Buy Godrej 50mm Brass Finish Padlock with 3 Keys (Gold, Pack of 1)
Godrej Locks Brushed Finish 50mm Padlock Hardened Shackle Gold (Free Shipping UK)\n\nAbout this item\n\nSolid brass body provides sturdiness and MADE IN INDIA\n\nHardened steel shackle provides resistance to hacksaw cutting and crowbar attacks,\n\nElectroplated shackle ensures long life,\n\nDouble L
0 views • 3 slides
Good Laboratory Practices Study Protocols for Effective Research Management
Supplemental materials providing detailed protocols for implementing Good Laboratory Practices (GLP) in research settings. The protocols cover GLP requirements, experimental design, reading regulatory sections, approval processes, amendments, circulation lists, and study plans. These materials aim t
0 views • 22 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
Understanding Transaction Management in DBMS
In this lecture, Mohammad Hammoud covers the key aspects of transaction management in database management systems (DBMS). Topics include locking protocols, anomaly avoidance, lock managers, and two-phase locking. The session delves into the rules, data structures, and processes involved in maintaini
1 views • 56 slides
Automotive Grade 10 Joining Methods: Locking Devices Overview
Automotive Grade 10 explores joining methods using locking devices to prevent nuts from loosening due to movement and vibration. Friction-locking devices include lock nuts, stiff nuts, and special washers. Positive-locking devices tighten nuts securely with slotted nuts, crowned nuts, tab washers, a
1 views • 7 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
Corrugated packaging box with flat pack and inner locking in style
Corrugated packaging boxes with flat packs and inner locking styles are popular for their durability, cost-effectiveness, and ease of assembly. They are widely used for shipping and storing products due to their protective qualities and customizable
1 views • 2 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
Laboratory Safety Protocols and Pathogen Classification
Scientist must adhere to lab safety protocols including wearing safety gear, proper waste disposal, and handling chemicals carefully. The classification of pathogens varies by country based on WHO guidelines into four risk groups. Understanding these protocols and classifications is crucial for a sa
0 views • 17 slides
SRYA Clinic Soccer Fall 2021 Updates and Protocols
Stay updated on the latest news and protocols for the SRYA Clinic Soccer Fall 2021 season. Learn about volunteer positions, contacts, fun facts about the program, COVID-19 updates, and general protocols from Rec & Parks. Ensure the safety and well-being of players, coaches, and families while enjoyi
0 views • 23 slides
State Transportation Department's Stormwater Monitoring Program Overview
This document presents findings and protocols from the National Cooperative Highway Research Program related to stormwater monitoring goals, objectives, and protocols for state departments of transportation. The project team, objectives, and report organization are outlined, aiming to provide guidan
0 views • 32 slides
Animal Use Protocols: Finding the Right Balance
Exploring the analogy between the story of the three bears and animal use protocols, this content delves into the importance of providing just the right amount of information in research protocols. Through examples of intravenous injections in mice, the text emphasizes the necessity of striking the
0 views • 8 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Network Routing Algorithms and Protocols Overview
Understanding network routing algorithms and protocols is crucial in the field of networking. This content provides insights into the initialization process, loop prevention mechanisms, and the use of algorithms like OSPF and IS-IS. It also touches on routing protocols such as RIP and EIGRP, explain
0 views • 17 slides
Computer Lab Safety Training Guidelines
Ensure safe usage of computer labs in the College of Science, Technology, Engineering, and Mathematics with guidelines on Onity lock operation, loss of privilege/access, responsibility, emergency procedures, and electrical safety. The instructions cover aspects like door locking procedures, unauthor
0 views • 8 slides
Understanding Reliable Transport and User Datagram Protocol in Computer Networking
This content covers the concepts of reliable transport in computer networking, including the reliable transport layer protocols like TCP, UDP, and the basics of Domain Name Service (DNS). It explains the layers of the Internet, the functions of each layer, and the differences between TCP and UDP pro
0 views • 28 slides
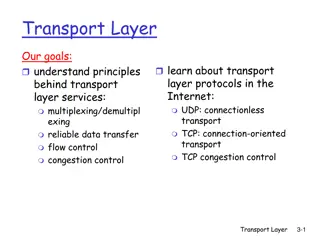
Understanding Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Securing Protocols with Fully Encrypted Protocols (FEPs)
In this research presented at the Cryptographic Applications Workshop, Ellis Fenske and Aaron Johnson address the challenges of Fully Encrypted Protocols (FEPs). They highlight the lack of precise understanding, formalized goals, and proven security in existing FEPs. The work introduces new security
0 views • 29 slides
Challenges and Solutions in Win32 Multithreading
Tackling complex problems in Win32 multithreading involves dealing with locking issues, such as insufficient lock protection and lock order violation. Central to this are the essential locking disciplines that are difficult to enforce in practice. Tools like EspC Concurrency Toolset help analyze and
0 views • 16 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Innovative Approach to Magnetron Phase Locking for RF Applications
This document explores a novel method for phase locking magnetrons, essential for various high-power RF applications. Traditional methods involve injecting RF signals through additional components, leading to complexity and inefficiency. The proposed method utilizes varactor diodes and feedback loop
0 views • 16 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Performance Analysis of Synchronization Methods in Concurrent Data Structures
Explore the impact of synchronization methods on the performance and behavior of concurrent data structures in multithreaded applications. The study involves developing and implementing concurrent data structures, analyzing coarse-grain locking, fine-grain locking, lock-free mechanisms, and assessin
0 views • 25 slides
Understanding Database Transactions and Concurrency Control
This content delves into the world of database transactions, exploring concepts such as ACID properties, locking schedulers, anomalies in scheduling, and implementing transaction control mechanisms like Two Phase Locking. It covers the importance of maintaining atomicity, consistency, isolation, and
0 views • 36 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Comprehensive Guide to Reamed Intramedullary Nailing Techniques
This educational material covers the principles of intramedullary nailing, including indications and contraindications, patient positioning, reduction techniques, surgical approach, and the procedure using the ETN. It delves into technique details, positioning, approach/entry points, reaming, nail i
0 views • 5 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Understanding Locking and Synchronization in Multithreaded Environments
Exploring the concepts of locking and synchronization in the context of shared resources in multithreaded environments. Covering topics such as thread cooperation, coordination of access to shared variables, and the importance of synchronization mechanisms for controlling execution interleaving. Exa
0 views • 41 slides
Best Locking wheel nut Removal in Hafod
If you\u2019re looking for a Locking wheel nut Removal in Hafod, contact Fastest Fit Tyres LTD. Their skilled mobile tyre fitters are available 24 hours a day, ensuring you're never stranded due to a flat or damaged tyre. They specialise in puncture
0 views • 6 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Understanding Semantics and Locking Specifications in Concurrency
Exploring the importance of semantics and locking specifications in concurrent programming, this content delves into issues such as data races, unsafe code, and solutions like locking discipline to manage shared data effectively and prevent corruption.
0 views • 22 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides