Understanding Encoder and Decoder in Combinational Logic Circuits
In the world of digital systems, encoders and decoders play a crucial role in converting incoming information into appropriate binary forms for processing and output. Encoders transform data into binary codes suitable for display, while decoders ensure that binary data is correctly interpreted and u
4 views • 18 slides
Comparison Microscope and Borescope
Instruments like Stereomicroscope, Comparison Microscope, and Borescope are used for individual examination, side-by-side comparison, superimposition, and analysis of barrels in forensic investigations. Comparison microscopes are used for examining fired cartridge cases but have limitations such as
1 views • 8 slides
Laxmi Nagar: Your Shortcut to Digital Marketing Stardom
Living in Laxmi Nagar and dreaming of online marketing magic? Don't get tangled in the web of confusing terms like SEO and PPC! Laxmi Nagar is bursting with awesome digital marketing courses that ditch the jargon and make you a marketing whiz-kid in no time.\nThese courses are like secret decoder ri
1 views • 6 slides
Discovering Geometry and Measurement Concepts in Grade 9 Mathematics
Explore the fundamentals of geometry and measurement in grade 9 math, covering topics such as regular polygons, congruence and similarity of triangles, construction of similar figures, trigonometric ratios application, circle properties, and problem-solving related to triangles and parallelograms. U
0 views • 17 slides
Understanding Decoders and Multiplexers in Computer Architecture
Decoders and multiplexers are essential components in computer architecture, converting binary information efficiently. Integrated circuits house digital gates, enabling the functioning of these circuits. A decoder's purpose is to generate binary combinations, with examples like the 3-to-8-line deco
0 views • 37 slides
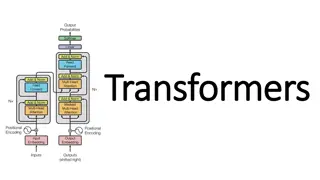
Evolution of Neural Models: From RNN/LSTM to Transformers
Neural models have evolved from RNN/LSTM, designed for language processing tasks, to Transformers with enhanced context modeling. Transformers introduce features like attention, encoder-decoder architecture (e.g., BERT/GPT), and fine-tuning techniques for training. Pretrained models like BERT and GP
1 views • 11 slides
Understanding Triangle Inequalities and Angle-Side Relationships
Explore the Vocabulary of Exterior Angle Inequality Theorem, Angle-Side Relationship Theorems 5.9 and 5.10. Understand how to order triangel angle measures and side lengths from smallest to largest through examples. Discover the principles governing triangles in terms of angles and side lengths.
0 views • 12 slides
Decoding and NLG Examples in CSE 490U Section Week 10
This content delves into the concept of decoding in natural language generation (NLG) using RNN Encoder-Decoder models. It discusses decoding approaches such as greedy decoding, sampling from probability distributions, and beam search in RNNs. It also explores applications of decoding and machine tr
0 views • 28 slides
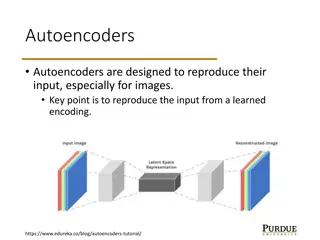
Understanding Variational Autoencoders (VAE) in Machine Learning
Autoencoders are neural networks designed to reproduce their input, with Variational Autoencoders (VAE) adding a probabilistic aspect to the encoding and decoding process. VAE makes use of encoder and decoder models that work together to learn probabilistic distributions for latent variables, enabli
6 views • 11 slides
Understanding the Structure and Role of Amino Acids in Proteins
Amino acids are building blocks of proteins, with distinct structures and properties. There are 20 common amino acids found in mammalian proteins, each with a carboxyl group, an amino group, and a unique side chain. The side chains determine the role of an amino acid in a protein, classified as nonp
8 views • 11 slides
Understanding Side Channels in Software Security
This content delves into the topic of side channels in software security, focusing on the leakage of sensitive information through timing side channels. It discusses the concept of covert channels, reference monitors, limitations of analysis, and prevention strategies to mitigate the risks associate
0 views • 25 slides
Stata-Python Rosetta Stone: Side-by-side Code Examples v1.0
A comprehensive guide providing side-by-side code examples in Stata, Python, and R, facilitating easy translation between the languages. It covers setting up Python for Stata, handling dataframes, storing datasets, working with log files, merging datasets, describing and summarizing data, and more.
1 views • 21 slides
Understanding Self-Realization and Balancing Left/Right Side Personality
Self-realization through understanding the subtle body's channels and chakras helps achieve emotional, physical, mental, and spiritual balance. The left side of the body is associated with past, desires, and emotions; imbalances can lead to negative emotions and psychometric diseases. Balancing tech
0 views • 17 slides
Understanding Triangle Congruence Properties
Delve into the principles of congruent triangles by exploring the properties of side-side-side (SSS), side-angle-side (SAS), angle-side-angle (ASA), and right-angle-hypotenuse-side (RHS) congruence. Visual explanations help clarify how these properties determine if triangles are congruent.
0 views • 18 slides
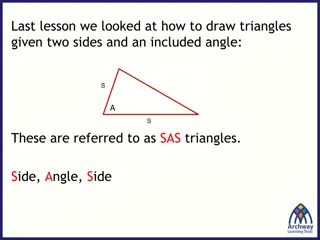
Constructing SSS Triangles: A Geometric Exercise
Explore the construction of Side-Side-Side (SSS) triangles step-by-step, using compass and straightedge techniques to draw triangles given specific side lengths. Understand the process of constructing triangles without angle information and enhance your geometric skills with practical examples.
0 views • 13 slides
Optimized Colour Ordering for Grey to Colour Transformation
The research discusses the challenge of recovering a colour image from a grey-level image efficiently. It presents a solution involving parametric curve optimization in the encoder and decoder sides, minimizing errors and encapsulating colour data. The Parametric Curve maps grayscale values to colou
0 views • 19 slides
Line Encoding Lab 6 - 2019/1440: Polar NRZ-L, RZ, and MAN Techniques with Decoder
Explore the Line Encoding Lab 6 from 2019/1440, featuring Polar NRZ-L, RZ, and MAN techniques with decoders. Dive into Simulink settings and output results for each encoding method. Discover how to modify binary number generators and pulse generators to enhance encoding. Conclude with a thank you me
0 views • 14 slides
Client-Side Tips & Tricks for RadControls for ASP.NET AJAX
Discover the client-side functionality offered by RadControls for ASP.NET AJAX, empowering developers to create high-performing web applications. Learn about client-side basics, common features, events, data binding, jQuery integration, and more.
0 views • 25 slides
Scatter-and-Gather Revisited: High-Performance Side-Channel-Resistant AES on GPUs
This research focuses on enhancing the security of AES encryption on GPUs by introducing the Scatter-and-Gather (SG) approach, aimed at achieving side-channel resistance and high performance. By reorganizing tables to prevent key-related information leakage, the SG approach offers a promising soluti
0 views • 34 slides
Investigation of LDPC Improvements in IEEE 802.11-24
This document delves into the investigation of LDPC (Low-Density Parity-Check) improvements within IEEE 802.11-24 standards. It discusses the history of LDPC codes in 802.11 networks, current FEC (Forward Error Correction) details, a new proposal for LDPC codes, recent LDPC code developments in vari
0 views • 24 slides
Understanding the Law of Sines for Finding Missing Side Lengths and Angle Measures
The Law of Sines is a fundamental concept in trigonometry that helps in finding missing side lengths and angle measures of any triangle. Through examples and explanations, this content teaches how to apply the Law of Sines to solve for unknowns in non-right triangles. It covers writing equations, su
0 views • 6 slides
Overview of Web Libraries, Tools, and Frameworks for Building Web Apps
Explore various client-side and server-side web libraries, tools, and frameworks such as Angular, Ember, Rails, Express, jQuery, d3, and more. Learn about the importance of web app frameworks, the challenges they solve, and considerations for choosing between server-side and client-side implementati
0 views • 57 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
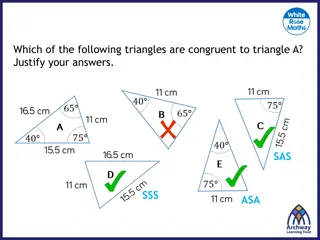
Understanding Triangle Congruence by SSS and SAS Postulates
Explore the Side-Side-Side (SSS) and Side-Angle-Side (SAS) postulates to prove triangle congruence. Learn how to use corresponding sides and included angles to establish congruence between triangles. Practice identifying congruent triangles and whether to use SSS or SAS for proof.
0 views • 11 slides
Common Side Effects of Diabetes Medications
Common side effects of diabetes medications include skin reactions, stomach issues, headaches, and more. Insulin injections may lead to localized or generalized reactions, while oral hypoglycemic drugs can cause gastrointestinal disturbances. Understanding these side effects is crucial for managing
0 views • 47 slides
Transformer Neural Networks for Sequence-to-Sequence Translation
In the domain of neural networks, the Transformer architecture has revolutionized sequence-to-sequence translation tasks. This involves attention mechanisms, multi-head attention, transformer encoder layers, and positional embeddings to enhance the translation process. Additionally, Encoder-Decoder
0 views • 24 slides
Exploring Triangle Similarity and Congruence
This content delves into understanding triangle congruence and similarity through various scenarios and visual representations. It discusses how to determine congruence using side-side-side, side-angle-side, and angle-side-angle criteria, and explores the concept of similarity in triangles based on
0 views • 21 slides
Advances in Completely Automatic Decoder Synthesis
This presentation by Y.C. Chou and H.S. Liu on "Towards Completely Automatic Decoder Synthesis" covers topics such as motivation, preliminary concepts, main algorithms, and experimental results in the field of communication and cryptography systems. The content delves into notation, SAT solvers, Cra
0 views • 35 slides
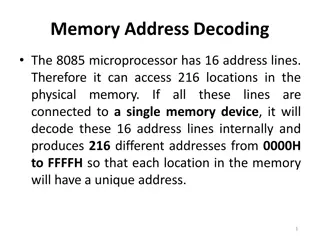
Memory Address Decoding in 8085 Microprocessor
The 8085 microprocessor with 16 address lines can access 216 locations in physical memory. Utilizing a 74LS138 address decoder, chip select signals are generated for memory block selection. The interfacing involves decoding address lines to enable memory access, with distinctions between RAM and ROM
0 views • 18 slides
Automatic Decoder Synthesis: Advancements in Communication and Cryptography
Cutting-edge progress in automatic decoder synthesis for communication and cryptography systems, presented in a comprehensive study covering motivation, prior work, preliminary notations, SAT solver algorithms, and experimental findings.
0 views • 32 slides
BIKE Cryptosystem: Failure Analysis and Bit-Flipping Decoder
The BIKE cryptosystem is a code-based KEM in the NIST PQC standardization process, utilizing the Niederreiter variant of the McEliece Construction with a QC-MDPC code. It ensures security against IND-CPA, and efforts are made to further confirm or disconfirm its estimates for IND-CCA security requir
0 views • 14 slides
High-Speed Hit Decoder Development for RD53B Chip
Development of a high-speed hit decoder for the RD53B chip by Donavan Erickson from MSEE ACME Lab, focusing on data streams, hitmap encoding, ROM splitting, decode engine building, and more. The process involves encoding methods, ROM setup with borrowed software look-up tables, and buffer systems fo
0 views • 33 slides
Understanding Drugs and Medicines: The Difference, Side Effects, and Prescription Necessity
Explore the distinctions between drugs and medicines, understanding side effects, and the importance of prescriptions for certain drugs. Learn about common side effects, prescription medicines, prescription drug abuse, and the roles of different types of medications in our body. Gain insights into r
0 views • 19 slides
Side Channel Monitoring in Additive Manufacturing for Cybersecurity and Quality Assurance
Side channel monitoring is crucial in the field of additive manufacturing to bridge cybersecurity and quality assurance. This process involves detecting physical domain data leakage through various side channels like acoustics, thermal, laser, vibration, electric current, optical, and pressure. By m
0 views • 10 slides
Neural Image Caption Generation: Show and Tell with NIC Model Architecture
This presentation delves into the intricacies of Neural Image Captioning, focusing on a model known as Neural Image Caption (NIC). The NIC's primary goal is to automatically generate descriptive English sentences for images. Leveraging the Encoder-Decoder structure, the NIC uses a deep CNN as the en
0 views • 13 slides
Side by Side Refrigerator in Pakistan: Best Picks for Spacious and Stylish Kitch
A Side by Side Refrigerator can be an exciting addition to modern kitchens that combine design space, efficiency, and space all in one piece. \/\/kinkedpress.com\/side-by-side-refrigerator-in-pakistan-best-picks-for-spacious-and-stylish-kitchens\/
1 views • 1 slides
Insights into the Rowhammering.BIKE Cryptosystem and Decoding Strategies
Explore the Rowhammering.BIKE cryptosystem, its parameters, and the black-grey flip decoder. Learn about the bitflipping algorithm, prior analysis of DFR in QC-MDPC decoders, and strategies for key recovery and decoding in this innovative system. Discover how understanding the error patterns related
0 views • 7 slides
Overview of BIKE Key Exchange Protocol by Ray Perlner
The BIKE (Bit-Flipping Key Exchange) protocol, presented by Ray Perlner, offers variants based on MDPC codes like McEliece and Niederreiter with a focus on quasi-cyclic structures. These non-algebraic codes show promise for key reduction, targeting IND-CPA security. The protocol features competitive
0 views • 18 slides
Understanding Attention Mechanism in Neural Machine Translation
In neural machine translation, attention mechanisms allow selective encoding of information and adaptive decoding for accurate output generation. By learning to align and translate, attention models encode input sequences into vectors, focusing on relevant parts during decoding. Utilizing soft atten
0 views • 17 slides
Understanding General Register Organization in Computer Architecture
In computer architecture, a common bus system is used to efficiently connect a large number of registers in the CPU. This enables communication between registers for data transfers and various microoperations. The setup includes multiple registers connected through a common bus, multiplexers for for
0 views • 40 slides