Securitization of Covid-19 in Hong Kong: Trust and Success
Analyzing the successful securitization of Covid-19 in Hong Kong amidst low political trust, this study explores the role of trust, smart technologies, and governmental factors in managing the pandemic. Key elements include political trust, audience acceptance, smart technology trust, and effectiven
2 views • 19 slides
Understanding Regular Expressions for Text Processing
Regular expressions provide a powerful way to search for and manipulate text strings by specifying patterns. This content explores different aspects of regular expressions, including disjunctions, negations, more disjunctions, optional characters, anchors, and examples. By learning how to use regula
2 views • 46 slides
Roughtime: Securing time for IoT devices
Accurate time is crucial for security protocols like DNSSEC and TLS in IoT devices. Roughtime protocol, with improved accuracy and security features, provides a solution for securing time in resource-constrained environments. The protocol addresses the bootstrapping problem and allows for microsecon
1 views • 8 slides
Understanding Trust in Contemporary Leadership
Trust is the foundation of effective leadership, comprising elements like integrity, competence, consistency, loyalty, and openness. Trust plays a crucial role in leadership, impacting team performance and cooperation. Different types of trust - deterrence-based, knowledge-based, and identification-
0 views • 9 slides
Understanding the Role of Alveolar Process in Dental Development
The alveolar process in the upper and lower jaw plays a vital role in housing, supporting, and protecting teeth. It anchors tooth roots, facilitates tooth movement for proper occlusion, absorbs and distributes occlusal forces, supplies vessels to the periodontal ligament, and aids in tooth eruption.
1 views • 28 slides
Examining Citizen Trust in Malawian Governance Over Two Decades (1999-2019)
This paper critically analyzes public trust in key government institutions in Malawi from 1999 to 2019, highlighting a general decline in trust levels and its impact on political legitimacy. The study explores factors influencing public trust, such as perceptions of government performance, integrity
0 views • 12 slides
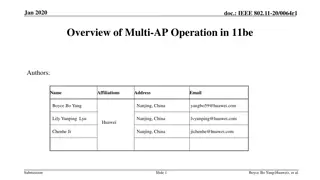
Overview of Multi-AP Operation in IEEE 802.11be
The document discusses the unique feature of multi-AP operation in IEEE 802.11be, emphasizing the performance benefits in various deployments. It addresses the need for AP-to-AP communication, the concept of anchor APs, interfaces for inter-AP communication, and backhaul options. The importance of f
0 views • 13 slides
Leadership, Trust, and Crisis: Lessons from Central Europe Project
The project funded by multiple governments in Central Europe aims to advance sustainable regional cooperation. The initiative focuses on understanding leadership as a process involving trust, especially in crisis situations. The lesson structure includes case studies, discussions on resources, and e
4 views • 19 slides
Methods of Joining Steel and Concrete in Construction
Connections between steel and concrete in construction projects require special consideration due to differences in material properties. Techniques like using bolts, shims, grouting, and resin anchors are employed to create strong and stable connections that distribute stresses effectively. Each con
0 views • 17 slides
Exploring Trust and Distrust in Social Interactions
Understanding the dynamics of trust and distrust within social interactions is vital for successful service delivery and relationship-building, especially in youth work settings. This case study highlights the complexities of gaining trust, the significance of trusting relationships, and the cultura
1 views • 50 slides
Challenges Faced in DNSSEC Deployment by Geoff Huston at APNIC June 2016
Geoff Huston addresses the challenges of DNSSEC deployment, discussing turning on validation in Bind configurations, reasons why it may be perceived as difficult, and the importance of DNSSEC in enhancing security within the DNS. Despite concerns about increased resolution time and limited signed na
0 views • 14 slides
Trust Dynamics in AI-Powered Pharmaceutical Business: A Critical Analysis
Exploring the intricate relationship between AI and human trust in the context of the pharmaceutical industry, this presentation delves into the factors influencing trust dynamics and proposes implementation strategies to foster trust between sales representatives and oncologists in AI-supported too
2 views • 12 slides
DNS Research Federation: Advancing Understanding of Cybersecurity Impact
The DNS Research Federation, a UK non-profit organization, aims to advance the understanding of the Domain Name System's impact on cybersecurity, policy, and technical standards through education, research, and improved data access. Motivated by the need to measure resolver capabilities, they have d
0 views • 17 slides
Exploring DANE, DNSSEC, and TLS in Go6Lab
Delve into the implementation of DANE, DNSSEC, and TLS protocols at Go6Lab, a testing facility affiliated with ISOC/Go6 Institute in Slovenia. The setup includes DNSSEC implementation with PowerDNS and OpenDNSSEC, DANE experimentation with Postfix servers, and verification processes for TLS certific
0 views • 36 slides
Medical Education Program Objectives (MEPOs) and Milestones for Trek Curriculum October 2023
The Medical Education Program Objectives (MEPOs) and Milestones for the Trek Curriculum in October 2023 focus on guiding principles for assessment and setting milestones to ensure student success in various phases of the curriculum. Detailed templates with definitions and descriptions of outcomes, m
0 views • 29 slides
Enhancing WHOIS Updates with DNSSEC, ASPLAIN, and Abuse Contact Implementation
Explore the latest updates in WHOIS, including DNSSEC deployment, ASPLAIN support, and abuse contact policies. Learn about DNSSEC deployment plans, ASPLAIN formats, and recommendations for abuse handling. Stay informed on domain security and network contact protocols.
0 views • 22 slides
Understanding Social Judgment Theory: Persuasion and Cognitive Maps
Social Judgment Theory (SJT) involves self-persuasion through comparing new ideas with existing attitudes. By considering an example where individuals have differing views on religion, the theory explores persuasion strategies focusing on anchors, alternatives, and ego-involvement. Reflective journa
0 views • 10 slides
Understanding Trust and Equitable Charges in Property Law
Trust and equitable charges in property law involve a legal obligation where the property holder manages the property for the benefit of another person. This trust relationship consists of elements like legal title, trust property, and beneficiaries. The creators of a trust can be referred to as set
0 views • 25 slides
Upgrade Requirements, Challenges, and Solutions for Same-Server DoT Implementation
Explore the transition from Do53 to DoT without changing resolvers, addressing challenges in DNS resolvers, TLS standards, and forwarder complications. Discover partial solutions through DANE TLSA certificates, DNS zone publishing, and DNSSEC trust anchors for enhanced security and upgrade process e
0 views • 14 slides
Trust-Based Anonymous Communication Models and Routing Algorithms
This research paper discusses trust-based anonymous communication models and routing algorithms in the context of onion routing, emphasizing the importance of trust in mitigating security risks from adversaries with resources. The paper presents a model of trust and proposes trust-based routing algo
0 views • 65 slides
Member Quality Update: Enhancing Strategic Anchors and Department Goals
Explore the latest updates on Member Quality from the Spring 2018 Regional Meetings. Discover strategic anchors, department goals, and ongoing optimization plans. Delve into monitoring processes, educational efforts, efficiency enhancements, and the focus on process improvement to ensure sustainable
0 views • 13 slides
Apache Traffic Control Update Highlights
Apache Traffic Control provides insights into recent changes and upcoming developments, including Traffic Router updates, DNSSEC implementation, monitoring changes, and roadmap fixes. Stay informed about the project's progress and future plans.
0 views • 8 slides
Understanding Regular Expressions in Natural Language Processing
Dive into the world of regular expressions for text processing in NLP, learning about disjunctions, negations, patterns, anchors, and practical examples. Discover how to efficiently search for specific text strings using these powerful tools.
0 views • 34 slides
Evolution of DNSSEC Implementation at Nominet
This content details the evolution of DNSSEC implementation at Nominet, covering key milestones from initial infrastructure deployment in 2008 to the adoption of a new approach in 2016. It discusses the challenges faced, technology used over the years, and the transition to a new DNSSEC approach in
0 views • 8 slides
Member Quality Update Spring 2018 Regional Meetings Overview
Explore the highlights of the Member Quality Update Spring 2018 Regional Meetings, focusing on strategic anchors, department goals, changes implemented, and those to come. Dive into topics like monitoring, education, efficiency, and process improvement. Engage with polling questions, reviews, and an
0 views • 13 slides
Social Divisions in 1920s America: Traditionalists vs. Modernists
In the 1920s, American society was divided along social, economic, and religious lines, leading to tensions between traditionalists and modernists. Traditionalists upheld long-held cultural and religious values as anchors of stability, while modernists embraced new ideas and trends, viewing traditio
0 views • 14 slides
Understanding Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
0 views • 7 slides
Understanding Regular Expressions and Pattern Matching
Learn about regular expressions, pattern matching, and text processing through examples and explanations provided in Dan Jurafsky's materials. Discover how to use disjunctions, negations, anchors, and other functionalities to search and manipulate text strings effectively.
0 views • 14 slides
SaudiNIC's Experience in Deploying DNSSEC
SaudiNIC embarked on a comprehensive journey to deploy DNSSEC, starting with observing its growth and conducting in-depth studies on pioneer implementations worldwide. The project involved creating a startup team, drafting procedures, conducting workshops, and enabling DNSSEC on various platforms. K
0 views • 16 slides
Understanding DNSSEC: Adding Digital Signatures to DNS Responses
DNSSEC (Domain Name System Security Extensions) allows for the addition of digital signatures to DNS responses, ensuring the authenticity, completeness, and currentness of the data received by a client. By validating the digital signature, clients can trust the response received is genuine and unalt
0 views • 27 slides
Evaluation of Ed25519 Cryptography Performance in DNSSEC Validation
Edwards Curve Cryptography, specifically the Ed25519 algorithm, offers faster performance and high crypto density compared to other algorithms. This evaluation study compares key sizes, processing times, and validation support for Ed25519, ECDSA P-256, RSA-2048, and RSA-4096 in DNSSEC validation sce
0 views • 19 slides
Trust as a Proxy for Certainty in Social Cohesion
Exploring the intricate relationship between trust, security, and social cohesion, this study delves into how trust serves as a proxy for certainty in uncertain environments. By analyzing societal properties and the role of trust in managing risks and insecurities, the Peace Research Institute Oslo
0 views • 16 slides
Cultivating Compassionate Trust in Society: A Qualitative Exploration
This qualitative investigation delves into the concept of compassionate trust and its role in fostering positive societal interactions. Through a social constructionist lens, the study explores how individuals understand and embody compassionate trust, emphasizing the interconnectedness of compassio
0 views • 16 slides
Evolution of ARIN: RPKI and DNSSEC Implementation
Explore the transformation at ARIN as it embraces RPKI and DNSSEC technologies. Discover the significance of DNSSEC and RPKI, the changes needed for DNSSEC deployment, and the functionalities of RPKI in securing network resources. Dive into the critical role these technologies play in enhancing rout
0 views • 46 slides
Trust Metric Estimator: Computational Model for Trustworthiness Assessment
The Trust Metric Estimator project aims to create a computational model to estimate user trust levels towards system performance over time. It considers social and technical factors, integrating trust, trustworthiness, and economic aspects to aid decision-making. Research includes surveys to identif
2 views • 8 slides
Trust-Based Data Governance Models and Their Impact on Personal Data Regulation
This article delves into trust-based data governance models, contrasting them with control-based models in the context of personal data regulation. It explores the challenges and benefits associated with both approaches, emphasizing the emergence of new models centered on trust such as data stewards
0 views • 11 slides
Building Trust in Public Institutions: Insights and Strategies
Public trust in government institutions is declining in many OECD countries. Existing measures of trust often reflect leadership approval. Satisfaction with public services plays a crucial role in fostering trust. Investing in trust involves focusing on governance drivers and actions that enhance tr
0 views • 15 slides
Trust Evaluation Process in Tribal Compacts and Trust Funds Administration
Trust Evaluations are mandated under the Tribal Self Governance Act for Tribes engaging in trust programs. The Bureau of Trust Funds Administration conducts these evaluations, focusing on compliance with federal laws and safeguarding trust assets. The process includes questionnaires, reviews, and re
0 views • 13 slides
Trust Dynamics in Political Relationships: Evidence and Implications
Exploring the intricate dynamics of trust between Principals and Agents in political relationships, this study delves into the implications of mistrust and the shift in trust levels over time. Utilizing surveys on political trust and data on trust in governmental branches, the analysis sheds light o
0 views • 22 slides
Edkaagmik Nbiizh Neyaashiinigamiingninwag Trust Overview
Edkaagmik Nbiizh Neyaashiinigamiingninwag Trust, established in 2012 by Chippewas of Nawash Unceded First Nation Coldwater Trust, aims to benefit the First Nations community through various initiatives such as land acquisition, education advancement, and cultural preservation. The Trust is managed b
0 views • 15 slides