Building a Macrostructural Standalone Model for North Macedonia: Model Overview and Features
This project focuses on building a macrostructural standalone model for the economy of North Macedonia. The model layout includes a system overview, theory, functional forms, and features of the MFMSA_MKD. It covers various aspects such as the National Income Account, Fiscal Account, External Accoun
2 views • 23 slides
NAMI Family Support Group Model Overview
This content provides an insightful introduction to the NAMI family support group model, emphasizing the importance of having a structured model to guide facilitators and participants in achieving successful support group interactions. It highlights the need for a model to prevent negative group dyn
6 views • 23 slides
Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
6 views • 31 slides
'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Communication Models Overview
The Shannon-Weaver Model is based on the functioning of radio and telephone, with key parts being sender, channel, and receiver. It involves steps like information source, transmitter, channel, receiver, and destination. The model faces technical, semantic, and effectiveness problems. The Linear Mod
1 views • 8 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Regression Diagnostics for Model Evaluation
Regression diagnostics involve analyzing outlying observations, standardized residuals, model errors, and identifying influential cases to assess the quality of a regression model. This process helps in understanding the accuracy of the model predictions and identifying potential issues that may aff
2 views • 12 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
Testing Residuals for Model Appropriateness in ARMA Modeling
This content discusses the importance of checking residuals for white noise in ARMA models, including methods like sample autocorrelations, Ljung-Box test, and other tests for randomness. It also provides examples of examining residuals in ARMA modeling using simulated seasonal data and airline data
0 views • 40 slides
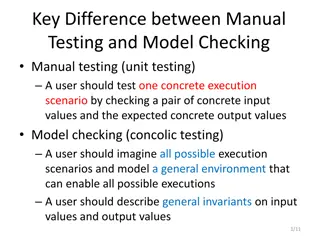
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
3 views • 4 slides
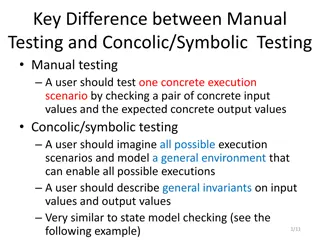
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
MFMSA_BIH Model Build Process Overview
This detailed process outlines the steps involved in preparing, building, and debugging a back-end programming model known as MFMSA_BIH. It covers activities such as data preparation, model building, equation estimation, assumption making, model compilation, and front-end adjustment. The iterative p
0 views • 10 slides
Proposal for Radio Controlled Model Aircraft Site Development
To establish a working relationship for the development of a site suitable for radio-controlled model aircraft use, the proposal suggests local land ownership with oversight from a responsible agency. Collins Model Aviators is proposed as the host club, offering site owner liability insurance throug
0 views • 20 slides
UBU Performance Oversight Engagement Framework Overview
Providing an overview of the UBU Logic Model within the UBU Performance Oversight Engagement Framework, this session covers topics such as what a logic model is, best practice principles, getting started, components of the logic model, evidence & monitoring components, and next steps. The framework
1 views • 33 slides
Regression Model for Predicting Crew Size of Cruise Ships
A regression model was built to predict the number of crew members on cruise ships using potential predictor variables such as Age, Tonnage, Passenger Density, Cabins, and Length. The model showed high correlations among predictors, with Passengers and Cabins being particularly problematic. The full
0 views • 16 slides
Exact Byzantine Consensus on Undirected Graphs: Local Broadcast Model
This research focuses on achieving exact Byzantine consensus on undirected graphs under the local broadcast model, where communication is synchronous with known underlying graphs. The model reduces the power of Byzantine nodes and imposes connectivity requirements. The algorithm involves flooding va
0 views • 7 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Calibration of Multi-Variable Rainfall-Runoff Model Using Snow Data in Alpine Catchments
Explore the calibration of a conceptual rainfall-runoff model in Alpine catchments, focusing on the importance of incorporating snow data. The study assesses the benefits of using multi-objective approaches and additional datasets for model performance. Various aspects such as snow cover, groundwate
0 views • 16 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
The Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
Inferential Statistics Solutions for Challenging Problems in Section B
The provided statistical problems in Section B involve calculating the expected number of shoppers spending specific durations at a furniture shop and reasons for not checking the weight of each packet when filling corn flakes. Solutions include determining the shoppers expected to spend more than 4
0 views • 25 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
1 views • 27 slides
Conflict Checking Process in Heraldry: Armory 104 Overview
Delve into the intricacies of conflict checking using the ordinary in heraldry with Armory 104. Explore prerequisites, review key concepts, understand where SCA-registered armory is located, and learn the process of identifying and analyzing charge groups to ensure uniqueness in designs. Avoid commo
0 views • 28 slides
Parcel Fabric and Local Government Model - Data Migration Process
Explore the data migration process for Parcel Fabric in the Local Government Model, covering topics such as the WV Factor, geometry requirements, topology rules, staging data, and checking results for successful load. Understand the challenges, conversion factors, and tools essential for migrating d
0 views • 17 slides
Innovation and Social Entrepreneurship Initiatives in Higher Education
This project focuses on establishing a leading center for promoting innovation and social entrepreneurship within higher education institutions. It aims to encourage students and staff to develop creative solutions for community challenges, expand social involvement, and foster sustainable positive
1 views • 13 slides
Principles of Econometrics: Multiple Regression Model Overview
Explore the key concepts of the Multiple Regression Model, including model specification, parameter estimation, hypothesis testing, and goodness-of-fit measurements. Assumptions and properties of the model are discussed, highlighting the relationship between variables and the econometric model. Vari
2 views • 31 slides
Cognitive Model of Stereotype Change: Three Models Explored
The Cognitive Model of Stereotype Change, as researched by Hewstone & Johnston, delves into three key models for altering stereotypical beliefs: the bookkeeping model, the conversion model, and the subtyping model. These models suggest strategies such as adding or removing features to shift stereoty
0 views • 58 slides
R Short Course Session 5 Overview: Linear and Logistic Regression
In this session, Dr. Daniel Zhao and Dr. Sixia Chen from the Department of Biostatistics and Epidemiology at the College of Public Health, OUHSC, cover topics on linear regression including fitting models, checking results, examining normality, outliers, collinearity, model selection, and comparison
0 views • 44 slides
Subtyping and Type Checking in Programming Language Design
In the realm of programming language design, subtyping and type checking play crucial roles. This content delves into how syntax-directed rule systems evolve when dealing with subtyping, presenting the challenges and the solutions through a recursive algorithm approach. The discussion includes the t
0 views • 40 slides
Orthogonal Vectors Conjecture and Sparse Graph Properties Workshop
Exploring the computational complexity of low-polynomial-time problems, this workshop delves into the Orthogonal Vectors Problem and its conjectures. It introduces concepts like the Sparse OV Problem, first-order graph properties, and model checking in graphs. Discussing the hardness of problems rel
2 views • 22 slides
Streamlining Technical Processing for Library Services
In the technical processing workflow of a library, utilizing tools like copy cataloging macros can significantly improve efficiency and accuracy. This involves checking for copy cataloging status, running fix routines, and updating catalog records. While these macros offer benefits such as saving ti
0 views • 17 slides
Enterprise Modelling Basics and Refinement Approach Overview
This overview delves into Enterprise Modelling basics, covering Domain Model, Enterprise Object Types, Atomic Activities, Life Cycles, and refinement techniques like adding attributes and constraints. The content explores extending the model to upper layers and emphasizes the importance of clarity f
0 views • 53 slides
Framework for Writing Trigger-Action Todo Comments in Executable Format
A framework developed by Pengyu Nie, Rishabh Rai, Junyi Jessy Li, Sarfraz Khurshid, Raymond J. Mooney, and Milos Gligoric which allows developers to write trigger-action todo comments in an executable format. The framework aims to address the issues of tedious and error-prone manual checking and exe
0 views • 38 slides
SciClops: Detecting Scientific Claims for Fact-Checking Assistance
In this research presented at CIKM '21, SciClops focuses on detecting and contextualizing scientific claims to aid in manual fact-checking processes. By analyzing the granularity of scientific literature sources and utilizing multifaceted contextual support, the study introduces a sentence classific
0 views • 16 slides