Temporal Action Localization
The Abstract Semi-Supervised Temporal Action Localization (SS-TAL) framework aims to enhance the generalization capability of action detectors using large-scale unlabeled videos. Despite recent progress, a significant challenge persists due to noisy pseudo-labels hindering efficient learning from ab
0 views • 30 slides
Analyzing Andrew Goodwin's Ideas in Music Videos Using Rihanna's "We Found Love
Explore Andrew Goodwin's concept that music videos are like advertisements, anchoring meaning and potentially more than just promotional tools. Discover how his 7 conventions apply to Rihanna's music video "We Found Love," examining the relationship between lyrics and visuals, editing to the beat, a
0 views • 11 slides