Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B073DZCNTR\n\n[READ DOWNLOAD] Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept to Implementation (Springer Praxis Books) | Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept t
1 views • 6 slides
READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B004NNUV54\n\n[READ DOWNLOAD] Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Praxis Books) | Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Pra
1 views • 6 slides
Conquer Clutter! Xtended Space: Your Storage & Organization Partner
Drowning in Stuff? Xtended Space offers secure storage solutions & organization hacks! Flexible plans, easy access, & top-notch security. Declutter your home & reclaim your space. Free consultation - Call Today at 9009000798. Our customizable storage units and modular systems offer flexibility to fi
5 views • 2 slides
Boost Your Restaurant's Efficiency and Growth with Xtended Space Storage Solutio
Does a lack of space hinder your restaurant's efficiency and growth? Xtended Space offers storage solutions that can help you organize your kitchen, free up space, and create a smoother workflow. This can lead to improved teamwork, happier customers, and even additional revenue streams. Let Xtended
10 views • 3 slides
United States Space Systems Command International Affairs Overview
The United States Space Systems Command's International Affairs division emphasizes partnership with countries worldwide to address the challenges of the current decade. The presentation highlights the growing threats in space, including developments by Russia and China, stressing the need for a res
0 views • 5 slides
Analysis of FY24 DoD Space Budget Requests for Space Force and Research & Development
The FY24 DoD Space Budget Requests show significant increases for the Space Force along with notable shortfalls and funding disconnects. The Space Force budget includes funding for core programs but also faces challenges in fully funding essential capabilities. The Research & Development budget sees
0 views • 18 slides
Four-Year Plan for WMO Space Weather Activities 2024-2027
Space Weather is a crucial aspect of the natural space environment affecting various technologies on Earth and in space. The plan outlines goals, historical context, and key recommendations by INFCOM-3 for monitoring and modeling solar, magnetospheric, and ionospheric activities. Integration of Spac
0 views • 9 slides
Sustainable Development of Outer Space Activities and Planet Earth: UN/Austria Symposium Insights
Discussion on the long-term sustainability of outer space activities and its impact on Earth at the UN/Austria Symposium. Highlights COPUOS's role in promoting peaceful space use, international space law development, and space debris mitigation. It addresses key areas like space exploration, safety,
0 views • 9 slides
National Aeronautics and Space Administration (NASA) Overview
The National Aeronautics and Space Administration (NASA) is America's leading civil space program focused on space exploration, scientific research, and technological advancements. With a workforce of nearly 18,000, NASA's mission includes human expansion across the Solar System, economic growth in
3 views • 9 slides
Fully Homomorphic Encryption: Foundations and Applications
Fully Homomorphic Encryption (FHE) allows computations on encrypted data without decrypting, enabling secure outsourcing of computations to untrusted servers. FHE involves key generation, encryption, homomorphic evaluation, and decryption processes. It ensures correctness, security, and compactness
0 views • 31 slides
Configuring Local Storage and File System in Linux System Administration
This module focuses on LUKS-Encrypted File Systems in Linux, detailing their design, benefits, and how to mount, unmount, and remove them securely. LUKS provides a secure standard for hard disk encryption, supporting multiple keys/passphrases and enabling effective passphrase revocation. Learn how t
0 views • 50 slides
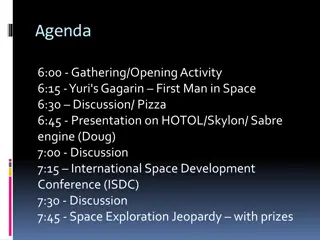
A Brief History of Space Exploration
Space exploration has seen significant milestones, from the German V2 rocket in 1942 to Yuri Gagarin becoming the first man in space in 1961 and the historic Apollo 11 moon landing in 1969. Animals like fruit flies and monkeys have ventured into space, contributing to scientific understanding. Russi
2 views • 14 slides
Exploring Space: From Yuri Gagarin to Modern Innovations
Discover the fascinating journey of space exploration from Yuri Gagarin's historic flight as the first man in space to modern innovations like the V-2 Rocket and the development of the Karman Line. Dive into key events such as the launch of the first intercontinental ballistic missile (ICBM) and the
2 views • 30 slides
Secure Memory Encryption Techniques for Virtual Machines across Multiple Hosts
Virtual machines with large memory capacities are common in cloud environments. To enhance security during VM migrations and data transmissions, techniques like split migration, encrypted split migration, and encrypted remote paging are employed. However, challenges such as data leakage, high CPU ut
0 views • 16 slides
Exploring Space: Pioneers, Missions, and the Role of Animals
Humans have a rich history of space exploration, with notable milestones including Yuri Gagarin's orbit in 1961, the Apollo 8 moon mission, and Sally Ride becoming the first American woman in space. Before human space travel, animals played a crucial role in understanding the effects of space on liv
4 views • 21 slides
Efficient Rekeying for Encrypted Deduplication Storage
Cloud storage outsourcing is common today, presenting challenges like security and storage efficiency. Encryption and deduplication play crucial roles in addressing these challenges. However, traditional encryption methods inhibit deduplication. Rekeying offers a solution by renewing security protec
0 views • 27 slides
WhatsApp End-to-End Encrypted Backup Protocol Security Analysis
This security analysis delves into the WhatsApp end-to-end encrypted backup protocol, highlighting the potential risks associated with chat history backups. It discusses the dangers of password guessing, the vulnerabilities of cloud providers, and proposes solutions for a more secure backup system t
0 views • 20 slides
Mitigating Conflict-Based Attacks in Modern Systems
CEASER presents a solution to protect Last-Level Cache (LLC) from conflict-based cache attacks using encrypted address space and remapping techniques. By avoiding traditional table-based randomization and instead employing encryption for cache mapping, CEASER aims to provide enhanced security with n
1 views • 21 slides
European Deep Space Surveillance and Tracking Collaboration
EU Space Surveillance and Tracking program involves five European nations collaborating to assess and reduce risks to European spacecraft, provide early warnings for re-entries and space debris, and prevent space debris proliferation. Available deep space sensors, such as optical telescopes, are uti
1 views • 8 slides
Encrypted Deduplication for Secure Cloud Storage
Encrypted deduplication enhances data storage efficiency by eliminating duplicate chunks and encrypting outsourced data to protect against cloud service providers. This approach uses message-locked encryption and metadata management to store unique data and key mappings securely. By leveraging encry
0 views • 24 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Securing Protocols with Fully Encrypted Protocols (FEPs)
In this research presented at the Cryptographic Applications Workshop, Ellis Fenske and Aaron Johnson address the challenges of Fully Encrypted Protocols (FEPs). They highlight the lack of precise understanding, formalized goals, and proven security in existing FEPs. The work introduces new security
0 views • 29 slides
Homomorphic Encryption and RLWE Schemes Overview
Homomorphic encryption allows computation on encrypted data, enabling privacy in outsourced computing services and applications like spam filters for encrypted mail. The Ring Learning With Errors (RLWE) scheme and its properties are discussed, along with symmetric encryption from RLWE and fully homo
0 views • 16 slides
Internet Number Resource Report June 2013
This report provides detailed information on the status of Internet number resources as of June 2013, including IPv4 address space allocations, available IPv4 /8s in each Regional Internet Registry (RIR), IPv4 address space issued by RIRs to customers, ASN assignments, 4-byte ASN assignments, and IP
0 views • 18 slides
Testing in Space Simulation Facilities: A Comprehensive Analysis
This webinar delves into testing in space simulation facilities, comparing the requirements at different stages of space missions such as launch, cruise, and operations. Presented by Miracle Israel Nazarious, it covers topics including space qualification testing involving static load, vibration, th
0 views • 12 slides
Ethics and Impacts of Space Expansion
Ethical considerations surrounding space exploration and expansion are discussed, highlighting both promising and problematic aspects. The debate includes the value of space science, environmental impacts, and the need for responsible expansion to mitigate potential damages. Topics such as launch si
0 views • 21 slides
Exploring Careers in the UK Space Sector
Discover the diverse job opportunities in the UK space industry and explore various disciplines of science involved. Learn about different roles such as design engineer, space business manager, space artist, and more. Find out how to enter these careers through university courses, apprenticeships, o
0 views • 20 slides
Encrypted Data Deletion for Cloud Storage Servers
Explore the concept of software with certified deletion for private cloud storage servers. Discover how data recoverability is influenced by secret key leaks and encryption scheme vulnerabilities. Learn about techniques for computing on encrypted data and ensuring provable deletion, with a focus on
0 views • 29 slides
Understanding Cryptanalysis: Key Concepts and Techniques
Cryptanalysis is a fundamental aspect of cryptography that involves decoding encrypted communications and messages. This topic delves into the basic cryptographic tools, such as the Caesar cipher, and explores how encryption and decryption functions work. By understanding cryptanalysis, you can anal
0 views • 12 slides
Managing Conflicts in Commercial Space Activities
Explore the challenges arising from the commercialization of space activities, the shift in focus towards sustainable space use, and the need to harmonize modern commercial ventures with traditional space laws to prevent conflicts among diverse space actors.
0 views • 14 slides
Development of GR740 Single Board Computer Reference Design by RUAG Space and Partners
RUAG Space collaborates with Gaisler and other partners in the development of a GR740-based single board computer reference design funded by ESA. The project aims to create an advanced technology platform for future space projects, leveraging RUAG's expertise in electronics and digital computers for
0 views • 12 slides
Overview of Fundamental Principles of Space Law and Outer Space Treaties
The content discusses the fundamental principles of space law highlighted at the United Nations Space Law Conference 2020, focusing on key treaties such as the Outer Space Treaty of 1967 and associated rights, duties, and obligations of states in space exploration and use, including non-appropriatio
0 views • 16 slides
The Manfred Lachs International Conference on Conflicts in Space and the Rule of Law
The 4th Manfred Lachs International Conference held in Montreal in 2016 explored the intersection of conflicts in space and the rule of law, specifically focusing on the legal framework surrounding outer space weaponry. Discussions highlighted the importance of upholding humanitarian values, promoti
0 views • 7 slides
FY23 DoD Space Budget Overview and Investments
The FY23 Department of Defense (DoD) budget continues to prioritize investments in national security space capabilities, with a $1.6B increase in funding for DoD space programs. The United States Space Force receives significant appropriations exceeding the request, emphasizing oversight and managem
0 views • 16 slides
Secure Out-of-Band Remote Management Using Encrypted Virtual Serial Consoles in IaaS Clouds
IaaS clouds provide virtual machines for users to manage through SSH. In scenarios where in-band remote management is not feasible, out-of-band remote management using Virtual Serial Consoles (VSC) offers a secure solution. However, challenges such as untrusted admins and potential attacks exist, wh
0 views • 22 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
Personalized Celebrity Video Search: Cross-space Mining Approach
This study presents a novel approach for personalized celebrity video search based on cross-space mining, aiming to match user interests with celebrity popularity. By learning the interest space of users and the popularity space of celebrities, the framework correlates the two spaces to enhance sear
0 views • 23 slides
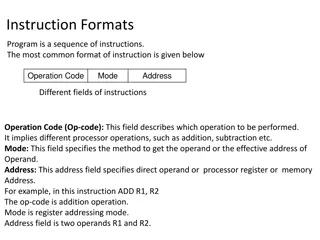
Understanding Different Instruction Formats in Computing
Instruction formats in computing include one-address, two-address, three-address, and zero-address instructions, each with specific ways of specifying operations and operands. One-address instructions utilize an implied accumulator register, while two-address and three-address instructions allow for
0 views • 18 slides
Quantum Space-Bounded Complexity in Logarithmic Space: A Comprehensive Overview
Quantum space-bounded complexity explores the memory requirements for solving problems in log space. Examples include matrix multiplication, undirected graph connectivity, and problems like inverting matrices and determining connectivity. The significance of deterministic log space (NL) and nondeter
0 views • 49 slides
Space Debris Removal - Towards Sustainable Space Traffic Management
The 3rd Annual Manfred Lachs Conference in Montreal discussed the pressing issue of space debris removal and the need for a legal framework for space traffic management. With the increasing number of objects in Earth's orbit posing a risk, international collaboration and regulatory initiatives are e
0 views • 9 slides
![Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te](/thumb/21519/read-ebook-pdf-linking-the-space-shuttle-and-space-stations-early-docking-te.jpg)
![READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea](/thumb/21554/read-pdf-emerging-space-powers-the-new-space-programs-of-asia-the-middle-ea.jpg)