How to Protect Your On-Demand App from Cyberattacks and Data Breaches
On-demand app development solutions provide convenient services but also carry cybersecurity risks like hacking, malware, and data breaches. This comprehensive guide explores best practices to secure on-demand apps and protect sensitive user data. Learn how encryption, multifactor authentication, ac
0 views • 4 slides
Decolonising Approach to Policy Impact: Lessons for Research Culture
Engaging with policy in Global South countries and addressing power imbalances and historical complexities is crucial in policy impact and research culture. The Institute for Policy and Engagement at the University of Nottingham focuses on decolonising policies and research practices to promote equi
0 views • 19 slides
Practical Guide to Writing Policy Briefs for Research Engagement with Policy Makers
Effective communication with policy makers is essential for influencing policy decisions. This practical guide offers advice on creating high-quality policy briefs based on research evidence, providing tools and indicators to measure impact.
0 views • 15 slides
Privacy Breach Management Guide by Health PEI
Understanding, Preventing, and Managing Privacy Breaches in Healthcare: Learn about what constitutes a privacy breach, how to prevent breaches, steps to determine and manage breaches effectively, including containment, investigation, and notification processes.
0 views • 10 slides
Gender Equity and Social Inclusion Policy Overview
This overview highlights the Gender Equity and Social Inclusion (GESI) Policy promoted by the Department of Personnel Management in Papua New Guinea. The policy aims to ensure fair participation of disadvantaged individuals in employment and opportunities, along with social inclusion to realize the
1 views • 18 slides
Cyber Data Breach Review_ A Comprehensive Insight with LDM Global in the USA
In today's digital landscape, cyber data breaches pose significant threats to organizations of all sizes. A cyber data breach can result in severe financial losses, reputational damage, and legal ramifications. To navigate these challenges effectively, companies turn to expert services like those pr
1 views • 13 slides
Overview of Policy Service Node (PSN) Architecture
The Policy Service Node (PSN) architecture consists of various key components such as Policy Administration Node (PAN), Monitoring Node (MnT), Inline Posture Node (IPN), and Multi-Function Node. These components work together to enable efficient policy management and network monitoring within a netw
1 views • 5 slides
Understanding Policy-Making Process for Health Improvement
Policy-making involves defining policy, recognizing its complex nature, identifying windows of opportunity, and framing health issues. The policy-making cycle includes stages like agenda setting, formulation, and implementation. Alignment of problems, policies, and politics is crucial for effective
1 views • 12 slides
Effective Writing and Policy Briefs: Enhancing Impact in Policy-making
A policy brief is a compelling document designed to influence decision-makers by outlining policy alternatives and courses of action. Discover the value of policy briefs, effective characteristics, and strategies for agenda setting and policy formulation in this comprehensive module.
1 views • 22 slides
Understanding Theories of the Policy Cycle in Policy Analysis
The policy cycle theory describes the evolution of policy issues from inception to evaluation, impacting scientific research and policy formulation. It outlines stages from the 1950s, influenced by Lasswell's seven-stage model, serving as a framework for organizing policy processes. Despite the line
3 views • 30 slides
Financial Services Commission Special Audit Report 2023 Findings
The Financial Services Commission (FSC) underwent a special audit in response to allegations of human resources and procurement malpractices. Key findings included positions created without approval, vacancies filled without advertisement, and other concerning practices. Detailed assessments were co
0 views • 13 slides
Lessons from Recent Data Breaches: Insights and Strategies
This presentation covers the landscape of data breaches, leading causes, and steps to take when facing a cyber incident. It discusses the impact of large-scale cyber attacks by external threat actors, outlines key considerations for response, and provides tips for notifying affected individuals to m
2 views • 20 slides
National Youth Policy 2030 Presentation to the Portfolio Committee
The National Youth Policy 2030 presentation provides an update on the approved policy, focusing on the youthful population in South Africa and the importance of youth development. The policy aims to address past injustices and current challenges, empowering young people to drive positive change. Pas
1 views • 19 slides
Understanding Public Policy-Making Process in Government
Explore the intricacies of public policy-making in government administration, focusing on the importance of providing equal access to basic services for all citizens. Delve into the nature of public policy, factors influencing policy-making, and the procedural aspects involved, including planning, o
0 views • 36 slides
Ransomware and Data Breaches in Public Libraries Analysis
Delve into the world of ransomware and data breaches in public libraries, exploring the definitions of ransomware and data breaches, the potential impacts on libraries, the financial losses incurred, and the value of library records. Understand the risks, implications, and consequences associated wi
0 views • 21 slides
Enhancing University Information and Records Management for Strategic Advancement
The University's continuous improvement strategy for 2020 focuses on managing information and records effectively to mitigate risks associated with data processing. Information is deemed a critical asset, and risks range from data breaches to operational disruptions. To address these challenges, an
1 views • 21 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Special Audit Report on Caribbean Maritime University (CMU) - December 2019
The special audit report on Caribbean Maritime University revealed unsatisfactory HR practices, poor governance, deficiencies in oversight, procurement breaches, and mismanagement of contracts. Issues included inconsistent HR practices, unapproved emoluments, infrequent council meetings, and inadequ
0 views • 12 slides
Understanding Response Patterns to Data Breaches in Firm IT Investment
This research explores how firms reallocate internal IT resources in response to security breaches and the impact of these allocation patterns on future firm performance. It delves into the allocation of IT budgets, changes in IT staffing, and examines antecedents and consequences of security breach
0 views • 47 slides
Essential Steps for Personal Data Breach Management
Detect, identify, and respond effectively to personal data breaches by containing the breach, assessing risks, notifying relevant authorities and affected individuals, and implementing measures to prevent future occurrences. Debunk common myths surrounding breach reporting and focus on mitigating ne
0 views • 5 slides
Green Industrial Innovation Policy Making in Europe by Reinilde Veugelers
Shifting economies towards green industrial innovation in Europe is a significant transformation that requires reconciling various objectives like decarbonization, economic growth, job creation, and global competitiveness. The role of innovation in green industrial policy is crucial for delivering n
2 views • 13 slides
Louisiana Coastal Flooding Litigation Overview
The content discusses various aspects related to the Katrina Canal breaches consolidated litigation in Louisiana, focusing on the legal implications, failures in flood control measures, geology of coastal Louisiana, coastal elevations, and the impact of canal breaches on flooding in the region. It a
1 views • 30 slides
Challenges in Policy Implementation and Lessons Learned
The content discusses the challenges faced in policy implementation, focusing on the gap between policy design and execution. It highlights key steps in policy-making, reasons for implementation failures, and factors influencing successful policy outcomes. Examples from Zambia's National Science and
0 views • 14 slides
Unpacking the RIA Process for Effective Policy Implementation
Delve deeper into the RIA process to understand its technical capacity and policy implications. This group exercise focuses on setting clear objectives, analyzing key policy issues, and creating a mock RIA process template tailored to the Indian context. Participants explore real-world problem-solvi
0 views • 14 slides
Privacy Breach Response and Reporting under the Health Information Act
Understanding privacy breaches under the Health Information Act (HIA) is crucial for organizations dealing with health data. This document outlines what constitutes a breach, mandatory notification requirements, factors to consider in determining risk of harm, and potential offences and penalties fo
0 views • 21 slides
Importance of Privacy & Data Security Training in Healthcare
Privacy and data security training in healthcare is crucial due to the interconnected nature of the industry, putting patient information at risk. Breaches have resulted in significant financial losses, emphasizing the need for mandatory training to safeguard patient privacy. Understanding responsib
0 views • 27 slides
Understanding PCI-DSS Compliance and Requirements
The Payment Card Industry Data Security Standard (PCI-DSS) is crucial for protecting cardholder data from fraud and breaches. This standard entails six objectives with specific requirements aimed at building a secure network, protecting data, maintaining vulnerability management, implementing access
0 views • 37 slides
HIPAA and Research Data Security Training for Researchers at BU Charles River Campus
This training provides essential information on how HIPAA impacts human subject research, the importance of protecting health data, reporting breaches, and utilizing BU resources. It also covers implications of HIPAA in research, national standards, consequences of breaches, and scenarios where HIPA
0 views • 37 slides
NHS Sussex Conflicts of Interest Breach Register Summary May 2024
NHS Sussex manages conflicts of interest breaches by recording and publishing them on their website. Breaches are documented with details of the nature of the breach and actions taken. In May 2024, no breaches were reported. Previous months had breaches due to late declarations of interest. Staff we
0 views • 5 slides
Compass Commission: Public Policy in Chile Based on Rigorous Scientific Evidence
The Compass Commission, initiated by the Ministry of Planning of Chile in collaboration with J-PAL, aimed to identify social policy challenges in Chile and propose innovative public policies for evaluation through randomized control trials. The initiative involved academic members, international and
0 views • 10 slides
Implementation of Cell Phone Policy to Improve English Grades at Richwoods High School
Implementation of a cell phone policy at Richwoods High School was driven by the need to enhance English grades and academic performance. The policy aims to reduce distractions and disruptions caused by non-academic cell phone use in classrooms. Results from previous semesters showed significant imp
0 views • 9 slides
Raw Materials Policy of the Czech Republic: History, Modernization, and Challenges
The Raw Materials Policy of the Czech Republic has undergone significant changes and challenges throughout its history. From the approval of the previous policy in 1999 to the recent modernization efforts in 2015, political and environmental factors have played a crucial role in shaping the current
0 views • 13 slides
Theories and Strategies for Effective Policy Change
Explore the intricacies of strategic planning, outcome mapping, change theories, policy windows, and more in the realm of policy entrepreneurship and advocacy. Learn about key concepts such as large leaps theory, policy streams theory, and how think tanks can influence policy decision-making process
0 views • 43 slides
Morality in UK Drug Policy: Policy Constellations Analysis
Morality plays a significant role in shaping drug policy in the UK, as revealed by the research conducted by Professor Alex Stevens at the University of Kent. The study investigates the moral commitments underlying different policy positions in UK drug policy debates, highlighting five ethico-politi
0 views • 19 slides
Industrial Policy: The Old and The New - Insights by Dani Rodrik
Industrial policy, as presented by Dani Rodrik in May 2019, emphasizes the importance of empirical work, the differences between old and new policies, and the targets industrial policy should focus on. The theoretical arguments for industrial policy highlight market imperfections, learning spillover
0 views • 26 slides
VAST: A Unified Platform for Interactive Network Forensics
VAST is a comprehensive platform designed for interactive network forensics, addressing the increasing frequency of security incidents and large-scale data breaches. It aims to provide solutions for detecting, analyzing, and preventing breaches efficiently, with features like data exploration, query
0 views • 17 slides
Data Breaches and Privacy Concerns: An Overview
Privacy expert Marilyn Prosch, Ph.D., sheds light on the significant issue of privacy, emphasizing recent data breaches in various institutions and outlining some alarming cases where sensitive information was compromised. The incidents range from stolen laptops and office break-ins to mishandling o
0 views • 34 slides
Understanding Policy Formulation: Key Concepts and Approaches
Policy formulation is a crucial step in the policy-making process, involving identifying and crafting policy alternatives to address various issues. This phase requires participants to define policy problems, develop alternatives, and select the most feasible solutions based on criteria such as feas
0 views • 12 slides
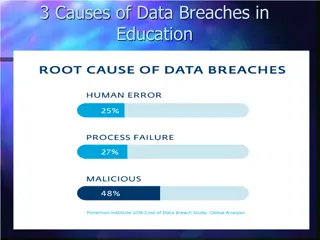
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Legal Issues in Data Breaches and Confidentiality Violations
The content covers various scenarios related to breach of confidence, liability of businesses in safeguarding data, and legal causes of action in case of data breaches. It discusses real-life analogies and legal principles concerning the mishandling of confidential information, including a case stud
1 views • 23 slides