Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
USDA Accessible Communications Program Overview
Advancing access and equity for individuals with disabilities is a key focus of the USDA Accessible Communications Program. Through initiatives like the National Disability Employment Awareness Month events and implementing the Rehabilitation Act, the program aims to promote accessible communication
5 views • 28 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Mastering Business Writing Skills: A Comprehensive Guide
Understanding the essence of business communication, types of communication, essentials of effective communication, smart communication tips, and communication across cultures is vital for professional success. Explore verbal, written, and non-verbal communication methods to enhance your communicati
0 views • 47 slides
Understanding Communication and Sign Language
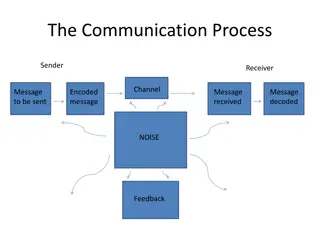
Communication is the vital process of exchanging information, ideas, and emotions through various channels such as speech, signals, and writing. This includes verbal and non-verbal communication, where sign language plays a crucial role. Effective communication depends on the sender, message, channe
1 views • 31 slides
Enhancing Zoonotic Disease Risk Communication in Public Health Emergencies
Explore the significance of adopting a One Health approach to zoonotic disease risk assessment and communication in the context of emergency health situations. The session emphasizes core capacities required by the International Health Regulations (IHR) 2005, effective risk communication processes,
2 views • 13 slides
Effective Communication Skills for Healthcare Professionals
Enhance your communication skills with the Accelerated Preceptorship Communication Session by Desiree Cox. Learn the importance of effective communication, different communication preferences, communication dynamics, non-verbal communication, listening skills, and more. Understand the communication
2 views • 28 slides
Understanding Implications of IG Empowerment Act and Paperwork Reduction Act
The IG Empowerment Act provides beneficial provisions for Inspector Generals (IGs) such as exemptions from certain acts, including the Computer Matching Act and Paperwork Reduction Act. The Paperwork Reduction Act requires federal agencies, including IGs, to obtain OMB clearance before conducting su
1 views • 25 slides
Understanding Speech Acts and Events in Communication
Speech acts and events play a crucial role in communication by impacting how utterances are interpreted. Speech acts such as apologies, compliments, complaints, and invitations are performed through utterances, with the locutionary act producing linguistic expression, illocutionary act conveying com
0 views • 30 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Understanding the Hatch-Waxman Act: Promoting Affordable Generic Drugs
The Hatch-Waxman Act, also known as The Drug Price Competition and Patent Term Restoration Act, was enacted in 1984 to amend patent laws and the Federal Food, Drug, and Cosmetic Act. It aims to reduce costs associated with generic drug approval, allow early experimental use, compensate branded drug
0 views • 49 slides
Understanding the Impact of Social Media and Legal Consequences
This presentation explores the effects of social media on individuals, particularly young users, and highlights the importance of age restrictions such as WhatsApp's minimum age policy. It also delves into the Malicious Communication Act of 1988, discussing the legal implications of sending offensiv
0 views • 17 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Ensuring Inclusive Communication and Services at Crouse Hospital
Individuals with hearing or visual impairments, limited English proficiency, or other disabilities are provided with necessary interpreter and communication services at Crouse Hospital. Regulations like Title VI of the Civil Rights Act of 1964 and the Americans with Disabilities Act of 1990 ensure n
3 views • 11 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Effective Communication Strategies in Business Environments
Explore the various aspects of communication processes within organizations, including sender-receiver dynamics, communication channels, small group networks, upward and downward communication methods, business communication tools, information richness of channels, email and voice mail etiquette, an
0 views • 21 slides
Legal Framework for Weigh-In Motion in South Africa
The legal framework in South Africa regarding weigh-in motion involves various acts and guidelines that impact the weighing of vehicles, such as the Trade Metrology Act, Legal Metrology Act, and National Road Traffic Act. The laws govern the requirements for mass measuring, equipment specifications,
0 views • 22 slides
Proposed Changes to Manitoba's Building Permitting System
Bill 38, "The Building and Electrical Permitting Improvement Act," introduces the Permit Dispute Resolution Act in Manitoba. This act allows for appeals to an adjudicator regarding building code compliance and performance standards under the Buildings Act. The adjudicator can confirm, vary, or set a
1 views • 6 slides
Understanding Classroom Communication and Management by Ramkrishna Chakraborty
Communication is a vital process of exchanging information, ideas, and opinions between individuals. In the educational context, effective communication is essential for achieving desired behavior patterns. This article explores the meaning, concept, and types of communication, emphasizing the impor
1 views • 19 slides
Effective Communication Strategies in Public Health Incident Leadership
Learn about the importance of effective communication within emergency operations centers during public health incidents. Explore communication tools, techniques, and case examples of communication failures. Discover key aspects such as team communication, situational awareness, shared mental models
0 views • 16 slides
Communication Protocols for System Integration
This technical document explores various communication protocols used for system integration, focusing on mailbox communication, interprocessor communication, system communication using IPCC, and BLE communication utilizing different IPCC channels. The document delves into the features, functions, a
1 views • 6 slides
Effective Communication Skills in Business Environment
Understand the importance of communication in organizations, learn about the process of communication, main objectives, types, and patterns of communication. Explore key points such as accuracy in conveying ideas, feedback, and communication channels. Enhance your knowledge on downward, upward, and
0 views • 24 slides
Mastering Effective Communication Skills in Daily Life
Enhance your communication skills with insights from Unit 5 Communication. Learn about different types of communication, speaking skills, effective communication strategies, assertiveness, and more. Understand the nuances of verbal, nonverbal, and paralanguage communication to convey your message cl
0 views • 52 slides
Effective Communication in Workplace Safety Training
This presentation covers the importance of effective communication in workplace safety training, emphasizing the elements of a communication plan, communication processes, and the realities of communication. It explores the consequences of failure to communicate safety information effectively and di
1 views • 31 slides
Communication Costs in Distributed Sparse Tensor Factorization on Multi-GPU Systems
This research paper presented an evaluation of communication costs for distributed sparse tensor factorization on multi-GPU systems. It discussed the background of tensors, tensor factorization methods like CP-ALS, and communication requirements in RefacTo. The motivation highlighted the dominance o
0 views • 34 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Strategic Communication Goals and Objectives
Clearly defining goals and objectives is essential in strategic communication. This involves setting realistic and aligned targets, such as building communication capacity, influencing policy, and engaging public will. Communication plays a crucial role in achieving social change and programmatic su
0 views • 67 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
Specialization in International Business Communication (SIBC)
Specialization in International Business Communication (SIBC) offered by the Department of Business Communication focuses on the critical role of communication in various business settings, emphasizing skills in language usage, communicative competence, and strategic language application. The progra
0 views • 11 slides
The Civil Rights Act of 1964 and the Supreme Court
In the 1960s, Congress passed the Civil Rights Act of 1964, a pivotal legislation that prohibited discrimination in public accommodations. This act represented a significant shift in focus towards minority rights. The Supreme Court's past rulings on the Civil Rights Act of 1875 influenced Congress t
0 views • 24 slides
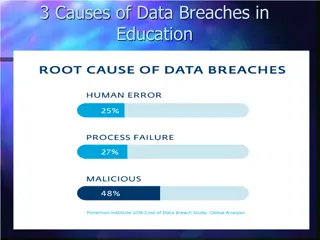
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Overview of Asynchronous MPC with Linear Communication and Optimal Resilience
Explore the concepts of Asynchronous Multiparty Computation (MPC) with Linear Communication and Optimal Resilience, discussing the model, motivation, and differences between synchronous and asynchronous protocols. The goal is to ensure correctness and privacy in a setting where parties may be corrup
0 views • 72 slides