Computer Peripherals and Interfacing
Computer peripherals are external devices that enhance the functionality of a computer. They include input devices like keyboards and mice, output devices like printers and monitors, and storage devices like hard disk drives and solid-state drives. Interfacing circuits connect these peripherals to t
1 views • 6 slides
Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
Safeguarding Canada's Research: Policy on Sensitive Technology Research and Affiliations of Concern (STRAC)
Canada's new Policy on Sensitive Technology Research and Affiliations of Concern (STRAC) aims to protect the country's research ecosystem from foreign entities posing security risks. The policy restricts funding for projects involving sensitive technology research if affiliated with military or stat
1 views • 10 slides
Advancements in Crystal Technology for Replacement of Electrostatic Septa
Crystal technology is being explored as a replacement for electrostatic septa in particle accelerators like the SPS at CERN. The transition aims to improve beam extraction efficiency and reduce radiation levels, impacting personnel safety and equipment lifespan. Various parameters and performance re
1 views • 17 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
3 views • 26 slides
TSN and Time Sensitive Wireless
This document explores the relationship between IEEE 802.11 and Time Sensitive Networking (TSN), defining TSN in the context of 802.11 and highlighting the importance of TSN for improving packet delivery, reducing latency, and enhancing network reliability. Various features like Multi-AP, preemption
6 views • 18 slides
Understanding Network Devices and Connectivity
Network devices play a crucial role in connecting computers and printers to networks, facilitating fast and secure data transfer. These devices, such as network interface cards and WiFi cards, help devices communicate effectively on the same or different networks. MAC addresses uniquely identify dev
6 views • 31 slides
Mistakes to Avoid When Parenting as a Sensitive Father_
Are you a sensitive father raising a strong-willed child? While it's natural to make mistakes along the way, being aware of common pitfalls can help you navigate parenthood more effectively. Below, we are going to outline some common mistakes to steer clear of when parenting as a sensitive father, d
7 views • 6 slides
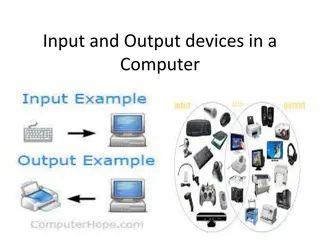
Understanding Input and Output Devices in Computing
In computing, input and output devices play a crucial role in enabling communication between users and computers. Input devices are used to enter data into a computer, while output devices display or provide the results of processed information. Common input devices include keyboards, mice, and joys
0 views • 17 slides
Understanding Basic Input/Output Operations in Computer Organization
Basic Input/Output Operations are essential functions in computer systems that involve transferring data between processors and external devices like keyboards and displays. This task requires synchronization mechanisms due to differences in processing speeds. The process involves reading characters
0 views • 11 slides
Understanding Electronic Components and Input/Output Devices
Explore the world of electronic components, input devices, and output devices through energy changes and symbol representations. Learn about LEDs, resistors, and energy conversions in a hands-on manner. Discover the role of various devices like microphones, solar cells, loudspeakers, and diodes in c
1 views • 24 slides
Understanding Computer Peripheral Devices: Definition, Examples, and Types
Learn about computer peripheral devices, which enhance a computer system's functionality. Examples include mice, keyboards, monitors, printers, and scanners. These devices can be categorized into input, output, and storage devices, each serving a specific purpose to expand the capabilities of your c
2 views • 13 slides
Understanding Programmable Logic Devices (PLD) in Digital Electronics
Programmable Logic Devices (PLDs) are versatile electronic components used to create reconfigurable digital circuits, distinct from fixed-function integrated circuits. PLDs require programming before use, enabling customization for specific functions. This article explores PLDs, digital electronic s
0 views • 10 slides
Automotive Grade 10 Joining Methods: Locking Devices Overview
Automotive Grade 10 explores joining methods using locking devices to prevent nuts from loosening due to movement and vibration. Friction-locking devices include lock nuts, stiff nuts, and special washers. Positive-locking devices tighten nuts securely with slotted nuts, crowned nuts, tab washers, a
1 views • 7 slides
Understanding Electrostatic Sensitive Devices (ESDS)
Electrostatic Sensitive Devices (ESDS) are susceptible to damage caused by electrostatic discharge (ESD). This results from the transfer of electrostatic charge induced by high electrical fields. ESD can alter the characteristics of semiconductor devices, leading to malfunctions or failures in elect
0 views • 34 slides
Understanding Input and Output Devices in a Computer
Input devices play a crucial role in sending data to a computer, allowing users to communicate instructions for processing, display, storage, and transmission. Key input devices include keyboards and mice, each serving specific functions and enhancing data collection and accuracy. Discover the advan
0 views • 17 slides
Data Protection Incidents and Fines: Lessons Learned
Learn from real-life data protection scenarios that led to fines and breaches, such as improper data handling with USB devices, confidential files ending up in public recycling, misdirected emails of sensitive data, and unsecured mobile devices leading to theft. Understand the consequences and best
0 views • 9 slides
Perceptions of Medical Students on Point-of-Care Ultrasound Devices
This study evaluates medical students' perceptions of SonoSite Edge II and Butterfly iQ ultrasound devices for enhancing learning experiences in ultrasound and medicine. The research involved first-year medical students using both devices and providing feedback through pre- and post-session surveys.
3 views • 10 slides
Guide to Creating Access from Wired to Wireless Devices Using Airborne AP Ethernet Bridge
Explore a comprehensive guide on setting up access from wired to wireless devices using Airborne AP Ethernet Role Bridge. Learn how to connect a PLC and a wireless laptop to the same network, configure settings for both devices, and successfully ping between the devices. Follow step-by-step instruct
2 views • 7 slides
Understanding Computer Hardware: Key Input Devices and Pointing Devices
Explore essential computer hardware components such as keyboards, mice, and pointing devices. Learn about the different types of keyboards including ergonomic and laser keyboards, as well as various mouse types like wireless, cabled, and optical mice. Discover how pointing devices like touch screens
0 views • 18 slides
Overview of Computer Input and Output Devices
Input devices of a computer system consist of external components like keyboard, mouse, light pen, joystick, scanner, microphone, and more, that provide information and instructions to the computer. On the other hand, output devices transfer information from the computer's CPU to the user through de
0 views • 11 slides
Understanding Input and Output Devices in Computers
Input devices like keyboards, mice, joysticks, light pens, scanners, and more play a crucial role in interacting with computers. This chapter explores the functions and features of various input devices used in computing, such as keyboards for data input, mice for cursor control, and joysticks for C
0 views • 12 slides
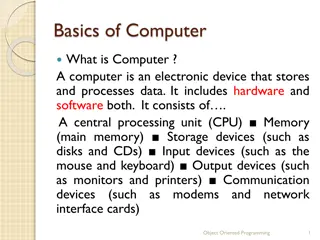
Understanding Basics of Computer Systems
A computer is an electronic device that stores and processes data using hardware and software components. It consists of a CPU, memory, storage devices, input/output devices, and communication devices. The CPU includes a Control Unit and Arithmetic Logic Unit, and the memory stores data in bytes. St
0 views • 57 slides
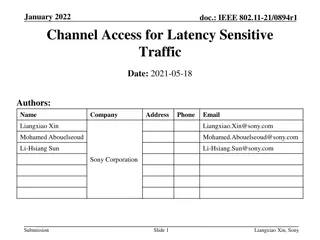
Enhancing Channel Access for Latency-Sensitive Traffic in January 2022
In the documentation IEEE 802.11-21/0894r1, the focus is on improving channel access for latency-sensitive traffic through concepts like Restricted TWT (Target Wake Time). The proposal suggests methods to protect TWT Service Periods from non-TWT scheduled STAs, ensuring prioritized transmission of l
0 views • 11 slides
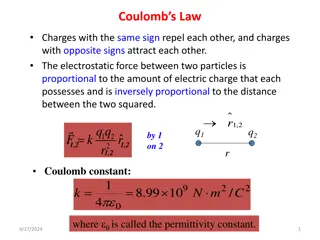
Understanding Coulomb's Law in Electrostatic Interactions
Coulomb's Law states that charges with the same sign repel each other, while charges with opposite signs attract. The strength of the electrostatic force between two particles is directly related to the amount of charge each possesses and inversely proportional to the square of the distance between
0 views • 24 slides
Security Concerns and Future Challenges of Internet Connected Devices in Budva, Montenegro
With the increasing number of Internet-connected devices and IoT, the security concerns are escalating. In the past, communication was restricted to servers and terminals, but now everyone is connected globally. The future poses even greater risks with IoT becoming prevalent. Reasons for concern inc
0 views • 17 slides
Gentle Cleanser for Maintaining Healthy and Refreshed Sensitive Skin
Atomy Aidam offers a gentle cleanser that maintains the health and freshness of sensitive skin, leaving you with a revitalizing feeling. The Oriental Herb Complex, developed with natural herbs like chamomile and rosemary, enhances skin immunity and provides a natural aroma that keeps your private ar
0 views • 4 slides
Understanding Electrostatic Discharge (ESD) in Precision Electronics
Explore the world of Electrostatic Discharge (ESD) and how it impacts precision electronics like op-amps and semiconductors. Learn about ESD generation, IC device sensitivity thresholds, ESD damage mechanisms, ESD protection methods, and device ESD robustness testing. Dive into the crucial aspects o
0 views • 33 slides
Understanding Electrostatic Properties of Polyelectrolyte Solutions for DNA Molecules
Double-stranded DNA molecules exhibit repulsion due to their linear charge distribution, which can be mitigated by positively charged counter-ions. The Bjerrum length and Manning structural parameter play crucial roles in defining charge density. Electrostatic repulsion terms and calculations involv
0 views • 27 slides
Wireless Office Docking Model for Multiple Devices
This document outlines a usage model for office docking involving wireless connections between mobile devices and various peripheral devices such as monitors, hard drives, printers, and more. It describes scenarios for single and multiple devices in both home and office settings, emphasizing the nee
0 views • 5 slides
Understanding I/O Systems and Devices
I/O systems and devices play a crucial role in computer operations. They can be categorized into block devices and character devices based on their functionalities. Block devices store information in fixed-size blocks with addresses, while character devices handle character streams. Some devices, li
0 views • 19 slides
Gait Device Selection for Children with Lumbar Level Myelomeningocele
This presentation discusses the considerations and choices of gait devices for children with lumbar level myelomeningocele. It covers the specific needs of pediatric patients, benefits and drawbacks of various devices, funding requirements, and clinical application through case studies. The material
0 views • 31 slides
Understanding Trauma-Sensitive Discipline Policies in Schools
Explore the concept of trauma-sensitive discipline policies in schools within the framework of VTSS TFI 1.6. Gain insights into changes in the Model Code of Conduct, identify vulnerable decision points, and incorporate trauma-sensitive approaches to respond to challenging behaviors. Embrace proactiv
0 views • 34 slides
Understanding Electric Potential and Its Relationship to Electrostatic Energy
Electric potential is intricately linked to electrostatic potential energy, much like how electric field correlates to electrostatic force. The change in electric potential equals the change in electrostatic potential energy per unit positive test charge, expressed in volts. By exploring scenarios s
0 views • 24 slides
Understanding the Risks of Sensitive Sectors in Free Trade Agreements
Explore the intricacies of sensitive sectors in Free Trade Agreements (FTAs) through an in-depth analysis of the potential dangers and benefits. Delve into the complexities of preferential tariff cuts, trade creation versus diversion, rules of origin, and the exemption of sensitive sectors. Learn ho
0 views • 27 slides
Electrostatic Distortion Studies at SINP Kolkata and DESY
Studies on electrostatic distortion were conducted at SINP Kolkata and DESY, focusing on a Large Prototype TPC experiment with Bulk Micromegas modules. The experiments included varying electron beam energies, gas mixtures, cosmic ray data collection, drift velocity estimation, and more. Distortions
0 views • 7 slides
The Water Sensitive City Theory: Climate Change Adaptation Approach
The Water Sensitive City Theory explores how cities can evolve into integrated, adaptive, and climate-resilient water systems. It emphasizes restoring natural water balance, providing ecosystem services, and fostering water-sensitive communities. This approach is crucial for climate change adaptatio
0 views • 16 slides
Combatting Counterfeit and Substandard ICT Devices: IMEI Ecosystem & Its Role
The conference held in Geneva, Switzerland in November 2014 addressed the critical issue of combatting counterfeit and substandard ICT devices, focusing on the IMEI ecosystem and its significance in preventing the use of counterfeit devices. James Moran, Security Director at GSM Association, highlig
0 views • 12 slides
Managing Sensitive Data in Cloud Infrastructures: Best Practices and Considerations
Explore the orchestration of cloud infrastructures for handling sensitive data, including the importance of context, legal considerations, and utilizing self-assessment tools like CAIQ. Learn about QDR's current infrastructure at Syracuse University and the challenges of storing sensitive data in th
0 views • 10 slides
Proxy QoS Management for XR Devices in IEEE 802.11-23/1958r0 - November 2023
This document discusses the challenges faced by XR devices in terms of size, thermal constraints, cost, and power limitations leading to the proposal of Proxy QoS Management to enhance Wi-Fi performance. The aim is to leverage TGbn devices for improving legacy devices' connectivity within a Wi-Fi ne
0 views • 6 slides