H3C GB0-601 Exam Preparation: What You Need to Know
Begin your preparation journey here--- https:\/\/bit.ly\/4c6E4N5 \ud83d\ude80. Access all the essential details to ace the H3C Certified Network Engineer for Server (H3CNE-Server) exam. Gather all the necessary information, including tutorials, practice tests, books, study materials, exam questions,
5 views • 19 slides
Resolving the “QuickBooks Unable to Connect to Remote Server” Issue
Resolving the \u201cQuickBooks Unable to Connect to Remote Server\u201d Issue\n\nStruggling with the \"QuickBooks Unable to Connect to Remote Server\" issue can disrupt your workflow. However, resolving this problem is crucial to ensure seamless access to your financial data. To tackle this issue ef
1 views • 4 slides
What's the Best Server for My Small Business?
Need the best server for your small business? VRS Technologies LLC offers top-notch Server Rental in Dubai. Call 0555182748 today.\n\nVisit: \/\/ \/computer-rentals\/reliable-server-maintenance-and-rental-in-dubai\/
2 views • 2 slides
What Is Proxy Card Access?
Explore the world of contactless access control. Learn how proxy cards work, their benefits, and common uses. Upgrade your security today!
1 views • 4 slides
Issues and Algorithms in Server Software Design
The content discusses fundamental issues in server software design such as connectionless vs. connection-oriented access, stateless vs. stateful applications, and iterative vs. concurrent server implementations. Various server algorithms like iterative and concurrent servers are explained with their
3 views • 44 slides
Understanding Client-Server Architecture
Client-server architecture is a computing model where a central server hosts and manages resources and services for client computers over a network. There are different types of clients and servers, each with unique characteristics and roles. This architecture offers various advantages and disadvant
3 views • 15 slides
Networked Server Verification Using Interaction Trees
This paper explores the process of specifying, testing, and verifying a networked server from C to interaction trees. It discusses the main contributions, including verifying a networked C program using VST and running in CertiKOS. The paper also delves into swap server specifications, observable be
0 views • 19 slides
How Can You Avoid Server Downtime with Server Rentals?
Server downtime can be costly, but in this PPT we explain the steps to avoid these risks. Our Server Rental Dubai services include top-quality servers and ongoing maintenance to keep your systems running smoothly. Contact VRS Technologies LLC today a
5 views • 2 slides
Optimum Solar Proxy for Long-Term Ionospheric Studies
The search for the best solar proxy for long-term ionospheric studies is ongoing due to the lack of consistent solar radiation data. Various solar proxies have been analyzed, and the use of Mg II for foF2 and F10.7 for foE has shown promising results, describing a high percentage of variance in the
1 views • 10 slides
Developing Proxy Indicators for Farm Profitability in Irish Agriculture
This study by Ciara O'Donovan focuses on developing and testing proxy indicators of farm profitability and efficiency measurements for knowledge transfer use on Irish farms. The research aims to identify indicators of farm performance, tailor them based on enterprise, scale, and seasonality, and tes
0 views • 20 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Proposal for AS Proxy Offer Optimization
This proposal aims to optimize AS proxy offers for TCPA and LCRA to ensure fair market prices without distorting market competition. It includes strategies like Proxy AS Price Floor Proposals and the use of L Factor to determine proxy AS offer prices. The goal is to make AS capacity available to ERC
0 views • 10 slides
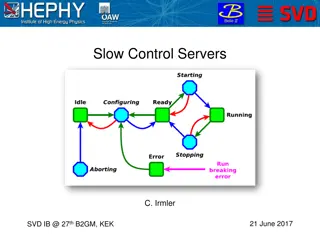
Slow Control Servers and Network Configuration for SVD Management
The documentation discusses the setup and requirements for slow control servers, network configuration, FADC server status, ENV server status, and general SC server status for SVD management. It outlines the need for backup servers, minimum server requirements, server specifications, procurement det
0 views • 11 slides
Understanding Modern Performance in SQL Server
Explore the evolution of performance in SQL Server with insights from Joe Chang, a seasoned SQL Server consultant. Delve into topics like query optimization, execution plans, CPU and memory advancements, storage technologies, and the significance of performance in today's data environment. Discover
0 views • 40 slides
Understanding Unidirectional Updatable Encryption and Proxy Re-Encryption
Unidirectional updatable encryption and proxy re-encryption are key concepts in secure cryptography deployments. Key management and rotation are essential for secure encryption schemes such as Proxy Re-Encryption (PRE) and Updatable Encryption (UE). PRE allows delegation of decryption abilities, whi
0 views • 16 slides
Enhancing Server State Detection in OpenStack for Immediate Host Fault Reporting
This blueprint proposes the development of a new API in Nova to promptly update the server state in OpenStack when a host fault occurs. The intention is to ensure reliability and real-time updates of server and host states for Telco-grade VIM, allowing users to take necessary actions swiftly in case
0 views • 5 slides
Accelerating the Mobile Web with Server-Aided Dependency Resolution
This research discusses the challenges of slow web page loads on mobile devices, presenting a solution utilizing server-aided dependency resolution. It covers the impact of slow loading times on mobile web dominance, the importance of efficient resource loading, and the key factors influencing fast
0 views • 29 slides
Understanding ASP.NET Server Controls and Their Importance
ASP.NET server controls play a crucial role in web development by allowing developers to create dynamic and interactive elements on a web page. These controls provide a way to encapsulate functionality, manage UI elements, and handle events efficiently on the server side. Learn about different types
0 views • 43 slides
Importance of Internet Security and Setting Up an Office Proxy Server
Learn how to enhance internet security by setting up an office proxy server to limit staff web surfing. Understand the risks associated with system flaws in Windows, Mac, browsers like Internet Explorer, Firefox, Chrome, and the immediate threat of Zero-Hour Attacks by hackers.
0 views • 28 slides
Understanding Client-Server Communication with Flask in Python
Explore the basics of implementing a client-server architecture using Flask in Python. Learn how to set up a server, create APIs, and interact with a client application. The process involves handling API calls, directing requests, and returning data to the client through the server.
0 views • 10 slides
Understanding Client-Server Paradigm in Distributed Systems
Client-server paradigm in distributed systems involves structuring systems as collaborating processes where clients request services from servers. The model follows a request/reply protocol, with servers providing centralized control of shared resources. Advantages include security and simplicity, w
1 views • 30 slides
Memory Resource Management in VMware ESX Server Overview
This presentation discusses the background of memory resource management in VMware ESX Server, focusing on server consolidation, memory abstractions, and memory reclamation techniques. It covers topics such as page sharing, memory allocation policies, and related work in the field. The use of VMware
0 views • 26 slides
Networking Solutions for Server Virtualization Challenges
This presentation discusses the challenges server virtualization technologies bring to data center networks. It demonstrates a standards-based approach to enhance the experience and economics in a virtualized environment. Topics include market drivers, limitations of legacy networks, simplification
0 views • 33 slides
Insight into Azure Server Subscriptions for CSP - September 2018
Explore the nuances of Server Subscriptions for Azure in CSP, including options for Windows Server and SQL Server virtual machines, Azure Hybrid Benefit, Reserved Instances, and more. Discover how customers can optimize prices based on workload types and licensing scenarios, all outlined in a compre
0 views • 37 slides
Optimal Power Allocation in Server Farms: A Study on Efficiency and Performance
This research study delves into the optimal allocation of power in server farms to enhance performance and efficiency. It explores the impact of power on server speed, response time, and workload distribution. The results aim to provide insights on minimizing mean response time and improving overall
0 views • 24 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Stepping Stone Detection at the Server Side: Real-Time Algorithm
An innovative real-time algorithm is introduced to detect the use of a proxy as a stepping stone from the server's perspective. The solution addresses the limitations of existing methods by focusing on TCP connection initiation. Previous research and vulnerabilities related to proxy servers and step
0 views • 37 slides
German eID and eIDAS: Secure Digital Identification Overview
The German eID system, including eIDAS integration, offers secure digital identification services through government-issued ID cards with embedded chips. It allows citizens and service providers to authenticate each other securely online. The system emphasizes interoperability and privacy protection
0 views • 16 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Proxy Access to Medications Implementation Stages
This document outlines the implementation stages for proxy access to medications. It covers agreements with healthcare providers, prerequisites including compliance and data sharing agreements, and systems configuration for access to medical records. The stages include setting up access for care pro
0 views • 7 slides
Proxy Voting in Indian Elections: Developments and Perspectives
India has seen progress in allowing proxy voting for Non-Resident Indians, with recent proposals to extend this privilege to overseas Indians. The initiative aims to enhance voter participation, especially for those residing abroad. While some political parties support proxy voting, concerns exist r
0 views • 35 slides
Understanding How the Web Works with Telnet and cURL Demonstrations at Millersville University
Explore the inner workings of the web through Telnet and cURL demonstrations in William Killian's CSCI 380 lecture at Millersville University. Discover how networking basics, proxies, and string manipulation in C play crucial roles in fetching content online. Dive into practical examples like manual
0 views • 37 slides
Enhancing Air Quality Forecasting with TEMPO Retrievals in Proxy Observing System
Improvements in Air Quality Forecast Skill (AQFS) are explored by assimilating TEMPO retrievals in a Proxy Air Quality Observing System (AQOS) using WRF-Chem/DART. The study focuses on benefits identified through a designed OSSE scenario, including application to the Front Range Air Pollution and Ph
0 views • 8 slides
Updates on GOES-R Aerosol Optical Depth Validation Activities
Generated proxy data algorithm enhancements for post-launch validation activities were discussed at the GOES-R AWG 2nd Validation Workshop in January 2014. The use of MODIS reflectances as a proxy for ABI to retrieve Aerosol Optical Depth (AOD) was emphasized, along with the importance of AERONET gr
0 views • 25 slides
Exploring High IOPS Applications and Server Configurations
Dive into the world of high IOPS applications, memory buffer configurations, and file server setups with a series of detailed images showcasing various server environments and code memory management. Discover the importance of optimizing IOPS for efficient data processing and explore advanced server
0 views • 16 slides
Setting Up a Proxy for Web Time Entry Approvers
Setting up a proxy is essential for Web Time Entry Approvers to ensure seamless approval processes when out of the office. Follow the outlined steps to grant proxy access and maintain security protocols. Remember to remove proxies when necessary and contact Payroll for any assistance.
0 views • 5 slides
Understanding Dynamic Proxy in Java for Type-Safe Proxy Objects
Learn about creating dynamic proxy classes in Java to implement interfaces at runtime without pre-compilation, enabling type-safe proxy object creation for method invocations. This allows for flexible and efficient handling of method calls through uniform interfaces.
0 views • 16 slides
Understanding Proxy ARP Implementation in IEEE 802.11ax
Proposed in September 2015, the document discusses the implementation of Proxy ARP with 802.11ax Access Points. It explains the Address Resolution Protocol (ARP), detailing how devices in a LAN communicate using MAC and IP addresses. The submission aims to provide comprehensive explanations on Proxy
0 views • 18 slides
Understanding Mobile Proxy Ecosystem: Privacy and Security Implications
The paper delves into the emerging trend of mobile proxy services, specifically focusing on the use of mobile devices as proxy peers. It addresses the security and privacy concerns associated with this practice, highlighting the potential risks posed to end-users. The study offers novel insights int
0 views • 21 slides
Understanding Content Distribution Networks and P2P File Sharing in Advanced Computer Systems
Exploring the challenges of single-server setups, skewed web traffic popularity, web caching techniques like forward and reverse proxies, and the role of proxy caches in optimizing content delivery and reducing server costs.
0 views • 27 slides