Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Discover the Hottest In-Frame Kitchen Designs of 2024
As an expert kitchen designer, it's thrilling to explore the evolving trends of Inframe Kitchen designs in the UK for 2024. At the heart of these trends is the resurgence of the In Frame Shaker Kitchen, which combines timeless elegance with modern functionality. To learn more visit here:https:\/\/ex
0 views • 9 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
IEEE 802.11-21/1737r0 Beacon and Group Frames Information
An IEEE document from November 2021 discusses Beacon and group frames in wireless networks, focusing on out-of-band signaling to improve BSS range determination and frame reception by non-AP MLDs. It addresses the impact of frame types and MCS on BSS range and transmission rates, proposing solutions
3 views • 14 slides
Soil Conservation Practices: Building an A-Frame for Erosion Control
Learn about the importance of soil conservation practices and how to build and utilize an A-frame tool for erosion control. Discover the causes of soil erosion and effective techniques like contour lines, contour planting, and vegetative barriers to prevent soil degradation. Find out how to construc
2 views • 14 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Operational Guidelines of the WCA 2020 Agricultural Census Frame Preparation
The webinar focuses on the preparation of frames and mapping for the Operational Guidelines of the WCA 2020 in the Europe and Central Asia region. It covers the definition of frames, types of frames, sources of information, guidelines for building frames, requirements for different census modalities
0 views • 33 slides
Creating an Archery VR Game with A-Frame and Unity - Project Journey
Embark on a virtual reality adventure through the development stages of an Archery VR game using A-Frame and Unity. Dive into VR technology, explore A-Frame vs. Unity, tackle coding challenges, conduct tests, and witness the final project demonstration. Follow the journey of building a VR archery ga
0 views • 11 slides
Understanding Wide Area Networking Using Frame Relay Cloud
The field of networking is advancing rapidly, with technologies like cloud computing relying on robust wide area networking. This presentation explores the use of Frame Relay Cloud in improving the security and configuration complexities faced in interconnecting wide area networks. It discusses the
0 views • 16 slides
Understanding Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Investigating Performance Bottlenecks in Smart Pointer Management
Investigation into performance issues caused by smart pointer manipulation, focusing on the use of boost
0 views • 8 slides
Understanding Earth Rotation and its Reference Frame
Exploring the dynamics of Earth's rotation, this content delves into the geoid as a reference frame for pressure calculations, rotating coordinates, and the concept of centripetal and centrifugal forces. Learn about the Earth's rotating reference frame, angular velocity, and how to calculate speed a
0 views • 19 slides
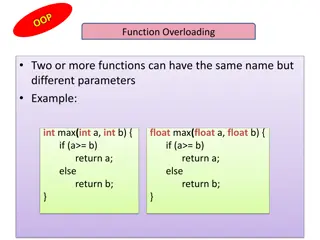
Understanding Function Overloading and this Pointer in C++
Explore the concept of function overloading in C++, allowing multiple functions with the same name but different parameters. Learn about the this pointer in object-oriented programming, which holds the memory address of the current object using a function. See examples of how to implement these conc
0 views • 13 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Effective S106 Process Management in Local Authority: Insights from Stephen Pointer, Harborough District Council
Explore the expertise of Stephen Pointer, Strategic Planning and Housing Manager at Harborough District Council, in managing an effective Section 106 (S106) process. Discover his role, responsibilities, and experiences in navigating the complexities of national and district contexts, community inter
0 views • 19 slides
Mitigating Client Frame Tracking in IEEE 802.11 Networks
Unencrypted and predictable frame fields in IEEE 802.11 networks can lead to client frame tracking, compromising user privacy. The Client Frame Tracking Countermeasures (CFTC) proposal aims to prevent tracking across epoch boundaries by obfuscating critical fields like PN, SN, and AID. Each epoch, l
0 views • 17 slides
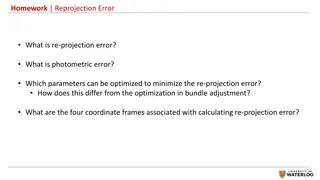
Understanding Spatial Error in Photogrammetry
Reprojection error in photogrammetry refers to the discrepancy between a known point in a scene and its projected position on an image. Photometric error, on the other hand, involves errors related to pixel intensity values. To minimize reprojection error, parameters such as camera intrinsics, extri
0 views • 5 slides
IEEE 802.11-17-1728-01-000m: Frame Body Capture Effect Study
Examining the impact of frame overlap in wireless networks during dense deployment scenarios, where stronger frames interfere with weaker ones, resulting in potential data loss and synchronization issues. Testbed evaluations reveal challenges and consequences of frame capture effects on standard com
0 views • 13 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing ov
0 views • 25 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Automatic Generation of Research Highlights from Scientific Abstracts
Huge growth in scientific publications has made it challenging for researchers to keep up with new research. This project focuses on automatically constructing research highlights from paper abstracts using deep learning models. The system employs sequence-to-sequence models with attention and point
0 views • 9 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Understanding Pointers in C: A Beginner's Guide
Delve into the world of pointers in C with this comprehensive guide covering topics such as the address operator, pass by copy versus pass by reference, pointer usage, NULL pointers, pointer allocation, and practical experiments to enhance your understanding. Learn about the fundamentals of pointers
0 views • 22 slides
Towards Low-Bandwidth Video Chats on Smartphones
This study by Xin Qi, Qing Yang, David T. Nguyen, Gang Zhou, and Ge Peng from the College of William and Mary focuses on reducing data usage in video chats on smartphones. The research explores methods such as reducing frame rate, context-aware frame rate adaption, and frame interpolation to maintai
0 views • 22 slides
Understanding Smart Pointers in C++ - Bonus Lecture CSE390c Spring 2022
Explore the concept and benefits of smart pointers in C++ as a solution to managing heap-allocated memory more effectively. Learn about avoiding memory leaks and errors when handling pointers through smart pointer implementation. Dive into a Toy Smart Pointer example using a custom class template.
0 views • 36 slides
Kookmin University PHY and MAC Proposal for Image Sensor Communication
Kookmin University's proposal focuses on the general architecture of PHY and MAC layers for image sensor communication. The document covers design principles, compatibility features, frame formats, error correction, and various considerations related to supporting commercial cameras, frame rates, sa
0 views • 39 slides
Seeking a General-Purpose CCSDS Link Layer Protocol: Next-Generation Data Link Protocol (NGDLP)
This document discusses the proposed Universal Frame Format for a next-generation data link protocol, focusing on major questions about transfer frames, Protocol Link Transmission Unit (PLTU), and Universal Transfer Frame Structure. It explores topics such as frame formats, telemetry transfer frames
0 views • 24 slides
Understanding DDoS Attacks: Simulation, Analysis & Defense
Delve into the world of Distributed Denial of Service (DDoS) attacks with this comprehensive study covering the architecture, advantages, bot installation phases, attack methods, defenses, and simulation. Learn about the detrimental impact of DDoS attacks on servers, their multi-tiered structure, an
0 views • 20 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides