RNA Interference Therapy Zilebesiran's Impact on Hypertension
Explore Zilebesiran, an investigational RNA interference therapeutic targeting hepatic AGT synthesis for hypertension. Primary findings from Phase 2 trial KARDIA-1 reveal sustained blood pressure reduction. Addressing the unmet need for innovative antihypertensive treatments.
1 views • 12 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Enhancing In-Device Coexistence and P2P Communication in IEEE 802.11-23/2002r0
This document discusses proposals to improve reliability in the presence of interference or other device activities within the IEEE 802.11-23/2002r0 standard. Solutions include long-term indications for periodic service periods, interference indication in the frequency domain, expected behaviors, an
6 views • 25 slides
Network Interference and Censorship in Social Media
Discover the insights into detecting network interference, censorship, and social media manipulation through a collection of case studies, research papers, and real-world examples discussed in a Spring 2018 lecture. Topics include the goals of PAM 2011 paper, the Green Dam and Blue Dam projects, the
2 views • 27 slides
Forgetting: Theories and Influence on Memory Recall
Forgetting is a complex phenomenon influenced by theories such as Decay Theory, Interference Theory, and Motivated Forgetting. The Ebbinghaus forgetting curve highlights how memories fade over time. Decay Theory suggests memories decay over time, while Interference Theory explains how old and new me
1 views • 25 slides
Exploring Wave Interference in Physics: Superposition, Constructive, and Destructive Interference
Delve into the fascinating world of wave interference in physics, from understanding the concept of superposition to identifying constructive and destructive interference patterns. Discover how light waves interact through different paths and sources to create coherent or incoherent light. Explore t
2 views • 37 slides
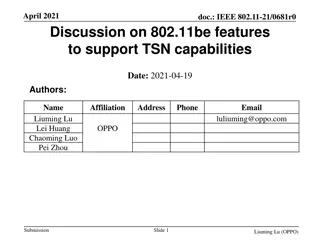
Discussion on IEEE 802.11be Features for TSN Capabilities
IEEE 802.11be introduces features to support Time-Sensitive Networking (TSN) capabilities by enhancing throughput, traffic delivery paths, scheduling flexibility, and latency reduction. The standard addresses the stringent latency requirements of real-time applications, medium access protection, mul
1 views • 10 slides
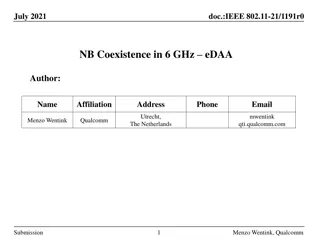
Coexistence Challenges and Solutions in 6 GHz Networks
Various submissions address narrowband (NB) coexistence issues in the 6 GHz frequency band, focusing on Enhanced Detect and Avoid (eDAA) mechanisms to ensure harmonious coexistence between Wi-Fi and NB devices. The proposals discuss channel access rules, interference measurements, simulation results
1 views • 14 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
1 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
IEEE 802.11-23/1999r0: Beacon Reception Impact of Narrow-Band Frequency Hopping Interference
Explore the impact of Narrow-Band Frequency Hopping (NBFH) interference on Wi-Fi beacon reception in IEEE 802.11-23/1999r0. The study delves into beacon traffic characteristics, spectrum usage assumptions, scenario analysis with Bluetooth links, and channelization details for Bluetooth ACL versus is
0 views • 15 slides
Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Follow-up on UWB Channel Usage Coordination for Improved Coexistence
This document provides additional details on UWB channel usage coordination to enhance coexistence, interference mitigation, and various improvements in wireless personal area networks. It discusses safeguards for data use cases, interference mitigation techniques, coexistence improvements, backward
0 views • 13 slides
Interference in Radiocommunication Systems
Interference calculations and definitions in radiocommunication systems are crucial for maintaining signal quality. This content explains various types of interference, such as co-channel and adjacent channel interference, and important parameters like Protection Ratio. It also covers the effect of
1 views • 52 slides
Interference and Beats in Waves
Explore the fascinating phenomena of interference and beats in waves, where overlapping waves interact to create patterns of constructive and destructive interference. Witness how sound waves can also produce beats when interfering in time, resulting in a slow envelope effect. Delve into the princip
1 views • 40 slides
Young's Double-Slit Experiment and Interference Patterns
Thomas Young's double-slit experiment in the late 1700s provided evidence of light behaving as a wave, showcasing interference patterns. This experiment challenged the particle theory of light and supported the wave theory. The interference patterns observed helped scientists grasp the wave nature o
0 views • 27 slides
Young's Double Slit Experiment and Interference Phenomena
Explore the fascinating world of Young's Double Slit Experiment, where interference and diffraction patterns emerge as monochromatic light passes through two slits. Learn about constructive and destructive interference, how differences in path lengths affect interference patterns, and the concept of
0 views • 5 slides
Light Interference and Interferometry
Discover the fascinating world of light interference and interferometry through examples like Young's double slit experiment and supernumerary rainbows. Understand how the path length difference affects interference levels and delve into the applications of interferometry across various scientific f
0 views • 12 slides
Radio Frequency Spectrum Requirements for Civil Aviation Workshop Proceedings
This document discusses frequency assignment planning and interference models for VHF communication systems in civil aviation. It covers methodologies for establishing separation distances to prevent air-to-air interference and provides insights into interference models for co-frequency separation b
0 views • 13 slides
Enhancing Throughput in Multi-Hop Wireless Networks Using Reconfigurable Antennas
In this study presented at IEEE SECON 2018, the authors investigate the throughput limits of multi-hop wireless networks employing reconfigurable antennas (RAs). Challenges such as unreliable links, interference, and large overhead are addressed, with existing approaches at both the link/network lay
1 views • 29 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Managing Cross-Border Interference in Laos: Insights and Challenges
Explore the management of cross-border interference in Laos through the country's profile, regulator policies, bilateral agreements, and key conclusions. Learn about the frequencies, bilateral relationships with neighboring countries, and the complexities of technological differences along border li
0 views • 10 slides
Interference Protection in Technician Licensing Classes
Learn how to address audio signal distortion, microphone gain settings, and interference issues in radio transmissions to ensure clear communication and compliance with licensing regulations. Discover practical solutions like adjusting transmitter frequency, managing battery power, and using noise b
0 views • 39 slides
Interference Susceptibility Evaluations of Pulsed Radio Altimeters Due to 5G Signal
This document presents the results of interference susceptibility testing of two pulsed radio altimeters in the presence of 5G mobile base station signals. The test parameters, setup, and results are detailed, including in-band and out-band interference evaluations. The objective is to assess the re
0 views • 16 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Enhancing Medium Access Efficiency in IEEE 802.11 Networks
This presentation discusses the utilization of chirp signals for Ultra High Rate (UHR) STAs to access the medium efficiently, transmit reliably at reduced power levels, and handle interference challenges in IEEE 802.11 networks. It explores the concept of chirps, their differentiation from other pro
0 views • 20 slides
ICE: An Integrated Configuration Engine for Interference Mitigation
ICE is an innovative system designed to mitigate interference in cloud services caused by VMs sharing physical hardware resources. The system aims to improve user experience by addressing latency issues through interference-aware configurations and load balancer adjustments. By reducing server load
0 views • 25 slides
Light Interference from Single Atoms and Their Mirror Images
Delve into the intriguing realm of light interference with single atoms and their mirror images, as discussed in a Nature article from 2001. The study challenges the conventional understanding of spontaneous emission and coherence, presenting experimental setups, resonance fluorescence, and the Opti
0 views • 11 slides
Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
2 views • 31 slides
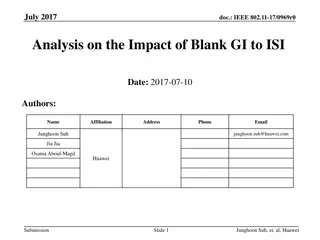
Analysis on Impact of Blank Guard Interval to Inter-Symbol Interference
Performance gain was observed with Blank GI in coping with Inter-Symbol Interference (ISI). However, Intra-Symbol Interference still remains. Three Waveform Coding Designs were evaluated for their effectiveness. The study analyzed the effects of Blank GI on ISI and Intra-Symbol Interference to enhan
0 views • 14 slides
Real-Time Digital Signal Processing Lab: Matched Filtering and Digital Pulse Amplitude Modulation
Explore the concepts of transmitting one bit at a time, matched filtering, PAM systems, intersymbol interference, communication performance, and prevention of intersymbol interference in a two-level digital PAM system. The presentation covers topics like bit error probability, symbol error probabili
0 views • 32 slides
Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Phonological Interference in French BIPA Students: A Literature Study
BIPA students face challenges in pronunciation due to phonological interference, especially in French-speaking students. This study explores the linguistic aspects contributing to pronunciation errors and proposes phonetic corrections. Literature review discusses language interference and factors in
0 views • 11 slides
Receiver Requirements for Realistic Interference Scenarios in Wireless Personal Area Networks
This document discusses the receiver requirements for handling realistic interference scenarios in Wireless Personal Area Networks (WPANs). It covers topics such as second-order distortion, direct conversion receivers, blocker mitigation techniques, and proposals to specify sensitivity levels in the
0 views • 6 slides
Two-Source Interference Patterns
Dive into the fascinating world of two-source interference patterns with the superposition principle, constructive and destructive interference concepts, and demonstrations illustrating how overlapping waves interact. Explore scenarios like people talking simultaneously and ripples on a pond to gras
0 views • 31 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Sub Working Group Conclusions on Various Spectrum Interference Analyses
The draft report highlights conclusions from different sub working groups regarding spectrum interference analyses in various sectors like aeronautical telemetry, small unmanned aerial systems, air combat training systems, and precision guided munitions. It discusses feasibility challenges, separati
0 views • 7 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides