Buy Australian counterfeit Notes for sale - hartogcounterfeitnotes.com
Australian counterfeit notes for sale, Buy Fake Australian Dollars, buy Australian dollars online, and Counterfeit Australian Dollars: we produce are also made of polymer plastic. They have advanced security features and a see-through window like the original bills. holograms have the 3D effect maki
5 views • 5 slides
Buy Adderall XR 25mg - trinexpharmacy.com
Australian counterfeit notes for sale, Buy Fake Australian Dollars, buy Australian dollars online, and Counterfeit Australian Dollars: we produce are also made of polymer plastic. They have advanced security features and a see-through window like the original bills. holograms have the 3D effect maki
7 views • 3 slides
Buy AED 100 Online - globcoff
Find the best Emirati Dirham for online sale by the best sellers of Globcoff, it\u2019s the counterfeit Docky. If you are looking for the cheapest price online to buy AED 100, you are in the right position because Counterfeit Docky is the leading brand to deliver the best Emitti Dirham online.\nCont
2 views • 2 slides
Buy Counterfeit British Pounds Online - @Eurosbillsnotes
Buy top-quality undetectable Buy Counterfeit British Pounds Online to cover most of your expenses. Get fake British bills to cover most of your expenses. The United Kingdom is one of the most expensive countries in the world, with a high standard of living that comes at a cost. With rising property
2 views • 1 slides
How Does Counterfeit Money Affect the Economy - geldbe.com
How does counterfeit money affect the economy? poses a significant threat to the stability and integrity of economies.\n\nWhatsapp: 49 176 93784298
1 views • 11 slides
Buy Counterfeit Notes Online - @Eurosbillsnotes
We have extensive experience in Bank Note production Undetectable Bank Notes we are on WHATSAPP Leave your mobile phone number and we will send you a message Whatsapp No: 1(424)242-2620Text on: 49 15510 365783Counterfeit Money For Sale US Dollar Notes Canadian Dollar Australian Dollar British Doll
2 views • 27 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Buy Counterfeit Money UK - undetectablecounterfeitbills.com
Buy Counterfeit Money UK, the demand for counterfeit money has seen a surge, especially in regions like the UK. However, navigating this market can be tricky due to the prevalence of scams and fraudulent activities. \nText\/ WhatsApp: 1 (507) 544-8062\nEmail: info@undetectablecounterfeitbills.com\n
0 views • 4 slides
Unveiling the Counterfeit Trinity in Revelation: A Revealing Revelation
Dr. Charles Zimmerman delves into the concept of the counterfeit trinity as depicted in Revelation, contrasting it with the genuine trinity of Father, Son, and Spirit. The images and descriptions provided shed light on the symbolic elements in the biblical narrative, including the dragon, the beast,
1 views • 26 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
REAL COUNTERFEIT MONEY FOR SALE - UNDETECTABLECOUNTERFEITBILLS.COM
In the ever-evolving landscape of finance and commerce, the specter of counterfeit money looms as a persistent challenge. Counterfeit currency, often meticulously crafted to resemble genuine notes, poses a serious threat to the integrity of financial systems worldwide.\nContact: 1 (507) 544-8062\nE
1 views • 1 slides
HOW TO DETECT COUNTERFEIT NOTES - UNDETECTABLECOUNTERFEITBILLS.COM
How to detect counterfeit notes is a growing concern worldwide, posing significant risks to economies and individuals alike. Knowing how to detect counterfeit notes is crucial for both businesses and consumers to protect themselves from fraud. Contact: 1 (507) 544-8062 Email: info@undetectablecount
3 views • 1 slides
CAN YOU BUY COUNTERFEIT MONEY ONLINE - UNDETECTABLECOUNTERFEITBILLS.COM
The term \"counterfeit money\" describes counterfeit money that is created without official government approval and usually is an intentional attempt to mimic real money. The act of creating counterfeit money has a long history; the first instances can be found in ancient Greece and China. Contact:
1 views • 5 slides
How To Identify Counterfeit Money - undetectablecounterfeitbills.com
How To Identify Counterfeit Money is crucial not only for protecting your finances but also for maintaining the integrity of the economy. With counterfeiters becoming more sophisticated, it's essential to stay informed about the various methods and tools available to distinguish genuine currency fro
7 views • 1 slides
BUY COUNTERFEIT CAD ONLINE - UNDETECTABLECOUNTERFEITBILLS.COM
The demand for counterfeit money, particularly Canadian dollars (CAD), has increased recently. While some people may find it alluring to Buy Counterfeit CAD Online it\u2019s important to be aware of the dangers and repercussions involved in doing so. This article seeks to clarify the subject by prov
1 views • 1 slides
Counterfeit Detection Techniques in Currency to Combat Financial Fraud
Currency counterfeiting poses a significant challenge to the financial systems of countries worldwide, impacting economic growth. This study explores various counterfeit detection techniques, emphasizing machine learning and image processing, to enhance accuracy rates in identifying counterfeit curr
0 views • 15 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Hepatitis B Vaccines: Genuine vs Counterfeit - Insights from Uganda National Drug Authority
Explore the difference between genuine and counterfeit Hepatitis B vaccines in Uganda, as detailed by the National Drug Authority. Learn about the authorized vaccine on the market, counterfeit batch numbers, fake addresses on invoices/receipts, and the availability of vaccines in private sectors. St
0 views • 8 slides
NC22Plex STR Detection Kit: Advanced 5-Color Fluorescence Detection System
Explore the cutting-edge NC22Plex STR Detection Kit from Jiangsu Superbio Biomedical, offering a 5-color fluorescence detection system suitable for multiple applications. Enhance your research capabilities with this innovative product designed for precision and efficiency.
0 views • 20 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
VIIRS Boat Detection (VBD) Research Overview
The Visible Infrared Imaging Radiometer Suite (VIIRS) program, a joint effort between NASA and NOAA, focuses on weather prediction and boat detection using low light imaging data collected at night. The VIIRS system provides global coverage with sensitive instruments and efficient data flow processe
1 views • 13 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Stop Hidden Water Damage: Your Ultimate Guide to Leak Detection in San Diego
Learn how San Diego leak detection services can help protect your home from water damage. Discover the signs of leaks, advanced detection technologies, and tips to prevent costly repairs. Stay ahead with proactive slab leak detection and expert solut
0 views • 6 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
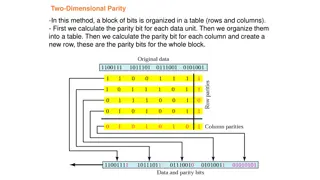
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
EPA Compliance Basics: Tank Leak Detection and Monitoring Methods
Learn about EPA requirements for tank leak detection, release detection methods, and compliance methods for monitoring tank systems. Understand the importance of implementing effective leak detection systems to prevent contamination and comply with federal regulations, including Automatic Tank Gaugi
0 views • 18 slides
Framework for Combatting Importation of Counterfeit Terminals in EACO Member States
This framework presentation by Mwende Njiraini from the Communications Authority of Kenya focuses on the definitions of counterfeit and substandard terminals, their impacts on industry, consumers, and governments, as well as proposed practical measures to combat the issue. It addresses challenges su
0 views • 26 slides
Addressing Counterfeit and Substandard ICT Devices in Brazil: The SIGA Project
The SIGA Project in Brazil aims to combat counterfeit and unauthorized ICT devices by implementing a centralized, automated, and scalable system to control the entrance of such devices into the market. Led by Anatel, the project involves key stakeholders to ensure the reliability and security of mob
0 views • 12 slides
Gas Detection of Hydrogen/Natural Gas Blends in the Gas Industry
Gas detection instruments play a crucial role in assessing the presence of hazardous atmospheres in the gas industry. This study focuses on the impact of adding hydrogen up to 20% in natural gas blends on gas detection instruments. The aim is to understand any potential inaccuracies in readings and
0 views • 30 slides
Timely San Diego Leak Detection | Protect Your Home from Water Damage
Discover the importance of timely leak detection in San Diego. Prevent costly water damage, reduce bills, and protect your home with professional leak detection services. Learn more about slab leak detection and prevention today!\n\nKnow more: \/\/m
0 views • 9 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
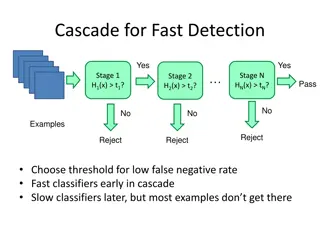
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Combatting Counterfeit and Substandard ICT Devices: IMEI Ecosystem & Its Role
The conference held in Geneva, Switzerland in November 2014 addressed the critical issue of combatting counterfeit and substandard ICT devices, focusing on the IMEI ecosystem and its significance in preventing the use of counterfeit devices. James Moran, Security Director at GSM Association, highlig
0 views • 12 slides