Protecting Accounts & Devices: Stay Secure Online
Secure accounts & devices, manage breaches, prevent attacks, recover lost data. What to do in case of security breach and steps to safeguard personal information and devices.
1 views • 18 slides
The Top 10 Signs Your Router May Have Been Hacked
Explore the 10 unmistakable signs indicating your router's security might have been compromised. Learn how to identify potential breaches and safeguard your network from cyber threats.\n
4 views • 1 slides
How to Protect Your On-Demand App from Cyberattacks and Data Breaches
On-demand app development solutions provide convenient services but also carry cybersecurity risks like hacking, malware, and data breaches. This comprehensive guide explores best practices to secure on-demand apps and protect sensitive user data. Learn how encryption, multifactor authentication, ac
0 views • 4 slides
Unlocking Vault Balancing Accessibility and Security in Medical Records Storage
In the digital age, accessibility and security stand as twin pillars shaping the landscape of medical records storage, Los Angeles. On one hand, seamless accessibility promises instant retrieval and enhanced coordination of care among healthcare providers. However, this accessibility often comes at
6 views • 6 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Privacy Breach Management Guide by Health PEI
Understanding, Preventing, and Managing Privacy Breaches in Healthcare: Learn about what constitutes a privacy breach, how to prevent breaches, steps to determine and manage breaches effectively, including containment, investigation, and notification processes.
0 views • 10 slides
Cyber Data Breach Review_ A Comprehensive Insight with LDM Global in the USA
In today's digital landscape, cyber data breaches pose significant threats to organizations of all sizes. A cyber data breach can result in severe financial losses, reputational damage, and legal ramifications. To navigate these challenges effectively, companies turn to expert services like those pr
1 views • 13 slides
Internet Safety Tips: Protect Yourself Online
Internet safety is crucial in safeguarding your online activities from threats like malicious software, hackers, and data leaks. Learn how to protect yourself against these risks, prevent password breaches, save passwords securely, back up your data, and be cautious about what information you share
1 views • 15 slides
Lessons from Recent Data Breaches: Insights and Strategies
This presentation covers the landscape of data breaches, leading causes, and steps to take when facing a cyber incident. It discusses the impact of large-scale cyber attacks by external threat actors, outlines key considerations for response, and provides tips for notifying affected individuals to m
2 views • 20 slides
Ransomware and Data Breaches in Public Libraries Analysis
Delve into the world of ransomware and data breaches in public libraries, exploring the definitions of ransomware and data breaches, the potential impacts on libraries, the financial losses incurred, and the value of library records. Understand the risks, implications, and consequences associated wi
0 views • 21 slides
Enhancing University Information and Records Management for Strategic Advancement
The University's continuous improvement strategy for 2020 focuses on managing information and records effectively to mitigate risks associated with data processing. Information is deemed a critical asset, and risks range from data breaches to operational disruptions. To address these challenges, an
1 views • 21 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Special Audit Report on Caribbean Maritime University (CMU) - December 2019
The special audit report on Caribbean Maritime University revealed unsatisfactory HR practices, poor governance, deficiencies in oversight, procurement breaches, and mismanagement of contracts. Issues included inconsistent HR practices, unapproved emoluments, infrequent council meetings, and inadequ
0 views • 12 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Response Patterns to Data Breaches in Firm IT Investment
This research explores how firms reallocate internal IT resources in response to security breaches and the impact of these allocation patterns on future firm performance. It delves into the allocation of IT budgets, changes in IT staffing, and examines antecedents and consequences of security breach
0 views • 47 slides
Essential Steps for Personal Data Breach Management
Detect, identify, and respond effectively to personal data breaches by containing the breach, assessing risks, notifying relevant authorities and affected individuals, and implementing measures to prevent future occurrences. Debunk common myths surrounding breach reporting and focus on mitigating ne
0 views • 5 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Louisiana Coastal Flooding Litigation Overview
The content discusses various aspects related to the Katrina Canal breaches consolidated litigation in Louisiana, focusing on the legal implications, failures in flood control measures, geology of coastal Louisiana, coastal elevations, and the impact of canal breaches on flooding in the region. It a
1 views • 30 slides
Privacy Breach Response and Reporting under the Health Information Act
Understanding privacy breaches under the Health Information Act (HIA) is crucial for organizations dealing with health data. This document outlines what constitutes a breach, mandatory notification requirements, factors to consider in determining risk of harm, and potential offences and penalties fo
0 views • 21 slides
Importance of Privacy & Data Security Training in Healthcare
Privacy and data security training in healthcare is crucial due to the interconnected nature of the industry, putting patient information at risk. Breaches have resulted in significant financial losses, emphasizing the need for mandatory training to safeguard patient privacy. Understanding responsib
0 views • 27 slides
HIPAA and Research Data Security Training for Researchers at BU Charles River Campus
This training provides essential information on how HIPAA impacts human subject research, the importance of protecting health data, reporting breaches, and utilizing BU resources. It also covers implications of HIPAA in research, national standards, consequences of breaches, and scenarios where HIPA
0 views • 37 slides
NHS Sussex Conflicts of Interest Breach Register Summary May 2024
NHS Sussex manages conflicts of interest breaches by recording and publishing them on their website. Breaches are documented with details of the nature of the breach and actions taken. In May 2024, no breaches were reported. Previous months had breaches due to late declarations of interest. Staff we
0 views • 5 slides
Cybersecurity Vulnerabilities and Solutions in Web Development
Discover the dangers of malicious scripting and the importance of sanitizing text inputs on servers to prevent security breaches in web applications. Explore techniques such as Atomic Replacement Constraints, Finite State Transducers, and Hierarchical FST modeling for enhancing security and analyzin
0 views • 23 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Importance of Security in Web Development
Our perception of security has evolved to acknowledge the presence of malicious actors and potential vulnerabilities in web applications. To write secure code, developers must assume the worst-case scenario and adopt a security mindset that trusts no one. Attackers have various goals, such as steali
0 views • 18 slides
VAST: A Unified Platform for Interactive Network Forensics
VAST is a comprehensive platform designed for interactive network forensics, addressing the increasing frequency of security incidents and large-scale data breaches. It aims to provide solutions for detecting, analyzing, and preventing breaches efficiently, with features like data exploration, query
0 views • 17 slides
Data Breaches and Privacy Concerns: An Overview
Privacy expert Marilyn Prosch, Ph.D., sheds light on the significant issue of privacy, emphasizing recent data breaches in various institutions and outlining some alarming cases where sensitive information was compromised. The incidents range from stolen laptops and office break-ins to mishandling o
0 views • 34 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
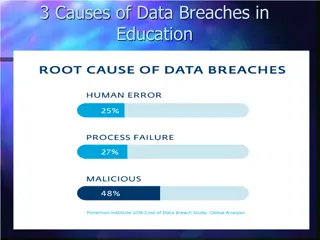
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Legal Issues in Data Breaches and Confidentiality Violations
The content covers various scenarios related to breach of confidence, liability of businesses in safeguarding data, and legal causes of action in case of data breaches. It discusses real-life analogies and legal principles concerning the mishandling of confidential information, including a case stud
1 views • 23 slides