Proposed Approach for MAC Address Assignment in IEEE 802.11
IEEE 802.1CQ is working on a mechanism to assign local MAC address blocks to end nodes specifically related to IEEE 802.11 standards. The current draft lacks a pre-association mechanism for IEEE 802.11 stations to obtain a local MAC address before association. The proposed remedy suggests specifying
6 views • 7 slides
APAC Position, Navigation, and Timing Solution Market Analysis & Forecast
The Asia-Pacific position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $1,410.5 million by 2033 from $466.1 million in 2023, at a CAGR of 11.71% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/asia-pacific-position
11 views • 3 slides
Position, Navigation, and Timing Solution Market Forecast to 2033
The global position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $5.24 billion in 2033 from $1.23 billion in 2022, at a CAGR of 10.85% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/position-navigation-timing-solu
0 views • 3 slides
Machine Learning for Predicting Path-Based Slack in Timing Analysis
Utilizing machine learning to forecast path-based slack in graph-based timing analysis offers a solution for optimizing power and area efficiency in the design process. The Static Timing Analysis incorporates accurate path-based analysis (PBA) and fast graph-based analysis (GBA) to estimate transiti
1 views • 31 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
Designing a Traffic Signal Timing Plan: Steps and Guidelines
This comprehensive guide covers the essential steps involved in designing a traffic signal timing plan, including determining lane configurations, proposing phase plans, identifying critical volumes, recommending phase plans, and establishing clearance intervals. It also provides insights into aspec
1 views • 26 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Numerical Abstract Domain with Max Operator in Timing Analysis
Explore a numerical abstract domain based on expression abstraction and the Max operator with applications in timing analysis. The challenges in timing analysis, such as disjunctive and non-linear bounds, are discussed along with simple examples illustrating these concepts. The difficulty of proving
0 views • 21 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
Harvesting and Postharvest Techniques for Quality Seed Production
Understand the importance of harvesting crops at the right timing to maximize seed quality. Learn about half-matured and full-matured stages, postharvest ripening, and indicators for precise timing. Discover the significance of counting days from flowering/pollination for determining harvest timing.
0 views • 24 slides
Privacy Issues in IEEE 802.11 Networks: Tracking and MAC Randomization
This presentation delves into the privacy concerns surrounding 802.11 networks, focusing on tracking vulnerabilities and the limitations of MAC randomization in preventing tracking. It discusses the ease of tracking devices, the risk of passive tracking due to MAC addresses being visible in frames,
0 views • 27 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
Cesarean Delivery Timing Guidelines for Women with Prior Uterine Scars
Society for Maternal Fetal Medicine provides cesarean delivery timing recommendations for women with prior uterine scars. For those with a history of classical cesarean, the risk of uterine rupture guides the timing of repeat cesarean. Similarly, women with prior myomectomy should plan delivery betw
0 views • 10 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
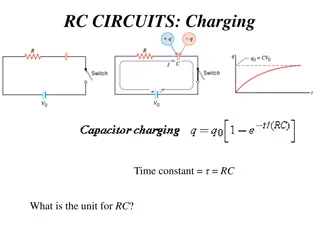
Applications of RC Circuits in Electronics and Biomedical Devices
RC circuits play a crucial role in various applications such as camera flashes, timing devices in automobiles, and heart pacemakers. These circuits involve charging and discharging a capacitor through a resistor, controlling voltage pulses for precise timing. In devices like camera flashes, the flas
0 views • 7 slides
NTN RRM Timing Related Requirements for Xiaomi Devices at 3GPP TSG-RAN4 Meeting #98-e
The agenda item for the 3GPP TSG-RAN4 Meeting #98-e involves discussing NTN RRM timing related requirements, specifically focusing on UE timing synchronization for Xiaomi devices. Key aspects include UE transmit timing error limits, timing advance accuracy, and UE timer accuracy requirements for NTN
0 views • 6 slides
WylasTiming - Wireless Semi-Automatic Timing System Overview
WylasTiming is a wireless semi-automatic timing system developed in Australia, utilizing off-the-shelf hardware and Android handsets. It provides accurate timing with automatic race starting and instantaneous data transmission. The timekeeper simply stops the clock at the end of the race, and data i
0 views • 15 slides
Implications of IEEE 802.11 State Machine and MAC Randomization
The document discusses the state machine transitions in IEEE 802.11, focusing on MAC address handling and implications for STA connectivity within an ESS. It explains the scenarios where a STA can use different MAC addresses, emphasizing the binding of state to specific address configurations and th
0 views • 11 slides
Simplifying Post-Silicon Timing Diagnosis with NGSPA Tool
Explore how the NGSPA tool by Intel simplifies post-silicon timing diagnosis, replacing costly machines with a CAD application running on an x86 server, saving resources and enabling parallelized CAD operations. Learn about the challenges in post-silicon speed debugging, the importance of static tim
0 views • 26 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
How to Record Your Voice: A Comprehensive Guide for Windows, Mac, and Smartphones
Learn how to record your voice for ePoster, MP3, or podcasts using Windows 10, Mac, Android, or iPhone/iPad devices. Find step-by-step instructions for recording on different platforms, including using Windows Voice Recorder on a Windows 10 computer and QuickTime Player on a Mac. Discover tips for a
1 views • 10 slides
Understanding Timing Models in Cell Design Environments
Delve into the intricacies of timing models for cells in design environments, exploring factors affecting delay, output transitions, linear and non-linear models, and the use of table models in cell libraries to specify delays and timing checks. Discover how input transitions and output capacitance
0 views • 11 slides
Exploring Mac OS & VoiceOver: A Comprehensive Guide with Belinda Rudinger
Dive into the world of Mac OS and VoiceOver with expert Belinda Rudinger in this detailed tutorial. Learn about screen readers, VoiceOver commands, built-in features, interaction tools, customization options, and useful utilities. Discover how to navigate the Mac ecosystem seamlessly using VoiceOver
0 views • 20 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
0 views • 25 slides
The Migration Advisory Committee Review and Findings
The Migration Advisory Committee (MAC) is an independent advisory body formed in 2007 to provide recommendations to the government on migration issues. The MAC does not create or implement policy but advises through research and analysis in various areas like economics, education, and stakeholder en
0 views • 13 slides
Understanding Timing Vulnerabilities in Computing Systems
Explore the evolution of timing attacks in computing systems, from traditional crypt-analysis to modern web-focused techniques. Discover the gap in implementing security measures and how universities can bridge this disparity. Delve into the history, challenges, and implications of timing vulnerabil
0 views • 26 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
Discussion on Timing Mask Requirement for ULSUP-TDM in RAN4#94e Meeting
In the RAN4#94e and #94e-Bis meetings, discussions were held on the timing mask requirement for ULSUP-TDM, particularly focusing on sub-topics like evaluating uplink timing differences between LTE and NR, clarifying present time mask conditions, and testing time mask requirements. The key issue cent
0 views • 4 slides
Caseous Mitral Valve Calcification (C-MAC) and Stroke: Overview and Management
Caseous Mitral Valve Calcification (C-MAC) is a rare condition characterized by spectrum liquefaction necrosis of the mitral annular calcification (MAC), potentially leading to cardiovascular complications like strokes and emboli. This article discusses the features, diagnostic aspects, and treatmen
0 views • 7 slides
Understanding Static Timing Analysis in Advanced VLSI Design
Static timing analysis is a crucial aspect of VLSI design, helping predict chip performance before fabrication. This article explores the importance of static timing analysis, its effectiveness, and the limitations of dynamic simulation tools like SPICE. Learn about the challenges in testing critica
0 views • 76 slides
Enhancing MAC Header Protection in IEEE 802.11 Networks
This document discusses the need for improved protection of MAC headers in IEEE 802.11 networks to address security concerns related to certain fields that are currently not adequately protected. It emphasizes the importance of safeguarding vital information in MAC headers to prevent potential attac
0 views • 12 slides
IEEE 802.11-22/0424r1 - MAAD MAC Protocol Overview
The document discusses the MAAD MAC protocol, where the AP assigns a MAAD MAC address to the STA during association. Key differences from other schemes are highlighted, emphasizing the use of MAAD MAC addresses as identification. Details on support indication, address allocation, and recognition mec
0 views • 7 slides
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
Understanding Sequential Circuit Timing and Clock Frequency
Sequential circuit timing is crucial for designing digital systems. The minimum clock period, slack values, clock frequency, and critical paths play key roles in determining the operational speed and performance of sequential circuits. By analyzing flip-flop timing parameters, combinatorial logic de
0 views • 20 slides
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
Understanding Variable Valve Timing (VVT) in Internal Combustion Engines
Variable Valve Timing (VVT) optimizes engine performance by adjusting valve duration, timing, and lift according to engine speed, enhancing torque, power, and fuel efficiency. VVT operates by varying intake valve opening/closing, regulating valve timing, and adjusting lift for better volumetric effi
0 views • 14 slides
IEEE 802.11-23/0421r1: Understanding the IRM Scheme for MAC Address Privacy
The document discusses the use of the Same MAC Address (SMA) scheme in IEEE 802.11-23/0421r1 and introduces the Improved Randomized MAC (IRM) scheme as a privacy-enhancing solution. It explores the implementation and benefits of IRM over SMA, addressing issues like privacy requirements, device ident
0 views • 7 slides
Enhancement of Rule-based Random and Changing MAC Proposal in IEEE 802.11-22/1802r0
This document details the enhancements proposed for the Rule-based Random and Changing MAC (RRCM) in IEEE 802.11-22/1802r0. The RRCM concept involves generating Random MAC (RMA) addresses locally to increase security and prevent trackability in wireless networks. Key aspects include RMA generation,
0 views • 12 slides
MAC Address Randomization in IEEE 802.11: Privacy Concerns and Solutions
The document discusses the rise of MAC randomization in IEEE 802.11 networks, addressing motivations, benefits, concerns over privacy implications, and real-life scenarios highlighting the risks associated with passive observation of MAC addresses. It emphasizes the importance of safeguarding privac
0 views • 14 slides