A-Block-Sector-3-Noida
Discover the fully furnished office space for your business at A Block Sector 3 Noida. This prime commercial space offers 500 Sq.ft to 5,000 Sq.ft. area with excellent connectivity, modern amenities, and a thriving business environment with walking distance from metro station. Unlock this opportunit
1 views • 1 slides
Enhancing Student Success through Block Scheduling at KSU
National Institute for Student Success (NISS) diagnostic analysis at KSU shows the importance of block scheduling in increasing graduation rates and student engagement. Actions to increase registration for full-time schedules and improve student success are underway. The goals of KSU's block schedul
0 views • 10 slides
Buy Block Heels for Women Online in India 9threadz
\nLooking to elevate your style with the perfect pair of block heels? Look no further than 9threadz, your go-to destination for fashionable footwear online in India. Whether you're dressing up for a special occasion or simply want to add a touch of sophistication to your everyday look, our collectio
2 views • 4 slides
Chemistry of f-Block Elements: Lanthanide and Actinide Series Overview
This segment delves into the properties, occurrence, and unique characteristics of the f-block elements, focusing on the Lanthanide and Actinide series. Covering topics such as color, oxidation states, spectral properties, lanthanide contraction, separation methods, and industrial applications of th
1 views • 15 slides
Roheenaz Mushq by Taneez Unstitched Pakistani Block Print Suits
Elevate your wardrobe with the Roheenaz Mushq by Taneez unstitched Pakistani block print suit. This exquisite ensemble features a printed lawn front, back, and sleeves, complemented by an embroidered silk neckline, side lace, and daman border. Paired with a printed chiffon dupatta and matching print
1 views • 10 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
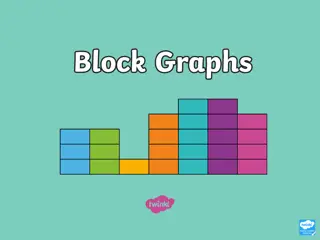
Understanding Block Graphs: Examples and Explanations
A block graph visually represents discrete data in a collection of blocks with no gaps between them. Each block must be carefully drawn with a title and axes labeled to explain the data shown. Examples include surveys on favorite activities, zoo animal sightings, and chocolate wrapper colors. Learn
0 views • 8 slides
Comparison of Erector Spinae Plane Block vs Serratus Anterior Plane Block in Thoracic Surgery Recovery
Minimally Invasive Thoracic Surgery often results in severe post-operative pain, typically managed with the Serratus Anterior Plane (SAP) block. This study compared the quality of recovery and morbidity between SAP and the relatively new Erector Spinae Plane (ESP) block. Results showed that ESP prov
1 views • 10 slides
IEEE 802.11-20/0055r0 Multi-link Block Ack Architecture Overview
This document from January 2020 presents an overview of the IEEE 802.11-20/0055r0 Multi-link Block Ack architecture proposed by Rojan Chitrakar from Panasonic. It discusses the negotiation of block ack agreements between multiple MLDs, common sequence number assignment, transmit and receive buffers,
1 views • 11 slides
Classification of Elements and Periodicity in Properties: Overview and Evolution
The journey of understanding the classification of elements and periodicity in properties begins with early laws like the Law of Triads and Newland's Law of Octaves. Mendeleev's Periodic Law revolutionized the organization of elements, leading to the modern periodic table. Discoveries of eka-alumini
3 views • 32 slides
Binary Basic Block Similarity Metric Method in Cross-Instruction Set Architecture
The similarity metric method for binary basic blocks is crucial in various applications like malware classification, vulnerability detection, and authorship analysis. This method involves two steps: sub-ldr operations and similarity score calculation. Different methods, both manual and automatic, ha
0 views • 20 slides
Understanding Renal Block: Drugs, Excretion, and Treatment Essentials
Renal block plays a crucial role in drug excretion, with processes like glomerular filtration and tubular secretion affecting drug elimination. Factors like blood flow, physiochemical properties, and urine pH influence renal excretion of drugs. Competition between drugs for transporters can have ben
0 views • 10 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
D-Block Elements: Properties and Classification in Chemistry
Welcome to the Department of Chemistry at Kisan Veer Mahavidyalaya, Wai. Explore the Chemistry of Elements of the 3d series, focusing on d-Block Elements and Transition Elements. Learn about their electronic structure, colored ions, magnetic properties, oxidation states, and complex formation. Under
0 views • 34 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Taekwondo Techniques and Blocks: Defensive Moves in Action
Explore Taekwondo techniques such as the Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block, used for defense against different types of attacks in martial arts. Detailed descriptions and illustrations demonstrate how to execute these blocks effectively to protect various parts of th
1 views • 25 slides
Taekwondo Techniques - Basics and Blocks for Self-Defense
Explore the fundamental Taekwondo techniques focusing on blocking movements for self-defense. Learn about Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block with detailed descriptions and images illustrating each move. Enhance your understanding of these essential blocks in Taekwondo
4 views • 11 slides
Understanding Cryptography: Basics of Encryption and Padding
Cryptography is essential for secure communication between parties, ensuring confidentiality and integrity of data. This overview covers basic math concepts, block ciphers, encryption modes like ECB and CBC, and the importance of padding in securing plaintext data.
0 views • 21 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Understanding Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
0 views • 21 slides
Overcoming Writer's Block: Strategies and Techniques for Creative Inspiration
Explore diverse methods to combat writer's block including diagnosing the type of block, generating ideas, dealing with an overflow of ideas, initiating writing, outlining effectively, dealing with being stuck, and managing boredom or stress. Discover helpful tips from understanding assignments to o
0 views • 12 slides
Enhancing Public Health Services at Block Level: BPHU Overview
The Block Public Health Unit (BPHU) plays a crucial role in improving public health outcomes at the block level by augmenting healthcare services, strengthening referral systems, and focusing on social and environmental determinants of health. Key components, functions, and goals of BPHUs are outlin
0 views • 16 slides
Crack the Code: A Journey into Transposition Ciphers
Mathematicians play a crucial role in industries like telecommunications and internet companies by condensing data and ensuring error detection. Transposition ciphers, like the Scytale used by Romans, offer a challenging way to encrypt messages. Test your skills with code-breaking challenges and exp
0 views • 4 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
MLA Style Guide for Block Quotations
Learn how to format block quotations according to MLA style guidelines. Use a block quote for material longer than four lines, indent one inch from the left margin, and type it double-spaced without quotation marks. Remember to introduce block quotations with a colon.
0 views • 4 slides
Exploring the Importance of Block Play in Early Childhood Education
Discover the influential educational philosophies of Froebel and Pratt, emphasizing the value of play in children's learning and development through block building activities. Learn about the significance of unit blocks and large hollow blocks, as well as the cognitive skills children acquire. Explo
0 views • 18 slides
Taekwondo Training: Block Techniques Explained
Dive into the world of Taekwondo block techniques with detailed descriptions and images of essential blocks such as Down Block, X Block, Knife-Hand Block, and Double Knife-Hand Block. Learn the proper execution and applications of each block to enhance your defensive skills in martial arts.
0 views • 25 slides
Taekwondo Techniques for Defense: Blocks and Movements
Explore the fundamental blocking techniques in Taekwondo, including the Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block. Learn the proper execution and defense strategies against different types of attacks targeting various body sections. Enhance your skills and understanding of s
0 views • 11 slides
Analysis of 20T Hybrid Block-Coil V5.8 Magnetic Model
This analysis focuses on the magnetic model of a 20T hybrid block-coil V5.8 system, including modifications to incorporate ribs, iron components, rigid boundaries, component bonding, sliding and separating configurations, and stress evaluations. The study explores the layout adjustments, peak magnet
0 views • 5 slides
Business Letter Writing Guidelines and Formats
Learn about the essential parts of a business letter, including the heading, addressee, subject, salutation, body paragraphs, complimentary close, and signature. Understand various formats/styles such as block, modified block, and semi-block. Discover sample formats and guidelines for writing effect
0 views • 23 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
0 views • 25 slides
Understanding S-Block Elements in the Periodic Table
The s-block elements in the Periodic Table consist of 14 elements with unique properties and characteristics. Lithium, sodium, and potassium are notable members of Group 1, characterized by their reactivity and ability to form alkaline solutions when in contact with water. These soft metals exhibit
0 views • 23 slides
Guide for File Download Block Creation
In this guide, you will learn how to create a file download block on your webpage step by step. First, you need to click the small plus symbol, then initiate the file download process. You can customize the title, format, text color, and background theme accordingly. Finally, you can choose when and
0 views • 34 slides
Hyper.block Concept for Efficient NBA-MMS Slot Resource Management
Utilizing a hyper.block-based mode for NBA-MMS can provide enhanced slot resource efficiency in densely populated areas. This approach addresses the need for improved coverage and reliability while optimizing slot allocation based on channel conditions and factors affecting preamble transmission. Th
0 views • 8 slides
Introduction to Traditional Ciphers: Columnar Transpositions
Traditional ciphers such as Columnar Transpositions involve rearranging plaintext letters based on a fixed number of columns. This technique enhances security by incorporating a keyword for encryption and decryption. Learn about the process and examples of implementing Columnar Transpositions in thi
0 views • 8 slides
Understanding Block Ciphers in Cryptography
Explore the world of block ciphers in cryptography through topics such as distinguishing attacks, key-recovery attacks, designing paradigms like Substitution-Permutation Networks (SPNs) and Feistel networks, concrete security considerations, confusion/diffusion principles, attack models, and more.
0 views • 27 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides