PowerPoint Slides Import Instructions
Learn how to import slides from your old PowerPoint presentation into a new template, ensuring they match the correct theme. Follow the step-by-step guide provided to seamlessly transition your content and maintain accessibility features. Additional tips on using the template effectively are include
2 views • 43 slides
5G NR Traffic QoS Management: Multi-Layer System View & End-to-End Evaluation
5G NR technology emphasizes enhanced QoS for XR traffic, including AR, VR, and Cloud Gaming. This research delves into handling QoS for XR/CG traffic at various layers, proposing QoS control mechanisms at the application and MAC layers, along with an evaluation of these approaches using a simulator.
6 views • 14 slides
Rwanda HIE Patient Identity Management System Overview
The Rwanda Health Information Exchange (HIE) system focuses on patient identity management to uniquely identify individuals seeking healthcare across the country. By maintaining a set of identifiers in the client registry and avoiding duplication of patient records, the system ensures efficient and
12 views • 8 slides
How to Find and Update QuickBooks License Number And Product Key
Finding and updating your QuickBooks license number and product key is essential for maintaining legal use of the software and ensuring access to updates and support from Intuit. The license number and product key are unique identifiers that authenticate your copy of QuickBooks. This guide will walk
1 views • 5 slides
Understanding DoDAACs in Department of Defense Operations
DoDAACs (DoD Activity Address Codes) are crucial identifiers in the Department of Defense, representing offices, organizations, and deployments. They contain information on addresses and points of contact, serving as essential components in the supply chain for managing shipments and billing. Change
1 views • 59 slides
Amateur Radio Licensing Regulations and Call Signs in the UK
Learn about the licensing regulations, privileges, call sign formats, secondary identifiers, and addresses for amateur radio operators in the UK. Discover the differences between Foundation, Intermediate, and Full license classes, as well as the various call sign formats used in England. Explore the
0 views • 87 slides
Fascinating Facts About Golden Eagles - Discover the Majesty of North America's Largest Bird of Prey
Learn intriguing details about golden eagles, including their lifespan, diet, wingspan, and key identifiers. Explore their habitat range, unique adaptations, and comparisons with other raptor species like bald eagles. Appreciate these magnificent birds as vital contributors to their ecosystems.
0 views • 7 slides
IEEE 802.11-20-0745r0 Identifier Privacy Service
In IEEE 802.11-20-0745r0, the focus is on protecting identifiers to enhance privacy in wireless networks. The proposal suggests using ECIES for identifier protection, covering various identifiers like password identifiers and PMKIDs. By implementing a scheme similar to 3GPP and IETF standards, the s
4 views • 7 slides
GHSP IOP & ESLP Progress Updates - December 2023
This update provides details on GHSP IOP and ESLP progress as of December 4, 2023. It includes information on remaining test cases, passes logged, mandatory test cases, and more. The document covers test purposes, test case identifiers, passes remaining, and specific test procedures related to healt
0 views • 6 slides
Understanding Compustat Global in WRDS: Key Insights and Data Overview
Compustat Global in WRDS offers a comprehensive collection of over 500 company-level fundamentals for publicly traded companies in global markets, covering more than 80 countries. The data includes income statements, balance sheets, cash flows, market data, and more, with no survivorship bias. With
1 views • 27 slides
Federal Agencies Guidance on Ethics, Compliance, and Audit Services under NSPM-33
The White House OSTP released guidance for federal agencies to implement NSPM-33 focusing on disclosure requirements, digital identifiers, consequences for violations, information sharing, and research security programs. The guidance emphasizes supporting open scientific inquiry and nondiscriminator
0 views • 10 slides
Discussion on CID 35 and Proposed Resolutions in IEEE 802.11-23/0623r2
Presentation by Mark Hamilton from Ruckus/CommScope discussing consensus on CID 35 in TGbh CC41, including proposed updates, comments, and resolutions regarding opaque identifiers, Device IDs, and network procedures. Various discussions held on identifier constructions and terminology.
1 views • 5 slides
Understanding Mode-S Radar Operations and Identifiers
This simplified explanation delves into the fundamental principles of radar operations, focusing on Primary and Secondary radar systems, including Mode A/C and Mode S functionalities. It covers radar interrogation, replies, and the significance of radar identifiers (II and SI codes) in managing over
0 views • 19 slides
Understanding FERPA: Family Educational Rights and Privacy Act
FERPA, the Family Educational Rights and Privacy Act, is a federal law that safeguards the confidentiality of student educational records and privacy rights. It grants parents rights until the student turns 18 or enters a postsecondary institution. Students can inspect records, seek amendments, cons
0 views • 19 slides
Understanding Budget Reports and Fund Accounting Basics
Explore the world of budget reports and fund accounting through visual representations, learning about fund accounting concepts, account structure, and the importance of organizing accounting records. Gain insights into different types of funds and their numeric identifiers. Delve into the big pictu
0 views • 66 slides
Emerging Global Trends in IoT by Davis M. Onsakia
The Internet of Things (IoT) is a system where various devices, machines, and objects are interconnected with unique identifiers to transfer data without human interaction. This concept involves connecting devices to the internet or to each other, leading to improved efficiency, better customer serv
0 views • 26 slides
Understanding Basic Elements of Python Programs
Explore the fundamental aspects of Python programming such as literals, assignments, datatype conversion, identifiers, and expressions. Learn how to work with variables, values, and simple Python commands effectively.
0 views • 38 slides
Understanding HIPAA Compliance in Research Settings
Health Insurance Portability and Accountability Act (HIPAA) plays a crucial role in safeguarding protected health information (PHI) in research conducted by covered entities like UConn Health. This content covers the definitions of PHI, the 18 identifiers defined by HIPAA, common methods to comply w
0 views • 11 slides
Distributed Algorithms for Leader Election in Anonymous Systems
Distributed algorithms play a crucial role in leader election within anonymous systems where nodes lack unique identifiers. The content discusses the challenges and impossibility results of deterministic leader election in such systems. It explains synchronous and asynchronous distributed algorithms
2 views • 11 slides
Setting up and Running Postal Code Conversion File Plus (PCCF+) - Step-by-Step Guide
In this detailed guide prepared by Statistics Canada, you will learn how to set up and run the Postal Code Conversion File Plus (PCCF+). The process involves creating an input file with unique identifiers and postal codes, producing a new dataset, saving it for import, importing the data to SAS, tra
0 views • 21 slides
Streamlining Customer Service Management with Digital Identifiers
Revolutionize your customer service experience by leveraging cloud-based digital identifiers for unique customer identification, service validation, and access control. Seamlessly create, personalize, and send identifiers to customers via mobile and email, enabling automated service activation post-
0 views • 15 slides
Understanding Data Linkages for DaVINCI
Explore the intricacies of patient identifier linkages and linking methodologies for direct care data in the context of DaVINCI. Learn about different systems such as CHCS, AHLTA/CDR, MHS Genesis, and how they utilize identifiers like EDIPN, SSN, and more to establish unique patient records. Discove
0 views • 29 slides
Unveiling the Realities of Privacy in App Usage
Exploring the complexities of privacy policies, the disclosure of user data by apps, and the implications of mobile tracking. Learn how AppCensus assists parents in understanding app data collection practices and the risks associated with sharing persistent identifiers. Discover how third parties ut
0 views • 25 slides
Framework for Research Data Management and Persistent Identifiers at Waipapa Taumata Rau
This research delves into the integrated framework for Research Data Management (RDM) and the initiatives around Persistent Identifiers (PIDs) and ORCID implementation at Waipapa Taumata Rau. It explores the background, aims, and priorities of the RDM Programme for 2022-2024, focusing on improving R
0 views • 9 slides
Proposal for Network-Generated Device ID Scheme in IEEE 802.11
A scheme proposing the generation of network-assigned device identifiers for STAs in IEEE 802.11 networks is outlined. The network assigns unique IDs to devices, allowing flexibility in ID formats across different networks. STAs receive and use these IDs for tracking purposes. The process involves c
0 views • 9 slides
Exact Identifier Matching Workflow for PAPR Database Management
Management system, PAPR, supports serials collections by ensuring accurate metadata and holdings information. The workflow involves adding serial holdings by matching primary identifiers like ISSN or OCLC#. The process includes validation, search, retrieval, and ensuring data integrity through unmed
0 views • 8 slides
Understanding Health Plan Identifiers: HPID vs. OEID
Health Plan Identifiers (HPIDs) play a crucial role in the healthcare industry by uniquely identifying health plans during electronic transactions. This article delves into the significance of HPIDs, the distinction between Controlling Health Plans (CHP) and Subhealth Plans (SHP), and the comparison
0 views • 17 slides
Understanding Naming Systems in Distributed Systems
Entities in distributed systems are uniquely identified using names, addresses, and identifiers. Naming systems assist in name resolution and can be categorized into flat, structured, and attribute-based naming. Flat naming uses random strings as identifiers, and various mechanisms such as broadcast
0 views • 21 slides
Key Concepts in AP Computer Science A Exam Review
Essential topics covered in AP Computer Science A Exam include identifiers, primitive data types, number representation, final variables, and arithmetic operators. Recognizing the basics, such as types, identifiers, operators, and control structures, is crucial for success in the exam. Understanding
0 views • 100 slides
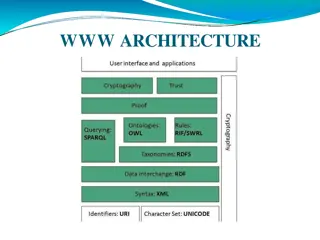
Understanding Web Technologies: From Identifiers to FTP
Explore the world of web technologies from identifiers and character sets to data interchange frameworks and ontologies like OWL. Learn about semantic web layers, cryptography, and FTP protocol objectives. Discover how these technologies work together to create a seamless online experience.
0 views • 72 slides
Understanding Unix Process Management in Computer Systems II
This overview delves into the creation, termination, memory layout, and dynamic memory management of Unix processes in Computer Systems II. It covers the distinctions between code, executables, and processes, the memory layout of Unix processes, management of heap memory using malloc and free functi
0 views • 27 slides
B2HANDLE: Managing Digital Object Identifiers for Data Persistence
B2HANDLE is a service for minting and managing persistent identifiers (PIDs) to facilitate common operations on digital objects across infrastructures. The system enables automated management of data objects and metadata, facilitates machine-driven workflows, and supports the construction of PID and
0 views • 17 slides
Understanding Persistent Identifiers (PIDs) and Handling Digital Objects
Explore the significance of Persistent Identifiers (PIDs) in assigning unique identifiers to digital objects, ensuring reproducibility, and facilitating reliable data management. Learn about versioning, PID binding, strategies for assigning PIDs, and the evolving role of repositories in managing dig
0 views • 6 slides
Understanding Persistent Identifiers (PIDs) in Research and Data Management
Persistent Identifiers (PIDs) play a crucial role in establishing long-lasting digital references for objects, contributors, and organizations in the realm of research and data management. This introduction delves into the significance of PIDs, focusing on their role in identifying and connecting di
0 views • 13 slides
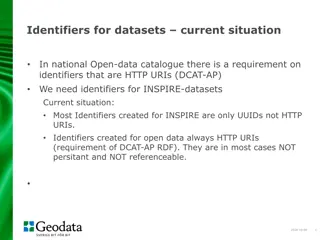
Recommendations for Creating Identifiers in Data Catalogues
National data catalogues have specific requirements for identifiers, such as using HTTP URIs for open data datasets. While most INSPIRE datasets only have UUID identifiers, adhering to the DCAT-AP standard recommends using HTTP URIs. Recommendations for creating identifiers in the geodata sector are
0 views • 5 slides
Understanding Data Modeling: Key Concepts and Applications
Explore the fundamentals of data modeling through concepts like entities, attributes, identifiers, and their real-world applications, including examples related to Greta Garbo, modeling reality, and global legal entity identifiers. Discover how to design data models for diverse scenarios, such as re
0 views • 57 slides
Piloting Unique Identifiers for Geospatial Data - Nordic Forum Presentation
Presentation at the Nordic Forum for Geography and Statistics on piloting unique identifiers for geospatial data by Tuuli Pihlajamaa. The agenda included terms used, background for the pilot, aims, results, and future plans. Detailed discussions on terms like URI, RDF, JHS 193, INSPIRE guidelines, a
0 views • 15 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Understanding Human Authentication and Digital Identity
Explore the complexities of human authentication, classes of countermeasures, principles, personal and digital identity, and aspects of digital identity. Dive into the philosophical problem of personal identity, different types of identities, attributes, identifiers, verifiers, and the process of id
0 views • 33 slides
Understanding Facial Recognition Technology and Applications Today
Explore the world of facial recognition technology through insights on its applications in various sectors, the process of identifying individuals based on facial characteristics, the distinction between face biometric templates and identifiers, and a case study on why a suspect wasn't identified by
0 views • 17 slides