727003-B21 HP BL460C G9 E5-2695 V3 14-CORE PROCESSOR KIT
Refurbished | HP 727003-B21 | BL460C G9 E5-2695 V3 14-CORE PROCESSOR KIT | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\n\/\/ \/727003-b21-hp-bl460c-g9-e5-2695-v3-14-core-processor-kit\/
0 views • 1 slides
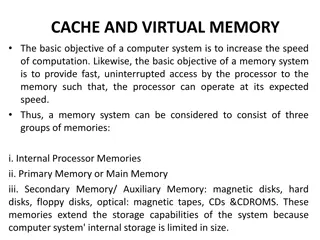
Understanding Cache and Virtual Memory in Computer Systems
A computer's memory system is crucial for ensuring fast and uninterrupted access to data by the processor. This system comprises internal processor memories, primary memory, and secondary memory such as hard drives. The utilization of cache memory helps bridge the speed gap between the CPU and main
1 views • 47 slides
Understanding Superscalar Processors in Processor Design
Explore the concept of superscalar processors in processor design, including the ability to execute instructions independently and concurrently. Learn about the difference between superscalar and superpipelined approaches, instruction-level parallelism, and the limitations and design issues involved
0 views • 55 slides
Understanding Basic Input/Output Operations in Computer Organization
Basic Input/Output Operations are essential functions in computer systems that involve transferring data between processors and external devices like keyboards and displays. This task requires synchronization mechanisms due to differences in processing speeds. The process involves reading characters
0 views • 11 slides
Introduction to Intel Assembly Language for x86 Processors
Intel Assembly Language is a low-level programming language designed for Intel 8086 processors and their successors. It features a CISC instruction set, special purpose registers, memory-register operations, and various addressing modes. The language employs mnemonics to represent instructions, with
2 views • 12 slides
Buy 872012-B21 HPE BL460C GEN10 XEON-S 4110 PROCESSOR KIT
Refurbished | HPE 872012-B21 | BL460C GEN10 XEON-S 4110 PROCESSOR KIT | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\n\/\/ \/872012-b21-hpe-bl460c-gen10-xeon-s-4110-processor-kit\/
0 views • 1 slides
Processor Control Unit and ALU Implementation Overview
In Chapter 4, the processor's control unit and ALU are detailed in a simple implementation scheme. The ALU performs operations based on opcode values, while the control unit provides signals for various functions such as load/store, compare, and branch. Decoding techniques and control signal generat
1 views • 21 slides
Understanding Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
2 views • 13 slides
Understanding Computer System Architectures
Computer systems can be categorized into single-processor and multiprocessor systems. Single-processor systems have one main CPU but may also contain special-purpose processors. Multiprocessor systems have multiple processors that share resources, offering advantages like increased throughput, econo
2 views • 25 slides
Techniques for Reducing Connected-Standby Energy Consumption in Mobile Devices
Mobile devices spend a significant amount of time in connected-standby mode, leading to energy inefficiency in the Deepest-Runtime-Idle-Power State (DRIPS). This study introduces Optimized DRIPS (ODRIPS) to address this issue by offloading wake-up timer events, powering off IO signals, and transferr
1 views • 31 slides
Understanding Processor Interrupts and Exception Handling in Zynq Systems
Learn about interrupts, exceptions, and their handling in Zynq Systems. Explore concepts like interrupt sources, Cortex-A9 processor interrupts, interrupt terminology, and the difference between pooling and hardware interrupts. Gain insights into interrupt service routines, interrupt pins, interrupt
0 views • 60 slides
Evolution of Microprocessors: A Historical Overview
The history of microprocessors traces back to Fairchild Semiconductors in 1959, leading to the founding of Intel in 1968. The evolution from 4-bit to 64-bit microprocessors by Intel revolutionized computing. Key milestones include the Intel 4004 and 4040 (4-bit), 8008, 8080, and 8085 (8-bit), and th
2 views • 44 slides
In-Depth Look at Pentium Processor Features
Explore the advanced features of the Pentium processor, including separate instruction and data caches, dual integer pipelines, superscalar execution, support for multitasking, and more. Learn about its 32-bit architecture, power management capabilities, internal error detection features, and the ef
0 views • 24 slides
What are the Top Features of Dell XPS 13 Laptop?
Looking for a high-performance laptop? The Dell XPS 13, available at Dubai Laptop Rental, features a 6th gen Intel Core i7 processor, 256GB SSD, and Intel Iris Graphics. For more details on Laptop Rental Dubai call us at 050-7559892.
3 views • 2 slides
Trends in Computer Organization and Architecture
This content delves into various aspects of computer organization and architecture, covering topics such as multicore computers, alternative chip organization, Intel hardware trends, processor trends, power consumption projections, and performance effects of multiple cores. It also discusses the sca
5 views • 28 slides
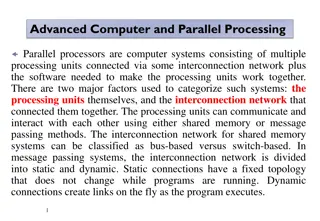
Parallel Processing and SIMD Architecture Overview
Parallel processors in advanced computer systems utilize multiple processing units connected through an interconnection network. This enables communication via shared memory or message passing methods. Multiprocessors offer increased speed and cost-effectiveness compared to single-processor systems
3 views • 24 slides
Understanding Processor Speculation and Optimization
Dive into the world of processor speculation techniques and optimizations, including compiler and hardware support for speculative execution. Explore how speculation can enhance performance by guessing instruction outcomes and rolling back if needed. Learn about static and dynamic speculation, handl
0 views • 33 slides
Understanding Pipelined Control in Processor Architecture
Explore the intricacies of pipelined control in processor design, detailing the control signals required at each stage of the pipeline. Learn about data hazards, forwarding, and stalling techniques to ensure efficient instruction execution. Dive into the concept of optimized control values for strea
0 views • 16 slides
Distribution and Occurrence of Trace Elements in Urban Wetland: A Case Study of Deepor Beel, Assam, India
This study focuses on the distribution and occurrence of trace elements and pharmaceutical pollutants in the urban wetland of Deepor Beel in Assam, India. The research investigates the presence of emerging contaminants like pharmaceuticals and personal care products, providing insights into the poll
0 views • 10 slides
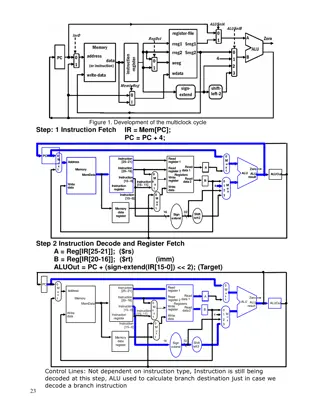
Development of Multiclock Cycle in Processor
The development process of the multiclock cycle in a processor is explained in detail through different steps, including instruction fetch, decode, register fetch, execution, and write-back for R-type instructions. Control lines and branching execution are also covered in the description. The conten
0 views • 5 slides
Overview of Inter-Processor Communication (IPC) in Processor Communication Link
Overview of Inter-Processor Communication (IPC) entails communication between processors, synchronization methods, and supported device types. The IPC architecture supports diverse use cases with various thread combinations and messaging types, catering to multi- or uni-processor environments. The A
0 views • 110 slides
Basic Principles of Medical Geology and Trace Elements Overview
This session delves into the fundamental principles of medical geology and its impact on human health. It explores how exposure to certain elements in the geologic environment can affect well-being, emphasizing pathways of trace elements into the body and their consequences. Dr. Patrick Asamoah Saky
0 views • 26 slides
Overview of Minerals and Trace Elements in Human Nutrition
Minerals and trace elements play essential roles in the human body, categorized into groups based on their functions and requirements. Nutritional minerals like calcium, phosphorus, and magnesium are needed in larger amounts, while trace elements such as zinc and iron are required in smaller quantit
0 views • 50 slides
Importance of Outdoor Ethics and Leave No Trace Principles
Outdoor ethics play a crucial role in preserving natural areas for future generations. The increase in visitors to wilderness areas highlights the need for responsible behavior. Integrating Leave No Trace principles into programs like BSA emphasizes the value of conservation and respect for the outd
0 views • 14 slides
Understanding Biological Uptake of Trace Elements in Natural Systems
Explore the connection between stoichiometric plasticity and trace metal distribution, investigate microbial acquisition systems, analyze modes of metal uptake, and address co-limitations and interactions within organisms. Utilize molecular tools to enhance knowledge on trace element bioavailability
0 views • 5 slides
Understanding Processor Hazards and Pipeline Stalls
Explore processor hazards like load-use and data hazards, along with strategies to avoid stalls in the pipeline. Discover how to detect and handle hazards efficiently for optimal performance in computer architecture. Learn about forwarding conditions, datapath design, and the impact of hazards on in
0 views • 30 slides
Out-of-Order Processor Design Exploration
Explore the design of an Out-of-Order (OOO) processor with an architectural register file, aggressive speculation, and efficient replay mechanisms. Understand the changes to renaming, dispatch, wakeup, bypassing, register writes, and commit stages. Compare Processor Register File (PRF) based design
0 views • 29 slides
Understanding Processor Cycles and Machine Cycles in 8085 Microprocessor
Processor cycles in microprocessors like 8085 involve executing instructions through machine cycles that are essential operations performed by the processor. In the 8085 microprocessor, there are seven basic machine cycles, each serving a specific purpose such as fetching opcodes, reading from memor
0 views • 17 slides
Transparent and Efficient CFI Enforcement with Intel Processor Trace
This research discusses Control Flow Integrity (CFI) enforcement to combat control flow hijacking attacks. It explores methods for runtime CFI enforcement, including instrumented checking and transparent monitoring. The study delves into trace mechanisms, buffer management strategies, and when to tr
0 views • 32 slides
Overview of E-Podium Specifications and Components
The E-Podium is equipped with a steel body, touch monitors, a PC with Intel i3 processor, controller, and various electronic components. The display includes a 19" touch monitor and a 10.4" sub-monitor. The PC features a motherboard with Intel H61 chipset, Intel HD2000 graphics, and dual-channel DDR
0 views • 8 slides
Trace-Driven Cache Simulation in Advanced Computer Architecture
Trace-driven simulation is a key method for assessing memory hierarchy performance, particularly focusing on hits and misses. Dinero IV is a cache simulator used for memory reference traces without timing simulation capabilities. The tool aids in evaluating cache hit and miss results but does not ha
0 views • 13 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Enhancing Precision and Accuracy in Trace Element Analysis Using EPMA Techniques
This research focuses on improving precision and accuracy for trace elements through advanced methods like MAN (mean atomic number) and MPB (multi-point background). By optimizing background measurements and calibration techniques, researchers aim to enhance the sensitivity and reliability of trace
0 views • 16 slides
Bringing Leave No Trace to Scouting: Expectations and Training Sessions
Encouraging Leave No Trace practices in Scouting is essential. This guide covers expectations for instructors, training sessions, BSA trainings, promotion strategies, and leadership positions related to Leave No Trace. From promoting the message to in-depth training opportunities, the focus is on in
0 views • 12 slides
Understanding Trace Tables for Algorithm Testing
Trace tables are a valuable technique used to test algorithms step by step and identify logic errors. They involve using truth tables to track variable values or conditions. This content provides insights into trace tables, correcting errors in pseudocode, using examples for variable tracking, and c
0 views • 9 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Understanding Processor Organization in Computer Architecture
Processor organization involves key tasks such as fetching instructions, interpreting instructions, processing data, and storing temporary data. The CPU consists of components like the ALU, control unit, and registers. Register organization plays a crucial role in optimizing memory usage and control
0 views • 21 slides
Understanding Processor Structure and Function in Computing
Explore the key components and functions of processors in computing, including user-visible and control status registers, instruction cycle, instruction pipelining, processor tasks like data processing and instruction interpretation, and the roles of arithmetic and logic units and control units. Lea
0 views • 61 slides
Understanding Processor Generations and VM Sizing for Azure Migration
Exploring the impact of processor generations on CPU performance, factors like clock speed, instruction set, and cache size are crucial. Choosing the right-sized VM plays a vital role in optimizing Azure migration. Passmark CPU Benchmark results provide insights on Intel processor generations for Az
0 views • 9 slides
Cutting-Edge Training Architecture Overview
Delve into the latest training innovations featuring NVIDIA Volta, Intel NNP-T/I, ScaleDeep, and vDNN. Learn about the impressive capabilities of the NVIDIA Volta GPU, Intel NNP-T with Tensor Processing Clusters, and Intel NNP-I for inference tasks. Explore the intricacies of creating mini-batches,
0 views • 32 slides