Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
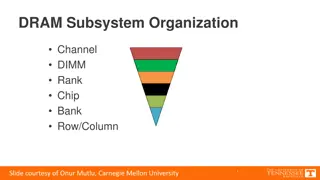
Understanding the Organization of DRAM Subsystem Components
Explore the intricate structure of the DRAM subsystem, including memory channels, DIMMs, ranks, chips, banks, and rows/columns. Delve into the breakdown of DIMMs, ranks, chips, and banks to comprehend the design and functioning of DRAM memory systems. Gain insights into address decoding, row/column
0 views • 16 slides
Computer Architecture: Understanding SRAM and DRAM Memory Technologies
In the field of computer architecture, SRAM and DRAM are two prevalent memory technologies with distinct characteristics. SRAM retains data as long as power is present, while DRAM is dynamic and requires data refreshing. SRAM is built with high-speed CMOS technology, whereas DRAM is more dense and b
1 views • 38 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
High-Throughput True Random Number Generation Using QUAC-TRNG
DRAM-based QUAC-TRNG provides high-throughput and low-latency true random number generation by utilizing commodity DRAM devices. By employing Quadruple Row Activation (QUAC), this method outperforms existing TRNGs, achieving a 15.08x improvement in throughput and passing all 15 NIST randomness tests
0 views • 10 slides
SIMDRAM: An End-to-End Framework for Bit-Serial SIMD Processing Using DRAM
SIMDRAM introduces a novel framework for efficient computation in DRAM, aiming to overcome data movement bottlenecks. It emphasizes Processing-in-Memory (PIM) and Processing-using-Memory (PuM) paradigms to enhance processing capabilities within DRAM while minimizing architectural changes. The motiva
2 views • 14 slides
Insights into DRAM Power Consumption and Design Concerns
Detailed experimental study reveals that DRAM power models may not provide accurate insights into power consumption. The increasing importance of managing DRAM power in system design is emphasized. The study delves into DRAM organization, operation, and power consumption patterns, highlighting the n
0 views • 43 slides
Dram Shop Act and Premises Liability for Bar and Tavern Owners
Understanding the liabilities and responsibilities of bar and tavern owners under the Dram Shop Act based on the case of Build It and They Will Drink, Inc. v. Strauch. The act outlines exceptions where licensees can be held civilly liable for selling alcohol to minors or visibly intoxicated individu
0 views • 12 slides
Improving GPGPU Performance with Cooperative Thread Array Scheduling Techniques
Limited DRAM bandwidth poses a critical bottleneck in GPU performance, necessitating a comprehensive scheduling policy to reduce cache miss rates, enhance DRAM bandwidth, and improve latency hiding for GPUs. The CTA-aware scheduling techniques presented address these challenges by optimizing resourc
0 views • 33 slides
Enhancing Multi-Node Systems with Coherent DRAM Caches
Exploring the integration of Coherent DRAM Caches in multi-node systems to improve memory performance. Discusses the benefits, challenges, and potential performance improvements compared to existing memory-side cache solutions.
0 views • 28 slides
Enhancing Memory Cache Efficiency with DRAM Compression Techniques
Explore the challenges faced by Moore's Law in relation to bandwidth limitations and the innovative solutions such as 3D-DRAM caches and compressed memory systems. Discover how compressing DRAM caches can improve bandwidth and capacity, leading to enhanced performance in memory-intensive application
0 views • 48 slides
Architecting DRAM Caches for Low Latency and High Bandwidth
Addressing fundamental latency trade-offs in designing DRAM caches involves considerations such as memory stacking for improved latency and bandwidth, organizing large caches at cache-line granularity to minimize wasted space, and optimizing cache designs to reduce access latency. Challenges include
0 views • 32 slides
Understanding RowPress: A New Read Disturbance Phenomenon in Modern DRAM Chips
Demonstrating and analyzing RowPress, a novel read disturbance phenomenon causing bitflips in DRAM chips. Different from RowHammer vulnerability, RowPress showcases effective solutions on real Intel systems with DRAM chips.
0 views • 46 slides
Managing DRAM Latency Divergence in Irregular GPGPU Applications
Addressing memory latency challenges in irregular GPGPU applications, this study explores techniques like warp-aware memory scheduling and GPU memory controller optimization to reduce DRAM latency divergence. The research delves into the impact of SIMD lanes, coalescers, and warp-aware scheduling on
0 views • 33 slides
Panopticon: Complete In-DRAM Rowhammer Mitigation
Despite extensive research, DRAM remains vulnerable to Rowhammer attacks. The Panopticon project proposes a novel in-DRAM mitigation technique using counter mats within DRAM devices. This approach does not require costly changes at multiple layers and leverages existing DRAM logic for efficient miti
0 views • 17 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
Understanding DRAM Errors: Implications for System Design
Exploring the nature of DRAM errors, this study delves into the causes, types, and implications for system design. From soft errors caused by cosmic rays to hard errors due to permanent hardware issues, the research examines error protection mechanisms and open questions surrounding DRAM errors. Pre
0 views • 31 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
Transparent Hardware Management of Stacked DRAM for Memory Systems
Explore the innovative use of stacked DRAM as Part of Memory (PoM) to increase overall memory capacity and eliminate duplication. The system involves OS-managed PoM, challenges, and the potential of hardware-managed PoM to reduce OS-related overhead. Learn about the practical implications and evalua
0 views • 24 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Challenges and Solutions in Memory Hierarchies for System Performance Growth
The evolution of memory scaling poses challenges for system performance growth due to limitations in memory hierarchy, capacity gaps, and DRAM scaling obstacles. The need for alternative technologies and architectural support to address these challenges is highlighted, focusing on reducing latency,
0 views • 23 slides
Understanding Latency Variation in Modern DRAM Chips
This research delves into the complexities of latency variation in modern DRAM chips, highlighting factors such as imperfect manufacturing processes and high standard latencies chosen to boost yield. The study aims to characterize latency variation, optimize DRAM performance, and develop mechanisms
0 views • 37 slides
Understanding Power Consumption in Memory-Intensive Databases
This collection of research delves into the power challenges faced by memory-intensive databases (MMDBs) and explores strategies for reducing DRAM power draw. Topics covered include the impact of hardware features on power consumption, experimental setups for analyzing power breakdown, and the effec
0 views • 13 slides
A Software Memory Partition Approach for Eliminating Bank-level Interference in Multicore Systems
Memory requests from different threads can cause interferences in DRAM banks, impacting performance. The solution proposed involves partitioning DRAM banks between threads to eliminate interferences, leading to improved performance and energy savings.
0 views • 32 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Enhancing DRAM Performance with ChargeCache: A Novel Approach
Reduce average DRAM access latency by leveraging row access locality with ChargeCache, a cost-effective solution requiring no modifications to existing DRAM chips. By tracking recently accessed rows and adjusting timing parameters, ChargeCache achieves higher performance and lower DRAM energy consum
0 views • 33 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
0 views • 68 slides
Intelligent DRAM Cache Strategies for Bandwidth Optimization
Efficiently managing DRAM caches is crucial due to increasing memory demands and bandwidth limitations. Strategies like using DRAM as a cache, architectural considerations for large DRAM caches, and understanding replacement policies are explored in this study to enhance memory bandwidth and capacit
0 views • 23 slides
Enhancing Data Movement Efficiency in DRAM with Low-Cost Inter-Linked Subarrays (LISA)
This research focuses on improving bulk data movement efficiency within DRAM by introducing Low-Cost Inter-Linked Subarrays (LISA). By providing wide connectivity between subarrays, LISA enables fast inter-subarray data transfers, reducing latency and energy consumption. Key applications include fas
0 views • 49 slides
CLR-DRAM: Dynamic Capacity-Latency Trade-off Architecture
CLR-DRAM introduces a low-cost DRAM architecture that enables dynamic configuration for high capacity or low latency at the granularity of a row. By allowing a single DRAM row to switch between max-capacity and high-performance modes, it reduces key timing parameters, improves system performance, an
0 views • 42 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Revolutionizing Security Testing with BDD-Security
Explore the innovative approach of Continuous and Visible Security Testing with BDD-Security by Stephen de Vries. Gain insights into how security testing can be integrated seamlessly into modern development practices, shifting the focus from reactive to proactive measures. Learn about the importance
0 views • 33 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides
Locality-Aware Caching Policies for Hybrid Memories
Different memory technologies present unique strengths, and a hybrid memory system combining DRAM and PCM aims to leverage the best of both worlds. This research explores the challenge of data placement between these diverse memory devices, highlighting the use of row buffer locality as a key criter
0 views • 34 slides