Campus Mail Services Package Shipping Tutorial
This tutorial guides you through the process of creating your ship request, validating return addresses, entering recipient addresses, verifying recipient addresses, providing package information, selecting a carrier, entering your cost account number, printing the ship request form, and attaching i
4 views • 8 slides
What is Email Marketing?
Email marketing is a cornerstone of digital marketing, leveraging targeted email communication to engage subscribers and drive desired outcomes. By crafting compelling content, personalized messages, and strategic segmentation, businesses can cultivate meaningful relationships with their audience. B
1 views • 7 slides
Enterprise Marketing Management (EMM) Capabilities for Effective Email Campaigns
Enterprise Marketing Management (EMM) offers a comprehensive suite of tools for tracking marketing expenditure, ROI, and lead performance. With capabilities ranging from Marketing Activity Codes (MAC) for tracking sources to customizable email templates and delivery reports, EMM streamlines the proc
0 views • 8 slides
Bluetooth Low Energy Addresses in IEEE 802.11-21/1535r0
The document explores the features of resolvable addresses in Bluetooth Low Energy (BLE) within the IEEE 802.11-21/1535r0 standard. It discusses the two types of addresses in BLE, Public and Random, and their usage. The emphasis is on Random addresses due to their popularity and privacy features. Th
2 views • 11 slides
Mail Server Basics from a Linux Operating System Perspective
Dive into the essentials of mail servers, exploring the key components of an email system, such as email clients and servers. Learn how email clients work, the functions they offer, and the role of email servers in managing and routing messages to ensure delivery over the Internet.
0 views • 25 slides
Mastering Email Management: Practical Tips for Efficiency
Learn how to conquer your email inbox with practical tips from Michael Lucido, MD, PhD, and David Thylur, MD. This seminar aims to improve your email culture, personalize management strategies, and enhance Outlook skills for increased efficiency. Discover how to shift to a compassionate email cultur
0 views • 18 slides
IPv4 Addresses and Classful Addressing in Computer Networks
Explore the basics of IPv4 addresses, address space, hierarchy in addressing, and classful addressing in computer networks. Learn about the unique 32-bit structure of IPv4 addresses, address space calculation, notation methods, and the hierarchical nature of network addressing. Dive into the concept
2 views • 14 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Mastering Email Communication: Layouts, Etiquette, and Best Practices
Dive into the world of email communication with this comprehensive guide covering email layouts, etiquette tips, common purposes, and general email format. Learn how to effectively structure your emails, address recipients, and maintain professionalism in your online correspondence.
0 views • 41 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
1 views • 8 slides
Professionalism and Communication in the Digital Age
This presentation delves into the nuances of professionalism and effective communication in today's digital world, emphasizing the importance of email and social media etiquette. It explores topics such as managing perceptions, the myth of casual email, the value of business email, and the essential
0 views • 24 slides
UNDERSTANDING EMAIL,SPF,DKM,AND DMARC
Email infrastructure involves protocols like SPF, DKIM, DMARC, and SMTP to ensure secure and reliable communication. SMTP is used to transport emails between servers, while MTA acts as the mail transport agent. Understanding these components is crucial for effective email communication and troublesh
5 views • 14 slides
Essential Email Writing Guidelines and Etiquette
Understanding the importance of email writing, this guide covers the functions, advantages, and pitfalls of using emails. It delves into the reasons for the popularity of emails, common mistakes to avoid, and key principles for composing effective emails. Additionally, it provides insights into emai
0 views • 8 slides
Mastering Email Management: Tips, Statistics, and Best Practices
Explore key insights and strategies for effective email management in the digital age. Discover email statistics, protocol etiquette, inbox management techniques, and insights on popular email platforms like Gmail. From understanding email distributions to implementing rules and filters, enhance you
0 views • 7 slides
Mastering Email Communication for Effective Interactions
Enhance your email communication skills by understanding the nuances of emotional intelligence, proper email etiquette, and effective email format. Learn how to craft compelling subject lines, avoid common email pitfalls, and tailor your tone based on recipients. Discover strategies for improved ema
0 views • 16 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
Email Campaigns in Internet Marketing
Email campaigns have transformed communication by allowing easy distribution of messages and documents worldwide within seconds. They can take various forms like direct emails, newsletters, and press releases. This chapter explores different types of email campaigns, including direct mail vs. direct
0 views • 25 slides
Addressing Privacy Concerns in IEEE 802.11-21: Changing MAC Addresses for Improved Security
The document discusses the implications of changing STA MAC addresses per association in IEEE 802.11-21 standard to enhance privacy and security. It explores the challenges of maintaining persistent identifiers in data frames and the risks associated with sending source/destination addresses in clea
0 views • 11 slides
Contact Information and Email Addresses
This content provides a list of contact information and email addresses for various individuals. It includes details such as email addresses, websites, and names. It emphasizes the importance of checking for updates in the school newsletter and emails. The information is presented in a structured fo
0 views • 22 slides
Mastering Email Communication in the Workplace
Dive into the intricacies of email communication in the workplace with insights on when to send emails, email etiquette, and valuable tips for composing effective professional emails. Understand the role of email in modern organizations, learn the do's and don'ts of email messaging, and enhance your
0 views • 32 slides
Email Technologies and Infrastructure
Explore the intricacies of email technologies, infrastructure, and architecture, including the format of HTTP messages, the role of proxy servers, creating web servers, and key components of email systems like user agents, mail servers, and SMTP protocol. Delve into email protocols like SMTP, POP3,
0 views • 38 slides
Email Security and Encryption Technologies Overview
Email security is crucial in today's digital world. This content discusses various email security measures, including PGP and S/MIME systems, and their utilization in business and personal communications. It also explores the history of PGP encryption, the role of Philip R. Zimmermann, and the chara
0 views • 10 slides
IP Addressing in Computer Networks
IP addressing provides a seamless network for users by abstracting and providing a uniform addressing scheme used by higher-layer protocols and applications. IP addresses identify connections rather than specific computers, with IPv4 using 32-bit integers and IPv6 using 128-bit addresses. The divisi
0 views • 19 slides
Mastering Email Etiquette for Business Success
Enhance your professional image by mastering email etiquette. Learn how to represent your company well, write effective emails, use proper subject lines, address recipients professionally, and avoid common mistakes. Understand the importance of email security and when not to use email for sensitive
1 views • 32 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Effective Email Strategies: Taming the Tiger
Strategies for managing email effectively are discussed in "Taming the Tiger: Strategies for Effective Use of Email," featuring insights from Elaine Shuck and Janine Lim. Tips include organizing emails into folders, using filters for newsletters and social media, and unsubscribing from listservs to
0 views • 25 slides
Privacy Address Requirements for Wireless Personal Area Networks
This document discusses the privacy address requirements for IEEE P802.15 Working Group's TG4ab standard for Wireless Personal Area Networks (WPANs). It covers the need for 48-bit addresses with collision resistance, the use of different privacy addresses for each frame, and the adequacy of 12-bit c
0 views • 8 slides
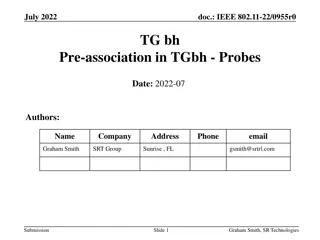
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
Network Security Part 2: Link Layer and ARP
Exploring the vulnerabilities in simple network topologies with hubs and the need for examining the link layer to prevent eavesdropping. Dive into MAC addresses, ARP (Address Resolution Protocol), and how machines translate IP addresses to physical Ethernet addresses. Learn about ARP tables, the tra
0 views • 61 slides
IP Addresses and Their Classification
IP Addresses, short for Internet Protocol addresses, are unique identifiers assigned to devices on a network. They can be IPv4 or IPv6, with IPv4 having 32 bits and IPv6 being 128 bits. IP addresses are classified into classes A, B, and C, each with specific range and usage. Understanding IP address
0 views • 14 slides
Address Resolution Protocol (ARP) in Computer Networks
Address Resolution Protocol (ARP) is essential for translating IP addresses to MAC addresses in computer networks. ARP facilitates communication between devices on the same network by resolving addresses and enabling efficient data transmission. This protocol involves message exchanges, hardware bro
0 views • 20 slides
IPv6 Public Policy Considerations - Addressing the Global IP Address Shortage
In light of the global shortage of IPv4 addresses, there is a pressing need for a fair policy for the allocation of remaining addresses. The rapid growth of the Internet has further increased demand for IP addresses, with IPv4 expected to run out soon. The deployment of IPv6 has become a critical is
0 views • 23 slides
Deliverability and IP Warming in Email Marketing
Explore the concepts of deliverability and IP warming to improve your email marketing strategy. Learn about the importance of sender reputation, key factors affecting email delivery, and the methodology for warming up IP addresses. Discover how to establish a positive sender reputation and navigate
0 views • 15 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Office 365 Email & Security Workshop Highlights
Office 365 Email & Security workshop was held with presenters Jason Hetterle, Steve Garcia, and Joseph Andreason covering topics like security awareness, self-service password reset, Office 365 webmail features, and more. The agenda included discussions on security measures, a case study on an anato
0 views • 9 slides
Challenges of Running an Email Campaign Without DMARC (1)
Secure Your Email Campaigns Today\nDon\u2019t let the absence of a DMARC record hinder your email marketing efforts. Take control of your domain\u2019s security, enhance email deliverability, and safeguard your brand from fraud.\nSet up your DMARC re
2 views • 2 slides