A-Block-Sector-3-Noida
Discover the fully furnished office space for your business at A Block Sector 3 Noida. This prime commercial space offers 500 Sq.ft to 5,000 Sq.ft. area with excellent connectivity, modern amenities, and a thriving business environment with walking distance from metro station. Unlock this opportunit
1 views • 1 slides
Enhancing Student Success through Block Scheduling at KSU
National Institute for Student Success (NISS) diagnostic analysis at KSU shows the importance of block scheduling in increasing graduation rates and student engagement. Actions to increase registration for full-time schedules and improve student success are underway. The goals of KSU's block schedul
0 views • 10 slides
Restauration des Zones Humides pour un Avenir Durable
Les zones humides sont des écosystèmes cruciaux menacés par la disparition rapide. Leur restauration est essentielle pour préserver la biodiversité, protéger les ressources en eau douce, atténuer les effets des tempêtes et inondations, et stocker le carbone. Découvrez pourquoi il est urgent
1 views • 18 slides
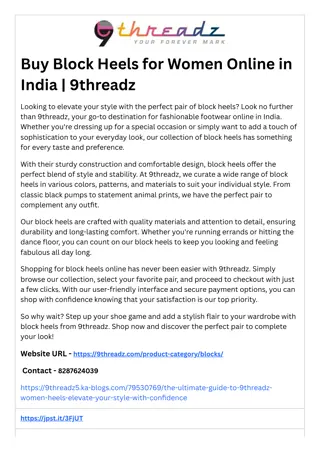
Buy Block Heels for Women Online in India 9threadz
\nLooking to elevate your style with the perfect pair of block heels? Look no further than 9threadz, your go-to destination for fashionable footwear online in India. Whether you're dressing up for a special occasion or simply want to add a touch of sophistication to your everyday look, our collectio
2 views • 4 slides
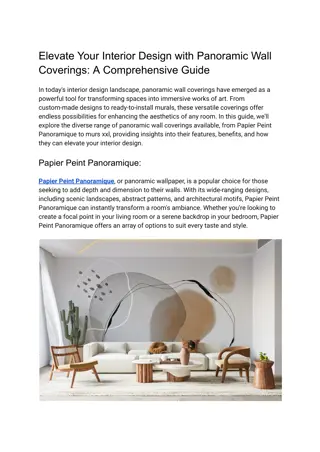
Transformez vos Murs avec du Papier Peint Panoramique et des Fresques Murales
D\u00e9couvrez une nouvelle dimension dans la d\u00e9coration murale avec notre s\u00e9lection de papier peint panoramique et de fresques murales. Que vous cherchiez \u00e0 cr\u00e9er une ambiance saisissante dans votre salon ou \u00e0 ajouter une touche artistique \u00e0 votre espace de travail, no
6 views • 6 slides
Améliorer la planification des transplantations hépatiques avis d'experts d'éminents chirurgiens en Inde
\ud83d\udc68\u200d\u2695\ud83d\udc89\ud83d\udc8a\ud83e\ude7a Le pays a connu des d\u00e9veloppements significatifs dans le domaine de la transplantation h\u00e9patique, avec des installations m\u00e9dicales de classe mondiale et des professionnels qualifi\u00e9s obtenant des r\u00e9sultats remarquab
3 views • 9 slides
Éléments Essentiels de Décoration : Découvrez l'Art des Fresques Murales Panoram
Plongez dans un monde d'expression artistique et d'\u00e9merveillement avec nos fresques murales panoramiques. Offrant des vues spectaculaires et des paysages captivants, ces \u0153uvres d'art murales transforment instantan\u00e9ment votre espace en une sc\u00e8ne immersive. Explorez notre collectio
2 views • 4 slides
Achetez des lampes de table et des appliques LED en ligne en France
Am\u00e9liorez votre cuisine avec des appareils \u00e9lectriques de qualit\u00e9 sup\u00e9rieure ! Achetez en ligne une large s\u00e9lection de gadgets efficaces. Faites de la cuisine un jeu d'enfant\u00a0!
1 views • 1 slides
Chemistry of f-Block Elements: Lanthanide and Actinide Series Overview
This segment delves into the properties, occurrence, and unique characteristics of the f-block elements, focusing on the Lanthanide and Actinide series. Covering topics such as color, oxidation states, spectral properties, lanthanide contraction, separation methods, and industrial applications of th
1 views • 15 slides
Plans de chirurgie de transplantation rénale à faible coût en Inde | Services de
\ud83d\udc68\u200d\u2695\ud83d\udc89\ud83d\udc8a\ud83e\ude7a L'Inde est connue pour fournir des services de sant\u00e9 abordables, notamment des chirurgies de transplantation r\u00e9nale \u00e0 faible co\u00fbt. Le pays compte plusieurs h\u00f4pitaux et centres m\u00e9dicaux sp\u00e9cialis\u00e9s da
1 views • 9 slides
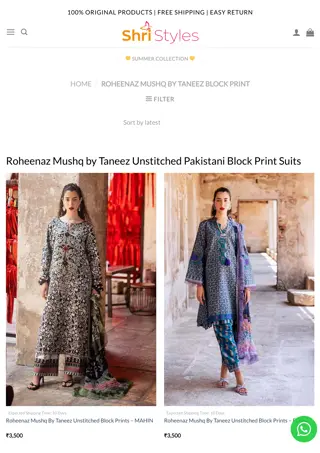
Roheenaz Mushq by Taneez Unstitched Pakistani Block Print Suits
Elevate your wardrobe with the Roheenaz Mushq by Taneez unstitched Pakistani block print suit. This exquisite ensemble features a printed lawn front, back, and sleeves, complemented by an embroidered silk neckline, side lace, and daman border. Paired with a printed chiffon dupatta and matching print
1 views • 10 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
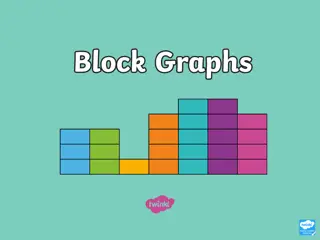
Understanding Block Graphs: Examples and Explanations
A block graph visually represents discrete data in a collection of blocks with no gaps between them. Each block must be carefully drawn with a title and axes labeled to explain the data shown. Examples include surveys on favorite activities, zoo animal sightings, and chocolate wrapper colors. Learn
0 views • 8 slides
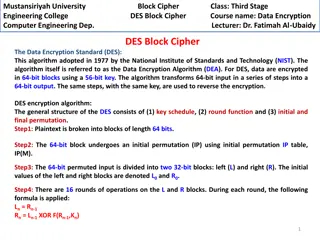
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Comparison of Erector Spinae Plane Block vs Serratus Anterior Plane Block in Thoracic Surgery Recovery
Minimally Invasive Thoracic Surgery often results in severe post-operative pain, typically managed with the Serratus Anterior Plane (SAP) block. This study compared the quality of recovery and morbidity between SAP and the relatively new Erector Spinae Plane (ESP) block. Results showed that ESP prov
1 views • 10 slides
IEEE 802.11-20/0055r0 Multi-link Block Ack Architecture Overview
This document from January 2020 presents an overview of the IEEE 802.11-20/0055r0 Multi-link Block Ack architecture proposed by Rojan Chitrakar from Panasonic. It discusses the negotiation of block ack agreements between multiple MLDs, common sequence number assignment, transmit and receive buffers,
1 views • 11 slides
Classification of Elements and Periodicity in Properties: Overview and Evolution
The journey of understanding the classification of elements and periodicity in properties begins with early laws like the Law of Triads and Newland's Law of Octaves. Mendeleev's Periodic Law revolutionized the organization of elements, leading to the modern periodic table. Discoveries of eka-alumini
3 views • 32 slides
Binary Basic Block Similarity Metric Method in Cross-Instruction Set Architecture
The similarity metric method for binary basic blocks is crucial in various applications like malware classification, vulnerability detection, and authorship analysis. This method involves two steps: sub-ldr operations and similarity score calculation. Different methods, both manual and automatic, ha
0 views • 20 slides
Deep Eutectic Solvents: Classification, Synthesis, and Applications
Deep Eutectic Solvents (DES) are versatile solvents formed by mixing specific acids and bases. These solvents exhibit unique hydrogen bonding properties, resulting in a lower melting point compared to individual components. DES can be classified into hydrophobic and hydrophilic types, each with dist
3 views • 7 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Utilisation du Pack PowerPoint pour Intégrer des Cartes dans Vos Présentations
Ce pack de PowerPoint fournit des cartes simples et personnalisables que vous pouvez intégrer dans vos présentations et rapports en ajoutant vos propres données. Il inclut des outils tels que des symboles, des légendes et des étiquettes que vous pouvez facilement copier et coller. Sélectionnez
0 views • 16 slides
D-Block Elements: Properties and Classification in Chemistry
Welcome to the Department of Chemistry at Kisan Veer Mahavidyalaya, Wai. Explore the Chemistry of Elements of the 3d series, focusing on d-Block Elements and Transition Elements. Learn about their electronic structure, colored ions, magnetic properties, oxidation states, and complex formation. Under
0 views • 34 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Taekwondo Techniques and Blocks: Defensive Moves in Action
Explore Taekwondo techniques such as the Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block, used for defense against different types of attacks in martial arts. Detailed descriptions and illustrations demonstrate how to execute these blocks effectively to protect various parts of th
1 views • 25 slides
Taekwondo Techniques - Basics and Blocks for Self-Defense
Explore the fundamental Taekwondo techniques focusing on blocking movements for self-defense. Learn about Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block with detailed descriptions and images illustrating each move. Enhance your understanding of these essential blocks in Taekwondo
4 views • 11 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
MLA Style Guide for Block Quotations
Learn how to format block quotations according to MLA style guidelines. Use a block quote for material longer than four lines, indent one inch from the left margin, and type it double-spaced without quotation marks. Remember to introduce block quotations with a colon.
0 views • 4 slides
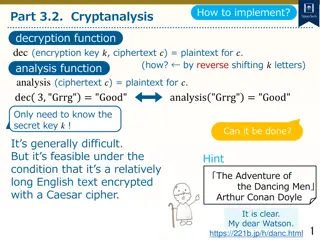
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Taekwondo Training: Block Techniques Explained
Dive into the world of Taekwondo block techniques with detailed descriptions and images of essential blocks such as Down Block, X Block, Knife-Hand Block, and Double Knife-Hand Block. Learn the proper execution and applications of each block to enhance your defensive skills in martial arts.
0 views • 25 slides
Taekwondo Techniques for Defense: Blocks and Movements
Explore the fundamental blocking techniques in Taekwondo, including the Down Block, X-Block, Knife-Hand Block, and Double Knife-Hand Block. Learn the proper execution and defense strategies against different types of attacks targeting various body sections. Enhance your skills and understanding of s
0 views • 11 slides
Understanding S-Block Elements in the Periodic Table
The s-block elements in the Periodic Table consist of 14 elements with unique properties and characteristics. Lithium, sodium, and potassium are notable members of Group 1, characterized by their reactivity and ability to form alkaline solutions when in contact with water. These soft metals exhibit
0 views • 23 slides
Guide for File Download Block Creation
In this guide, you will learn how to create a file download block on your webpage step by step. First, you need to click the small plus symbol, then initiate the file download process. You can customize the title, format, text color, and background theme accordingly. Finally, you can choose when and
0 views • 34 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides