Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Weather Monitoring Systems Market 2
The increased need for continuous weather monitoring to enable disaster management and the rapid weather fluctuations and climate changes drive the growth of this market. In addition, the increasing adoption of sensors for weather monitoring and the emergence of advanced technologies are expected to
8 views • 2 slides
Weather Monitoring Systems Market
Weather Monitoring Systems Market by Component (Solutions, Services), Monitoring Type (Temperature Monitoring, Humidity Monitoring, Air Quality), End-use Industry (Agriculture, Aerospace), and Geography - Global Forecast to 2030\n
0 views • 4 slides
Weather Monitoring Systems Market
Weather Monitoring Systems Market by Component (Solutions, Services), Monitoring Type (Temperature Monitoring, Humidity Monitoring, Air Quality), End-use Industry (Agriculture, Aerospace), and Geography - Global Forecast to 2030\n
0 views • 4 slides
Weather Monitoring Systems Market
Weather Monitoring Systems Market by Component (Solutions, Services), Monitoring Type (Temperature Monitoring, Humidity Monitoring, Air Quality), End-use Industry (Agriculture, Aerospace), and Geography - Global Forecast to 2030\n
0 views • 4 slides
NIMH Clinical Research Education and Monitoring Program Overview
NIMH's Clinical Monitoring and Clinical Research Education, Support, and Training Program (CREST) aims to ensure the proper conduct, recording, and reporting of clinical trials. This program includes clinical monitoring plans, guidelines for site monitoring activities, and independent clinical monit
1 views • 29 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Rethinking Network Monitoring: A Journey from Troubleshooting to Automation
Explore the evolution of network monitoring from reactive troubleshooting to proactive automation. Discover the importance of timely response, the role of tools like MTR and NLNOG RING, the need for alerts and automation, and the challenges in obtaining accurate network performance insights. Delve i
0 views • 22 slides
Metamodel-based Photovoltaic Monitoring System for Renewable Energies at Hongik University
This project at Hongik University focuses on developing a metamodel-based photovoltaic monitoring system to address the challenges of managing diverse solar monitoring systems in Korea. By utilizing a unified data communication protocol, the system aims to streamline the monitoring process for solar
0 views • 18 slides
Network Monitoring and Vulnerability Scanning Overview
Kashif Mohammad from the Department of Physics at the University of Oxford provides insights into their setup involving ZEEK, ELK Monitoring, and OpenVas for network monitoring and vulnerability scanning. The team aims to enhance network security through structured classification of nodes based on t
1 views • 10 slides
Understanding Security Onion: Network Security Monitoring Tools
Security Onion is a Linux distribution designed for network security monitoring using various tools like Full Packet Capture, Network IDS, Host IDS, and Analysis Tools. It offers capabilities for detecting and responding to security incidents effectively, making it a valuable asset for defensive net
0 views • 17 slides
Understanding Flow Monitoring in OVS for Efficient Network Management
Learn how Flow Monitoring in Open vSwitch (OVS) allows controllers to track and manage changes to flow tables, enabling efficient network management. Explore topics such as Flow Mod programming, Flow Monitor messages, OVS support, monitoring vs. snoop, and practical examples of flow monitoring in ac
0 views • 9 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Framework for Building National Forest Monitoring Systems for REDD+
This module outlines a comprehensive framework for developing national forest monitoring systems for REDD+ initiatives. It covers key components such as satellite land monitoring, national forest inventories, greenhouse gas reporting, emission factors, and integrated monitoring systems focusing on c
0 views • 14 slides
Developing Monitoring Tools for Programmatic Oversight
This presentation covers key aspects of monitoring tools for program oversight, including types of monitoring documents, notice of monitoring, and elements to consider. It discusses the importance of informing subawardees about monitoring visits and outlines the components of monitoring forms used i
0 views • 64 slides
Unpredictable Arctic Monitoring Framework for Extreme Event Integration
This project focuses on integrating extreme event monitoring into existing biodiversity monitoring efforts in the Arctic. The task involves developing a monitoring framework, identifying types of extreme events, and monitoring variables aligned with biodiversity plans. The review paper discusses the
0 views • 15 slides
Continuous Monitoring of Water Quality in Little Bear River
Explore the implementation of sensors, cyberinfrastructure, and continuous monitoring networks in the Little Bear River to improve water quality predictions. Discover the challenges and solutions related to designing monitoring networks, integrating optical measurements with water quality data, and
1 views • 38 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Effective Monitoring Practices for Federal Programs in Education
Effective monitoring practices for federal education programs, such as ESEA Title I-A, II-A, IV-A, V-B, McKinney-Vento, Foster Care, and Equitable Services to Private Schools by the Oregon Department of Education. The monitoring process involves desk monitoring and on-site visits to ensure education
0 views • 23 slides
Advancements in Online Saw Monitoring for Wood Industry 4.0
Explore the latest research on online saw monitoring in the context of Industry 4.0, focusing on tools like cloud computing, smart sensors, and artificial intelligence for enhanced monitoring capabilities in the sawmill industry. Discover the importance of tool health monitoring, wear detection, and
0 views • 22 slides
Importance of Field Monitoring in Adventure Activities
Field monitoring plays a vital role in ensuring the safety and effectiveness of adventure activities. It involves providing necessary information, instruction, training, and supervision to staff members, thus assuring management of real-time happenings and instilling confidence in both staff and man
0 views • 8 slides
Comprehensive Overview of GLAAS, SDG Monitoring, and Goal 6 Indicators
The content delves into the Global Analysis and Assessment of Sanitation and Drinking-Water (GLAAS), its relationship with the Sustainable Development Goals (SDGs), particularly Goal 6 on clean water and sanitation. It discusses regional monitoring initiatives, the 2030 Agenda for Sustainable Develo
0 views • 16 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Network Monitoring Workshop - Incident Response Overview
This workshop covers various aspects of incident response, including tools and techniques such as network taps, protocol analysis with Wireshark, data summarization with Bro/Zeek, alerting with Snort/Suricata, and more. Sessions delve into topics like TLS inspection, wireless network monitoring, and
0 views • 17 slides
Network Security Breakout: Science DMZ, BGP, Data Movement, Measurement & Monitoring Tools
Delve into network security topics related to Science DMZ, BGP, data movement, and measurement tools discussed at the NSF CC* PI Workshop. Key speakers include Jason Zurawski from LBNL and representatives from the University of South Carolina. The workshop covers various aspects of network security
0 views • 13 slides
Review of Post-Distribution Monitoring Tools - Analysis and Insights
This review analyzes existing post-distribution monitoring tools and methodologies used by various partners, highlighting common themes and challenges. It discusses the need for a common monitoring template and methodological guidance to streamline processes. Key findings include variations in monit
0 views • 10 slides
Insights from RIS3 Monitoring Working Group Meeting at Ken Guy Wise Guys Ltd.
The feedback from the second meeting of the RIS3 Monitoring Working Group at Ken Guy Wise Guys Ltd. in Barcelona highlighted key tasks, including presentations on monitoring exercises, participatory exercises, and the RIS3 Monitoring Clinic. The presentation emphasized humor in communication, while
0 views • 5 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
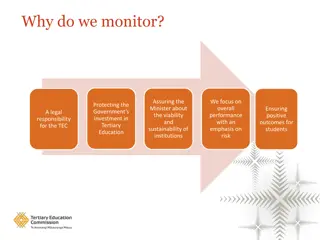
Effective Monitoring and Investment Relationship in Tertiary Education Institutions
Assurance of viability and sustainability of institutions, focusing on overall performance and risk assessment, safeguarding government investments in tertiary education, ensuring positive student outcomes, and fulfilling legal responsibilities for the Tertiary Education Commission. Monitoring activ
0 views • 6 slides
Advanced Field Monitoring Specialist Training for FRMAC - MS-400
Providing a refresher for FRMAC Field Monitoring Specialists, this advanced MS-400 training emphasizes sampling and monitoring equipment, data collection methods, and operations. The course includes updates in Monitoring Division operations, lessons learned from past experiences, refresher topics fr
0 views • 12 slides
Understanding BCG Matrix: Market Growth and Relative Market Share
BCG Matrix, developed by Bruce Henderson of the Boston Consulting Group, categorizes business units into Question Marks, Stars, Cash Cows, and Dogs based on market growth and relative market share. Market share and market growth are crucial factors in determining a company's position in the market.
0 views • 31 slides
Difference Between Capital Market and Money Market: A Comprehensive Overview
The capital market and money market serve different purposes in the financial world. While the capital market provides funds for long-term investments in securities like stocks and debentures, the money market deals with short-term borrowing and lending of funds. The capital market acts as a middlem
0 views • 4 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Side Channel Monitoring in Additive Manufacturing for Cybersecurity and Quality Assurance
Side channel monitoring is crucial in the field of additive manufacturing to bridge cybersecurity and quality assurance. This process involves detecting physical domain data leakage through various side channels like acoustics, thermal, laser, vibration, electric current, optical, and pressure. By m
0 views • 10 slides
Enhancing Disaster Preparedness with Indonesia's Seismic Monitoring Network
Indonesia's Digital Seismic Network, operated by the Indonesian Agency for Meteorology, Climatology, and Geophysics (BMKG), comprises 164 stations strategically located across the country. The network provides critical seismic data for the Seismic Integration System of InaTEWS, supporting real-time
0 views • 11 slides
Global Climate Monitoring and Data Quality Analysis at NCMP Ayako Takeuchi, JMA ET-NCMP Meeting
Monitoring world climate using CLIMAT and SYNOP data, the GCOS Surface Network (GSN) plays a crucial role in global climate monitoring. The GSN Monitoring Centre, led by DWD and JMA, ensures the availability and quality of CLIMAT reports from over 1,000 monitoring stations globally. With a focus on
0 views • 13 slides
Overview of Title I, Part D Monitoring in Education
This presentation covers the importance of monitoring Title I, Part D programs in education to ensure compliance with State and Federal laws. It includes information on the monitoring review processes, benefits of monitoring, and the different levels at which programs are monitored. The content also
0 views • 27 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides
Comprehensive Network Forensics Course Overview
Explore the essentials of network monitoring, forensics, and analysis in this detailed course by Jim Irving. Learn about network events capture, forensic data interpretation, working with PCAP and flow data, host forensics, logs, alerts, SIEMs, and more. Gain a broad understanding of network forensi
0 views • 102 slides