Master NS0-604 Elevate Your Hybrid Cloud - Architect Exam Success
Prepare for the NS0-604 exam and excel as a Hybrid Cloud - Architect. Access comprehensive study materials, practice tests, and expert guidance to ace the certification. Gain the skills and knowledge needed to design, implement, and manage hybrid cloud solutions. Our resources will help you navigate
2 views • 5 slides
Adelaide s Premier Hybrid Solar Systems by Allstate Solar
Allstate Solar, your go-to provider for cutting-edge hybrid solar solutions in Adelaide. Hybrid solar systems combine the best of both worlds, integrating solar power with battery storage to ensure a consistent and reliable energy supply. Whether you're looking to reduce your carbon footprint, save
1 views • 2 slides
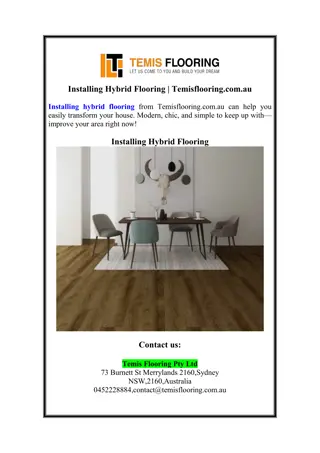
Installing Hybrid Flooring | Temisflooring.com.au
Installing hybrid flooring from Temisflooring.com.au can help you easily transform your house. Modern, chic, and simple to keep up with\u2014improve your area right now!\n\n\/\/temisflooring.com.au\/product-category\/hybrid-floor\/
4 views • 1 slides
Drive Clean Truck Incentive Program Details
Drive Clean Truck initiative in Chicago offers point-of-sale incentives to move fleets towards zero and low-emission vehicles, focusing on Class 2 to Class 8 trucks and buses. The program, funded by the Chicago Department of Transportation and administered by CALSTART, issued $11.3M for 288 trucks a
0 views • 9 slides
Embracing Hybrid Working for Enhanced Productivity
Hybrid working allows employees to work from various locations, blending on and off-campus arrangements. The framework being developed by the Hybrid Working Programme aims to support staff in making informed decisions based on business, team, and individual needs. By focusing on flexibility, social
0 views • 10 slides
Embracing Hybrid Working: A New Framework for Success
Hybrid working offers a flexible approach to work, allowing employees to operate from various locations while ensuring safety and productivity. This new framework being developed aims to support staff in adopting hybrid practices, considering the organization's needs and individual preferences. By v
0 views • 10 slides
UCL Staff Feedback on Hybrid Work Model Implementation
UCL conducted a survey among staff to gather feedback on the interim guidance for transitioning back to onsite work. The survey highlighted staff support for a hybrid work model, emphasizing productivity, efficiency, and well-being benefits. Staff also expressed a preference for clear expectations a
2 views • 21 slides
Cyber Threats and Security Controls Analysis for Urban Air Mobility Environments
The Urban Air Mobility (UAM) environment, with its service-oriented architecture, faces various cyber threats related to end-users, cyber-physical systems, cloud services, and on-premise computing. Threats include unauthorized interception of data, phishing attacks, and Denial of Service (DoS) incid
1 views • 9 slides
Understanding Hybrid Threats and Resilience through Civil Preparedness
Exploring the concept of hybrid threats that combine external threats and internal vulnerabilities, this academic viewpoint by Ramon Loik emphasizes the importance of civil preparedness in building resilience against crises. It delves into aspects such as target selection, active influencing, and th
0 views • 11 slides
Guidelines and Setup for Hybrid Speech Contests
Overview of guidelines for organizing hybrid speech contests, including format guidelines to follow, definitions of online and hybrid contests, and detailed instructions for contest setup in both online-only and hybrid configurations. The guidelines cover aspects such as selecting contest formats, a
3 views • 13 slides
Hybrid Apps vs. Native Apps_ Making the Right Choice for Your Mobile Strategy
Discover the key differences between hybrid and native apps in our latest blog post, \"Hybrid Apps vs. Native Apps: Making the Right Choice for Your Mobile Strategy.\" Learn how each approach impacts performance, user experience, and development cost
0 views • 3 slides
Understanding Planetary Gear Trains in Hybrid Powertrains
Hybrid powertrains utilize planetary gear trains to achieve different operating modes such as motor-alone, engine-alone, combined mode, and more. These gear trains consist of planetary gears orbiting around a central axis, enabling multiple shaft configurations for input and output. Understanding th
0 views • 55 slides
How to Develop Hybrid Work Policies that Boost Employee Productivity_
As the modern workforce continues to evolve, hybrid work models have become a staple in many organizations. A hybrid work environment offers flexibility, enabling employees to work both remotely and in the office. However, with this flexibility comes
0 views • 23 slides
Introduction to NASA Hybrid Rocket Competition
The NASA Hybrid Rocket Competition is sponsored by the NASA Florida Space Grant Consortium and NEFAR. Participants develop a hybrid rocket capable of reaching an altitude of two thousand feet. The rocket utilizes a combination of solid and liquid/gaseous fuels to generate thrust. Motor classificatio
1 views • 29 slides
Guidelines for Session Chairs and Room Managers at Hybrid Conferences
Guidelines and instructions for session chairs and room managers at hybrid conferences are provided, detailing the setup of the hybrid room, onsite and online presentation procedures, responsibilities of session chairs, and the role of the room manager in ensuring smooth coordination between onsite
0 views • 5 slides
Coastal Challenges: Threats and Uses Analysis
The Year 9 Geography homework booklet focuses on the topic of coasts, emphasizing grid references and mapping skills. Students are tasked with identifying grid references for shapes, drawing specific shapes on grids, and demonstrating understanding of 4 and 6 figure grid references. Additionally, in
0 views • 13 slides
High-Frequency Inverter for Hybrid Vehicles
This project focuses on developing a wide-bandgap semiconductor-based, three-phase voltage source inverter for high-frequency electromechanical energy conversion in next-generation hybrid vehicles. With the aim to reduce CO2 emissions by 30% by 2030, the research explores the use of GaN HEMTs in pow
0 views • 8 slides
Advantages of Inter-Especific Hybrid Cotton Varieties in the Mediterranean Area
The research conducted by Manuel Lopez Garcia, Felipe Rey Montero, and Khaled Shalabi focuses on studying different cotton varieties in Spain through pivot irrigation systems to determine the species best suited for the Mediterranean climate. The study, initiated in 2014, compared fertigation system
1 views • 26 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Construction Schedule for Baseline and Hybrid A Configuration at J-POWER MDI-CFS Meeting, Ichinoseki City, Japan
This document outlines the construction schedule for the Baseline and Hybrid A configurations for the J-POWER MDI-CFS Meeting held in Ichinoseki City, Japan. It includes details of the Baseline, Hybrid A structures, assumption of the schedule, issues discussed, and the construction procedures for th
2 views • 12 slides
Enhancing Student Interaction in Hybrid Teaching with BigBlueButton: Strategies and Considerations
Exploring the utilization of BigBlueButton (BBB) for hybrid teaching environments, this study delves into the opportunities and challenges faced by educators in fostering student interaction. From managing group work in hybrid formats to overcoming technical hurdles in online settings, valuable insi
0 views • 10 slides
Mobile Issues and Cyber Threats in Nigeria - Presentation by Dr. J.O. Atoyebi, NCC
Evolution of GSM in Nigeria, the impact of mobile phone deregulation, and the rise of cyber threats highlighted in a presentation by Dr. J.O. Atoyebi of the Nigerian Communications Commission. The report reveals Nigeria's position in global internet security threats and the challenges faced by the c
0 views • 7 slides
Challenges and Strategies for Leading Hybrid Teams in the Workplace
Managing hybrid teams presents challenges related to changes in work culture, fear, crisis management, and more. Issues such as balance, loneliness, and disconnect can arise in hybrid working environments. Despite these challenges, effective communication, equity awareness, and strategic leadership
0 views • 25 slides
Understanding Hybrid Dispute Resolution Processes
This content delves into the realm of hybrid dispute resolution processes, exploring concepts such as Med-Arb, Arb-Med, and Arb-Med-Arb. It highlights important terminologies, variations on hybrid themes, and ethical considerations for single neutrals in the alternative dispute resolution landscape.
0 views • 18 slides
Recognizing and Preventing Insider Threats in National Security
Insider threats pose a significant risk to national security and industry, involving individuals using authorized access to carry out harmful actions. This content covers the definition of insider threats, indicators, consequences, and ways to recognize and report suspicious behaviors. It emphasizes
0 views • 15 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Analysis of 20T Hybrid Block-Coil V5.8 Magnetic Model
This analysis focuses on the magnetic model of a 20T hybrid block-coil V5.8 system, including modifications to incorporate ribs, iron components, rigid boundaries, component bonding, sliding and separating configurations, and stress evaluations. The study explores the layout adjustments, peak magnet
0 views • 5 slides
Addressing Revenue Shortfalls from Hybrid and Electric Vehicles in Virginia
Gasoline tax revenues in Virginia fund road construction and maintenance, but the increase in electric and hybrid vehicles poses a challenge to this revenue source. The Commonwealth needs to incentivize electric and hybrid vehicles while maintaining funds for infrastructure. Recommendations include
0 views • 14 slides
Understanding Cyber Threats in Today's Digital Landscape
Cyberspace is a vast realm encompassing the Internet, where we engage in various activities ranging from communication to entertainment. With the majority of children exposed to the online world, cybersecurity awareness is crucial to tackle the rising cyber threats. These threats include job frauds,
0 views • 33 slides
Understanding Experiments and Threats to Validity
Explore the world of experimental research, internal and external validity, threats to validity, and the importance of proper study design in ensuring the credibility of research results. Learn about confounding variables, threats to internal validity such as environmental factors and group comparis
0 views • 15 slides
Understanding Electric and Hybrid Vehicles: Hybridization and Interdisciplinary Aspects
Electric and hybrid vehicles (HEVs) feature different hybridization ratios based on the power rating of their electric motors. Concepts like full hybrid, mild hybrid, and micro hybrid define the extent of electric motor usage for driving. HEVs involve a mix of electric machines, power electronics, b
0 views • 50 slides
The Science Behind Hybrid AC Systems Comfort Meets Efficiency
Discover how Hybrid AC systems maximize comfort and efficiency by switching between electricity and gas, reducing energy costs while providing climate control. \/\/help4seo.com\/the-science-behind-hybrid-ac-systems-comfort-meets-efficiency\/
1 views • 1 slides
Hybrid Optimization Heuristic Instruction Scheduling for Accelerator Codesign
This research presents a hybrid optimization heuristic approach for efficient instruction scheduling in programmable accelerator codesign. It discusses Google's TPU architecture, problem-solving strategies, and computation graph mapping, routing, and timing optimizations. The technique overview high
0 views • 33 slides
Best Hybrid Sets in Cabramatta West
Are you looking for the Best Hybrid Sets in Cabramatta West? Then contact Lash Bee Studio. Their expert technicians offer a variety of lash options, from natural lash lifts to glamorous hybrid lashes, tailored to your style. Beyond lashes, they provi
0 views • 6 slides
Best Hybrid Sets in Cabramatta West
Are you looking for the Best Hybrid Sets in Cabramatta West? Then contact Lash Bee Studio. Their expert technicians offer a variety of lash options, from natural lash lifts to glamorous hybrid lashes, tailored to your style. Beyond lashes, they provi
0 views • 6 slides
Navigating Current and Emerging Cyber Threats: Leadership Insights
Delve into the realm of current and emerging cyber threats with a focus on leadership considerations. Understand the evolving landscape of cyber risks, the importance of cyber expertise in leadership planning, and the essential role of cybersecurity in today's digital world. Explore the various thre
0 views • 16 slides
Understanding Threats and Attacks in Information Systems
Threats and attacks pose risks to information systems through vulnerabilities that can be exploited, leading to data loss, system unavailability, and compromised security. Four primary classes of threats include unstructured threats from inexperienced individuals, structured threats from skilled hac
0 views • 21 slides
Comparison of Traditional and Cyber Threat Assessment Methodologies
In the digital age, understanding cyber threats alongside traditional threats is crucial. Cyber adversaries operate globally and are hard to identify, posing challenges for intelligence agencies. The ease of acquiring cyber skills and resources makes cyber threats dynamic and dangerous. Classical cy
0 views • 17 slides
Benefits of Hybrid Cars Explained with Facts and Figures
Learn about the advantages of hybrid cars, including lower emissions, cost savings, and environmental benefits compared to petrol cars. Discover why hybrid cars are a practical and eco-friendly choice for modern drivers.
0 views • 10 slides
STEAME Goes Hybrid: Blueprint Guidelines and Policy Recommendations Project
The project funded by the European Commission aims to introduce STEAME hybrid learning environments through blueprint guidelines and creativity plans. Teachers will be trained in recording and implementing hybrid learning ideas using Learning and Creativity (L&C) Plan templates, enhancing their abil
0 views • 29 slides