Understanding Static GNSS Techniques and Products for Geospatial Applications
This educational material provides insights into static GNSS techniques, products, and their societal benefits. It covers topics such as distinguishing static GNSS techniques, understanding different products, and the capabilities of static GNSS stations. The content explores the Network of the Amer
3 views • 20 slides
Staining techniques
Explore a series of images illustrating various staining techniques used in histopathology, including fixation, different types of staining methods like Gram staining and acid-fast staining, as well as vital and supra-vital staining. Learn about the principles and applications of these techniques in
2 views • 42 slides
Techniques and Tools for Health Education in Primary Care
Explore various educational techniques and tools for promoting health in the context of primary care. Delve into the concepts, classifications, characteristics, and advantages of individual and group techniques. Discover the significance of life skills education in positively transforming individual
3 views • 25 slides
Understanding Kinesiology Taping Techniques and Benefits
Kinesiology taping is a technique utilizing thin, flexible tape to relieve pain, reduce swelling, and provide support to muscles and joints. Introduced by Dr. Kenzo Kase in the 1970s, it includes techniques such as muscle, ligament, fascial, correction, lymphatic drainage, and functional movement te
8 views • 14 slides
Understanding Measurement Scales and Scaling Techniques
Measurement scales play a crucial role in marketing research, with techniques like scaling helping to categorize data. The content discusses four types of measurement scales: nominal, ordinal, interval, and ratio, outlining their characteristics and differences. Scaling techniques involve placing re
5 views • 7 slides
Crafting Success: Effective Techniques in C-Level Recruiting
\"Crafting Success: Effective Techniques in C-Level Recruiting\" delves into the strategic approaches and methodologies crucial for identifying, attracting, and securing top-tier executive talent. Explore proven techniques in c-level recruiting and c-level staffing that drive organizational growth a
1 views • 6 slides
Demand Forecasting Techniques in Cargo Operations
In the dynamic world of cargo operations, effective demand forecasting is pivotal for streamlined logistics and maximized profitability. Revenue Technology Services (RTS), a leader in cargo strategy consulting, emphasizes the importance of leveraging sophisticated demand forecasting techniques to st
0 views • 6 slides
Soil and Water Conservation Techniques in Rainfed Agriculture by Mr. Anil Swami
Explore soil erosion and various conservation techniques discussed by Mr. Anil Swami, an Assistant Professor specializing in Rainfed Agriculture and Watershed Management. Learn about prevalent soil and climatic conditions in rainfed areas, water harvesting techniques, contingent crop planning, seaso
0 views • 66 slides
Techniques Used in Lino Printmaking and Linocut Printmaking
Explore the techniques used in lino printmaking, a form of relief printing where artists carve into a linoleum block to create prints. Learn how to sketch, transfer designs, carve using tools, ink, and print by hand or with a press. Discover different methods like reduction, jigsaw, and multiple blo
10 views • 11 slides
Fish Processing and Preservation Methods for Quality and Longevity
Fish are highly perishable and require proper preservation techniques to maintain their quality and freshness. Methods such as chilling, freezing, and other preservation techniques are employed to extend the shelf life of fish for short and long durations. Quick freezing is preferred for long-term s
1 views • 17 slides
Laboratory Techniques for Biologists: Advanced Biology Unit Overview
Explore essential topics in the field of advanced biology including health and safety protocols, risk assessments, dilution methods, colorimetry, separation techniques like chromatography and electrophoresis, and more. Gain insights on handling hazardous substances, controlling risks, and applying v
1 views • 31 slides
Techniques for Investigating Plant Metabolic Pathways and Biogenetic Studies
This content explores various techniques used in pharmacognosy and phytochemistry to investigate the metabolic pathways in plants and study the formation of primary and secondary metabolites. Methods such as utilizing radioactive isotopes, tracer techniques, isolated organs/tissues, grafting, and mu
4 views • 12 slides
Exploring Graph-Based Data Science: Opportunities, Challenges, and Techniques
Graph-based data science offers a powerful approach to analyzing data by leveraging graph structures. This involves using graph representation, analysis algorithms, ML/AI techniques, kernels, embeddings, and neural networks. Real-world examples show the utility of data graphs in various domains like
3 views • 37 slides
Exploring Narrative Techniques in Storytelling
Delve into the world of narrative techniques used in storytelling, including first person narration, flashbacks, framed narratives, and foreshadowing. Understand how these techniques shape the way stories are told and immerse readers in captivating storytelling experiences.
0 views • 19 slides
Counterfeit Detection Techniques in Currency to Combat Financial Fraud
Currency counterfeiting poses a significant challenge to the financial systems of countries worldwide, impacting economic growth. This study explores various counterfeit detection techniques, emphasizing machine learning and image processing, to enhance accuracy rates in identifying counterfeit curr
0 views • 15 slides
Understanding Fingerprint Development Techniques
Exploring the development of latent fingerprints through physical and chemical methods, conditions affecting latent prints, and various fingerprint development techniques like visual examination, powder techniques, and chemical techniques. Techniques such as alternate light sources and powder method
2 views • 22 slides
Understanding Fact Finding Techniques in System Analysis and Design
Fact finding techniques play a crucial role in collecting essential data and information for system analysis and design. Techniques include sampling existing documentation, research, observation, questionnaires, interviews, prototyping, and joint requirements planning. Extracting facts accurately is
1 views • 8 slides
Understanding Test Techniques in Software Testing
Explore test techniques in software testing including checklist-based testing, black-box test techniques, decision coverage, statement coverage, and their relationships. Learn how these techniques contribute to effective software testing practices.
3 views • 38 slides
Understanding Sorting Techniques in Data Structures
Sorting is the process of arranging elements in a specific order, be it ascending or descending, for efficient data access. This content covers internal and external sorting, types of sorting techniques like Bubble Sort and Quick Sort, factors influencing the selection of sorting techniques, efficie
7 views • 12 slides
Urban Design Techniques for City Improvement
Urban design techniques play a crucial role in urban improvement by providing concepts and tools for city building. Some of these techniques include the Open Space Technique, Transportation System Technique, Capital Network Technique, Public Policies Technique, Physical Design Technique, Plug-in Tec
1 views • 11 slides
Understanding Artificial Intelligence Techniques
Artificial Intelligence (AI) techniques leverage knowledge representation to achieve generalization, ease of adaptation, and problem-solving capabilities. Knowledge, although voluminous and dynamic, is crucial for developing effective AI solutions. By capturing important properties and enabling adju
0 views • 25 slides
Exploring Web Application Vulnerabilities and JavaScript Worms
Web applications face pervasive vulnerabilities, with Cross-site Scripting (XSS) leading the threats. The domination of XSS and buffer overruns has enabled the propagation of JavaScript worms, exemplified by infamous cases like Samy's MySpace outbreak. These exploits, marked by obfuscation and polym
1 views • 20 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Mastering Electronic Information Searching Techniques
Electronic information searching requires thorough preparation and the use of various search techniques to retrieve valuable information. This module by Nancy Kamau from Kenya Methodist University covers the process of search preparation, importance of search techniques, and developing effective sea
0 views • 44 slides
Comprehensive Malware Analysis Techniques
This detailed guide covers basic static techniques, malware analysis in virtual machines, and basic dynamic analysis. It includes information on static analysis, such as examining payloads without execution, file signatures, and signatures generated via analysis. Additionally, it delves into counter
0 views • 17 slides
Understanding Weird Machines in Transient Execution
Weird machines refer to models exhibiting unintentional behaviors triggered by adversarial inputs. They serve as computation primitives, enabling tasks like program obfuscation and secret computations. TSX weird machines, computing with time, manipulate cache states through gates like Assign, AND, O
0 views • 18 slides
Awareness and Techniques of Garment Recycling Among Housewives
This seminar conducted at S.M. Patel College of Home Science focused on studying the awareness of garment recycling and techniques adopted by housewives from different socio-economic backgrounds. The study aimed to promote the reuse and reprocessing of textiles to reduce waste. Through data collecti
0 views • 22 slides
Encrypted Data Deletion for Cloud Storage Servers
Explore the concept of software with certified deletion for private cloud storage servers. Discover how data recoverability is influenced by secret key leaks and encryption scheme vulnerabilities. Learn about techniques for computing on encrypted data and ensuring provable deletion, with a focus on
0 views • 29 slides
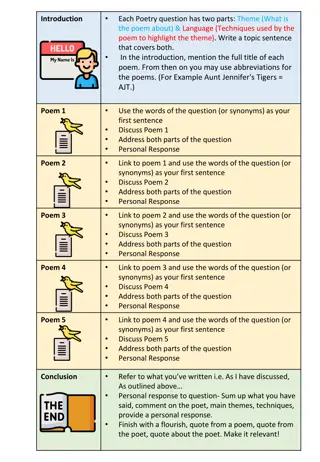
Crafting Literary Analyses: Study of Poetry Themes and Language Techniques
Explore an insightful approach to analyzing poetry themes and language techniques through a structured paragraph template. Delve into five poems, dissect their themes and techniques, and craft personal responses to each piece. Uncover the beauty of poetry with a systematic examination that includes
0 views • 4 slides
Essential Techniques in Chemical Research
Learn about key research techniques in chemistry including preparation methods, drying techniques, chromatography, spectroscopic techniques, and specific solvents used. Understand the importance of starting material preparation, drying reagents such as calcium chloride and molecular sieves, and how
0 views • 15 slides
Advanced Security Concepts in SNARGs Using iO and Lossy Functions
Explore the latest research on Adaptive and Selective Soundness in Succinct Non-interactive Argument of Knowledge (SNARGs), presenting theorems and the inclusion of subexponentially secure techniques like indistinguishability obfuscation, one-way functions, and very lossy functions. Discover the pot
0 views • 20 slides
CERT Basic Training Unit 7 Review: Search & Rescue Techniques
In the CERT Basic Training Unit 7 Review, participants learn essential search and rescue techniques including conducting size-up assessments, interior and exterior searches, survivor rescue methods, and safe debris removal. The learning objectives focus on identifying size-up requirements, demonstra
0 views • 13 slides
Understanding Anti-Anti-Virus Techniques and Retroviruses
Explore the world of anti-anti-virus techniques including Retroviruses and Entry Point Obfuscation. Learn about the methods used by viruses to evade detection and damage anti-virus software. Discover how Retroviruses like Ganda virus operate stealthily to hinder anti-virus programs. Delve into strat
0 views • 24 slides
Techniques for Protecting Web User Identity: Part 2 Overview
Explore offensive, defensive, and forensic techniques for safeguarding web user identity in this detailed guide by Zachary Zebrowski. Learn about obfuscation methods, browser protection, and important caveats to enhance online privacy. Discover strategies like borrowing a neighbor's network, using s
0 views • 45 slides
Evaluating Android Anti-malware Against Transformation Attacks
This study evaluates the effectiveness of Android anti-malware solutions against transformation attacks, focusing on the resistance to various types of malware obfuscations. It explores different transformations such as repacking, trivial changes, and sophisticated obfuscation techniques. Ten popula
0 views • 23 slides
Exploring SMT Solvers for Malware Unpacking
In this informative content, we delve into the world of malware analysis, binary packers, and the challenges posed by obfuscation techniques. The article discusses tools like UPX and Themida, as well as the complexities of virtualization and handler obfuscation in unpacking malware. Understanding th
0 views • 24 slides
Understanding Fingerprint Development Techniques
Latent fingerprints are hidden impressions left by the friction ridges of the skin which require physical or chemical techniques for visualization. Factors affecting latent prints include surface type, touch manner, weather, humidity, perspiration, and suspect care. Techniques such as visual examina
0 views • 22 slides
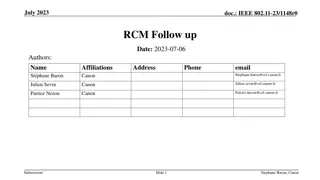
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
Analytical Techniques in Pharmaceutical Analysis
Analytical techniques play a crucial role in determining the identification and concentration of chemical substances in pharmaceutical analysis. Techniques range from simple gravimetric analysis to sophisticated methods using specialized instrumentation. Various techniques like gravimetric, titrimet
0 views • 17 slides
Microscopic Techniques in Cell Biology: Lessons and Labs Overview
Explore the fascinating world of optical microscopy in cellular biology, covering topics such as image formation, contrasting techniques, fluorescence microscopy, live-imaging techniques, and quantitative microscopy. Dive into the principles behind various microscopy techniques and experimental labs
0 views • 7 slides