Revisiting LDPC Rate Matching in IEEE 802.11 for Improved Performance
The document discusses revisiting LDPC rate matching in IEEE 802.11, focusing on issues such as performance loss compared to previous standards, power consumption in LDPC decoding/encoding, and over puncturing. It covers preliminary concepts, packet size distribution in various devices like laptops
2 views • 17 slides
Certification of Core Flight Software (cFS) for NASA's Gateway Program
The project aims to certify the Core Flight Software (cFS) for NASA's Gateway program, ensuring safety-critical flight software for Gateway's modules. The certification work is led by a dedicated team, enabling cost savings across the program. The goal is to deliver a class-A certified cFS bundle wh
1 views • 10 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Guide to Apprenticeship Gateway Quality Assurance and Enhancement
The guide outlines the journey through the Apprenticeship Gateway at UEL, detailing key steps such as off-the-job training, enrollment, skills assessment, tripartite progress reviews, and endpoint assessment readiness. It explains the concept of Gateway, the ESFA definition, and the requirements for
3 views • 6 slides
Enhancing Network Performance with RoCE Technology
Remote Direct Memory Access (RDMA) benefits, RoCEv2 packet format, resilient RoCE feature progression, optimizing network performance with QoS, and RoCE congestion control convergence analysis are discussed in this proposal. RoCE technology offers low latency, high throughput, and efficient CPU usag
0 views • 19 slides
Understanding Security Onion: Network Security Monitoring Tools
Security Onion is a Linux distribution designed for network security monitoring using various tools like Full Packet Capture, Network IDS, Host IDS, and Analysis Tools. It offers capabilities for detecting and responding to security incidents effectively, making it a valuable asset for defensive net
1 views • 17 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Explore Cisco Packet Tracer for Network Simulation
Discover Cisco Packet Tracer, a powerful network simulation program used for hands-on LAN configuration and managing large-scale distributed systems. Learn about its availability to Networking Academy users and how to download the software for free through Academy Connection.
0 views • 8 slides
Understanding Programmable Traffic Management for Network Optimization
Programmable Traffic Management involves packet scheduling, traffic shaping, policing, drop policies, packet buffering, replication, and classification to optimize network performance. It is used in integrated switch architectures and is crucial for addressing diverse traffic characteristics and req
0 views • 66 slides
Understanding Checksums in Packet Headers
Checksums play a crucial role in validating the integrity of packet headers in various protocols. This tutorial explores the concept of checksums, the use of algorithms like CRC, and the process of recalculating checksums to ensure data integrity in network communications.
0 views • 11 slides
Understanding EIGRP: A Comprehensive Overview
Enhanced Interior Gateway Routing Protocol (EIGRP) is a dynamic routing protocol providing various advantages to network administrators. It is a classless routing protocol supporting VLSM and is considered an Interior Gateway Protocol (IGP). EIGRP uses advanced distance vector routing and is known f
1 views • 5 slides
Understanding Packet Radio: A Comprehensive Guide
Packet radio, utilizing VHF FM technology, is a digital mode allowing keyboard-to-keyboard communication, messaging, mailboxes, bulletins, and more. It uses the AX.25 protocol and operates at varying data rates on VHF and HF bands. The system comprises basic stations and automated nodes, each requir
0 views • 20 slides
Understanding Interconnect Topology Design and Performance Metrics
Interconnect topology design plays a crucial role in determining the cost and performance of a network. Factors such as the number of switches and links, switch port count, network layout, throughput, packet latency, average hop counts, nodal degree, hop count, and diameter are essential considerati
0 views • 38 slides
Enhancing Network Debugging with CherryPick in Software-Defined Datacenter Networks
Explore CherryPick, a technique for tracing packet trajectory in software-defined datacenter networks. It helps in debugging by ensuring data plane conforms with control plane policies, localizing network problems, and enabling packet trajectory tracing challenges like non-shortest paths. CherryPick
0 views • 14 slides
DAG2000 Series VoIP Access Gateway Overview
DAG2000 series Voice Gateway is a VoIP access gateway that supports SIP protocol, compatible with mainstream IP PBX and softswitch platforms. It provides quality voice services for carriers, enterprises, village users, and companies. The gateway offers features such as primary and secondary SIP acco
2 views • 4 slides
OpenNF: Enabling Network Function Control
OpenNF enables innovation in network function control by supporting various network functions, dynamic allocation of instances, and addressing challenges such as packet loss and SLA fulfillment. The architecture focuses on state export/import, operation guarantees, and efficient handling of NFs with
1 views • 32 slides
Understanding Internet Architecture and Networking Principles
The content explores the architecture and goals of the Internet, focusing on its original objectives, survivability in the face of failure, and evolving requirements. It delves into how networks function, describing behaviors and packet handling. Additionally, it discusses the framework for describi
0 views • 15 slides
Comprehensive Overview of Computer Networks and Protocols for GCSE Level
Explore the diverse aspects of computer networks and protocols through in-depth discussions on LAN, WAN, client-server relationships, hardware requirements, network topologies, protocols like TCP/IP and HTTP, and the significance of network layers. Understand the roles, benefits, and risks associate
0 views • 23 slides
Understanding the Impact of 1% Packet Loss on TCP and the Cubic Congestion Avoidance Algorithm
Delve into the surprising effects of even 1% packet loss on network flows, the methods TCP uses to mitigate loss, and how the CUBIC congestion avoidance algorithm works. Explore the researched but not quantified problem of packet loss and learn about a test methodology using Ubuntu hosts to measure
0 views • 24 slides
FY25 Title III Consortium Packet Overview
FY25 Title III Consortium Packet provides information on English Language Proficiency allocations, consortium formation, grant management, board approval requirements, and responsibilities of the lead fiscal agent. English Learner counts determine funding eligibility, with consortiums formed to reac
0 views • 15 slides
Understanding Gateway and NDE Linking Process
Explore the process of linking Gateway and NDE for access control software commands, emphasizing the importance of proper commissioning and communication protocols. Discover the requirements, steps, and indicators for successful communication between the Access Control Software (ACP) and Gateway. Le
0 views • 20 slides
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
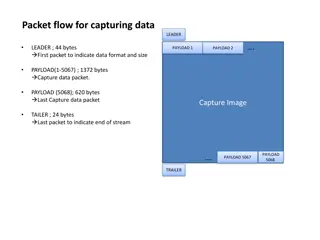
Wireshark Data Capture and UDP Analysis
Capturing data flow through packets in Wireshark reveals a series of fragmented payloads, starting with a leader packet of 44 bytes and ending with a trailer of 24 bytes. The UDP data payloads range from 44 to 1372 bytes, with specific lengths for different payloads and packets. Analysis includes UD
0 views • 4 slides
Dictionary Compression and Deep Packet Inspection (DPI) Overview
This content discusses Decompression-Free Inspection (DPI) for shared dictionary compression over HTTP, the challenges and solutions in deep packet inspection (DPI), compressed HTTP methods, examples of intra-response and inter-response compression, and current operations of Network Intrusion Detect
0 views • 33 slides
Enhancing Network Security Using Snort Virtual Network Function with DPI Service
Deep Packet Inspection (DPI) as a service is explored in this work, aiming to improve performance, innovation, and security in network operations. By extracting DPI from middleboxes and offering it as a shared service, the paper suggests benefits such as optimized packet scanning, enhanced functiona
0 views • 55 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Advancements in Network and Database Integration
This presentation discusses the convergence of network advancements and database technologies, highlighting key challenges such as packet processing at increasing line rates and latency issues. It explores the current landscape of databases from a research perspective and proposes solutions for opti
0 views • 13 slides
Exploring the Evolution of Data Communications: A Brief Overview
Delve into the progression of data communications from Morse code to modern radio email systems like Winlink. Discover the history of protocols, technologies, and the impact of the internet on amateur packet radio. Unravel the development of ARQ data protocols, X.25 packet switching, and the transit
0 views • 51 slides
Issues and Tests in Data Analysis at IHEP Experimental Center
Data analysis issues and tests were found by Tingxuan Zeng at the TDAQ Group within the Experimental Center at IHEP. Various issues were identified during the last data taking session, including discrepancies in GEMDC packet counts, incorrect packet lengths, and buffer pile-up. Analysis and testing
0 views • 4 slides
Mint: Cost-Effective Network-Address Translation Architecture
Mint (Multiple Inexpensive Network-address Translation) presents a cost-effective, scalable, fault-tolerant, and flexible approach to handling IP address depletion by utilizing multiple NAT servers. The system architecture includes NAT servers and a Mint-NAT gateway to enhance packet handling effici
0 views • 18 slides
Understanding the Basics of Packet Radio for Amateur Communication
Explore the world of packet radio, a digital mode used by amateur radio operators to build wireless computer networks. Learn about its benefits, how it works using the AX.25 protocol, making connections, advantages such as error checking, and building a packet station with the necessary components.
0 views • 19 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Understanding Interconnection Networks, Flow Control, and Microarchitecture
Interconnection networks play a crucial role in determining the flow control and routing paths within a network, impacting throughput and latency. Different switching techniques like circuit-switching, packet-based, and flit-based control the allocation of resources at various granularities. Circuit
0 views • 41 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Enhancing Data Center Network Performance through Packet Scheduling and ECN
Explore the advancements in data center network performance improvement through techniques like packet scheduling, Explicit Congestion Notification (ECN), and strict priority for different types of flows. The research discusses the requirements of low latency for short messages and high throughput f
0 views • 48 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
Considerations on PHY Padding and Packet Extension in 11ax
The document discusses the proposed PHY padding and packet extension for IEEE 802.11ax, focusing on considerations for processing data within SIFS duration and relaxation of LDPC decoding processing time. It outlines the overview of the proposed padding scheme, considerations for LDPC implementation
0 views • 15 slides
Innovative Application Packet for ACE Solutions - Explore the Visual Journey
Dive into the visually captivating world of ACE Solutions with their cutting-edge application packet. From stunning visuals to advanced functionality, this packet showcases the power and versatility of ACE Solutions for modern applications. Discover the seamless navigation, engaging content, and ric
0 views • 59 slides
Enhancing Packet Processing Performance with AF_XDP Technology
Explore the high-performance packet processing capabilities of AF_XDP integrated with the Linux kernel. Discover how AF_XDP socket provides advanced processing features, achieving impressive data transfer rates while ensuring security and isolation for enhanced network efficiency.
0 views • 16 slides
The Future of Fast Data Processing with fd.io VPP
Explore the future of fast data processing through the innovative fd.io VPP technology. VPP stands as a high-performance packet processing platform running on commodity CPUs. It leverages DPDK for optimal data plane management and boasts fully programmable features like IPv4/IPv6 support, MPLS-GRE,
0 views • 15 slides